IAM Role Last Used
Ensures IAM roles that have not been used within the given time frame are deleted.
IAM roles that have not been used for a long period may contain old access policies that could allow unintended access to resources if accidentally attached to new services. These roles should be deleted.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Log in to the AWS Management Console.
Select the “Services” option and search for IAM.
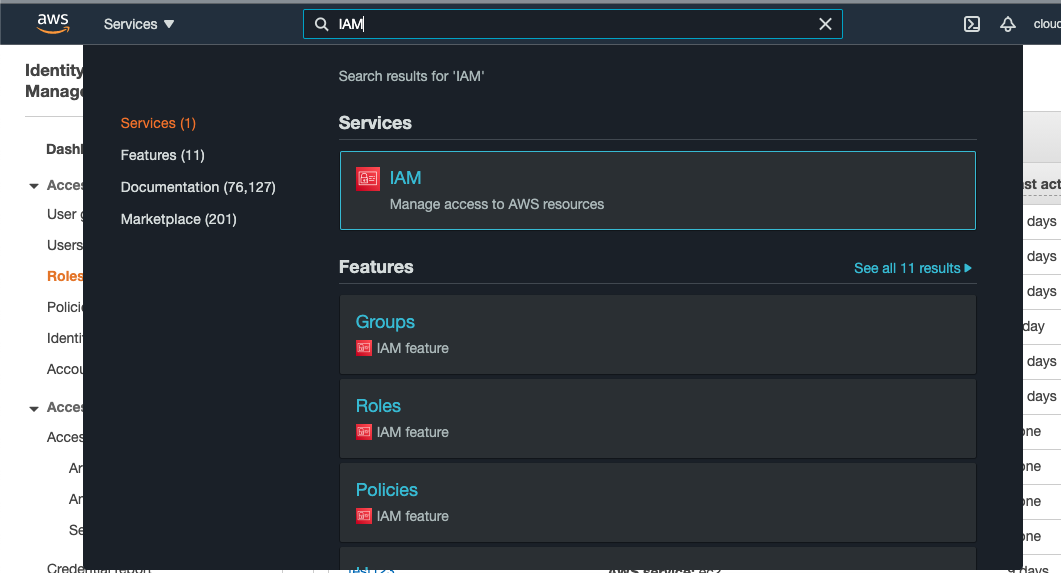
Scroll down the left navigation panel and choose “Roles”.
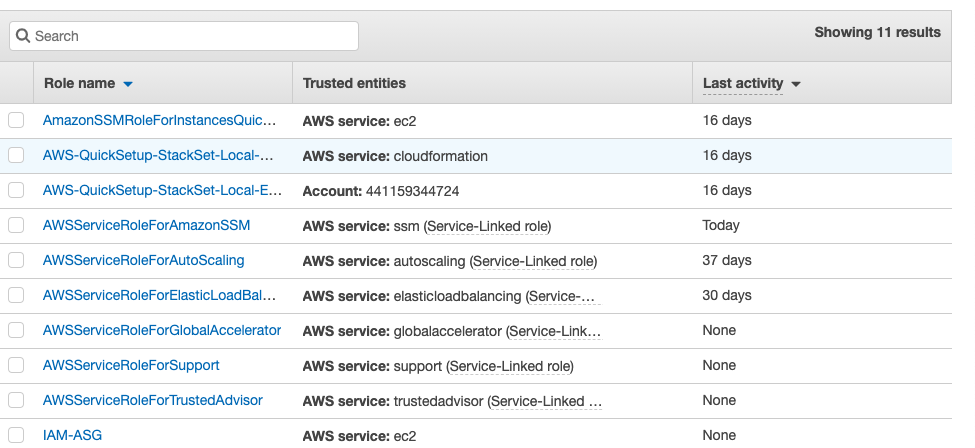
On the “Roles” page, scroll down and check the “Last Activity” column to verify when the IAM Roles are last used.
