Open All Ports Egress
Ensure no firewall rules allow egress to all ports and protocols.
Allowing outbound traffic to all protocols and ports can lead to internal resources accessing unwanted and untrusted resources. It is a best practice to follow the principle of least privilege, and grant access to only required protocols and ports.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Log into the Google Cloud Platform Console.
Scroll down the left navigation panel and choose the “Networking” to select the “Firewall rules” option under the “VPC network.”
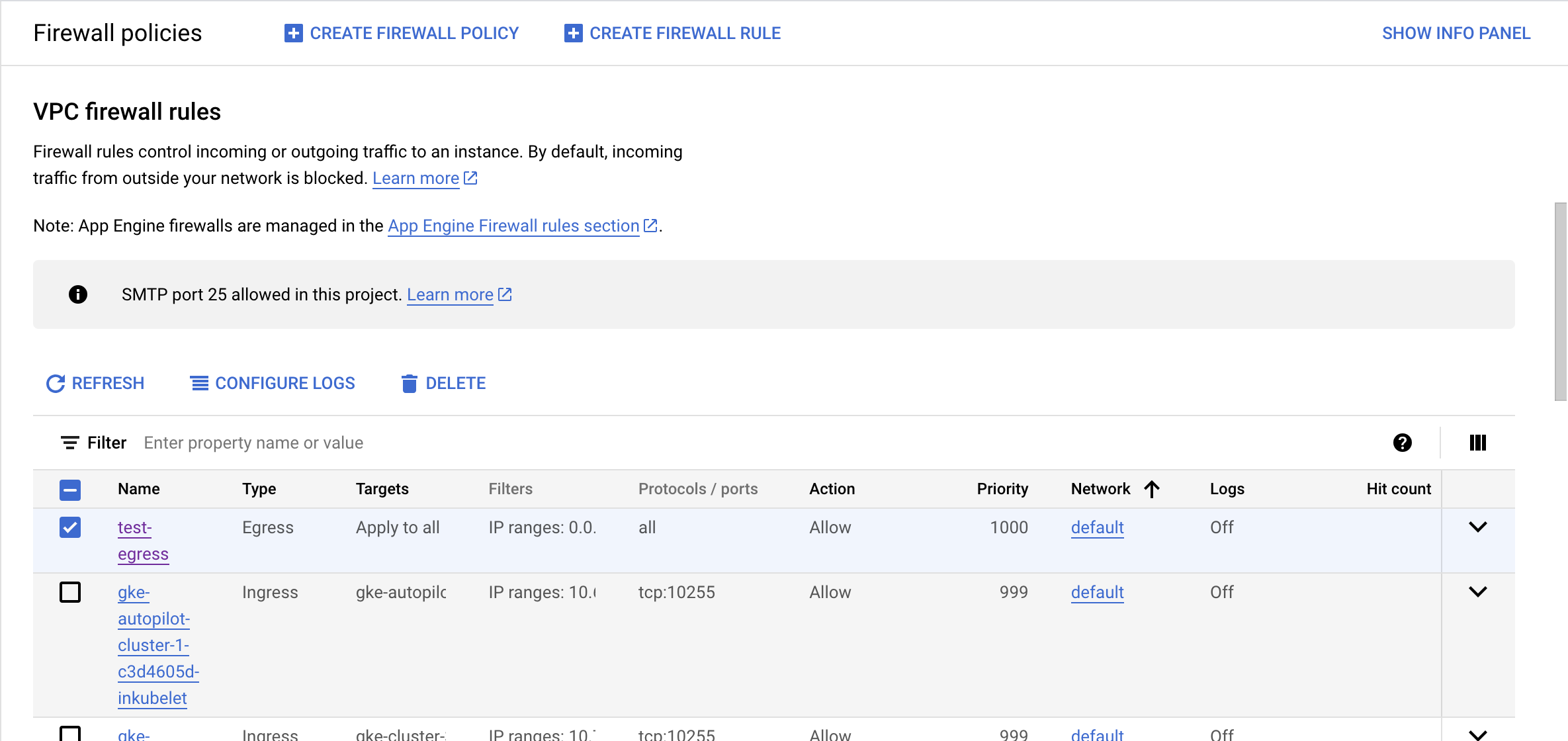
On the “Firewall rules” page, select the “Firewall rule” which needs to be verified if it allows egress to all port and protocols.
