CloudFront distribution uses outdated SSL/TLS protocols.
You should not use outdated/insecure TLS versions for encryption. You should be using TLS v1.2+. Note: that setting minimum_protocol_version = “TLSv1.2_2021” is only possible when cloudfront_default_certificate is false (eg. you are not using the cloudfront.net domain name). If cloudfront_default_certificate is true then the Cloudfront API will only allow setting minimum_protocol_version = “TLSv1”, and setting it to any other value will result in a perpetual diff in your terraform plan’s. The only option when using the cloudfront.net domain name is to ignore this rule.
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Use the most modern TLS/SSL policies available
|
|
-
Log in to the AWS Management Console.
-
Select the “Services” option and search for CloudFront.

-
Select the “CloudFront Distribution” that needs to be verified.
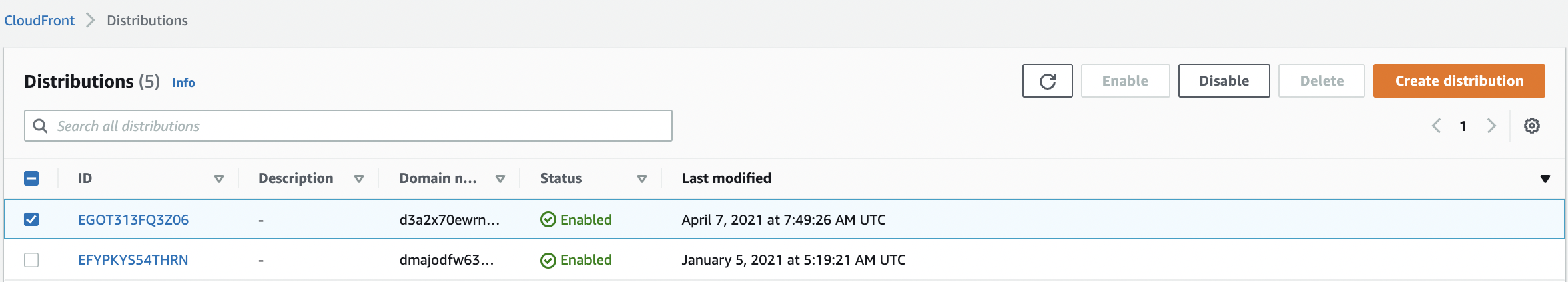
-
Click the “Distribution ID” of the selected Distribution to get into the “CloudFront Distribution” configuration page.
-
In the “General” tab of top menu, scroll to settings and click on the “Edit” button.
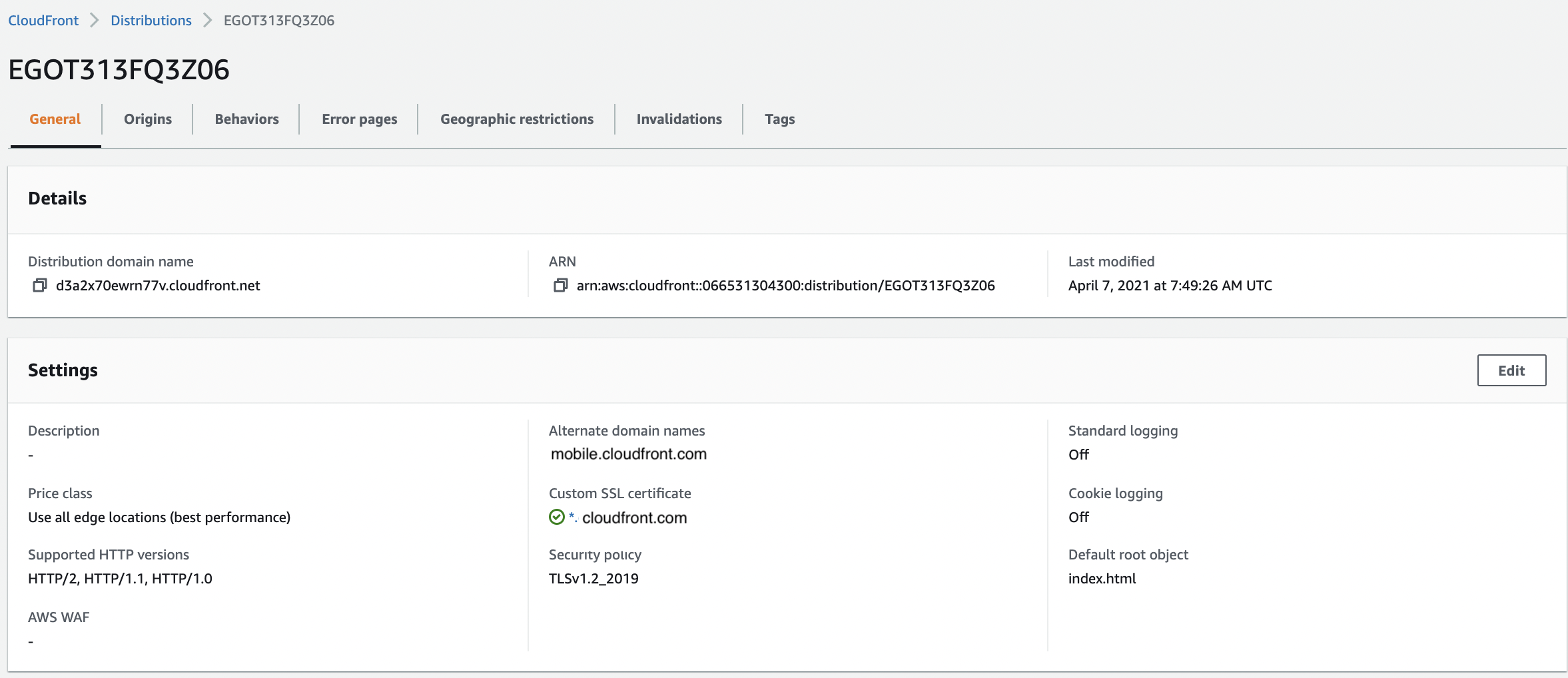
-
On the Edit Settings page, scroll down and choose the “Security Policy” that you want CloudFront to use for HTTPS connections and must use TLSv1.2 “recommended” or higher SSL protocols.
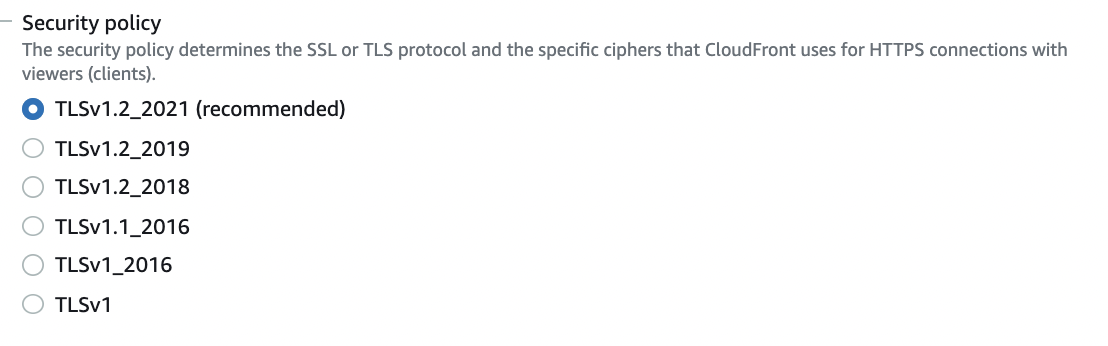
-
Scroll down and click on “Save Changes” to save the settings.

-
Repeat the steps number 3 to 6 to verify whether any other “CloudFront Distribution” is not using an insecure SSL protocol for HTTPS traffic.
Use the most modern TLS/SSL policies available
|
|
|
|