Empty Groups
Ensures all groups have at least one member
While having empty groups does not present a direct security risk, it does broaden the management landscape which could potentially introduce risks in the future.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the AWS Management Console.
-
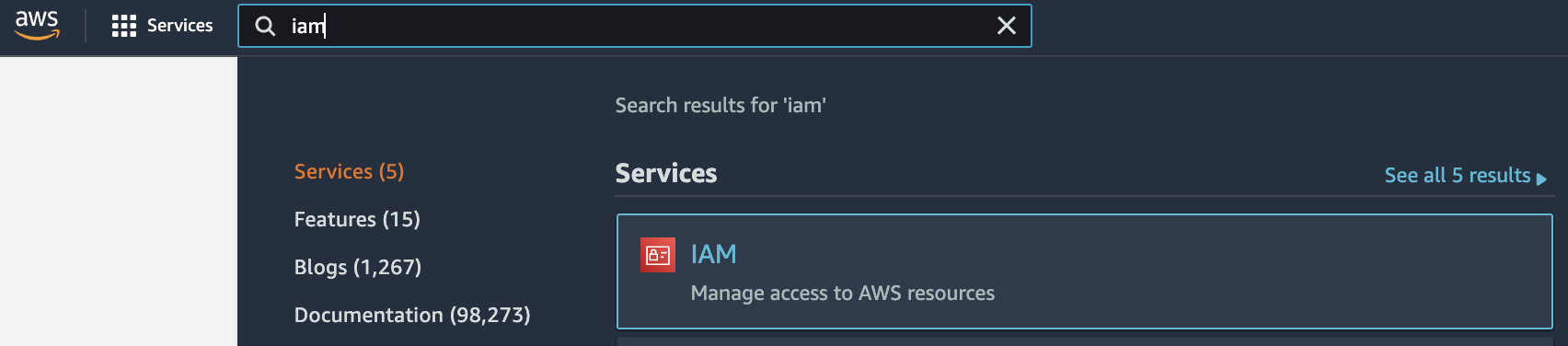
Select the “Services” option and search for IAM.
-
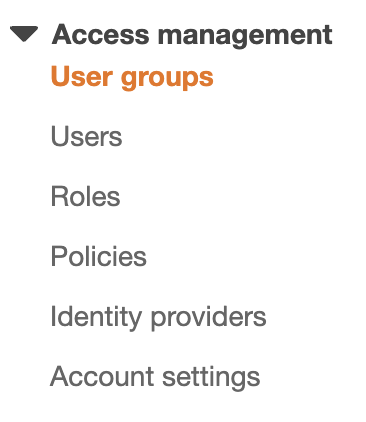
Scroll down the left navigation panel and choose “User Groups” under “Access management”.
-
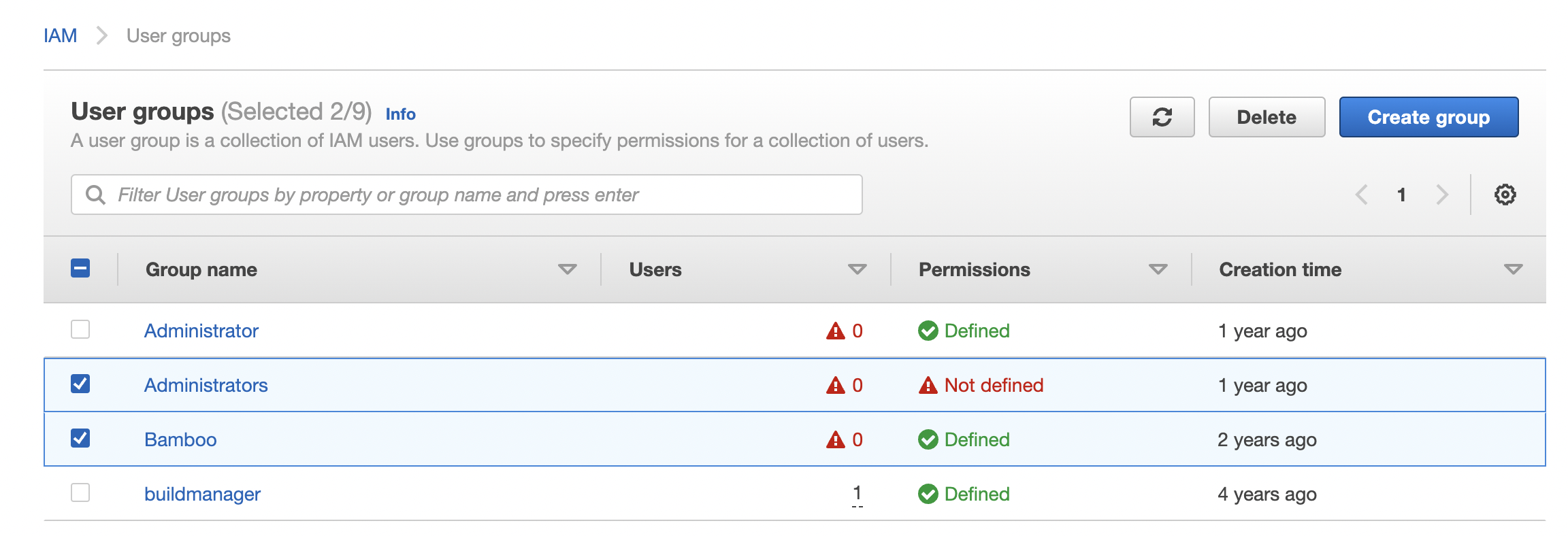
