Overlapping Security Groups
Determine if EC2 instances have security groups that share the same rules
Overlapping security group rules make managing EC2 instance access much more difficult.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the AWS Management Console.
-
Select the “Services” option and search for EC2.
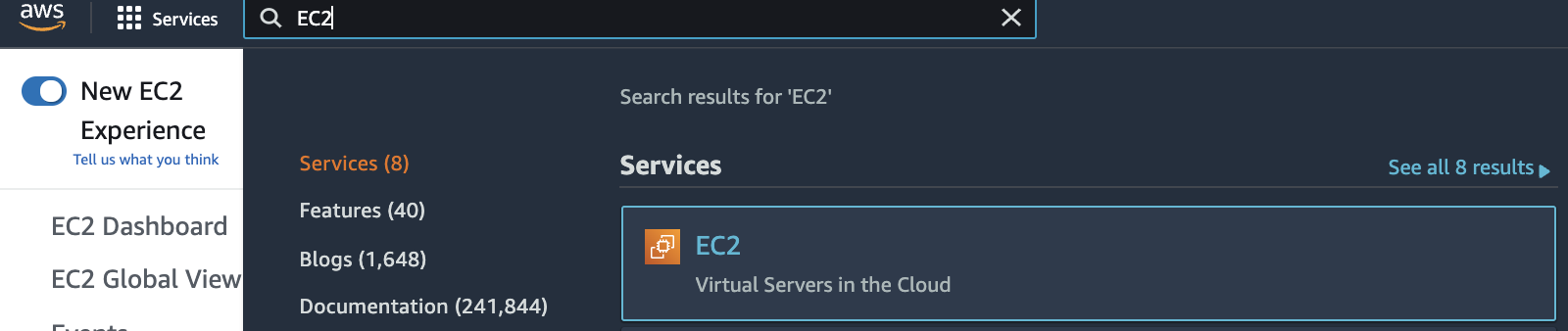
-
Scroll down the left navigation panel and choose “Security Groups” under “Network & Security”.
-
Select the “Security Group” that needs to be verified and scroll down and click on the “Details” tab and copy “Security group ID”.
