CloudFront distribution allows unencrypted (HTTP) communications.
Plain HTTP is unencrypted and human-readable. This means that if a malicious actor was to eavesdrop on your connection, they would be able to see all of your data flowing back and forth. You should use HTTPS, which is HTTP over an encrypted (TLS) connection, meaning eavesdroppers cannot read your traffic.
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Only allow HTTPS for CloudFront distribution communication
|
|
-
Log in to the AWS Management Console.
-
Select the “Services” option and search for CloudFront.
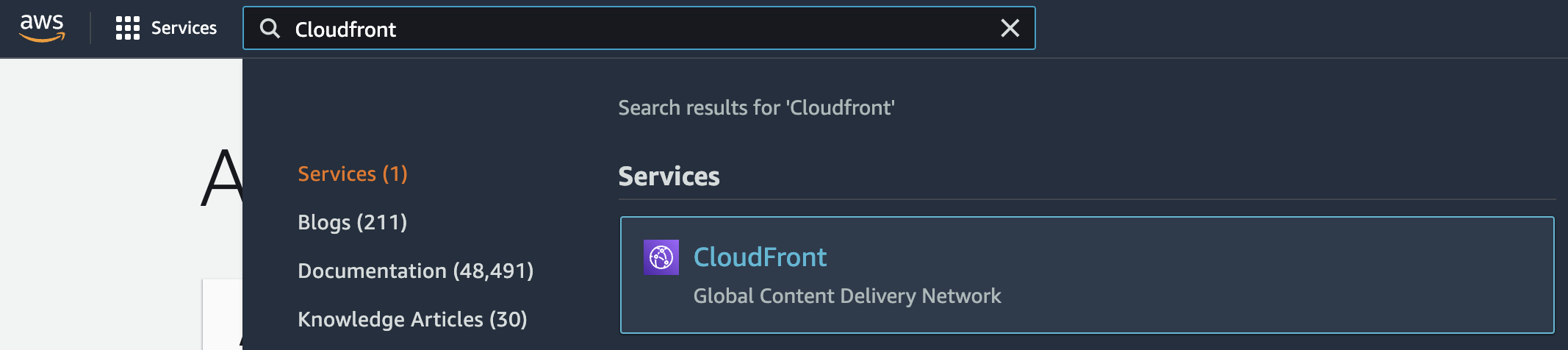
-
Select the “CloudFront Distribution” that needs to be verified and click on it to open its configuration settings.
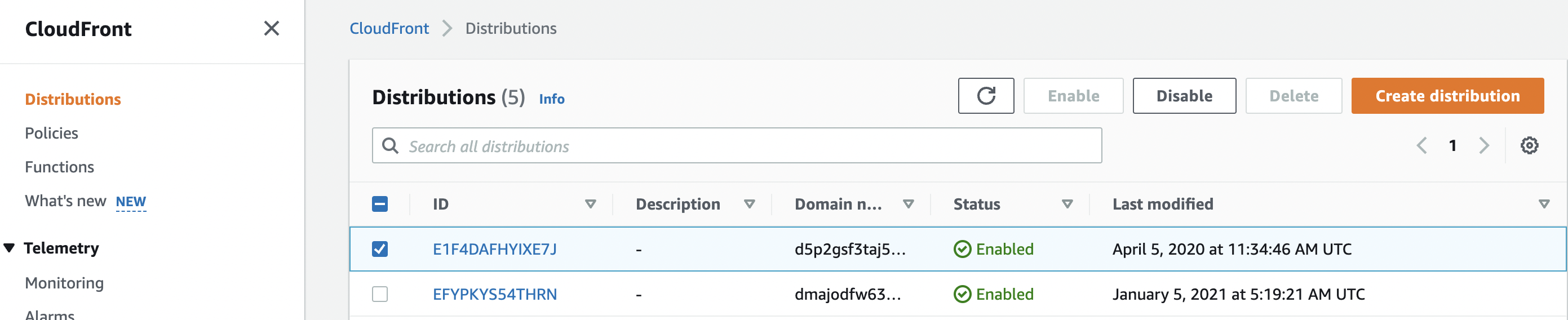
-
