Open All Ports Protocols
Determine if security group has all ports or protocols open to the public
Security groups should be created on a per-service basis and avoid allowing all ports or protocols.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the AWS Management Console.
-
Select the “Services” option and search for EC2.
-
Scroll down the left navigation panel and choose “Security Groups” under “Network & Security”.

-
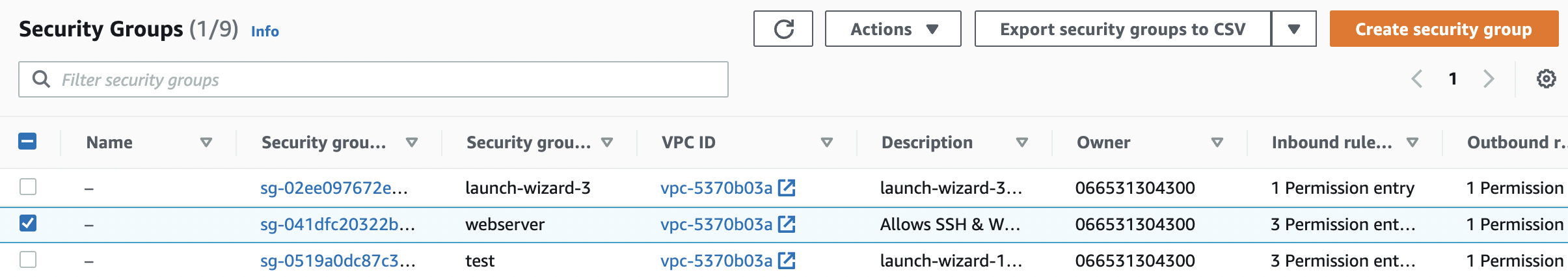
Select the “EC2 Security Group” that needs to be verified.
-
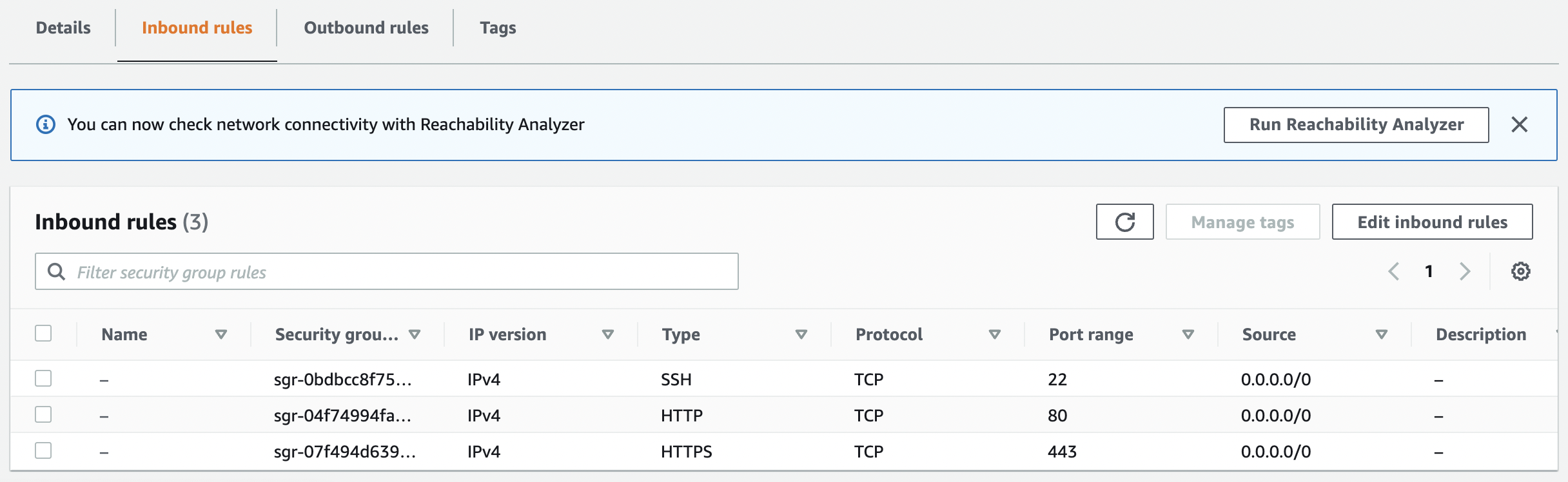
Scroll down the bottom panel and choose “Inbound rules”. Verify the value for “Source” column and if any rule have value set to “0.0.0.0/0” or “::/0 " then the selected “Security Group” has one or many ports open to the public.
-
Repeat steps number 2 - 5 to verify other “Security Groups” in the selected AWS region.
-
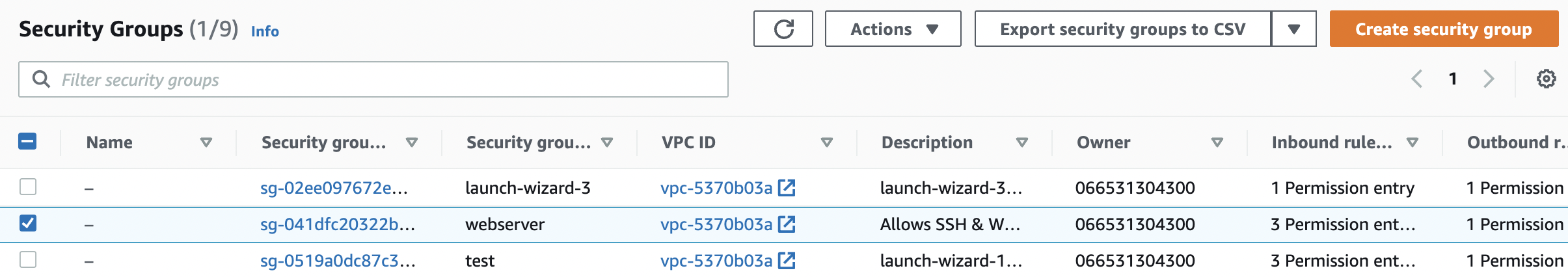
Navigate to “Security Groups” under “Network & Security” and select the “Security Group” that needs to be modified to restrict the access to specific IP address.