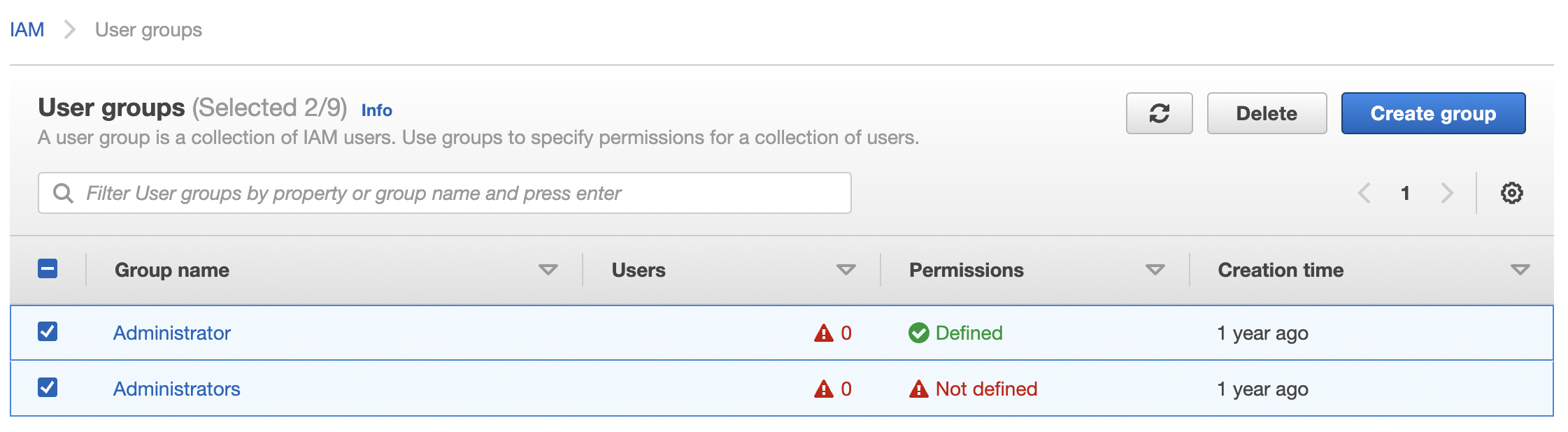
Under the “User Groups” configuration panel check the “Users” column. If the “Users” column won’t have any user make sure to delete that “Group” as it can potentially increase risks in the future. Select the “Groups” with no user.
-
Click on the “Delete” button at the top right to delete the selected “User Groups”.
-
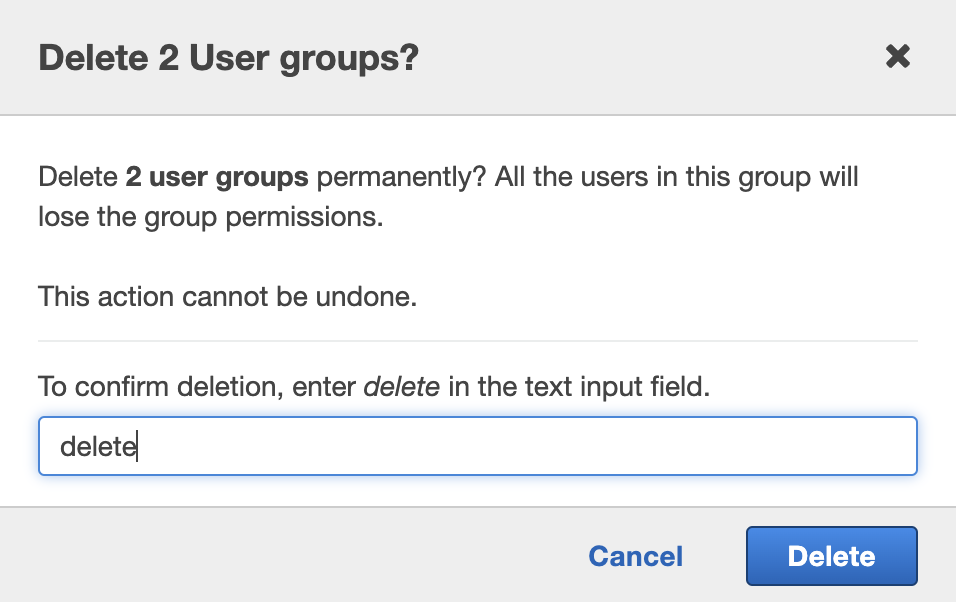
In the “Delete User groups” pop up type “delete” in the text box and click “Delete” button to delete the selected “Group”.
-
Repeat steps number 3 and 6 to verify other “Groups” with at least one user.