NSG Log Analytics Enabled
Ensures Network Security Group logs are sent to the Log Analytics workspace
Enabling Log Analytics for Network Security Groups ensures that logs are shipped to a central repository that can be queried and audited.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Microsoft Azure Management Console.
-
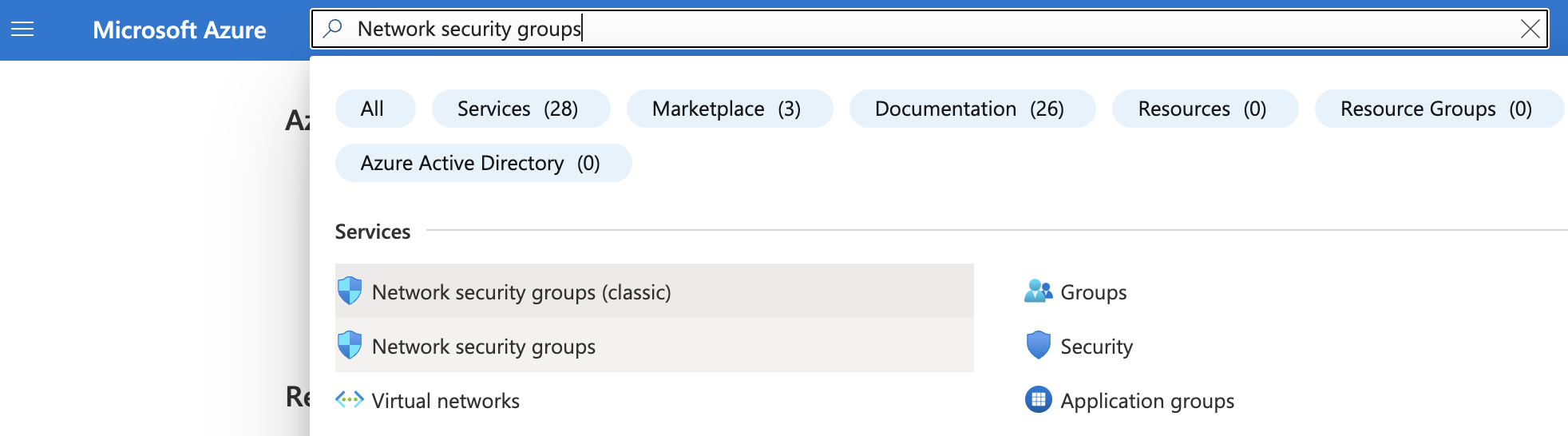
Select the “Search resources, services, and docs” option at the top and search for “Network security groups”.
-
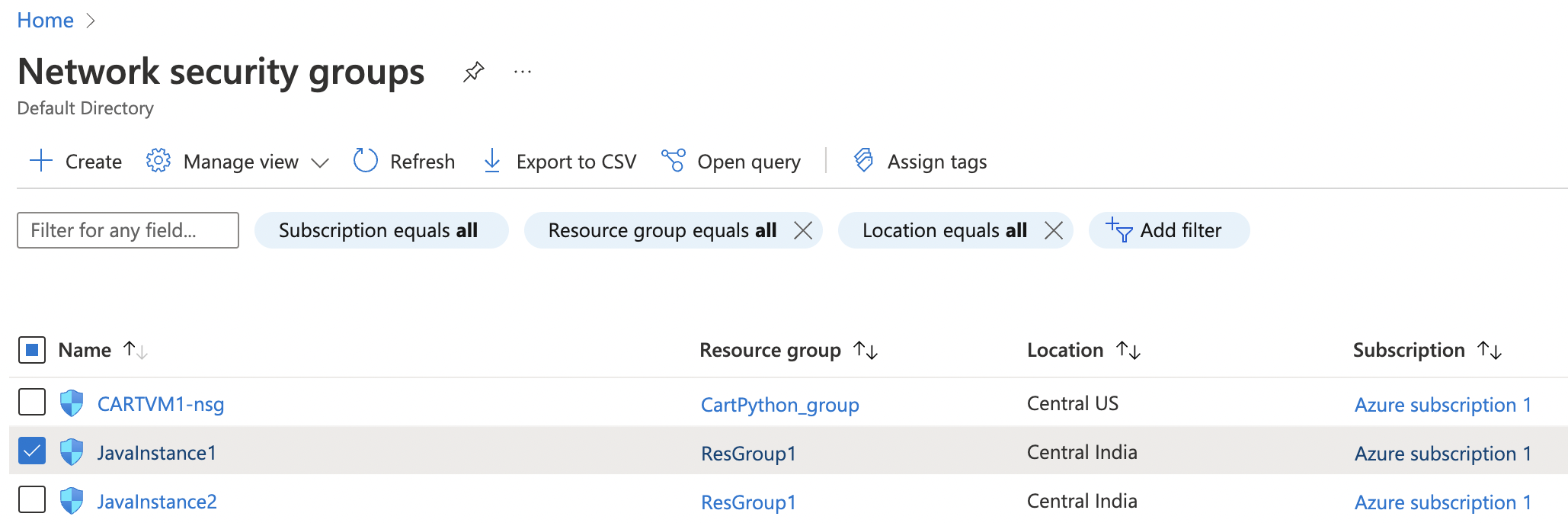
Select the “Network Security Group” which needs to be verified.