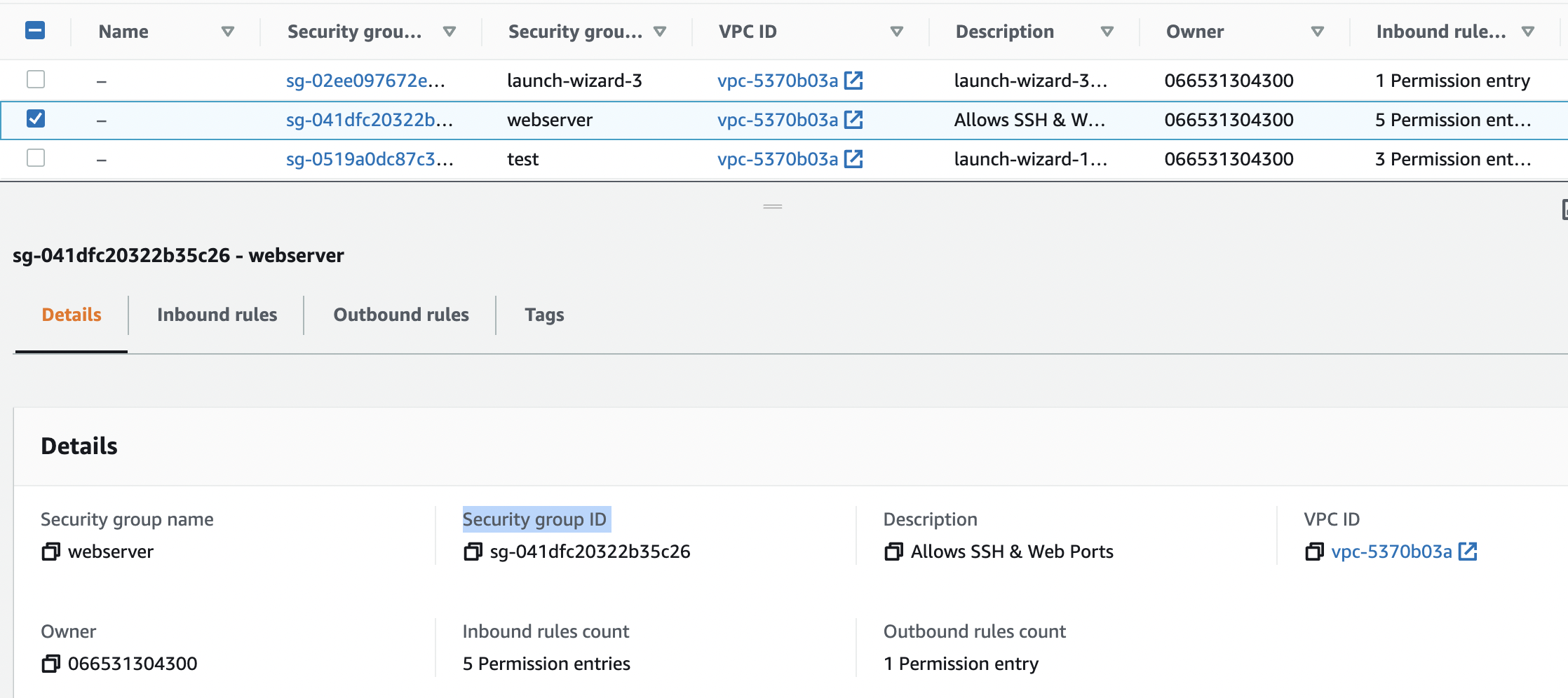
-
Scroll down the left navigation panel and choose “Instances” and search the copied “Security Group ID” copied above.
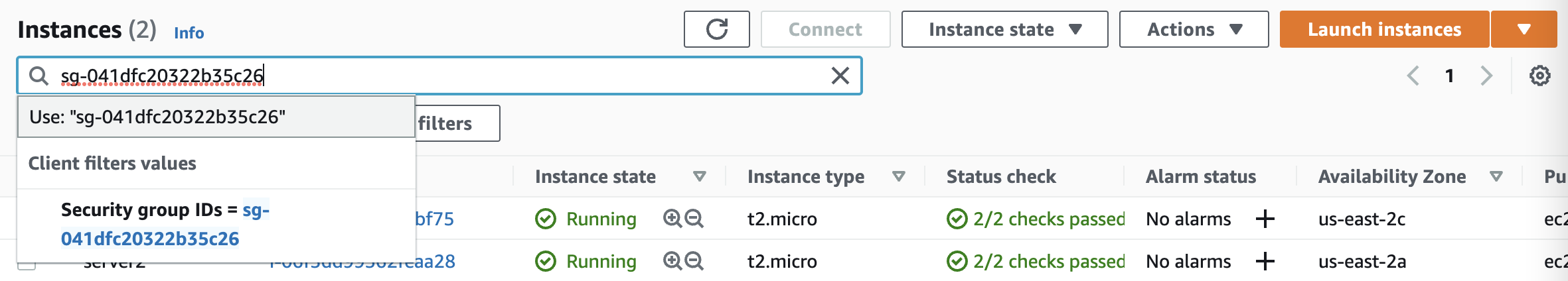
-
Check the number of “EC2 Instance(s)” using the Security Group and if there are more than 1 instances sharing the same “Security Group” then it’s not according to the standard practice of AWS.
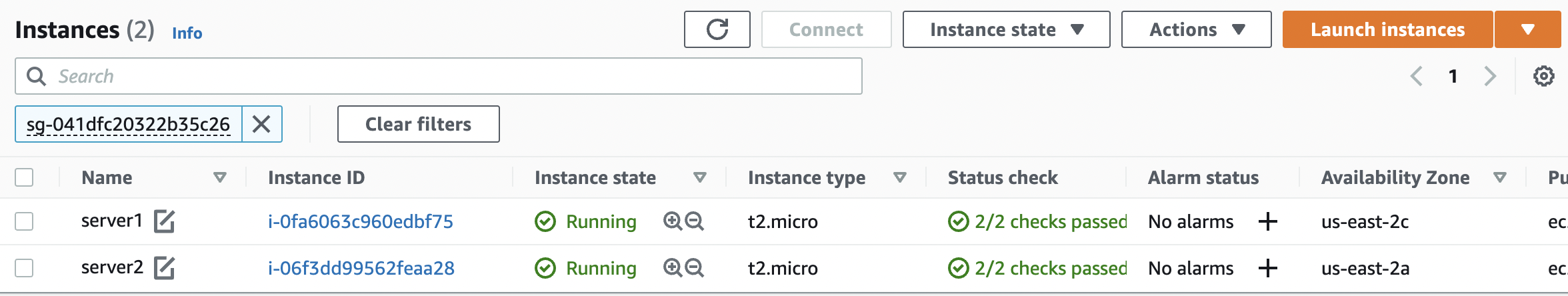
-
Repeat steps number 2 - 6 to verify other “EC2 Instances” using same “Security Group”.
