Send Alerts Enabled
Ensures that send alerts is enabled in advanced data security for SQL servers.
Enabling send alerts in advanced data security on all SQL servers ensures that monitored data for unusual activity, vulnerabilities, and threats get sent to the email addresses configured in advanced data protections.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Log in to the Microsoft Azure Management Console.
Select the “Search resources, services, and docs” option at the top and search for “SQL servers”.
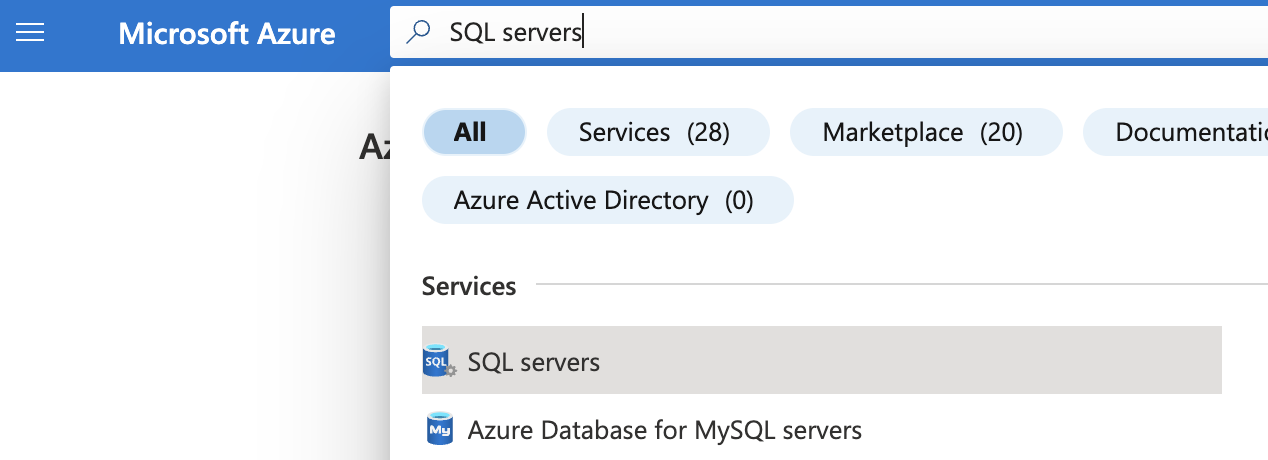
On the “SQL server” page, select the SQL server that needs to be examined.
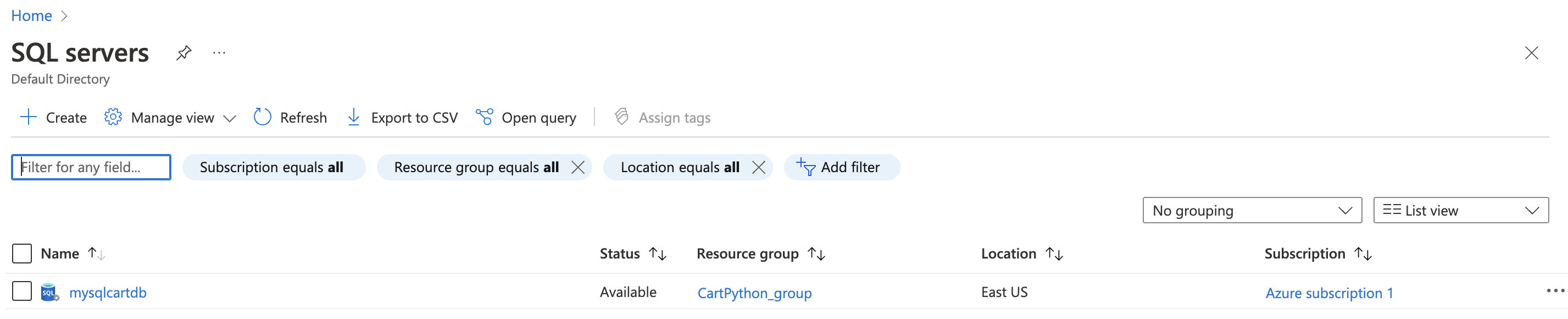
On the selected “SQL server” page, scroll down the left navigation panel and select “Microsoft defender for cloud” under “Security”.

