SSM Encrypted Parameters
Ensures SSM Parameters are encrypted
SSM Parameters should be encrypted. This allows their values to be used by approved systems, while restricting access to other users of the account.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the AWS Management Console.
-
Select the “Services” option and search for SSM.
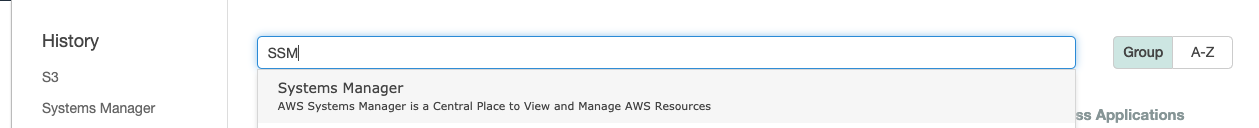
-
Scroll down the left navigation panel and choose “Parameters” under “Shared Resources”.
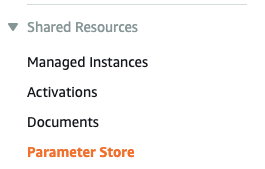
-
Select the “SSM Parameter” that needs to be verified and click on its name from the “Name” column.
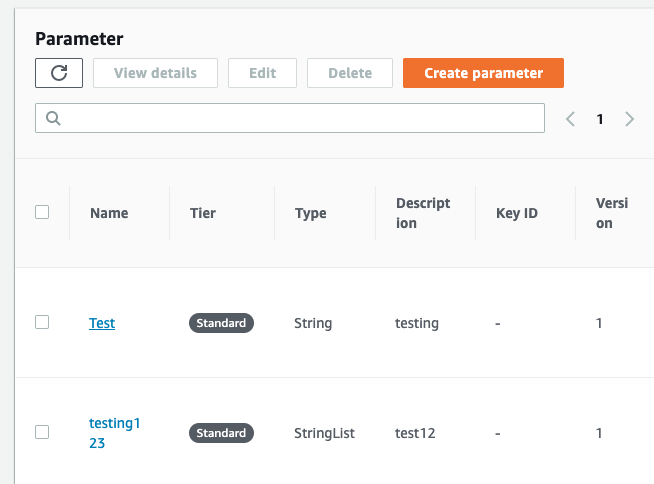
-
Scroll down the “Parameter Store” configuration page and if the selected “Parameter” holds important information such as passwords, security tokens as values under “Value” attribute and “Type” are showing as “String” then the selected SSM parameter is not encrypted.
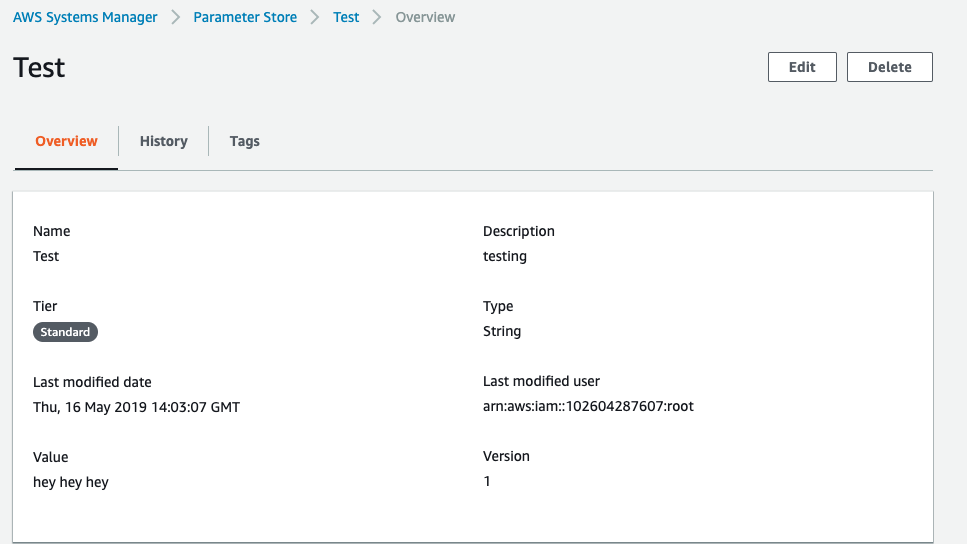
-
Repeat steps number 2 - 5 to verify other “SSM Parameters”.