-
Navigate to “Security Group” under “Network & Security” and click on the “Create Security Group” at the top.
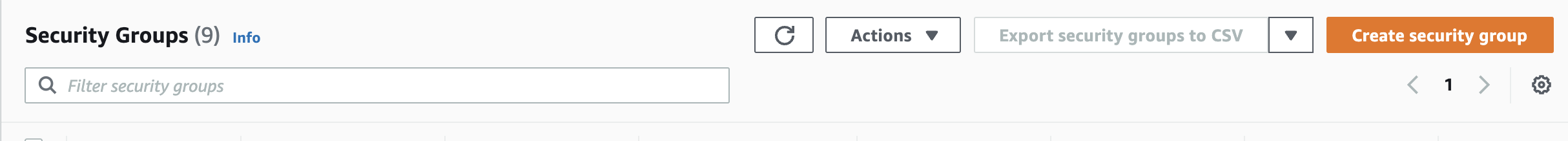
-
On the “Create Security Group” panel provide a “Security Group Name” and “Description” for the new “Security Group”.Select the “VPC” to which “Security Group” belongs.
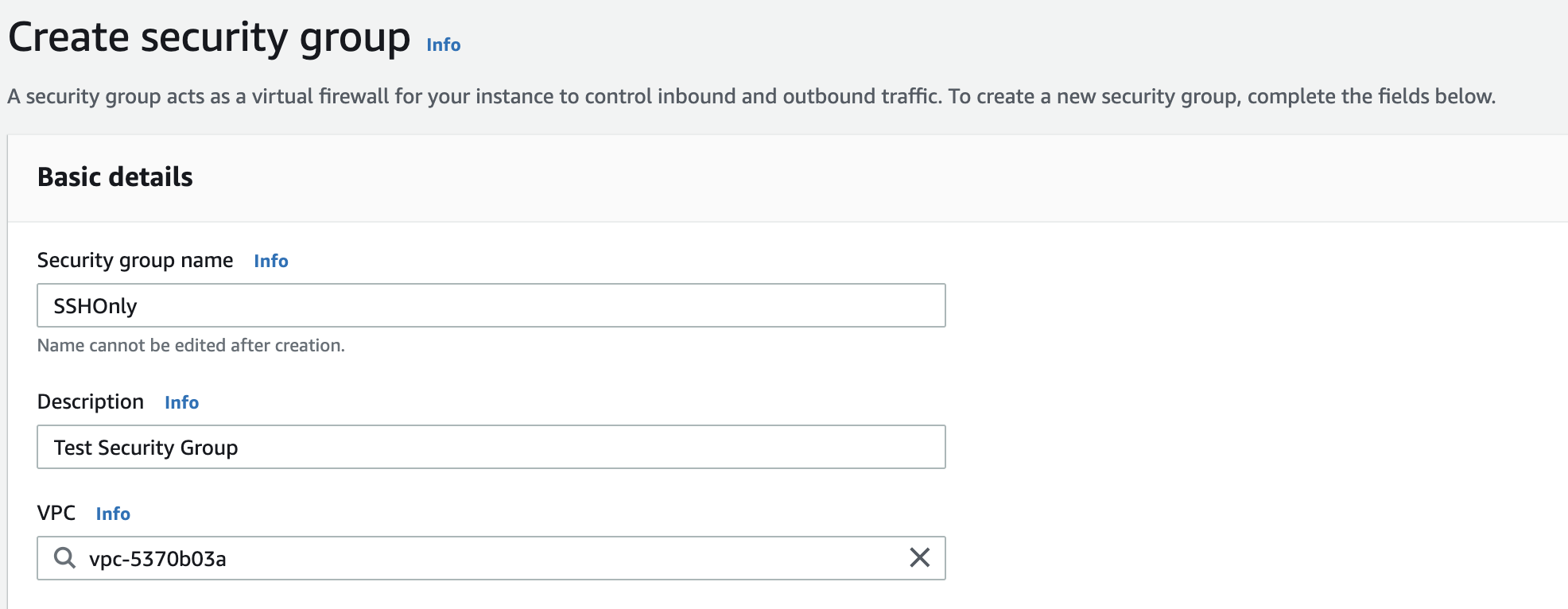
-
Select the “Inbound Traffic Rules” by clicking on the “Add Rule” button and select the “Protocols” as per the requirement.
