Users Password Last Used
Detects users with password logins that have not been used
Having numerous, unused user accounts extends the attack surface.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Log in to the AWS Management Console.
Select the “Services” option and search for IAM.
Scroll down the left navigation panel and choose “Credential report”. Click on the “Download Report” button to download a report that lists all your account’s users and the status of their various credentials.
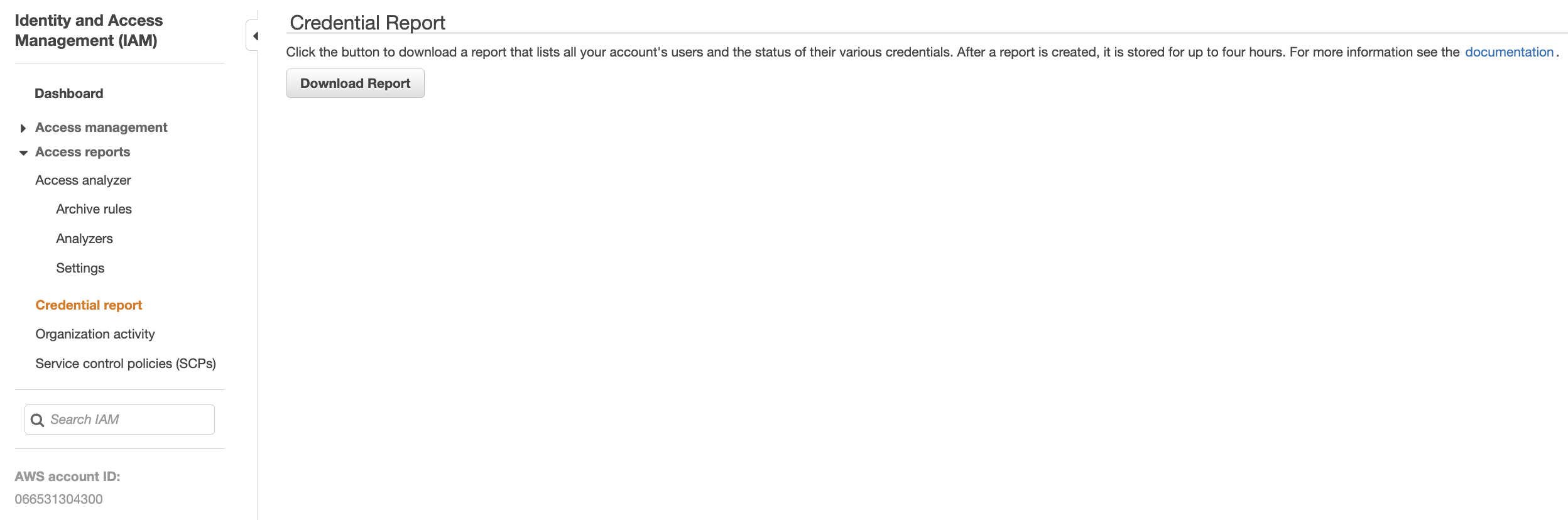
Open the downloaded credentials report and check the “password_last_used_date” column for each IAM account. If the timestamp value for “password_last_used_date” is recorded within the last 7 days, the above credentials have been used to access the AWS account. If however, the timestamp value is older than 90 days, then the account should be deleted or disabled.
Scroll down the left navigation panel and choose “Users”.
Select the “User” that needs to be verified and click on the “User name” to access the selected IAM User.
