CLB HTTPS Only
Ensures that HTTP(S) CLBs are configured to only accept connections on HTTPS ports.
For maximum security, CLBs can be configured to only accept HTTPS connections. Standard HTTP connections will be blocked. This should only be done if the client application is configured to query HTTPS directly and not rely on a redirect from HTTP.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Log into the Google Cloud Platform Console.
Scroll down the left navigation panel and choose the “Network Services” option under the “NETWORKING” and select the “Load balancing.”
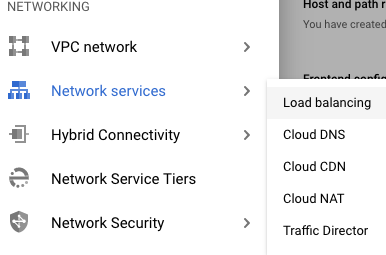
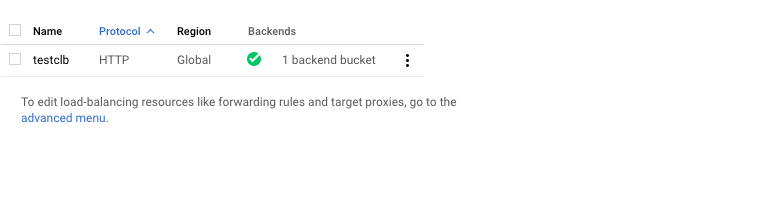
On the “Load balancing” page , click on the “Name” as a link option to select the load balancer.
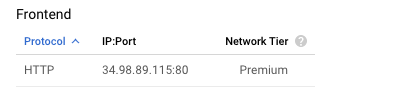
On the “Load balancer details” page, scroll down the page and check the “Protocol” option under the “Fronend.” If it’s set to “HTTP” then the selected “Load balancer” is not a part of GCP best practices.
Repeat steps number 2 - 4 to verify other “Load balancers” in the account.
Navigate to the “Load balancing” option under the “Netowrk Services” of the “NETWORKING”, choose the “load balancer” and click on the “Edit” button at the top.
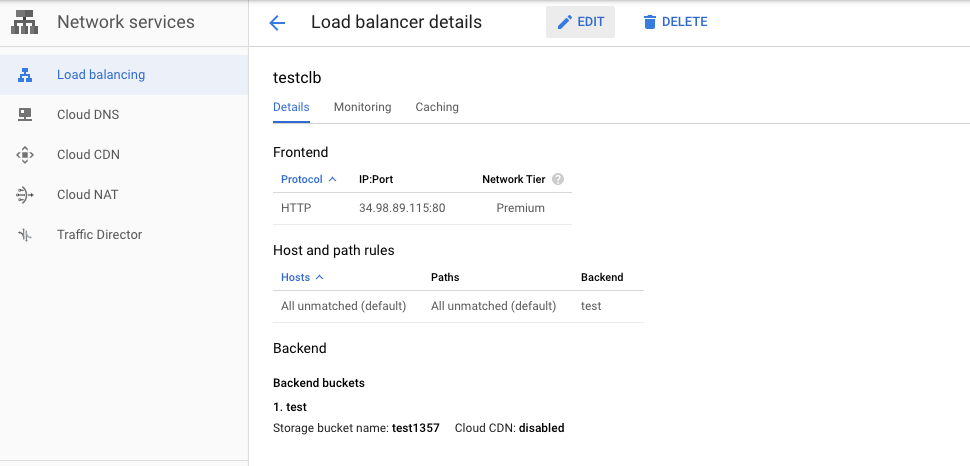
On the “Edit HTTP(S) load balancer” page, click on the “Frontend configuration” option, click on the pencil icon next to the “Bucket/VM” present in the “Frontend configuration” page.
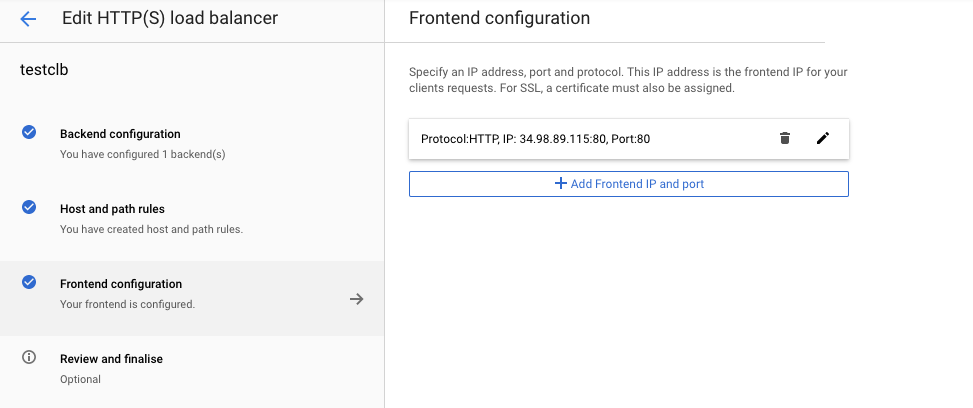
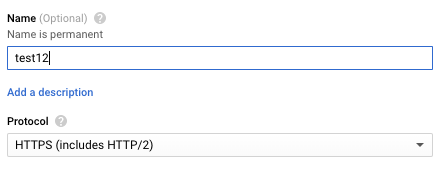
On the “Frontend configuration” tab, select the “Protocol” as “HTTPS” and select the corresponding certificate and click on the “Done” button.
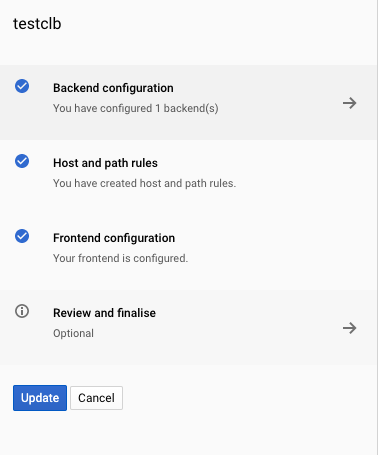
On the “Edit HTTP(S) load balancer” page, click on the “Update” button to save the changes.
Repeat steps number 6 - 9 to remove non-HTTPS listeners from the load balancer.