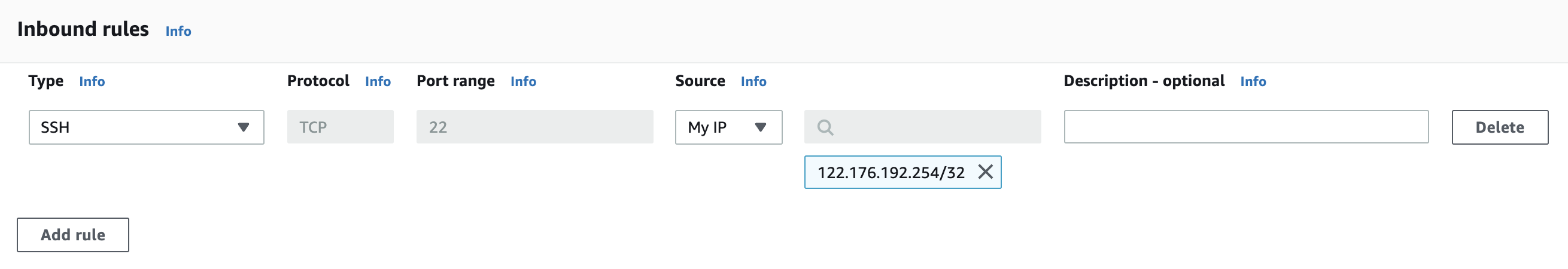
-
Click on the “Create security group” button at the bottom to create a new “Security Group”.
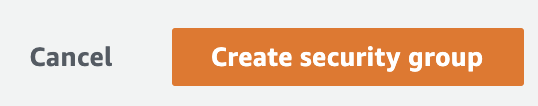
-
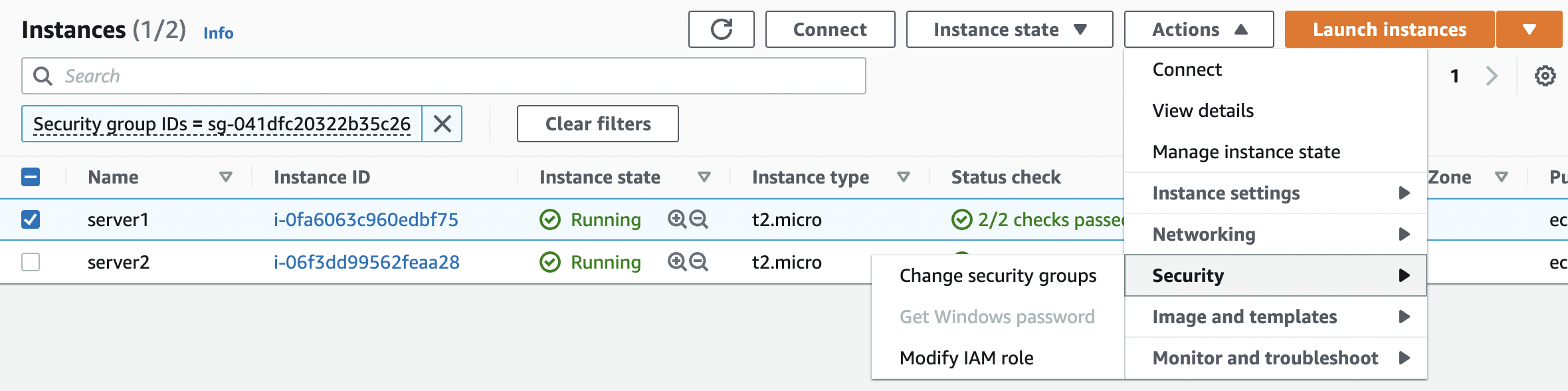
Navigate to “Instances” in the left panel and select the “Instance(s)” which are sharing the same “Security Group”. Click on the “Actions” button at the top and click on the “Change security groups” under “Security”.