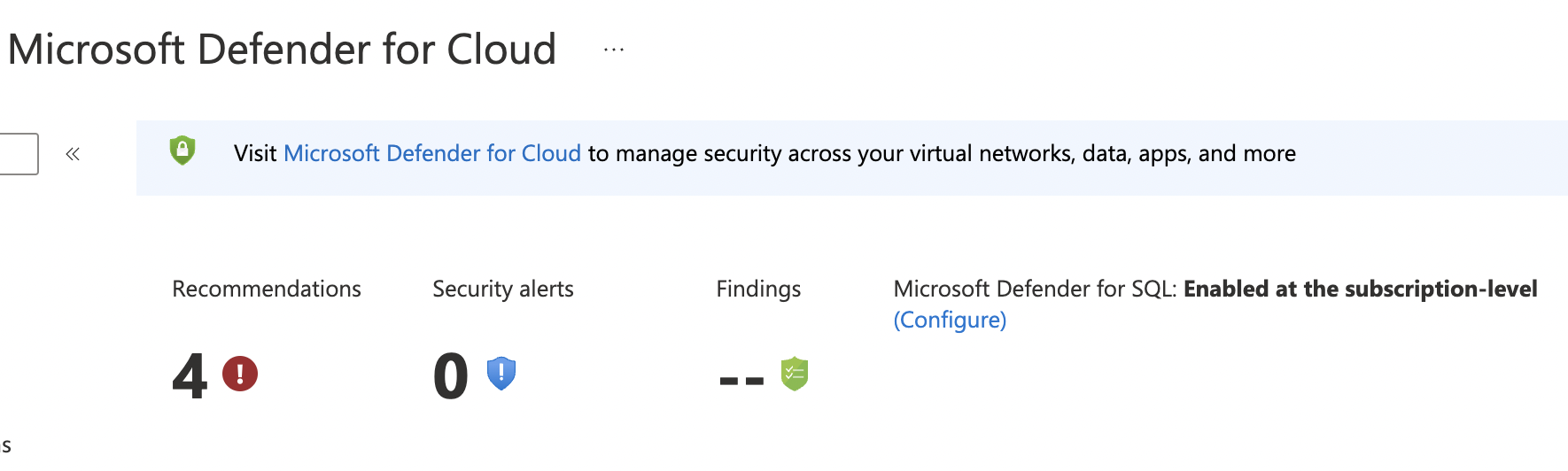
On the “Microsoft defender for cloud” page, click on “Configure” next to “Microsoft Defender for SQL”.
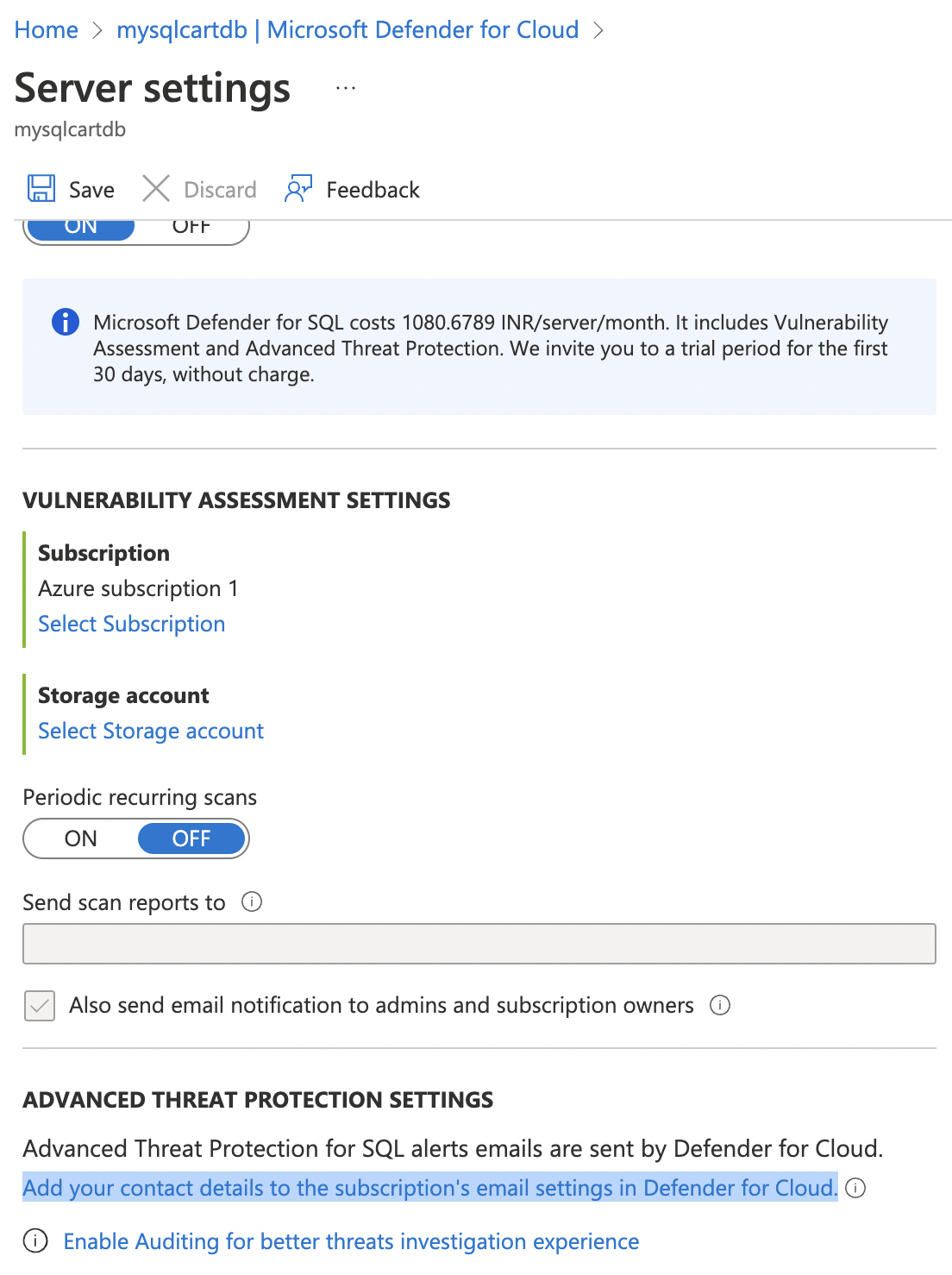
On the “Server settings” page, scroll down to “ADVANCED THREAT PROTECTION SETTINGS” and click on “Add your contact details to the subscription’s email settings in Defender for Cloud”.
