Cloudtrail should be enabled in all regions regardless of where your AWS resources are generally homed
Activity could be happening in your account in a different region. When creating Cloudtrail in the AWS Management Console the trail is configured by default to be multi-region, this isn’t the case with the Terraform resource. Cloudtrail should cover the full AWS account to ensure you can track changes in regions you are not actively operating in.
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Enable Cloudtrail in all regions
|
|
-
Log into the AWS Management Console.
-
Select the “Services” option and search for “CloudTrail”.
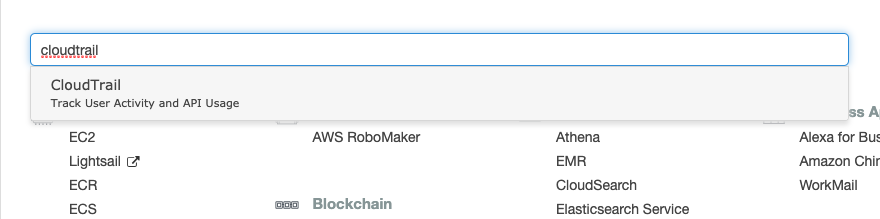
-
In the “Dashboard” panel click on “View trails” button.
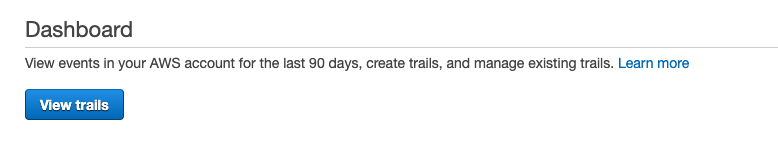
-
Select the “trail” that needs to be verified under “Name” column.
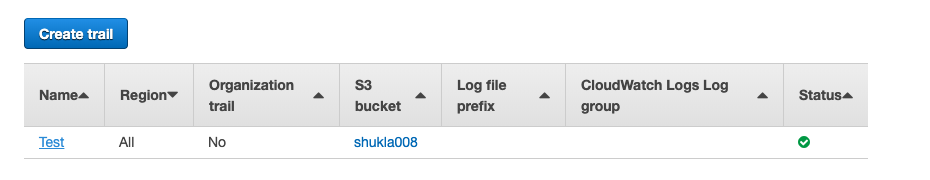
-
Click the pencil icon to go into “Trail Settings” and verify the checkbox marked against “Apply trail to all regions “. If “No” is selected than create and manage a trail across all regions is not possible.
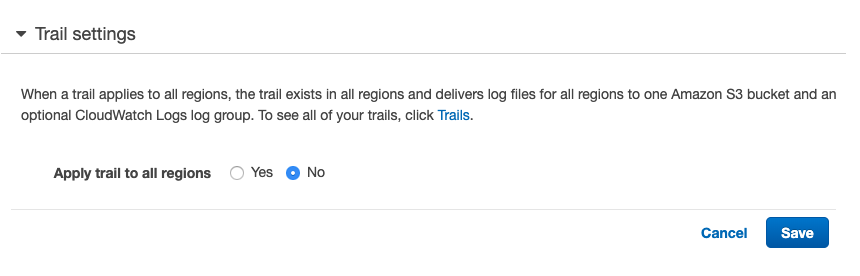
-
Go to “Trail Settings” and click on “Yes” checkbox to enable the “Apply trail to all regions” which receive the log files containing event history for the new region without taking any action. Click on the “Save” button to make the changes.
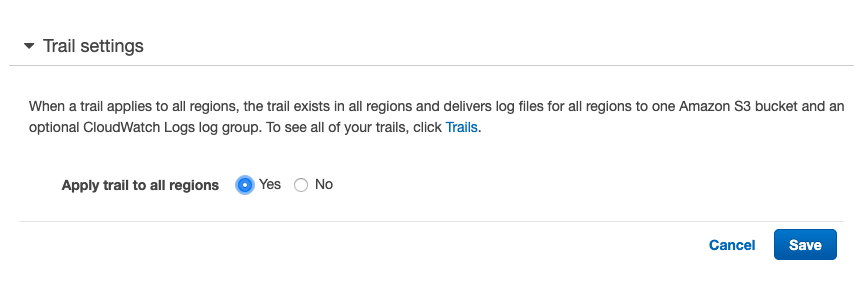
-
Scroll down and go to “Additional Configuration” settings and click on the pencil icon to make the changes.
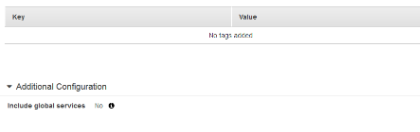
-
Click on the “Yes” checkbox corresponding to the “Include global services” and click on “Save” button to make the changes.
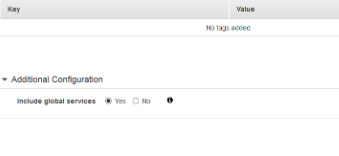
-
CloudTrail is enabled for all regions with global service events now.