-
Select the unencrypted “SSM Parameter” that needs to be re-created and click on its name from “Name” column and copy the values set for the “Name”, “Description” and “Value attributes” in another location.
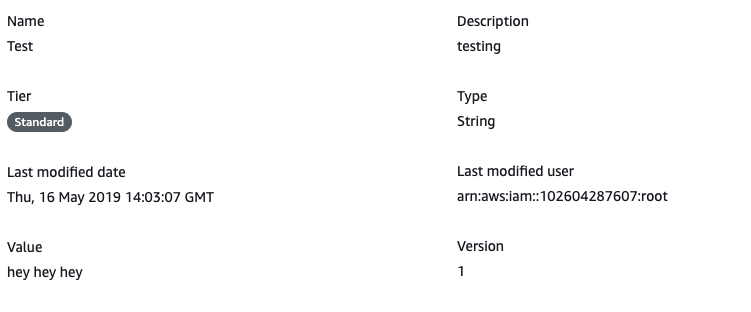
-
Click on the Parameter Store and delete the unencrypted “SSM Parameter” by clicking on “Delete” button at the top panel.
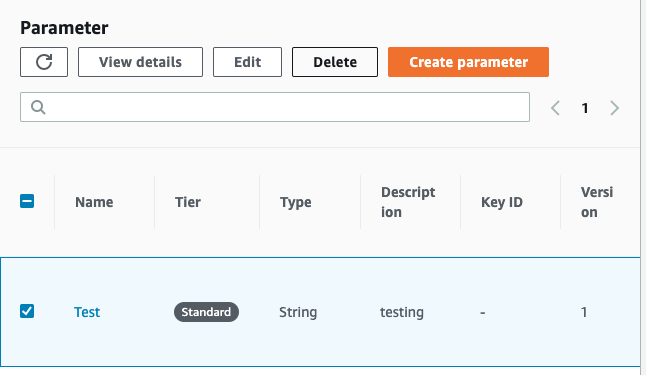
-
Click on the “Create parameter” button at the top panel.
-
Copy the value set for the “Name”, “Description” and “Value attributes” from the location where we copied earlier.
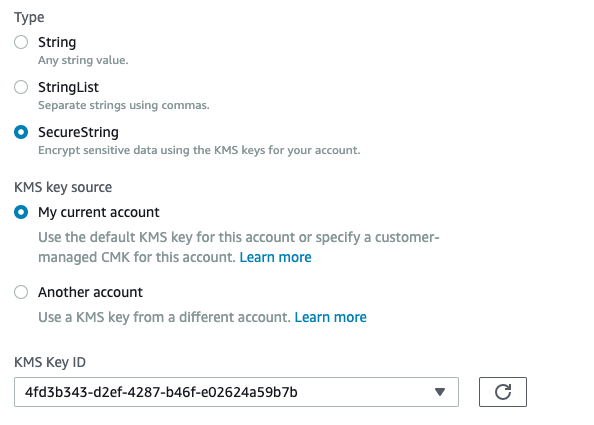
-
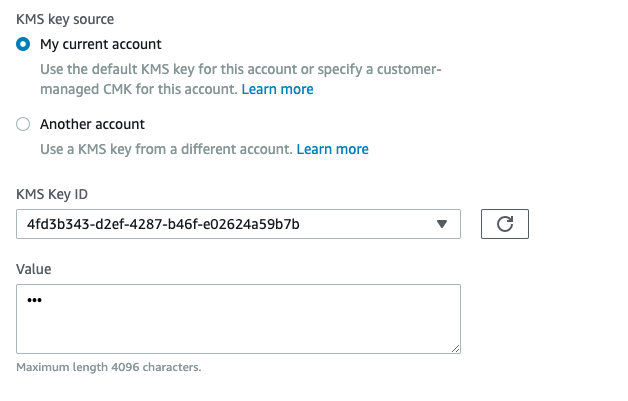
Choose “SecureString” under “Type” and choose whether to use “KMS key” from current account or from another account and choose the “KMS Key ID” from dropdown menu accordingly and provide the “Value” which needs to be encrypted.
-
Scroll down and click on the “Create parameter” button.
-
Repeat the steps number 6 - 12 to recreate unencrypted “SSM Parameters” with “Type” set to “SecureString”.