On the “Email notifications” page if there is no email address configured and no roles are selected then send alerts are not enabled.
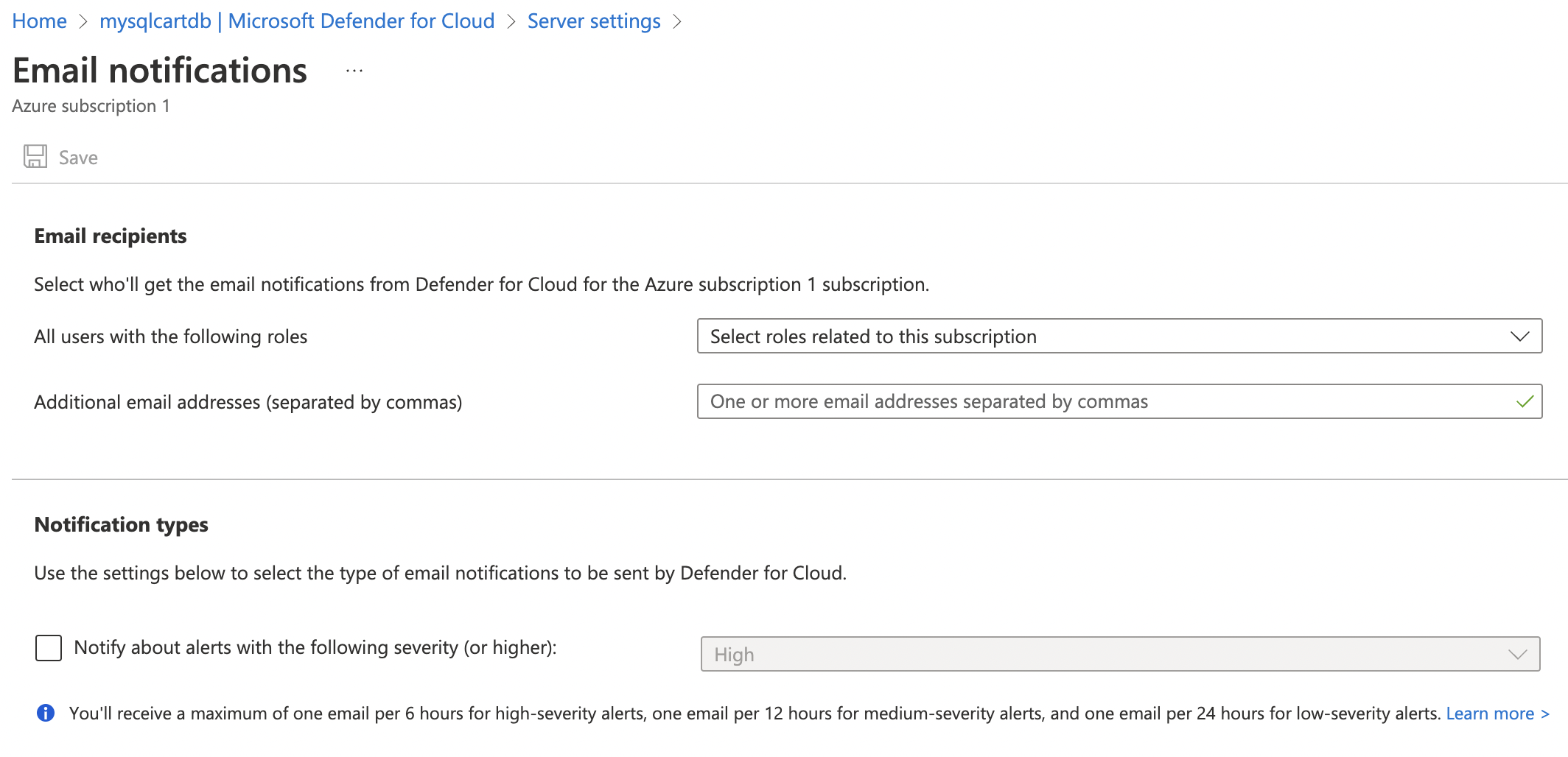
To enable send alerts, under “Email receipients” select “Owner”, “AccountAdmin”. ServiceAdmin" from the dropdown and assign an email for “Additional emal addresses”.
