Monitor Next Generation Firewall
Ensures that Next Generation Firewall (NGFW) Monitoring is enabled in Microsoft Defender.
When this setting is enabled, Microsoft Defender for Cloud will search for deployments where a NGFW is recommended.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Log in to the Microsoft Azure Management Console.
Select the “Search resources, services, and docs” option at the top and search for “Policy” and select the “Policy”.
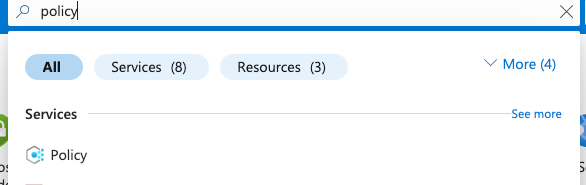
Scroll down the left navigation panel and select “Compliance”.
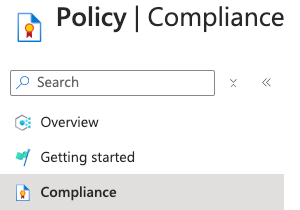
On the “Policy | Compliance” page, under “Name” column select compliance for the “Scope” of necessary Subscription.
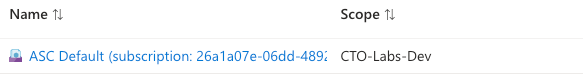
On the “Policy| Compliance” page select the “View Assignment” Tab on the top.
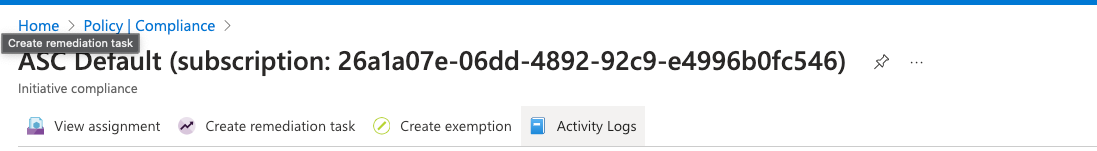
On the “Policy| Compliance | Subscription” page, Select the “Edit Assignment” Tab at the top.
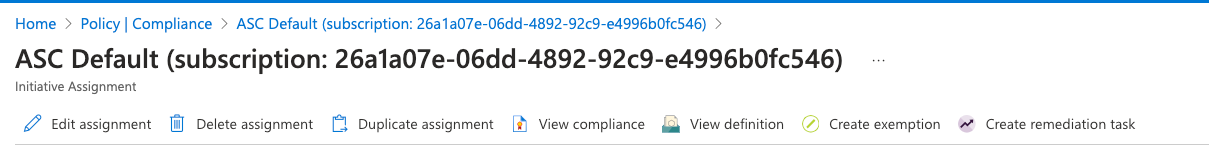
On the Assign Initiative page, select the “Parameters” tab and uncheck “Only show parameters that need input or review”. It will show you a list of parameters.
In the list search for the setting “All Internet traffic should be routed via your deployed Azure Firewall”. If it’s set to “Disabled” then “Next Generation Firewall Monitoring” is not enabled on the selected “Subscription”.
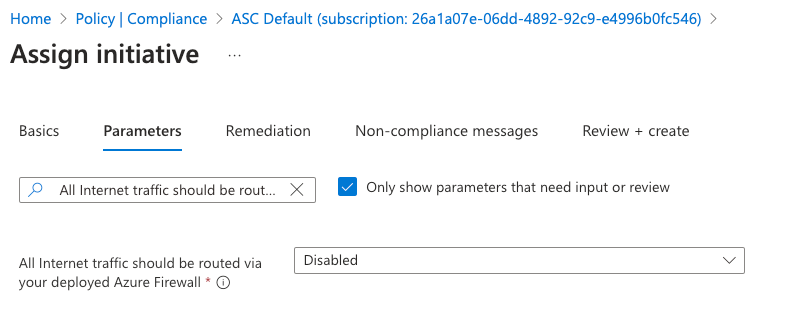
To enable “Next Generation Firewall Monitoring” click to open the dropdown of “All Internet traffic should be routed via your deployed Azure Firewall” and select the “AuditIfNotExists” option.
Click on the “Review + save” button to make the necessary changes.
Repeat steps number 3 - 10 to ensure “Next Generation Firewall Monitoring” is configured from the Azure Defender.