High Severity Alerts Enabled
Ensures that high severity alerts are enabled and properly configured.
Enabling high severity alerts ensures that microsoft alerts for potential security issues are sent and allows for quick mitigation of the associated risks.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Log in to the Microsoft Azure Management Console.
Select the “Search resources, services, and docs” option at the top and search for “Microsoft Defender for Cloud”.
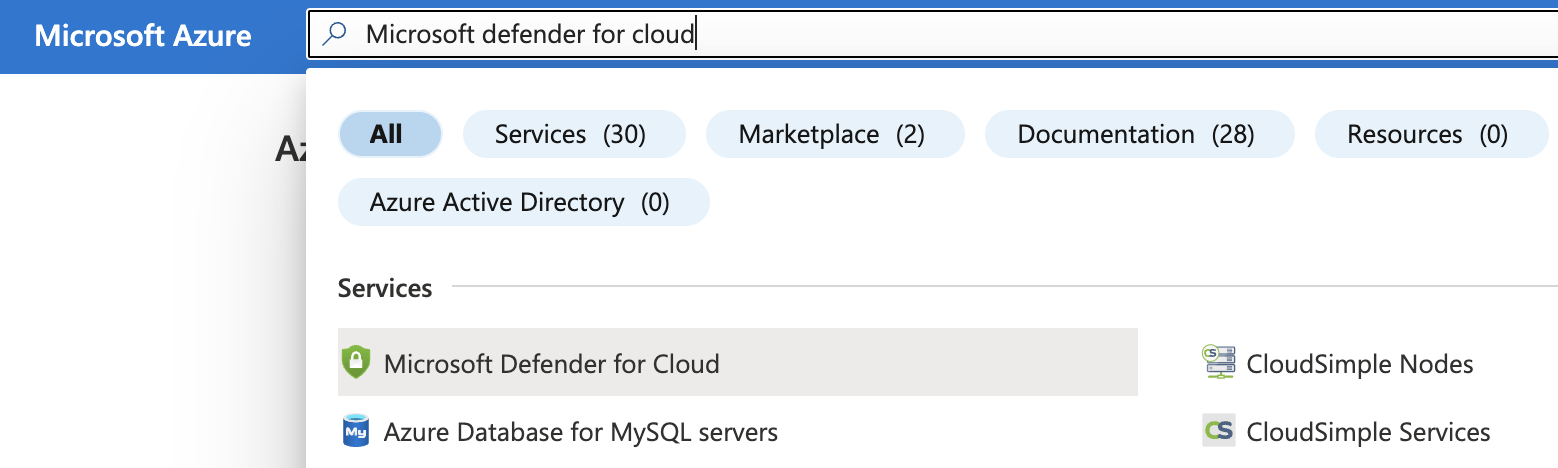
On the “Microsoft Defender for Cloud” page, scroll down the left navigation panel and choose “Environment Settings”.
