CloudTrail should use Customer managed keys to encrypt the logs
Using AWS managed keys does not allow for fine grained control. Using Customer managed keys provides comprehensive control over cryptographic keys, enabling management of policies, permissions, and rotation, thus enhancing security and compliance measures for sensitive data and systems.
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Use Customer managed key
|
|
Remediation Links
-
Log in to the AWS Management Console.
-
Select the “Services” option and search for “CloudTrail”.
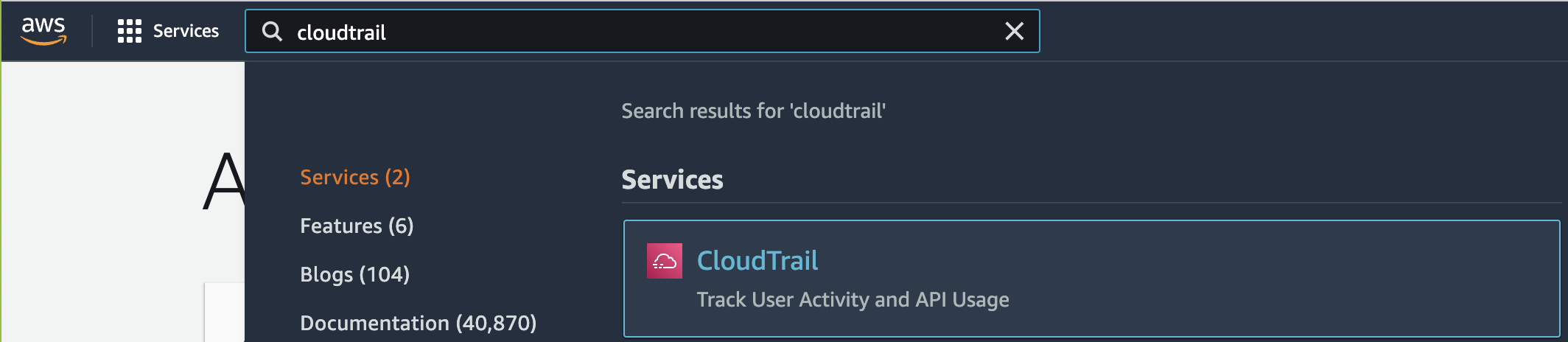
-
In the “Dashboard” panel click on the desired trail from the list under “Trails” to get to its configuration page.
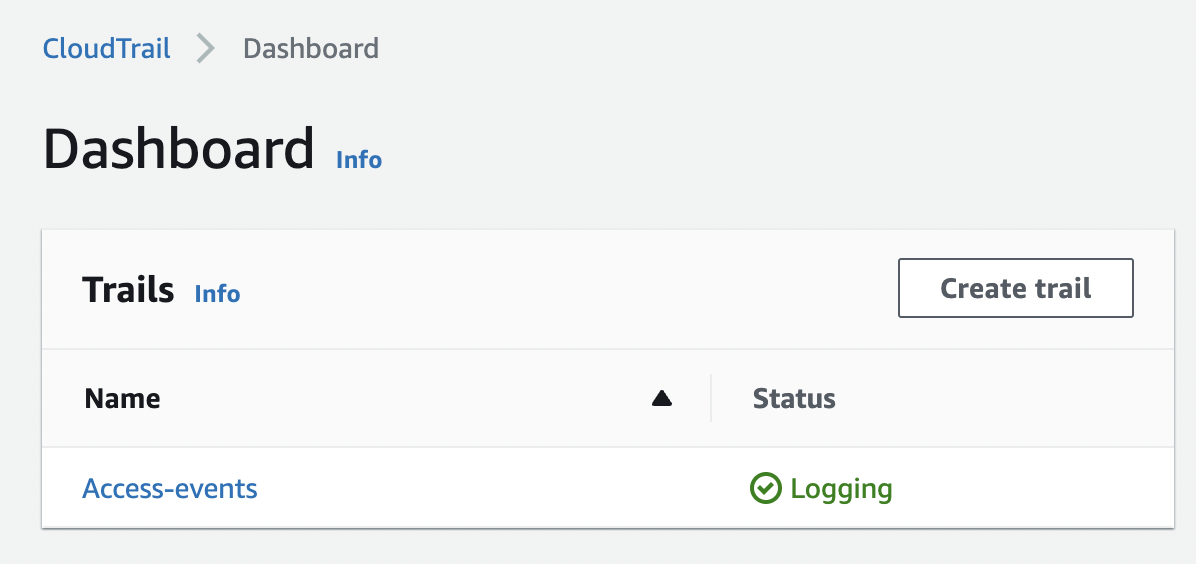
-
Click on “Edit” button under “General details”.