-
Scroll down the “Security Group” page and select the “Inbound rules” and click on the “Edit inbound rules” button to the right.
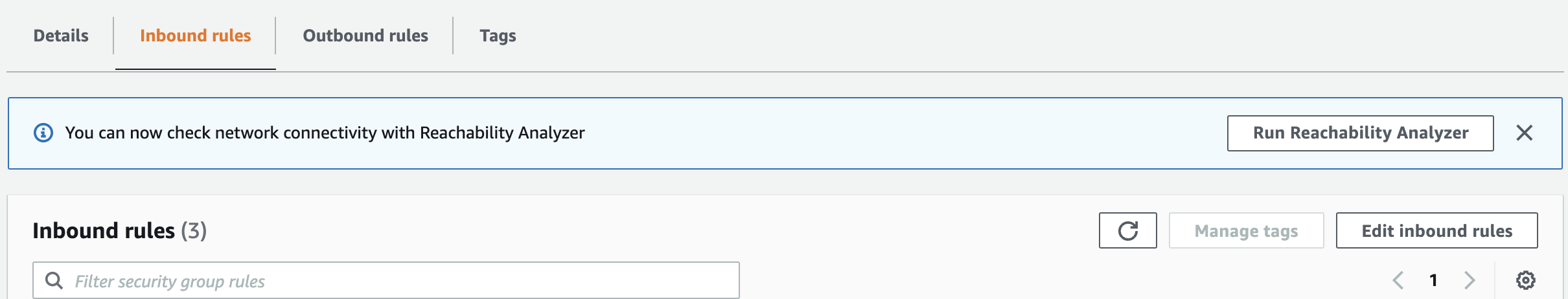
-
In the “Edit inbound rules” tab select the “MyIP” from the “Source” column of type “SSH” to allow inbound traffic only from your current IP address.
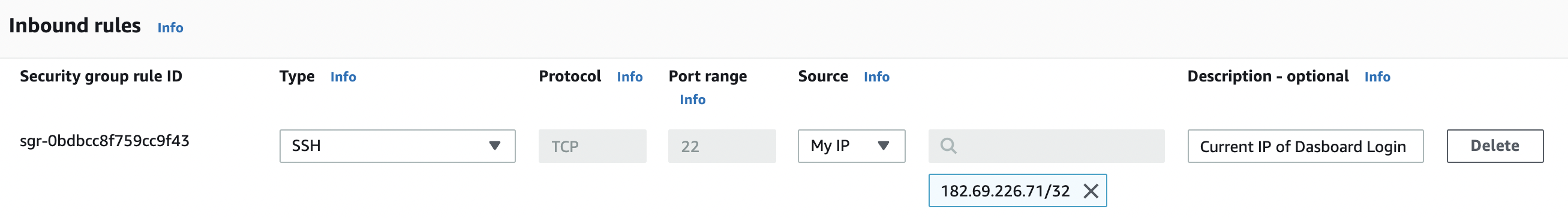
-
In the “Edit inbound rules” tab select the “Custom” from the “Source” column if you want to specify a “static IP” address of the permitted host along with “Description” for the “Security Group” rule.
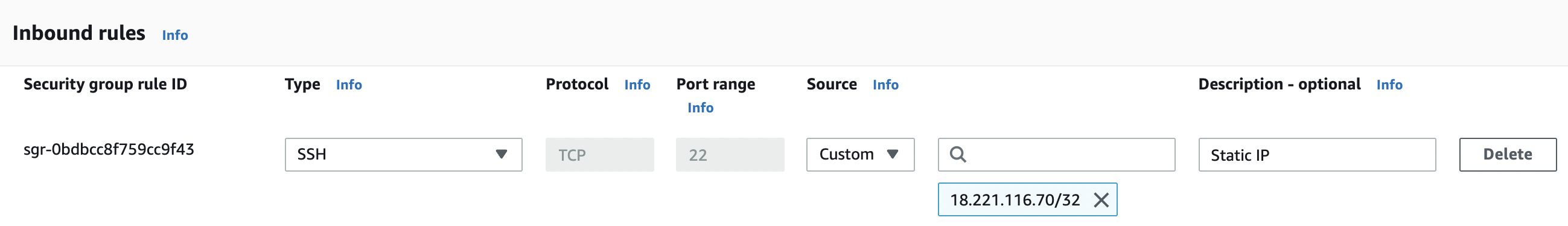
-
Click on the “Save rules” button to make the necessary changes.
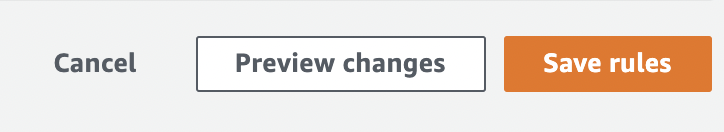
-
Repeat steps number 7 - 11 to modify the security group to add a specific port and protocol to allow.