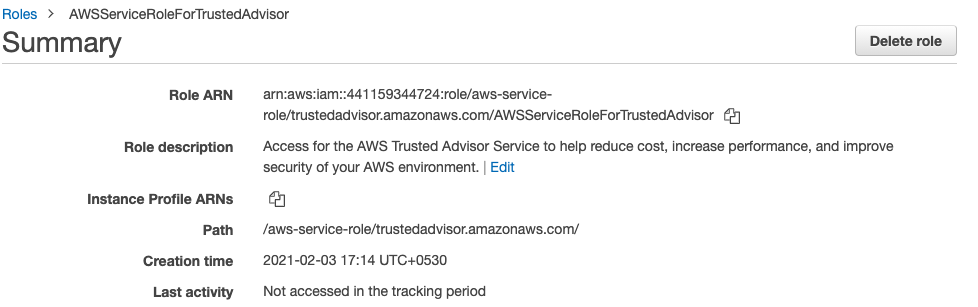
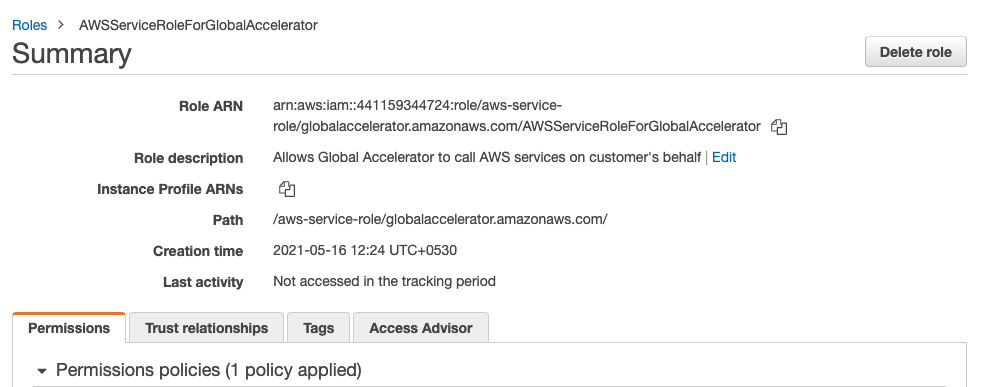
For any Roles with the attribute “None” in the “Last Activity”, click on the Role and check the Creation time.
Repeat steps 2 - 4 to verify IAM Roles in other AWS account.
Navigate to IAM dashboard at https://console.aws.amazon.com/iam/.
In the “IAM dashboard”, click on the “Roles” option at the left navigation panel.
Select the roles whose “Last Activity” is greater then 90 days or whose Creation time is greater then 90 days but showing None in Last Activity.
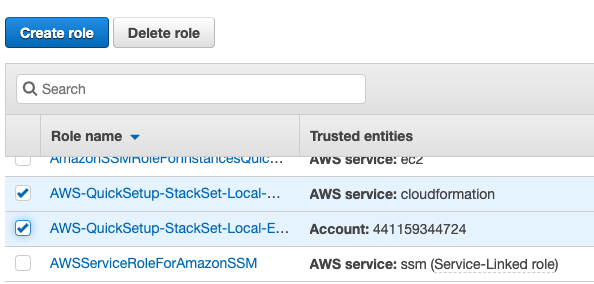
Click on the “Delete” option at the top to remove the selected IAM roles.
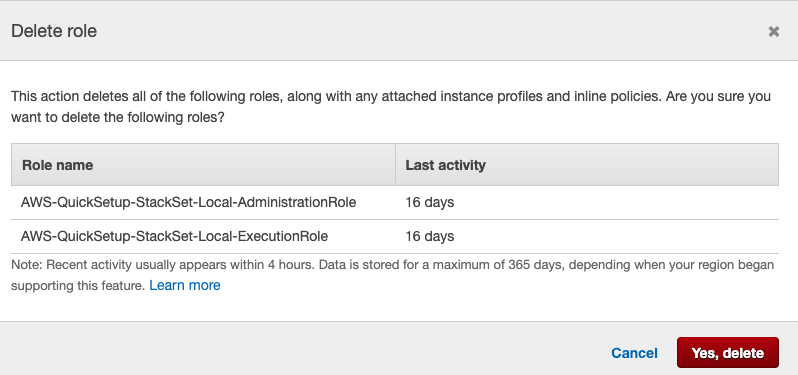
On the “Delete role” tab, click on the “Yes, delete” button to make the changes.
Repeat steps number 7 - 11 to delete IAM roles that have not been used within the expected time frame.