Cloudtrail log validation should be enabled to prevent tampering of log data
Illicit activity could be removed from the logs. Log validation should be activated on Cloudtrail logs to prevent the tampering of the underlying data in the S3 bucket. It is feasible that a rogue actor compromising an AWS account might want to modify the log data to remove trace of their actions.
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Turn on log validation for Cloudtrail
|
|
-
Log in to the AWS Management Console.
-
Select the “Services” option and search for “CloudTrail”.
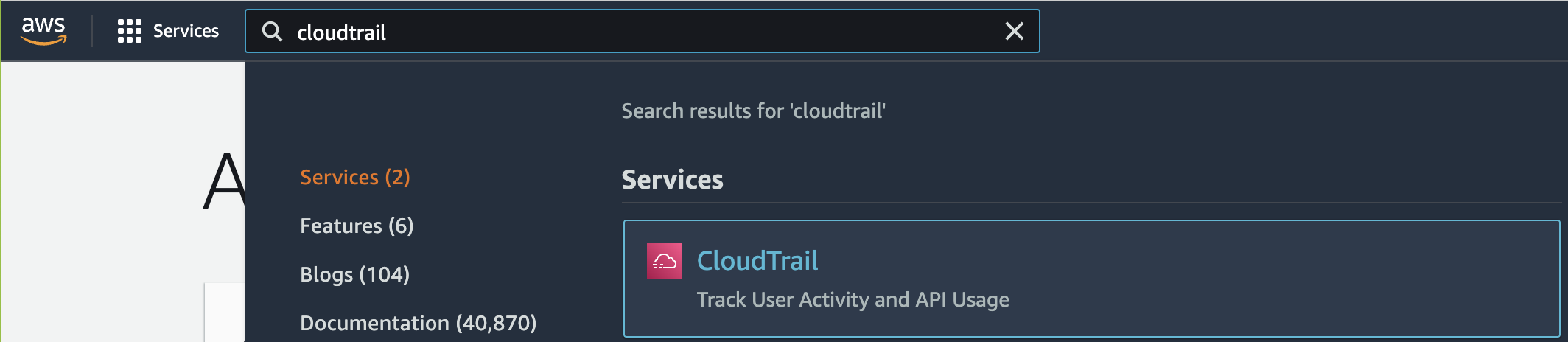
-
In the “Dashboard” panel click on the desired trail from the list under “Trails” to get to its configuration page.
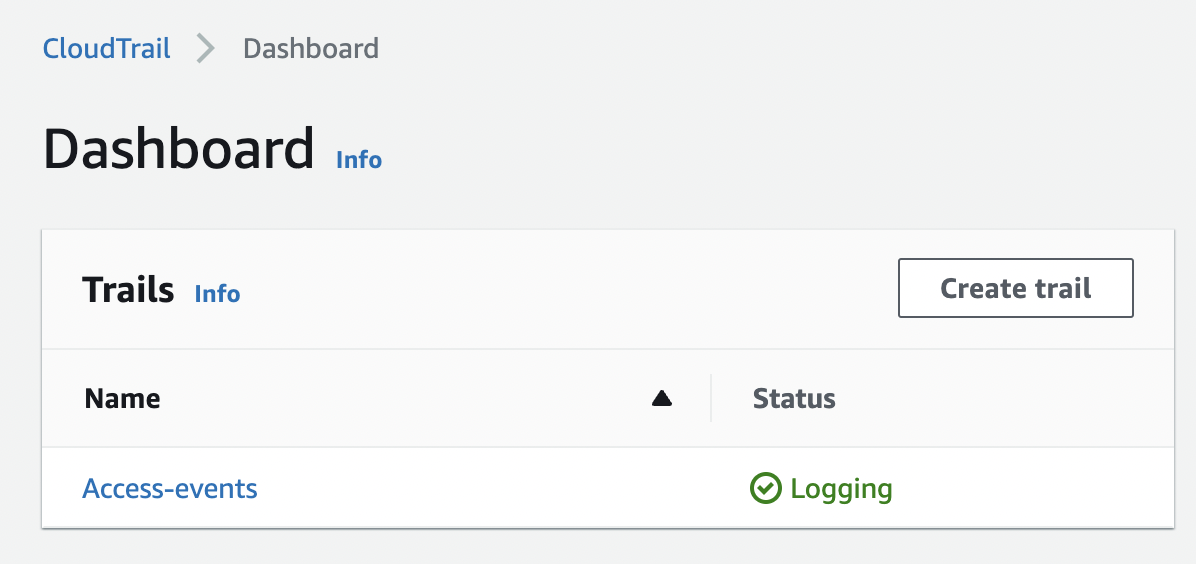
-
Click on “Edit” under “General details”.
