Ensure that Cloud SQL Database Instances are not publicly exposed
Database instances should be configured so that they are not available over the public internet, but to internal compute resources which access them.
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Google Cloud Platform Console.
-
Scroll down the left navigation panel and choose the “SQL” option under the “Storage.”
-
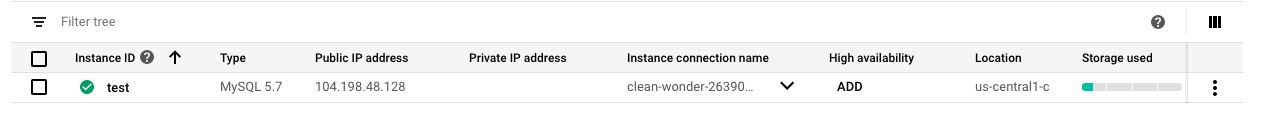
On the “SQL” page , click on the “Instance ID” as a link option to select the “SQL” instance.
-
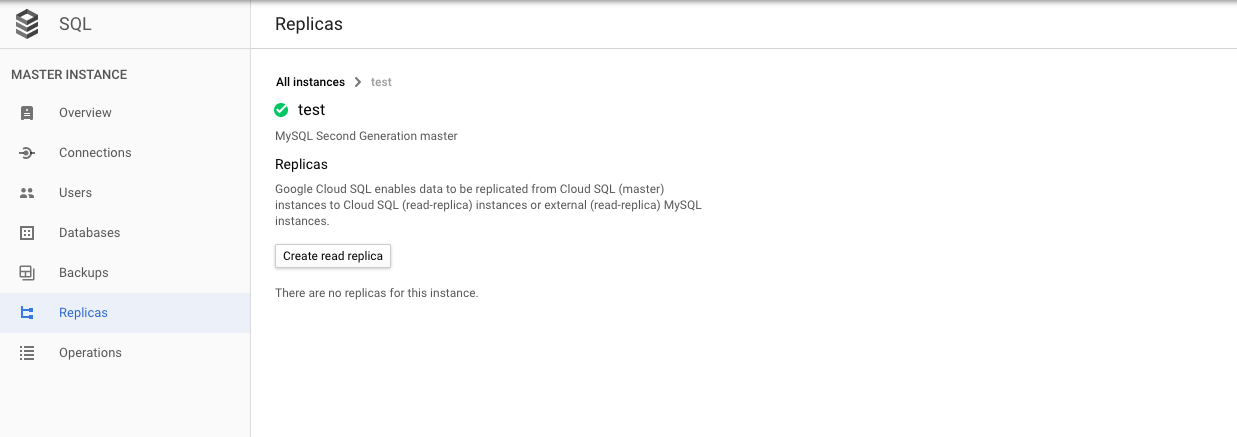
On the “SQL” page, click on the “Replicas” under the “MASTER INSTANCE.”
-
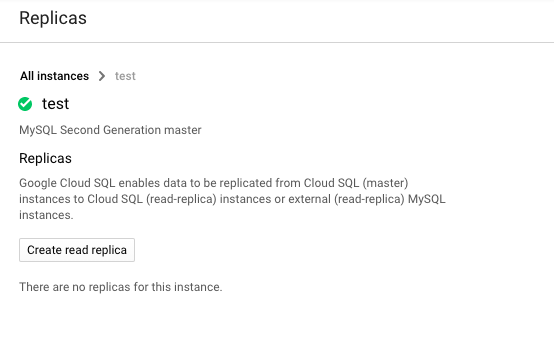
On the “Replicas” page, check is there any “Relica” is there or not. Creating SQL instances in with a single AZ creates a single point of failure for all systems
-
Repeat steps number 2 - 5 to check other SQL instance in the account.
-
Navigate to the “SQL” option under the “Storage”, choose the “SQL Instance”.
-
Click on the “Replicas” from the left panel and click on the “Create read replica” button at the bottom.
-
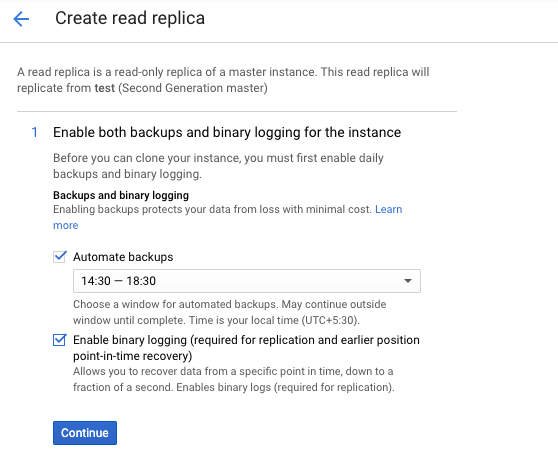
On the “Create read replica”, click on the checkbox next to “Automate backups”, “Enable binary logging” and click on the “Continue” button.
-
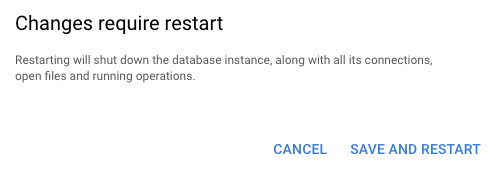
Once you click on the “Continue” button, “Changes require restart” tab will open and click on the “SAVE AND RESTART” option.
-
Click on the “Create” button to make the changes.
-
Repeat steps number 7 - 11 to ensure all SQL instances should be created in multiple AZs to ensure proper failover.
Remove public access from database instances
|
|