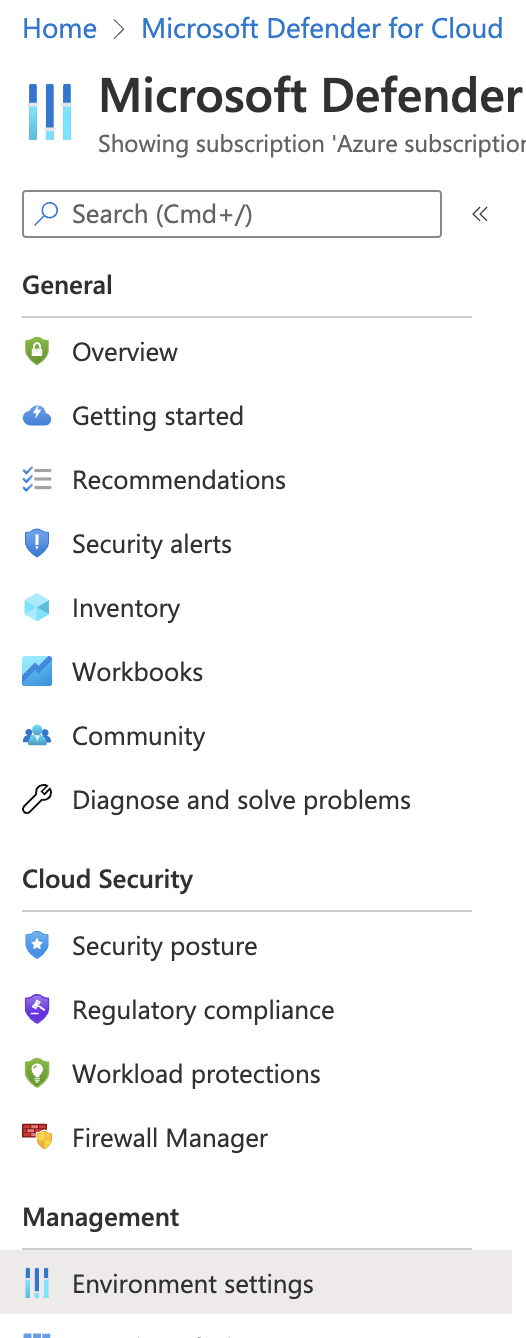
On the “Environment Settings” page, select the “Subscription” by clicking on the “Name”.
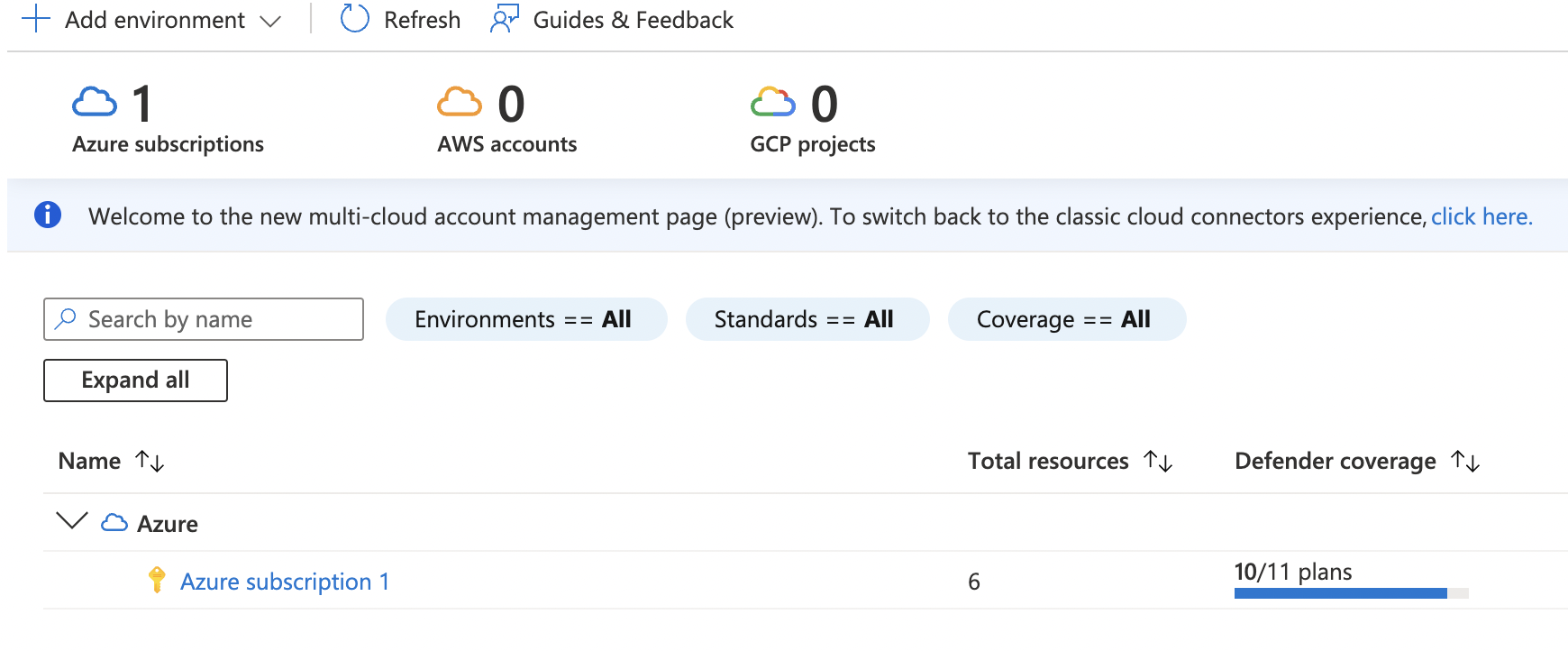
Under the “Settings | Defender plans " page, click on the “Email Notifications”.