-
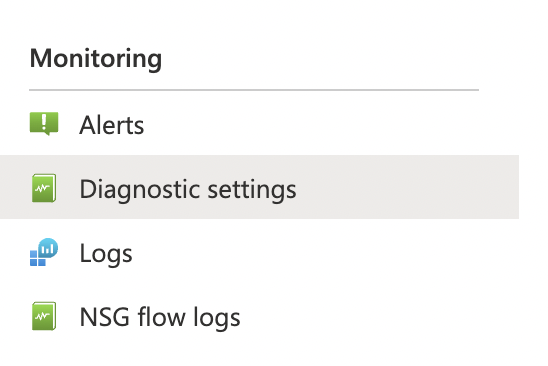
On the “Network security groups” page, scroll down the left navigation panel and choose “Diagnostics Settings” under “Monitoring”.
-
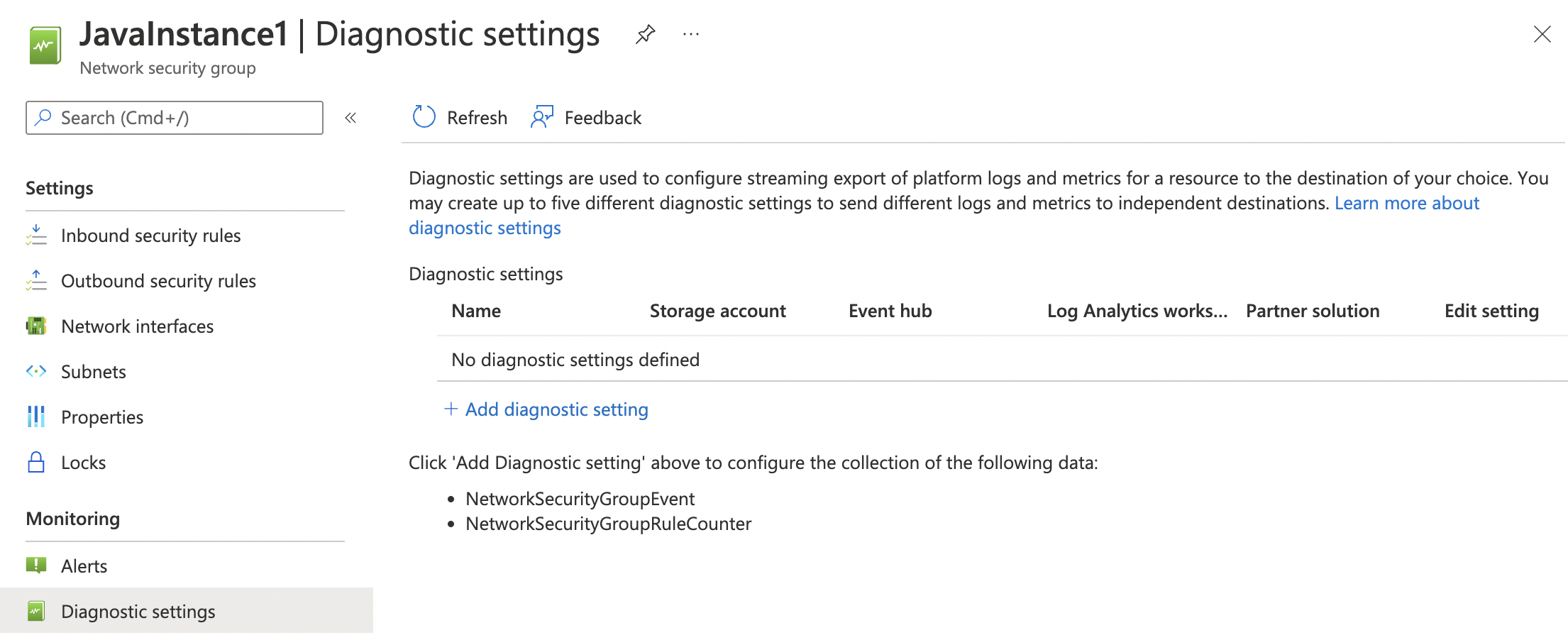
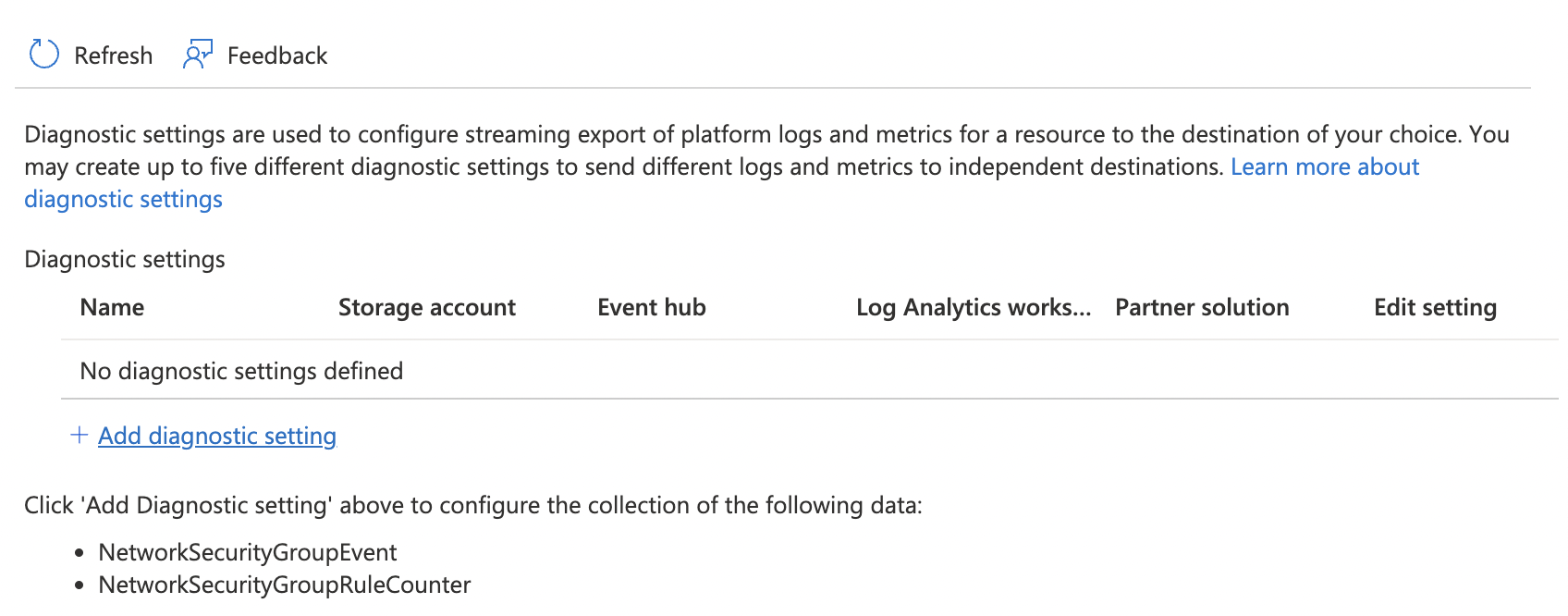
On the “Network security groups - Diagnostic Setting” page if “No diagnostic settings defined” is showing for the selected “Network Security Group” then logs are not being sent to the Log Analytics workspace.
-
To enable sending of logs to Log Analytics for each Network Security Group, on the “Diagnostic settings” page click on the “Add diagnostic setting” option.