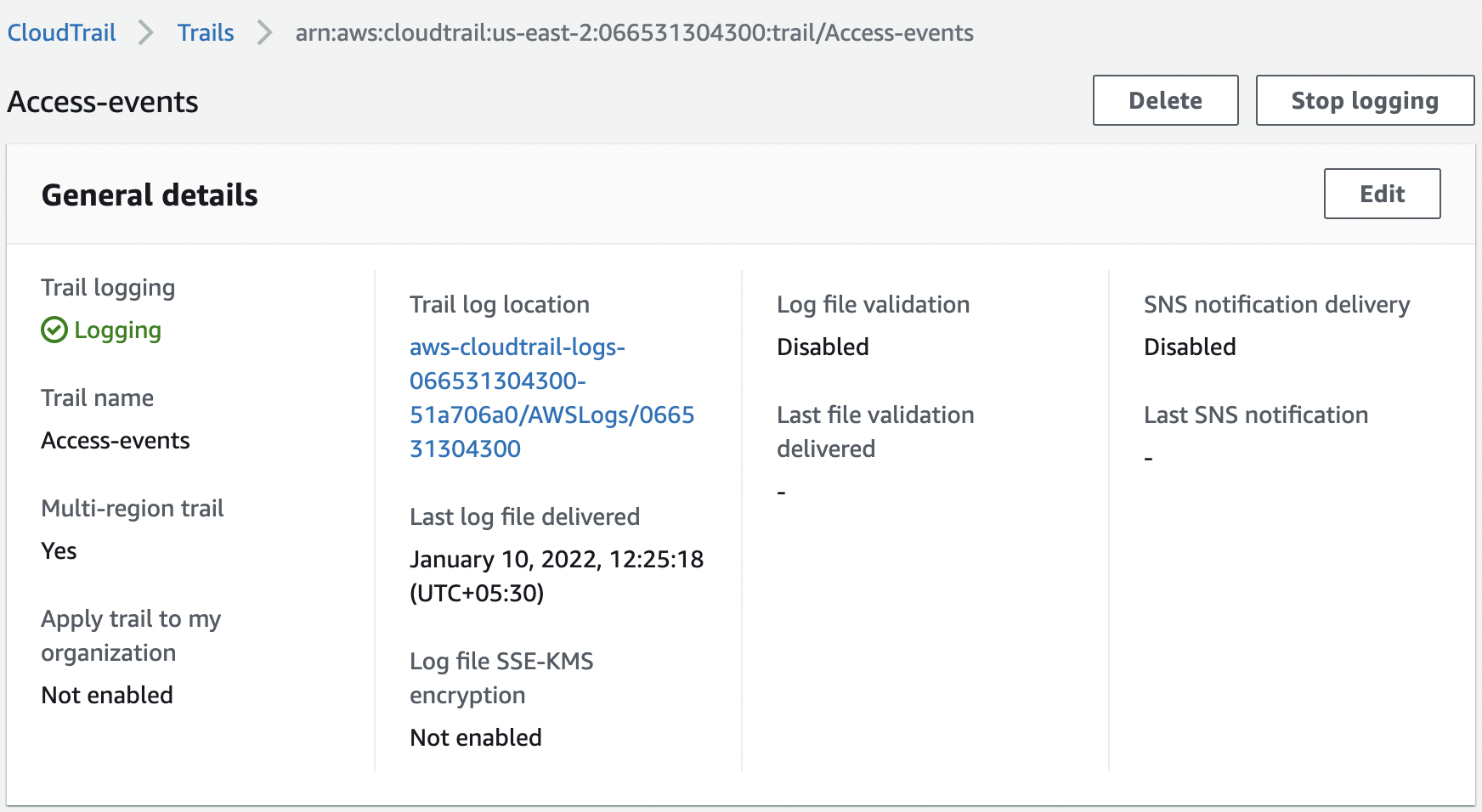
-
Scroll down and under the “Additional settings” option check for “Log file validation”. If its status is not selected as “Enabled” then the selected trail does not support file validation.
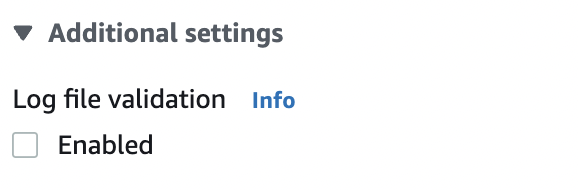
-
Click on the checkbox under “Log file validation” to change its status to “Enabled” so that the “CloudTrail” file validation to determine whether a log file was modified, deleted or unchanged after “CloudTrail” delivered is enabled.

-
Scroll down and click on “Save changes” to enable the CloudTrail log encryption.