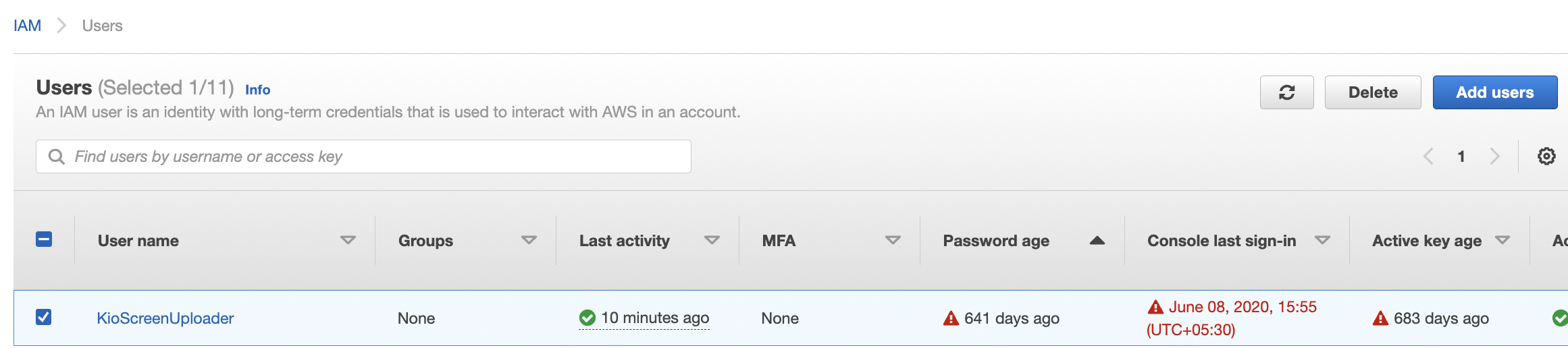
Click on the “Security Credentials” tab under the configuration page.
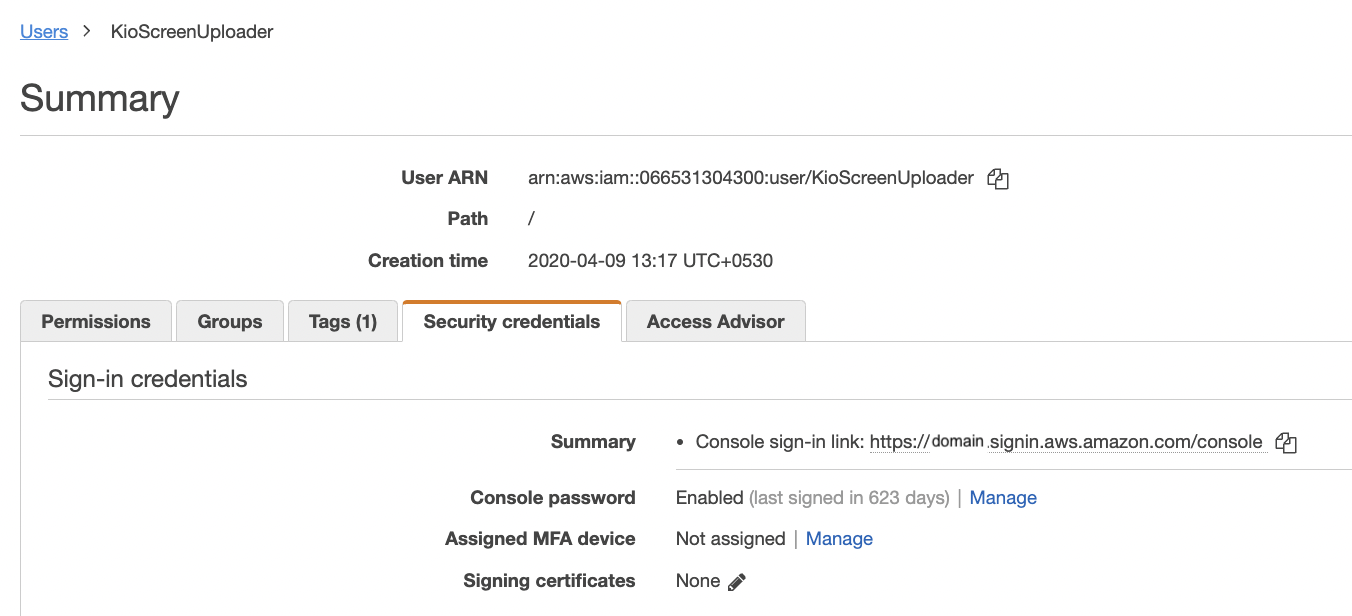
Under the “Security Credentials” tab check the “Console password” section for status “Enabled/Disabled”. If the status is “Enabled” then the console sign in is enabled and needs to be disabled.