-
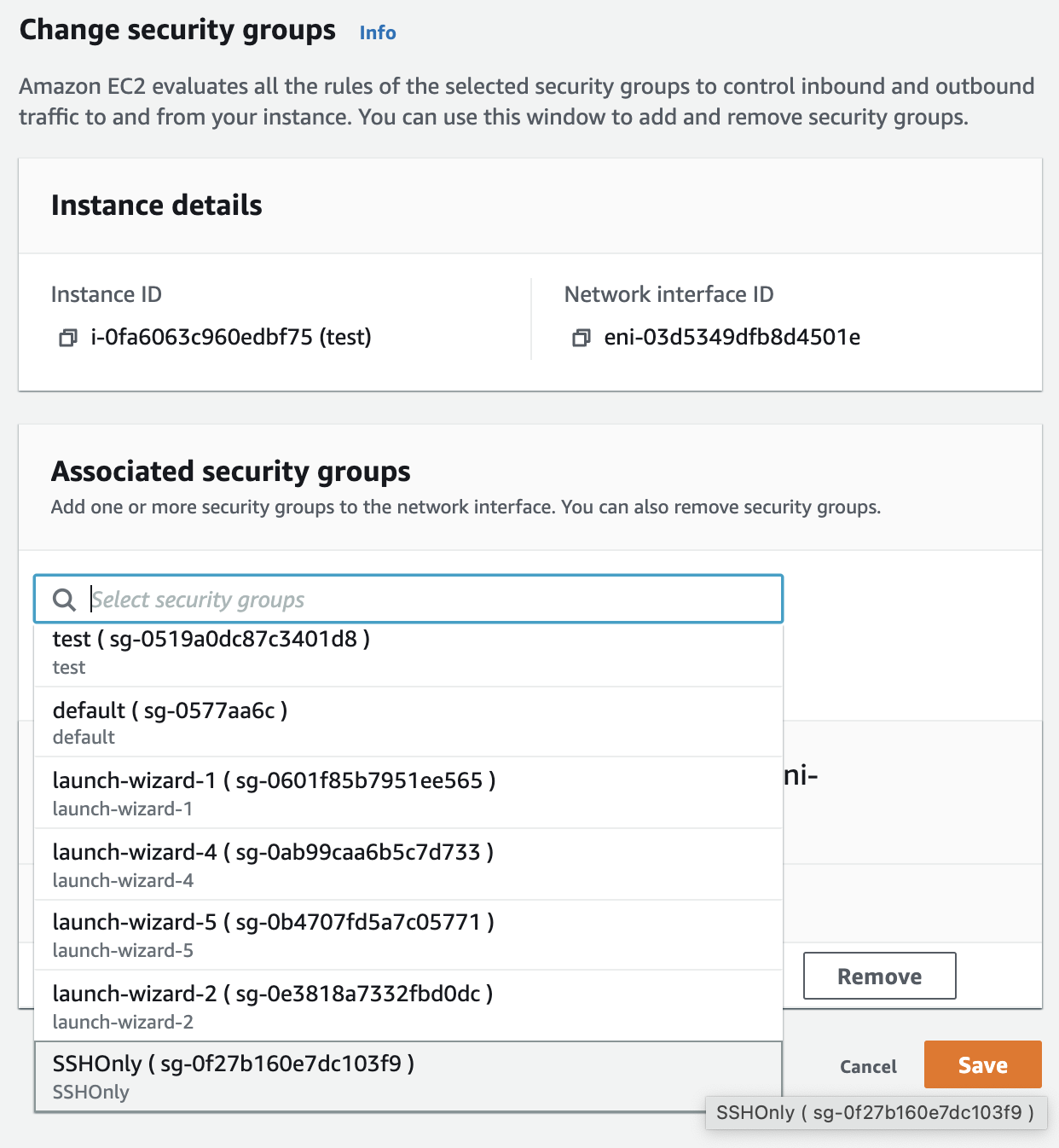
On the “Change Security Groups” tab select the new “Security Group” under “Associated security groups” and click on “Add security group” button.
