Storage Bucket All Users Policy
Ensures Storage bucket policies do not allow global write, delete, or read permissions
Storage buckets can be configured to allow the global principal to access the bucket via the bucket policy. This policy should be restricted only to known users or accounts.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Log into the Google Cloud Platform Console.
Scroll down the left navigation panel and choose “Cloud Storage” to select the “Buckets” option.
On the “Buckets” page, select the bucket which you want to configure by clicking on its name.
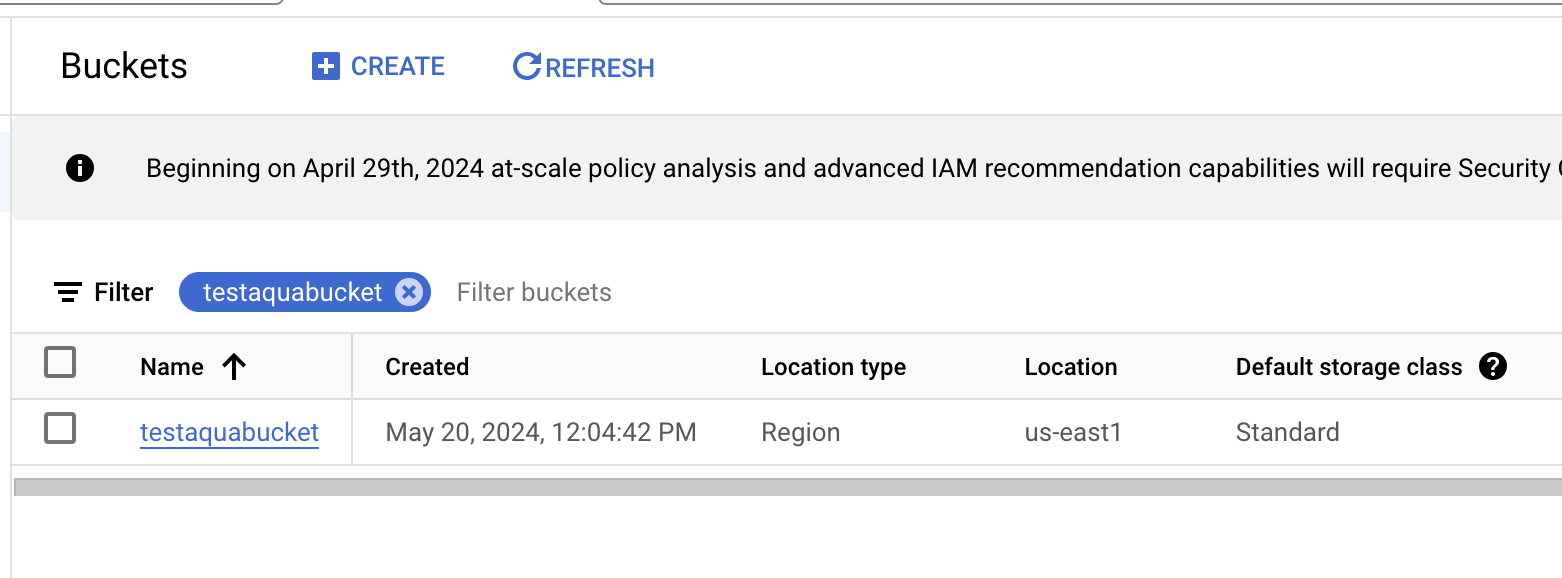
Select the “PERMISSIONS” tab to access the permissions defined for selected bucket.
