Open SQL Server
Determine if TCP port 1433 or UDP port 1434 for SQL Server is open to the public
While some ports such as HTTP and HTTPS are required to be open to the public to function properly, more sensitive services such as SQL server should be restricted to known IP addresses.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Log in to the AWS Management Console.
Select the “Services” option and search for EC2.
Scroll down the left navigation panel and choose “Security Group” under “Network & Security”.

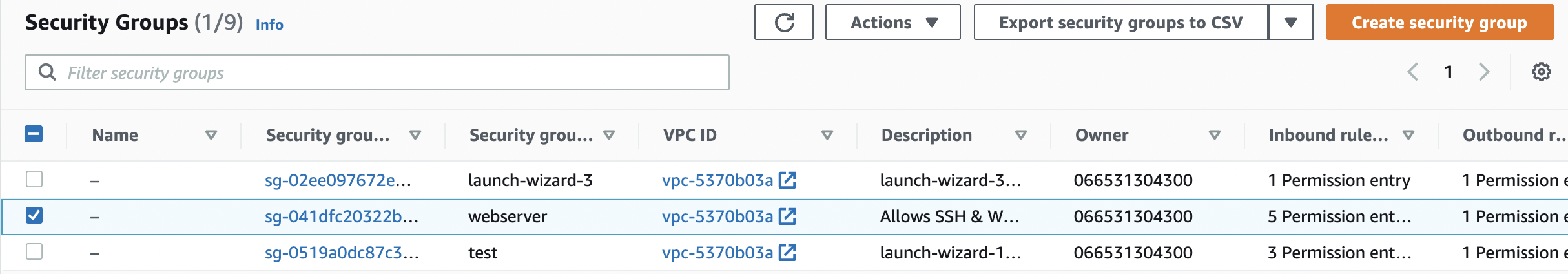
Select the “EC2 Security Group” that needs to be verified.
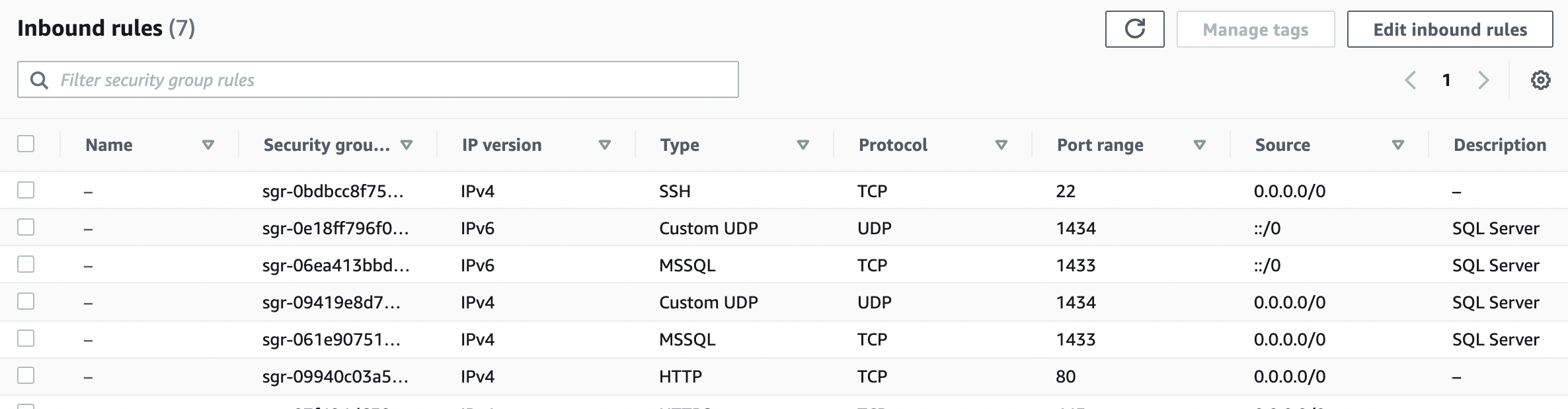
Scroll down the bottom panel and choose “Inbound rules”. Verify the value for “Source” column for “Custom UDP” or “MSSQL” for ports 1434 and 1433 under “Type” and if any rule have value set to “0.0.0.0/0” or “::/0 " then the selected “Security Group” has “UDP/TCP” port for “SQL Server” open to the public.