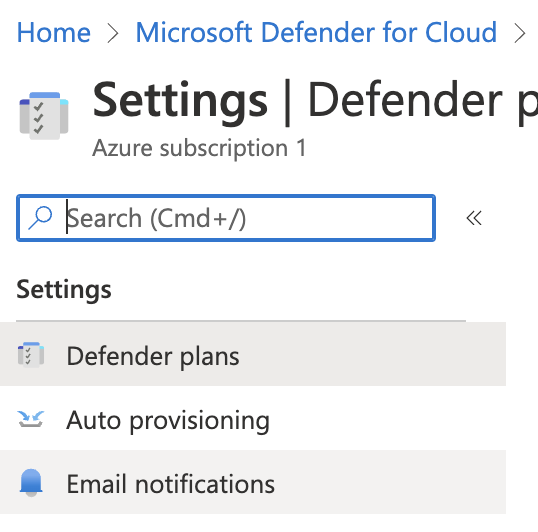
On the “Settings | Email notifications” page under “Email recipients” if the “Additional email addresses (separated by commas)” is empty and only “owner” is selected in “All users with the following roles” then high severity alerts are not configured to be sent to the admins.
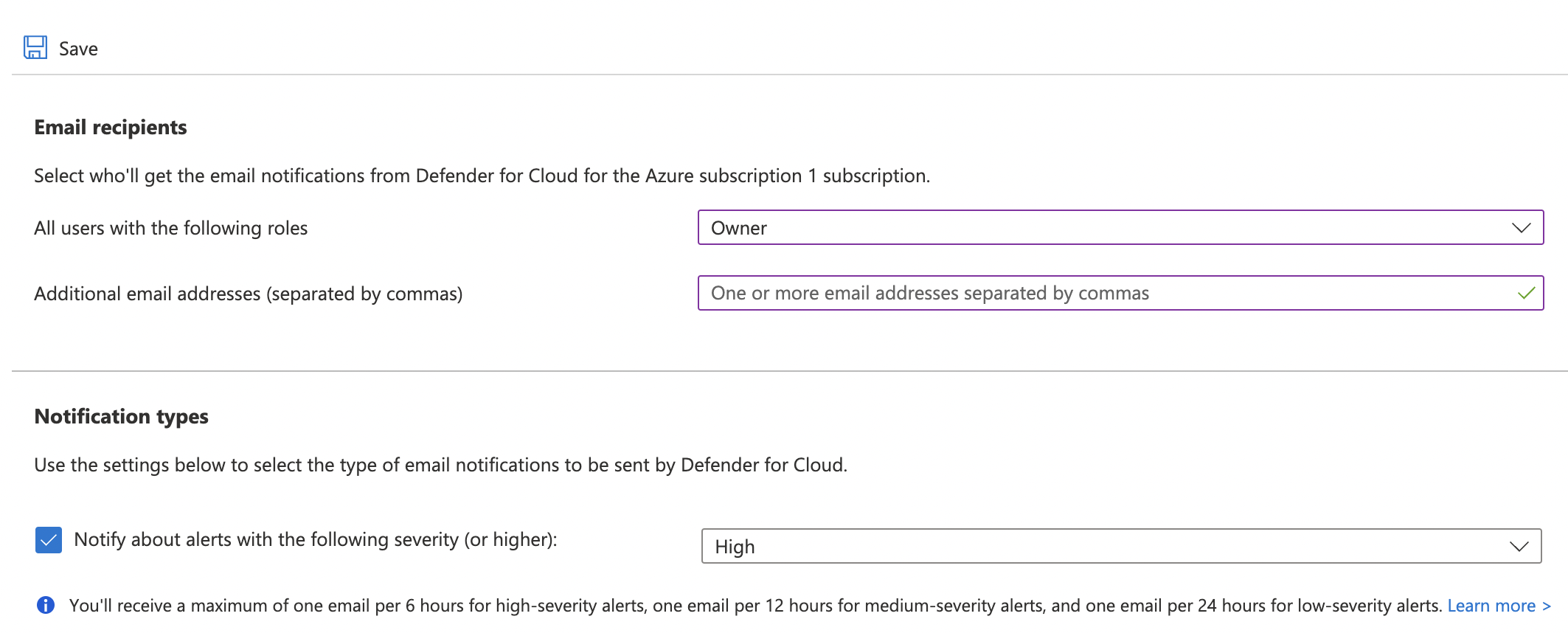