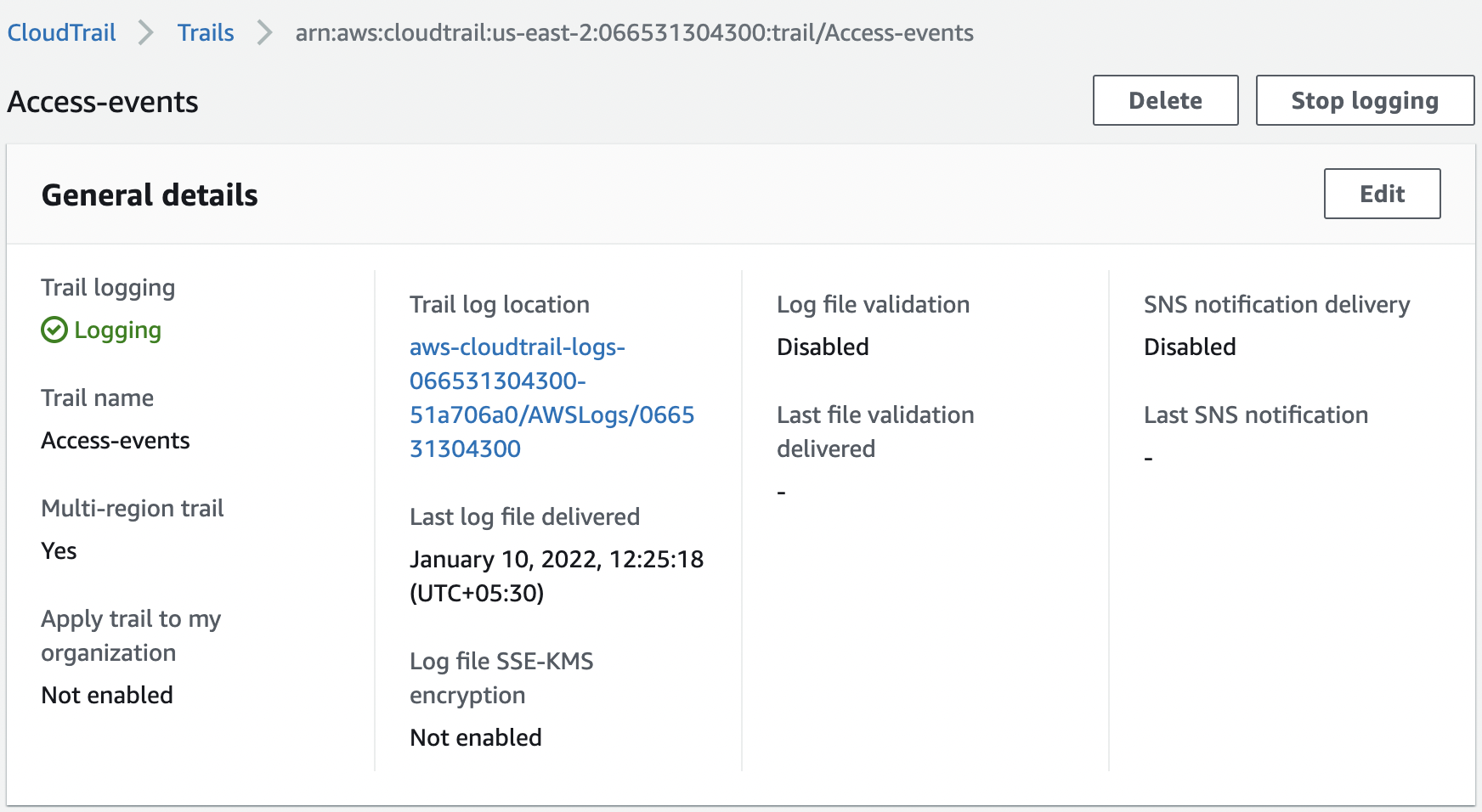
-
On the Edit Trail page scroll down and check for “Log file SSE-KMS encryption”. If its status is not selected as “Enabled” then the selected trail does not support log encryption.
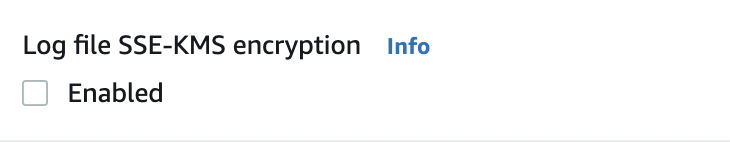
-
Select the checkbox to change the status as “Enabled” under “Log file SSE-KMS encryption” to enable the “CloudTrail” log encryption.