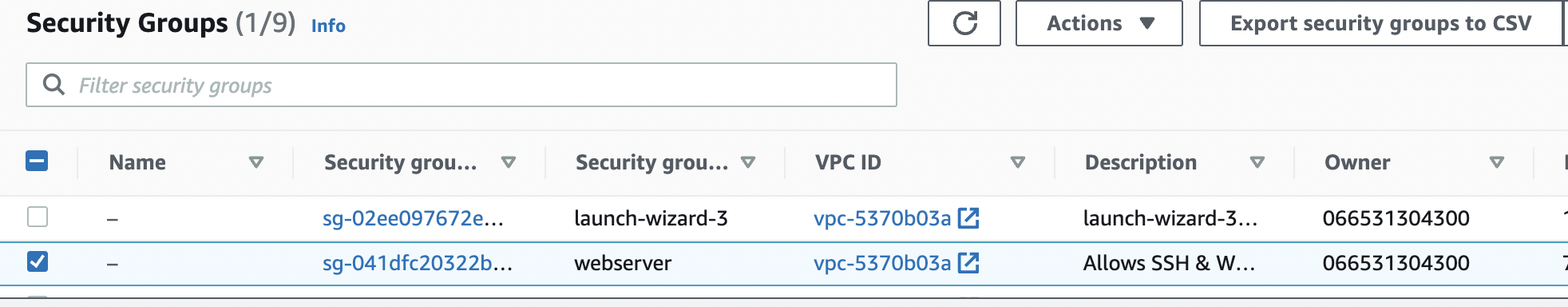
Repeat step number 2 - 5 to verify other “Security Groups” in the selected AWS region.
Navigate to “Security Groups” under “Network & Security” and select the “Security Group” that needs to be modified to restrict the access of “UDP/TCP” port 1434 and 1433 for “SQL Server” to specific ip address.
Scroll down the page and select the “Inbound rules” and click on the “Edit Inbound rules” button to the right.
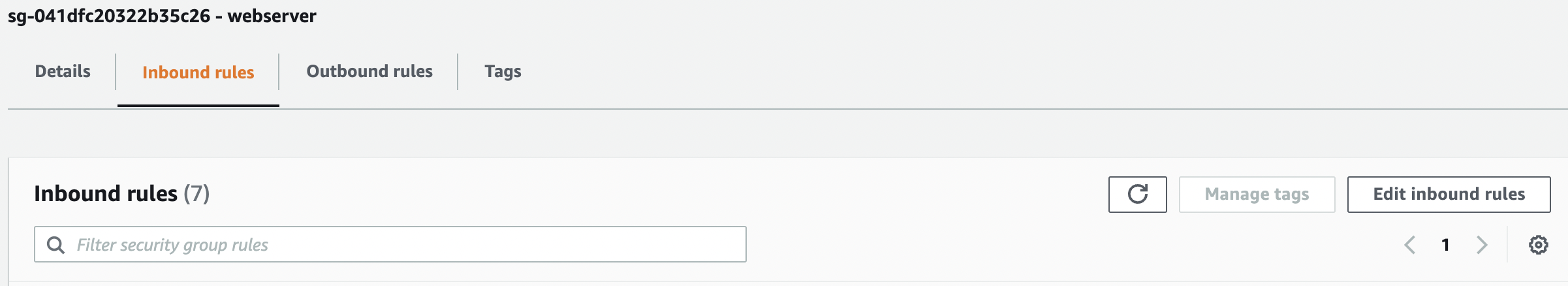
In the “Edit inbound rules” tab select either the “MyIP” or “Custom” from the “Source” column.