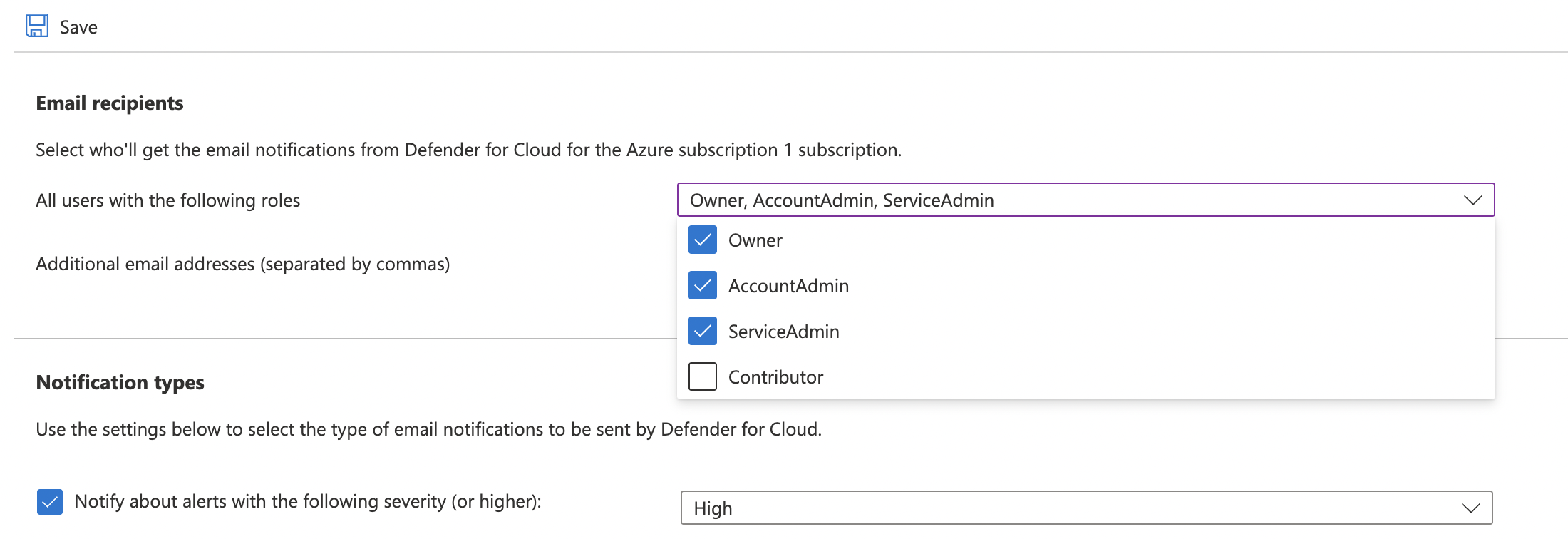
Under “Email recipients”, click the dropdown for “All users with the following roles” and check mark “AccountAdmin and “ServiceAdmin” along with owner and enter one or more than one “Email addresses” separated by “comma in section “Additional email addresses (separated by commas)”.