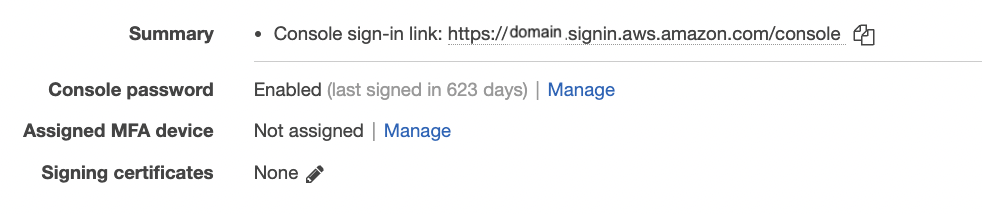
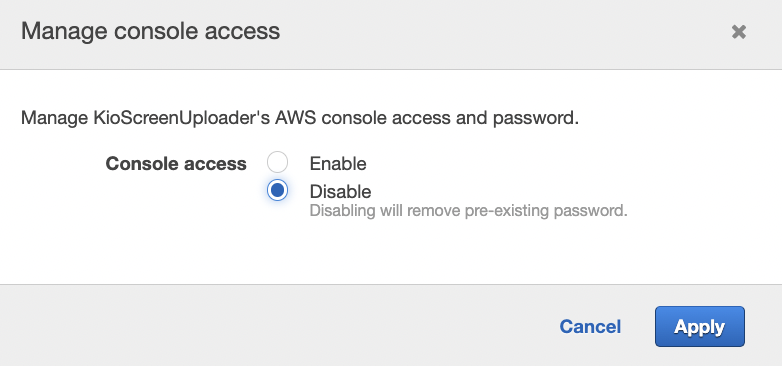
Click on “Manage” to open “Manage console acess” pop up.
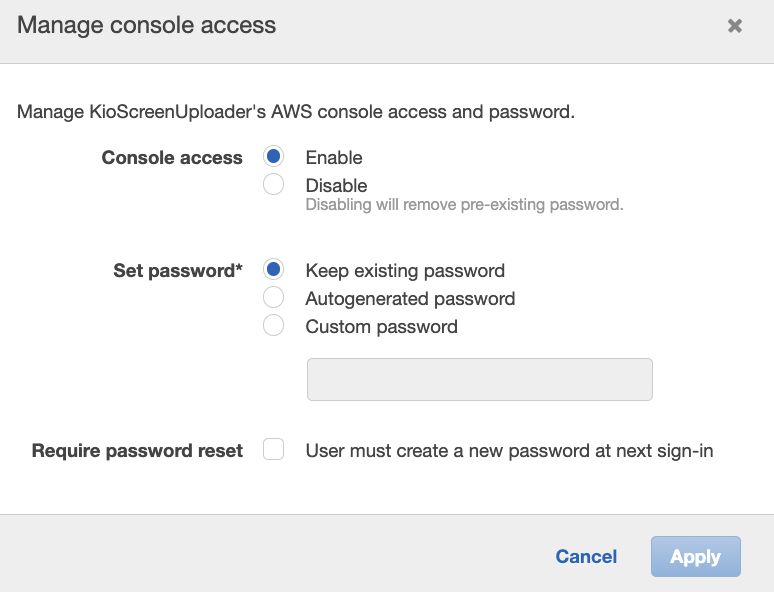
Select “Disable” for the Console access and click on “Apply” button.
Repeat step number 2 - 11 to verify for other IAM users.