Open All Ports Protocols
Determine if security list has all ports or protocols open to the public
Security lists should be created on a per-service basis and avoid allowing all ports or protocols.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Google Oracle Platform Console.
-
Scroll down the left navigation panel and choose the “Virtual Cloud Networks” under the “Networking.”
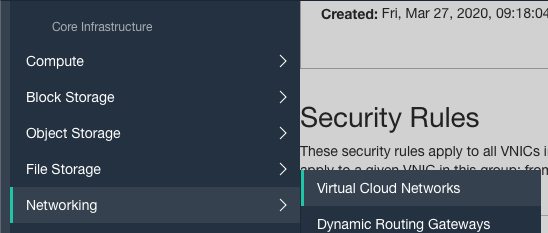
-
On the “Virtual Cloud Networks” page, click on the “Name” as a link to access the “Virtual Network.”
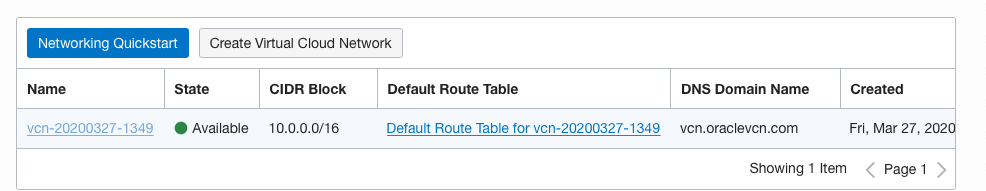
-
On the “Virtual Cloud Network Details” page, scroll down the left navigation panel and choose the “Network Security Groups” option under the “Resources.”
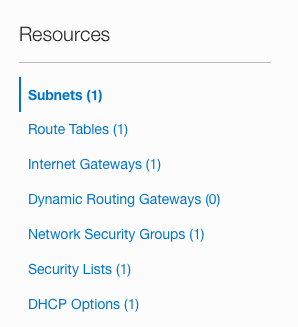
-
On the “Network Security Groups” page, select the “Security group” by clicking on the “Name” as a link to access the security group.
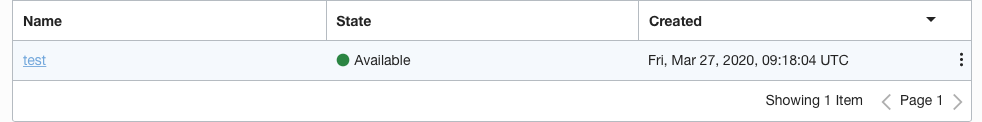
-
On the “Network Security Group Details” page, under the “Security Rules” check if security list has all ports or protocols open to the public.
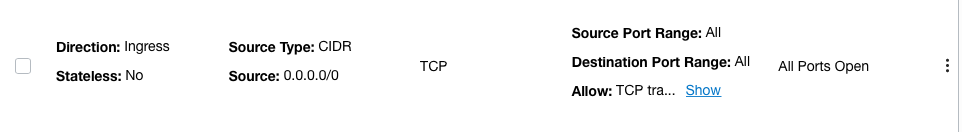
-
Repeat steps number 2 - 6 to check other “Security Groups” in the account.
-
Navigate to “Virtual Cloud Networks” under the “Networking”, click on the “Name” as a link to access the “Virtual Network”, select the “Security Group” in which security list has all ports or protocols open to the public.