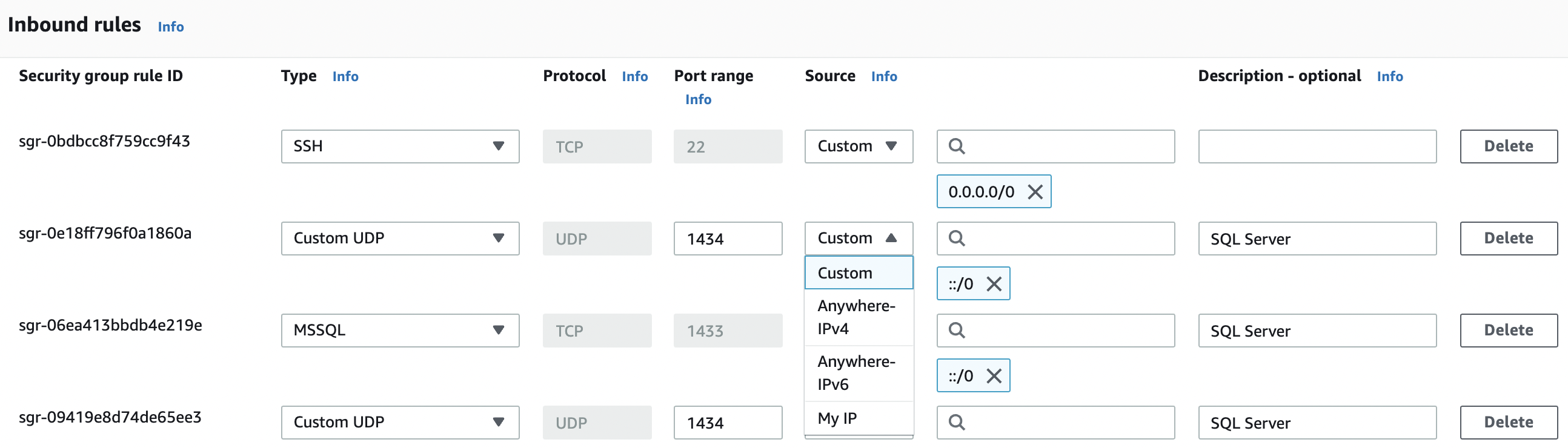
In the “Edit inbound rules” tab select the “MyIP” from the “Source” column to allow “SQL” inbound traffic only from your IP address.
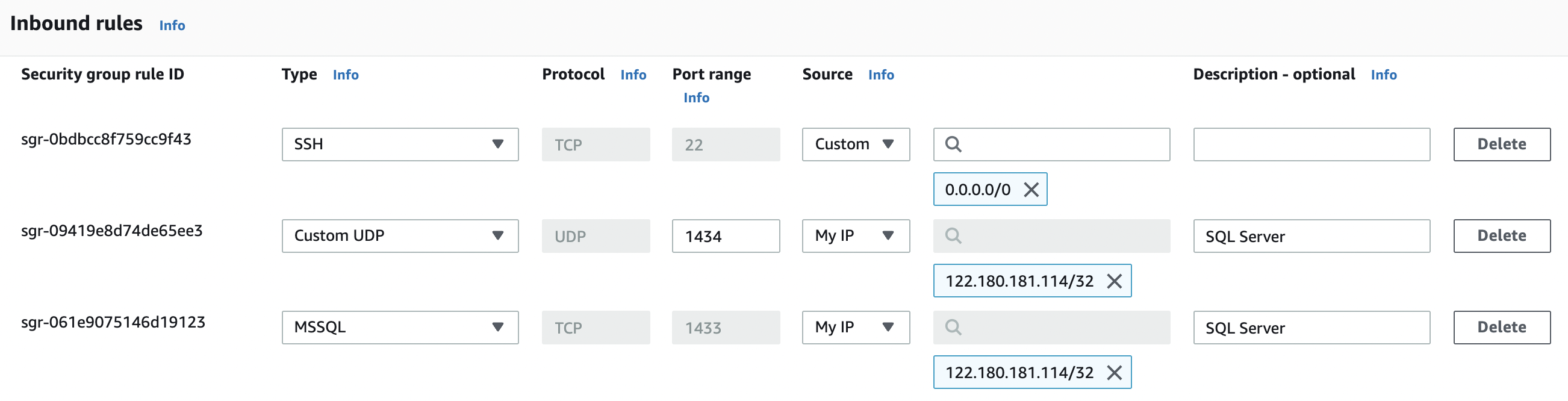
In the “Edit inbound rules” tab select the “Custom” from the “Source” column as per the requirements for “SQL” and specify static IP/Elastic IP address along with “Description” for the “Security Group” rule.
Click on the “Save rules” button to make the necessary changes.
Repeat step number 7 - 12 to restrict UDP port 1434 and TCP port 1433 for “SQL Server” to known IP address.