Click the “Behaviors” tab, select the “Behavior” which needs to be verified and click “Edit”
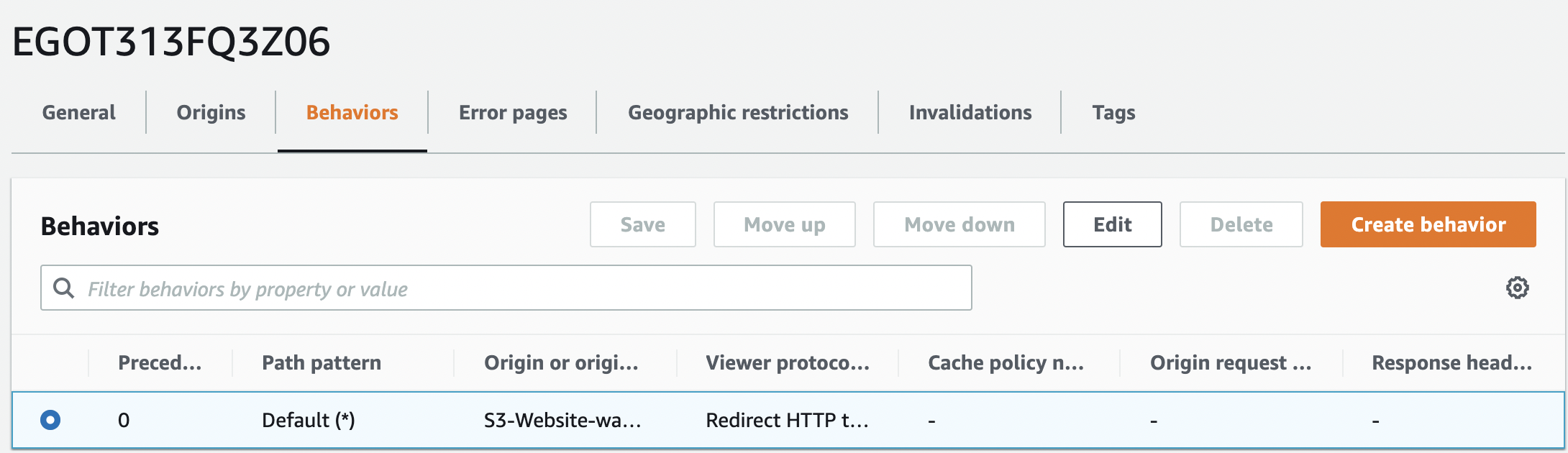
-
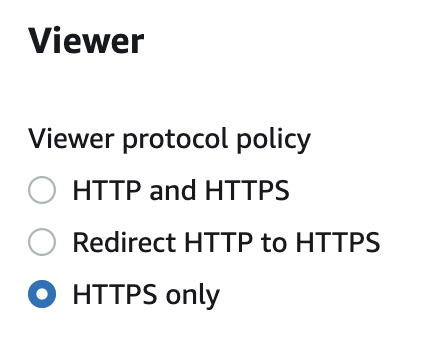
On the Edit Behavior page scroll down to “Viewer” Settings, verify the “Viewer Protocol Policy” and if “HTTP and HTTPS” is selected than CloudFront allows viewers to access your web content using either HTTP or HTTPS.

-
To redirect all HTTP traffic to HTTPS under the “Viewer Protocol Policy” choose “Redirect HTTP to HTTPS” to redirect all HTTP requests to HTTPS.
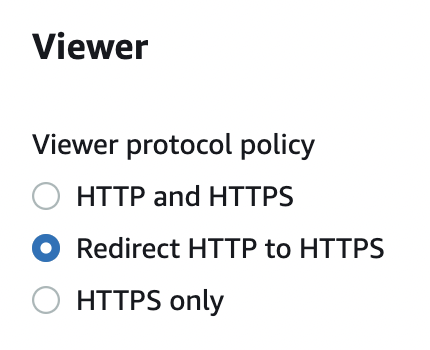
-
If you want to drop all HTTP traffic then under the “Viewer Protocol Policy” choose “HTTPS Only” so CloudFront allows viewers to access your content only if they’re using HTTPS.
-
Repeat steps number 3 to 7 for all other CloudFront Distributions using HTTP-only listeners.