-
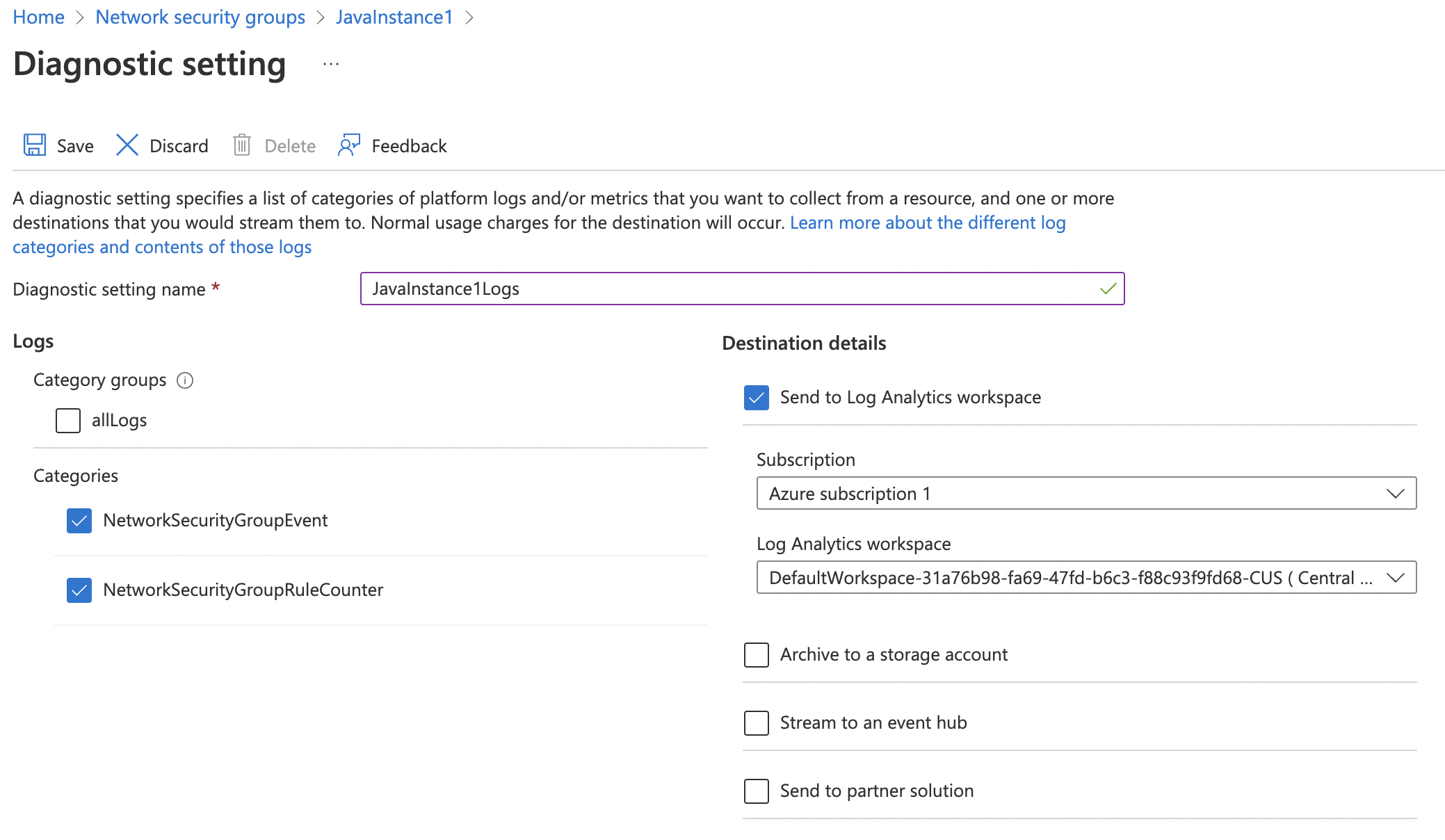
On the “Diagnostics Settings” page enter the “Diagnostic setting name”, click the checkbox for “Send to Log Analytics workspace”, select the “Subscription” and an existing Log Analytics workspace, or create a workspace. Under “Logs” select categories “NetworkSecurityGroupEvent” and “NetworkSecurityGroupRuleCounter”.
-
Click on the “Save” button at the top to make the necessary changes.
-
Repeat steps number 7 - 9 to enable sending of logs to Log Analytics for each Network Security Group resource in the Azure Monitor.