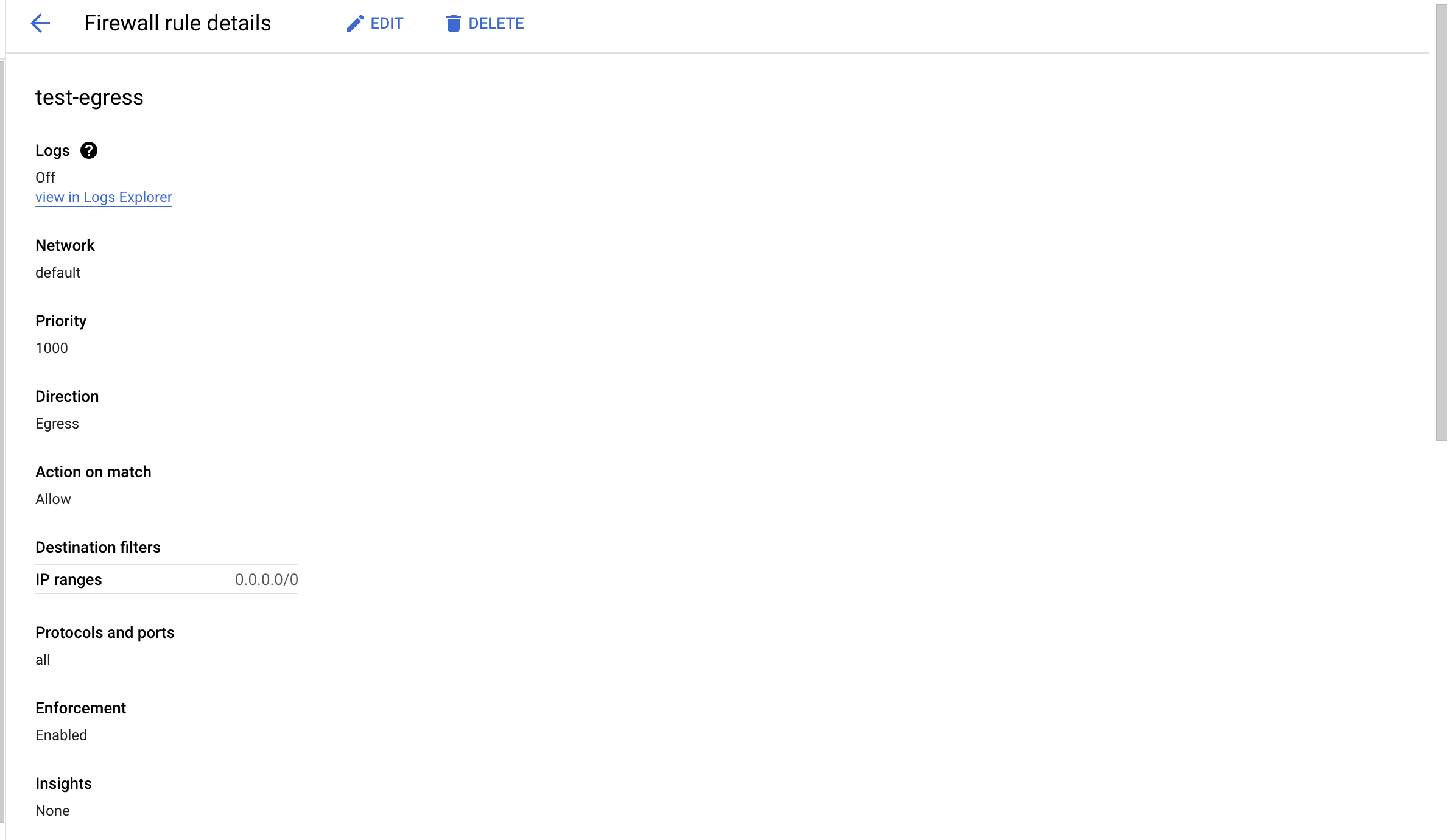
On the selected “Firewall rules”, if all ports are open to the public then the selected “Firewall rule” is not as per the best standards.
Repeat steps number 2 - 4 to verify another “Firewall rule” in the network.