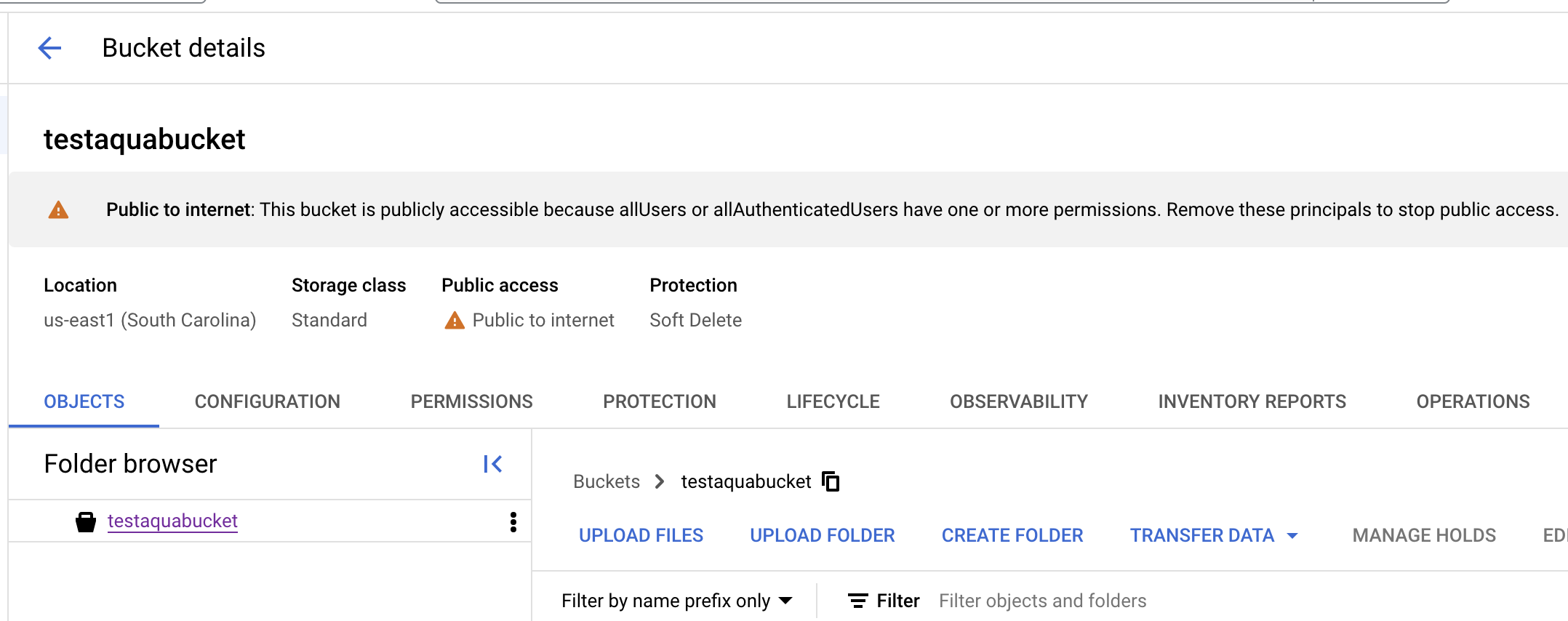
Select the “VIEW BY PRINCIPALS” tab to display all IAM members (principals) that have access to the selected resource.
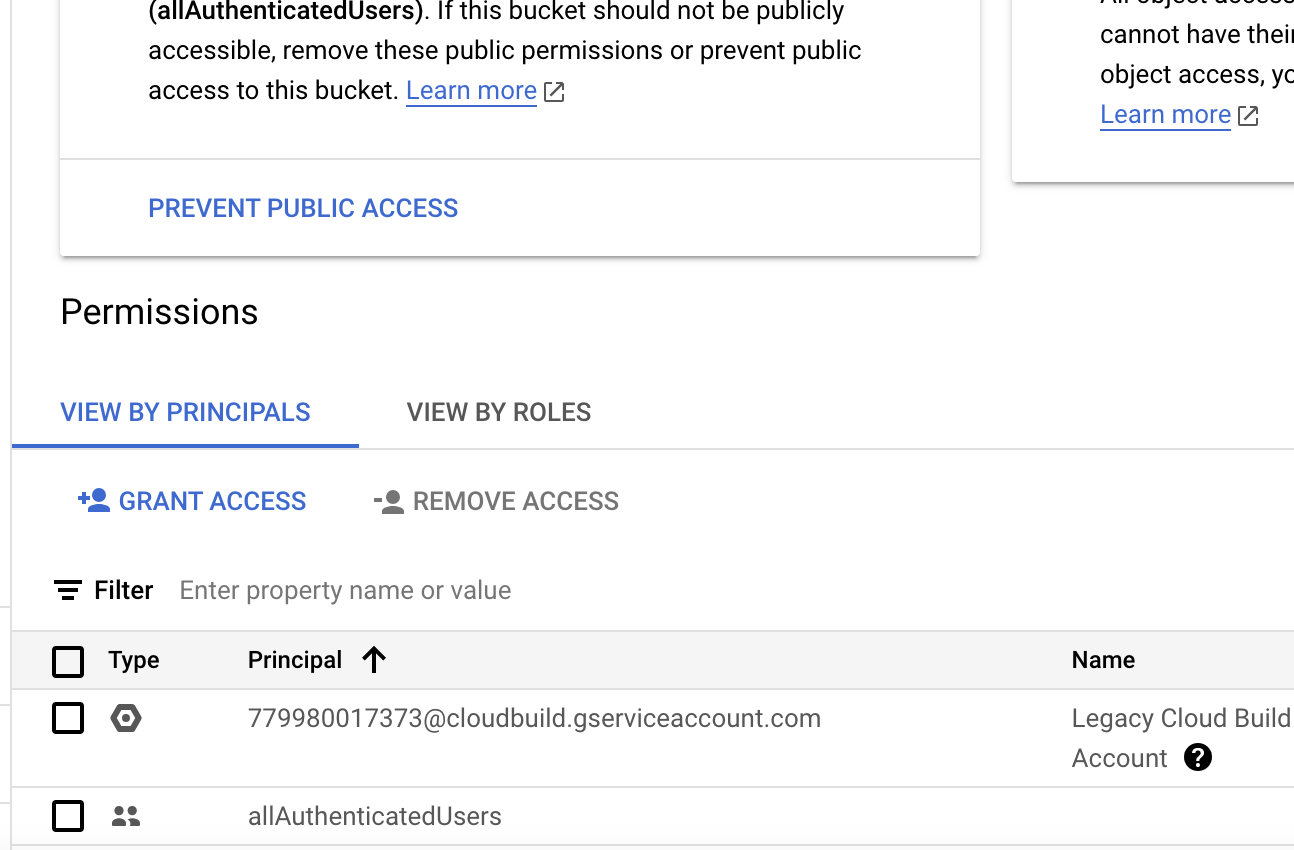
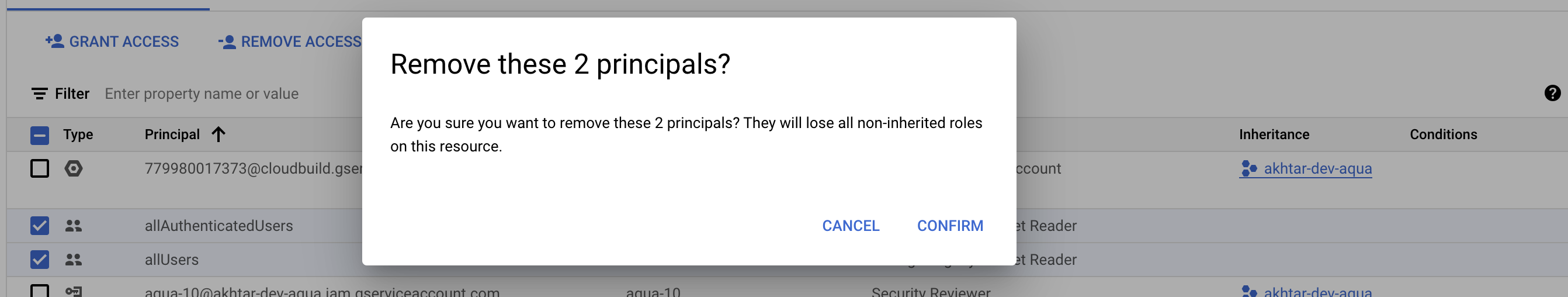
Select all the allUsers and allAuthenticatedUsers principals available and choose REMOVE