Under “Notification types” select “High” from the dropdown next to “Notify about alerts with the following severity (or higher). Click on the “Save” button to make the changes.
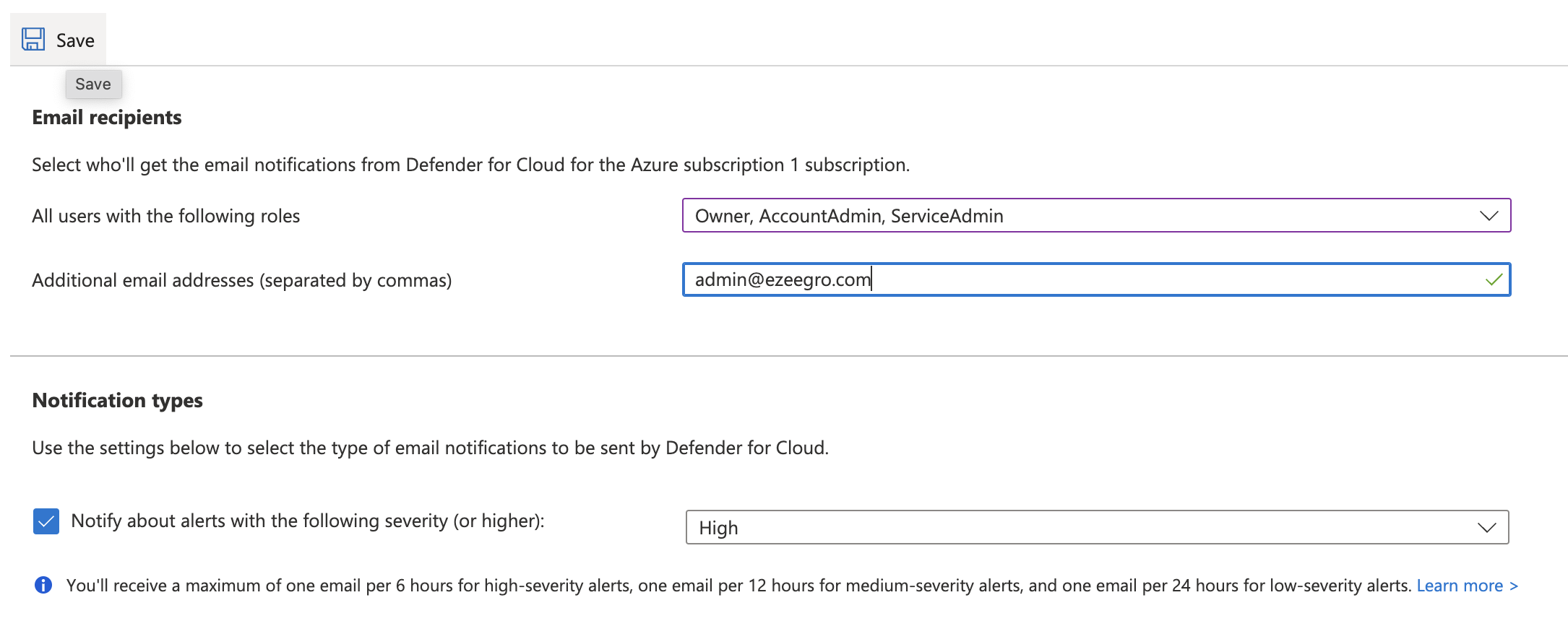
Repeat step number 3 - 8 to ensure that high severity alerts are configured to be sent to subscription owners.