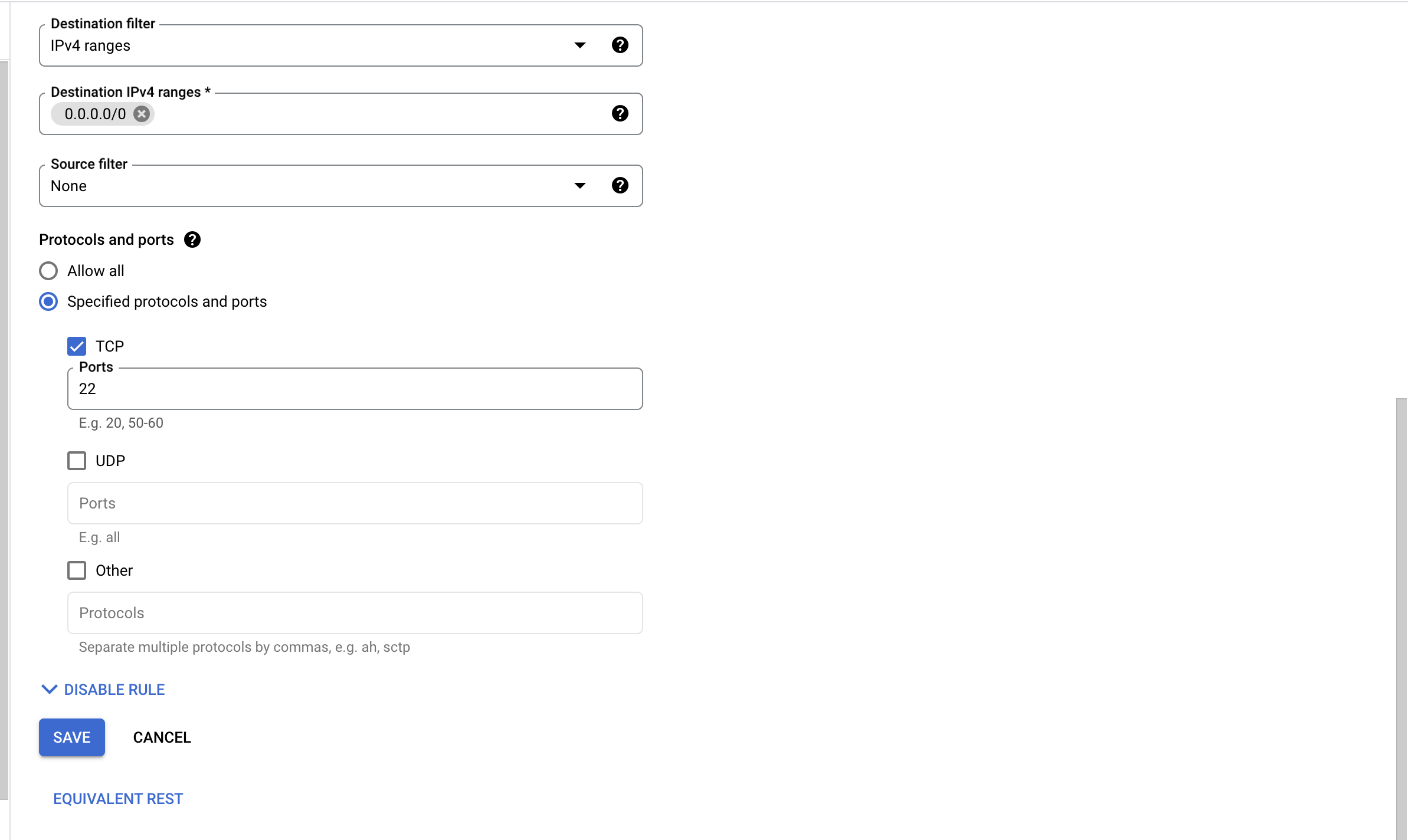
Navigate to “VPC network” and choose the “Firewall rules” option under the “Networking” and select the “Firewall rule” which needs to restrict outbound traffic to known IP addresses.

On the “Firewall rules” page, click on the “Edit” button at the top and enter the “Destination IP ranges” and select the “Specified protocols and ports” as per the requirements then click on the “Save” button at the bottom to make the changes
Repeat steps number 6 - 8 to restrict ports to known IP addresses.