ACCESS to initiate the removal action for the selected bindings.
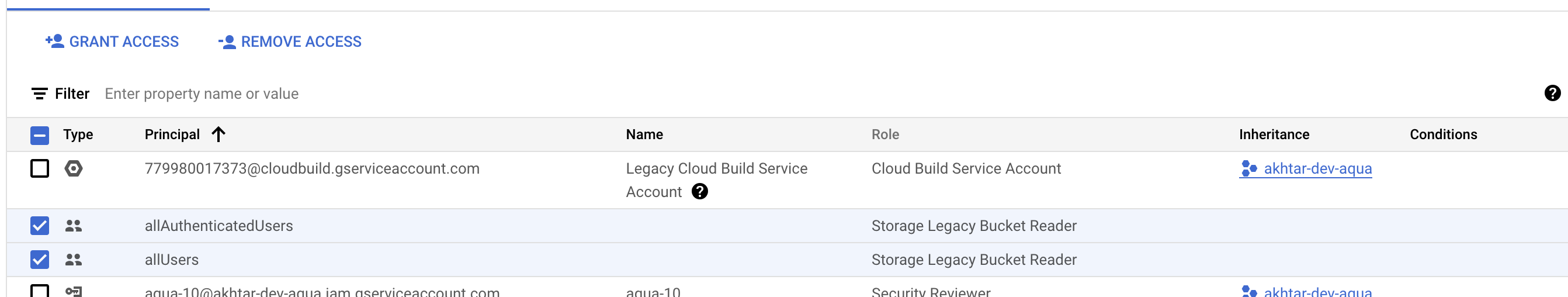
On the removal confirmation box, choose “CONFIRM” to remove the allUsers and/or allAuthenticatedUsers principals.
Repeat steps number 4-7 to remove all allUsers or allAuthenticatedUsers access from all other buckets in the project.