VM Instances Least Privilege
Ensures that instances are not configured to use the default service account with full access to all cloud APIs
To support the principle of least privilege and prevent potential privilege escalation, it is recommended that instances are not assigned to the default service account, Compute Engine default service account with a scope allowing full access to all cloud APIs.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Google Cloud Platform Console.
-
Scroll down the left navigation panel and choose the “Compute Engine” to select the “VM Instances” option.
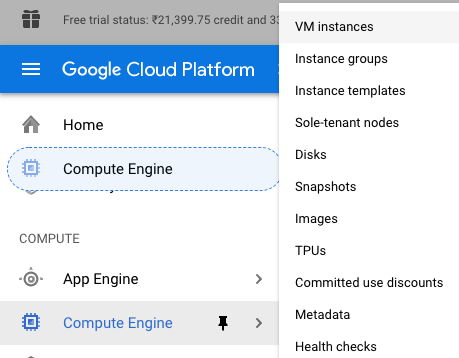
-
On the “VM Instances” page, select the VM instance which needs to be verified.
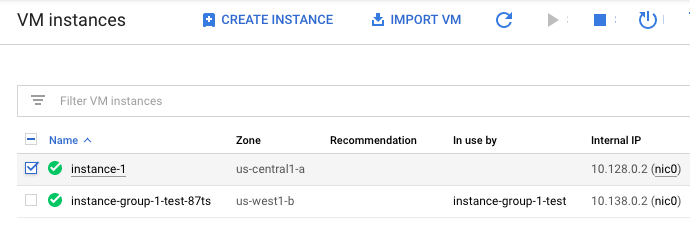
-
On the “VM instance details” page, scroll down and check “Cloud API access scopes” and see if the “Default service account” is used or not.

-
Repeat steps number 2 - 4 to verify other VM instances in the network.
-
Navigate to “Compute Engine”, choose the “VM instances” and select the “VM instance” which needs to ensures that instances are not configured to use the default service account with full access to all cloud APIs.
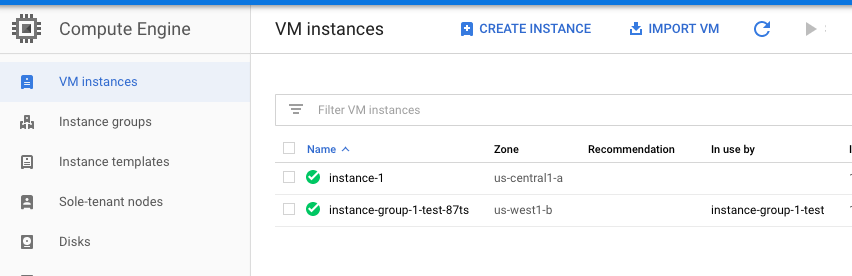
-
On the “VM instance details” page, select the “Edit” button at the top.
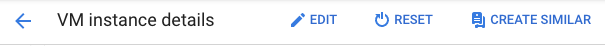
-
On the “VM instance details - Edit page”, scroll down the page and check the “Cloud API access scopes” and make sure “full access to all cloud APIs is not configured.”
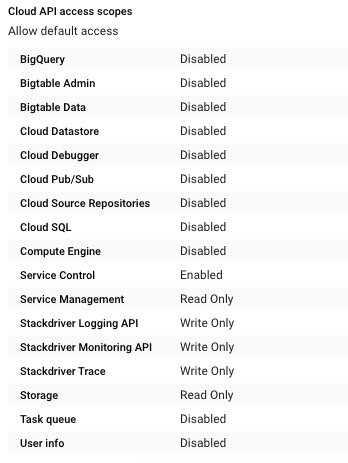
-
Click on the “Save” button to make the changes.
-
If “full access to all cloud APIs is configured”, we need to create a replica of that instance and need to launch the “Instance” with restricting “Cloud APIs” access.
-
Repeat steps number 6 - 10 to ensure if the default service account is used, ensure full access to all cloud APIs is not configured.