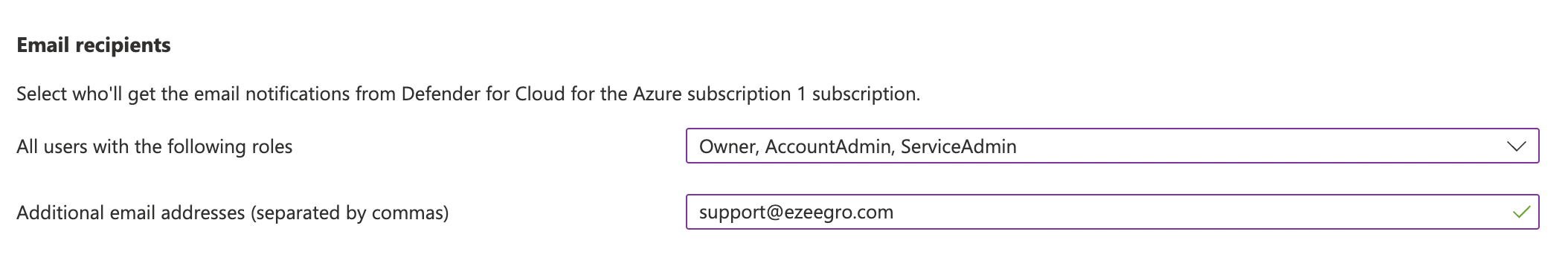
In the “Notification types” checkmark “Notify about alerts with the following severity (or higher)” and select “High” from the dropdown.
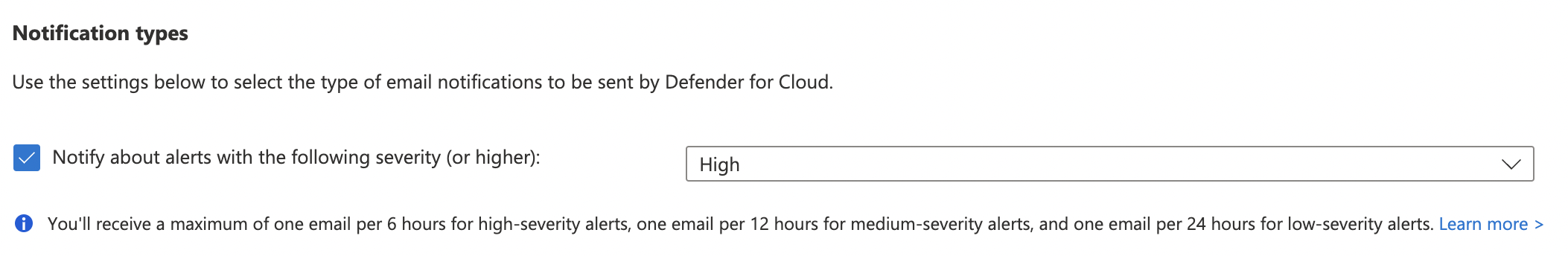
Click “Save” at the top to make the necessary changes.
Repeat steps 3-10 to ensure that an email address is activated under send alerts for all SQL servers.