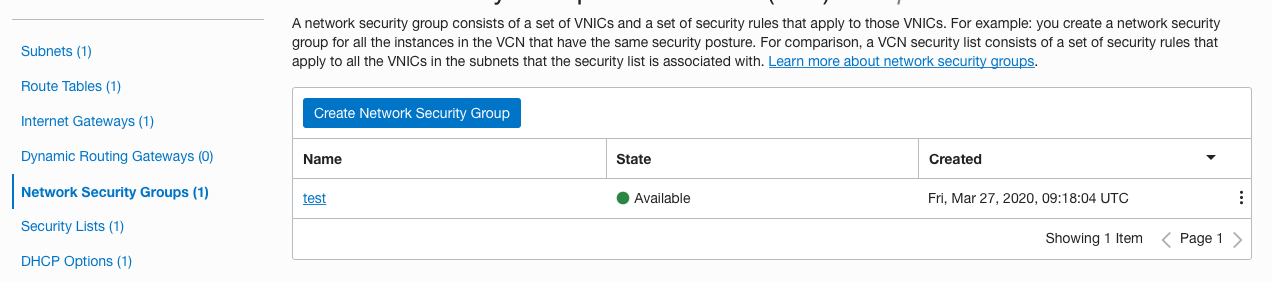
-
On the “Security Rules” page, click on the checkbox of the “Ingress” and click on the “Edit” button at the top to make the changes.
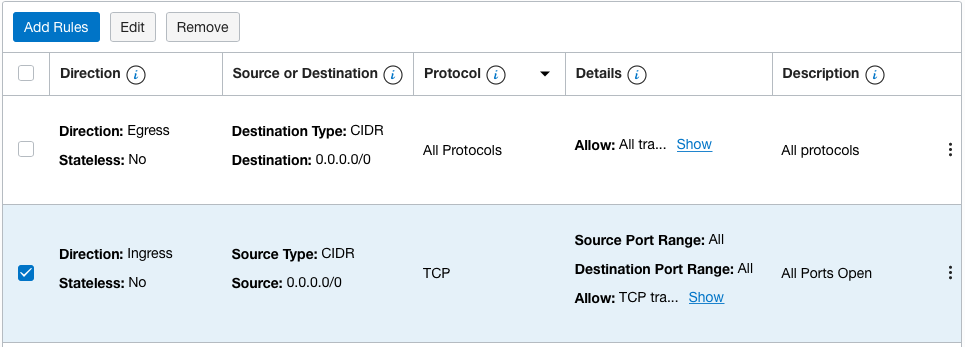
-
On the “Edit Rules” page, enter the “IP Address” as per requirements under the “Source CIDR” and click on the “Save” button to make the changes.
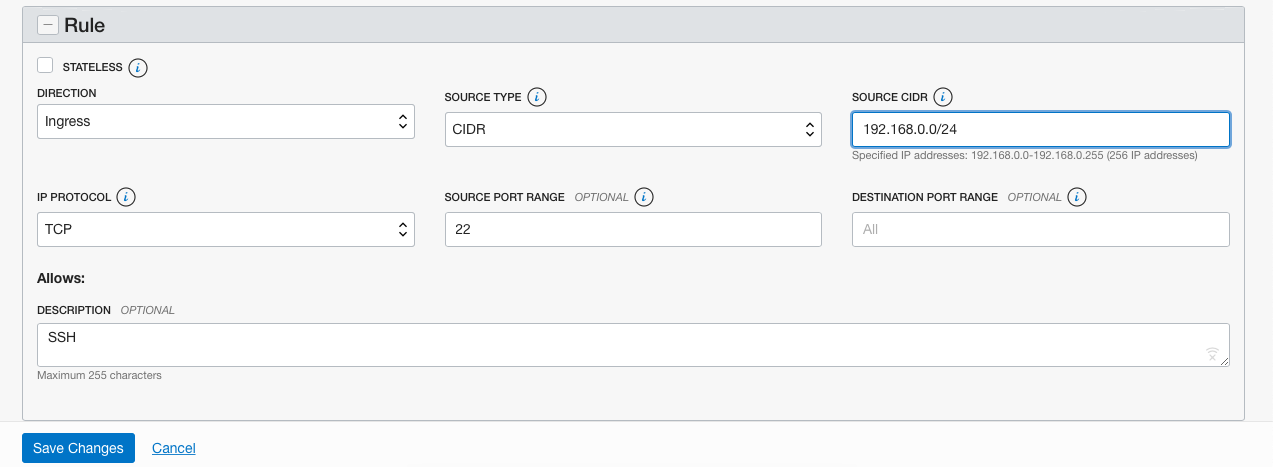
-
Repeat steps number to restrict security list to specify a specific port and protocol to allow.