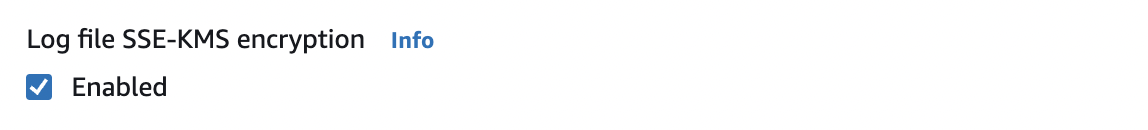
-
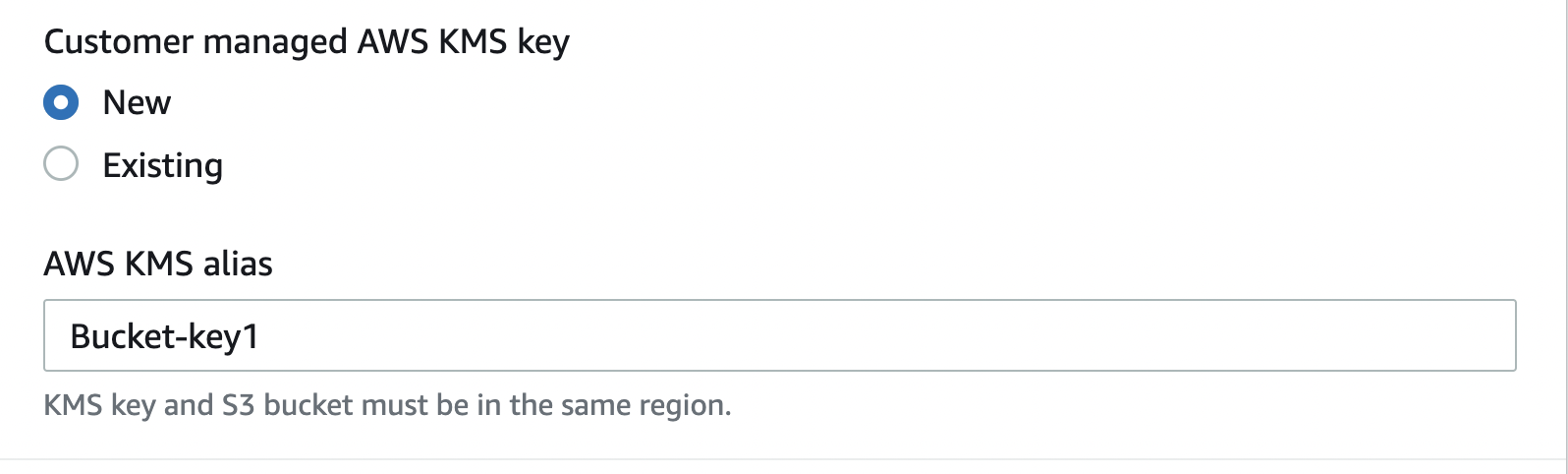
If you do not have an existing KMS key then under “Customer managed AWS KMS key” option select “New” and enter a name for “AWS KMS alias”. Make sure KMS key and S3 bucket must be in the same region.
-
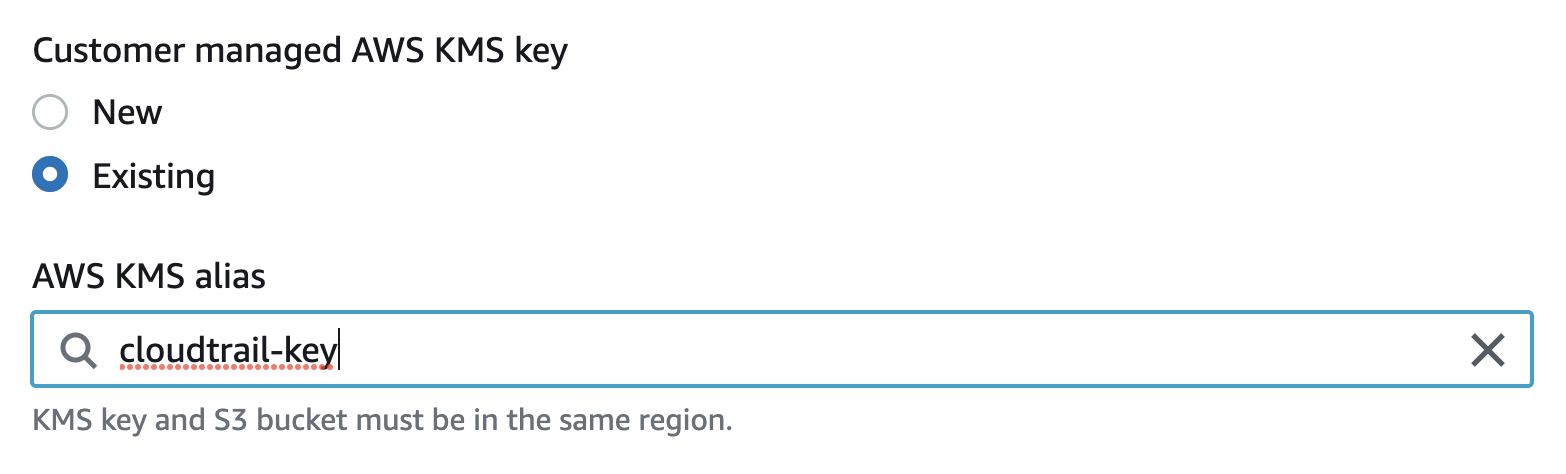
If you already have a “KMS key” available then under “Customer managed AWS KMS key” option select “Existing” and click to choose an existing key under “AWS KMS alias”. .
-
Scroll down and click on “Save changes” to enable the CloudTrail log encryption.

Use Customer managed key
|
|