-
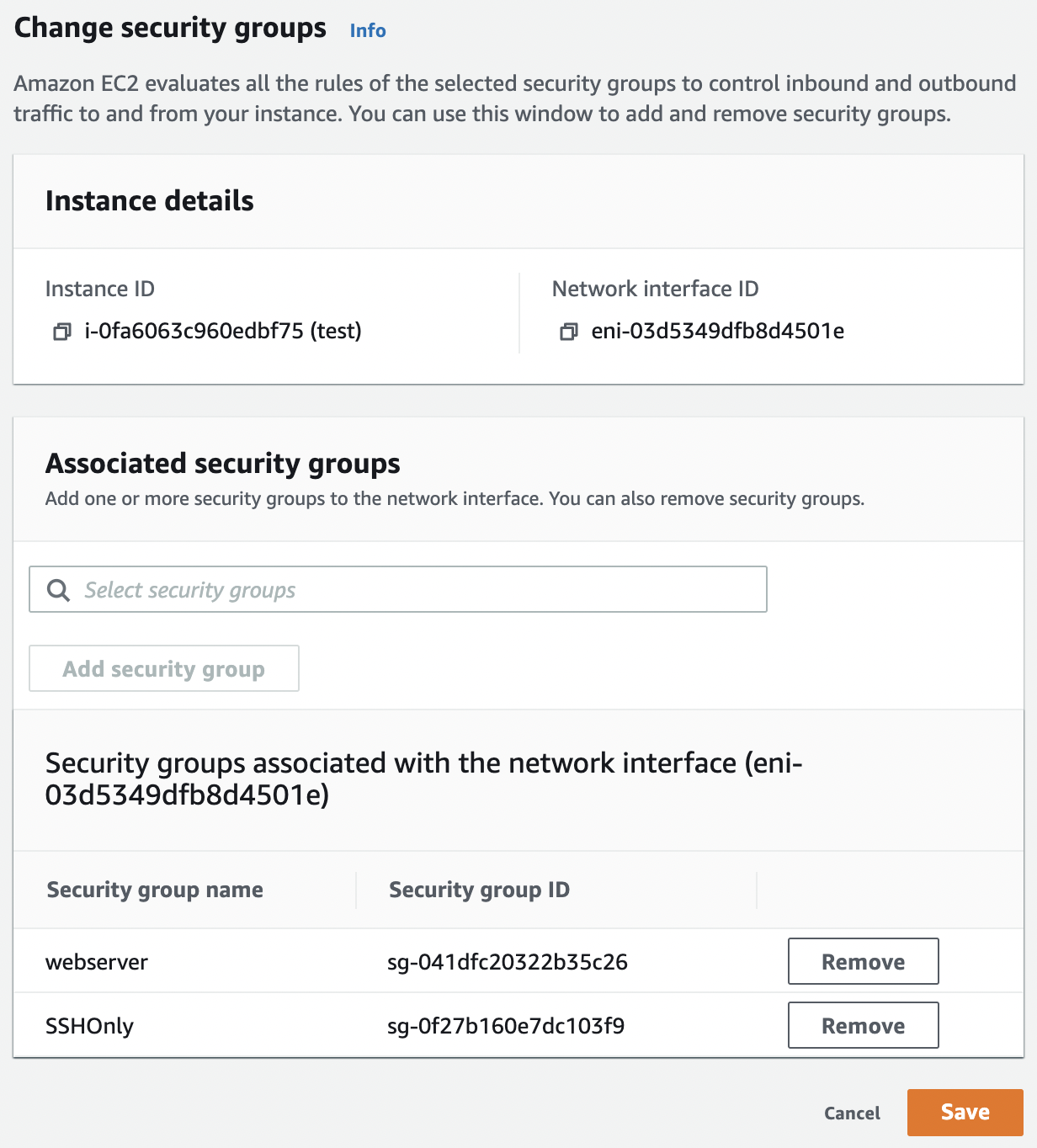
Click on the “Save” button to assign the selected “Security Group” to the “EC2 Instance”.
-
Remove any security group which may not be needed as required from the instance.
-
Repeat steps number 8 - 15 to structure security groups and to avoid their overlapping in “EC2 Instances”.