SSH Keys Rotated
Ensures SSH keys are not older than 180 days in order to reduce accidental exposures
SSH keys should be rotated frequently to avoid having them accidentally exposed.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the AWS Management Console.
-
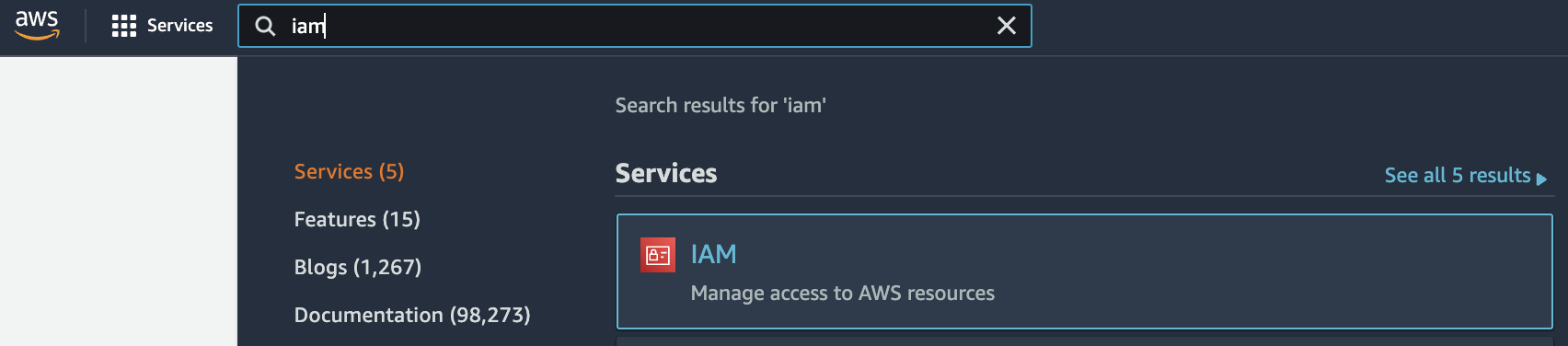
Select the “Services” option and search for IAM.
-
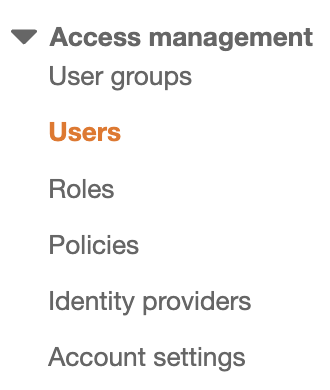
Scroll down the left navigation panel and choose “Users”.
-
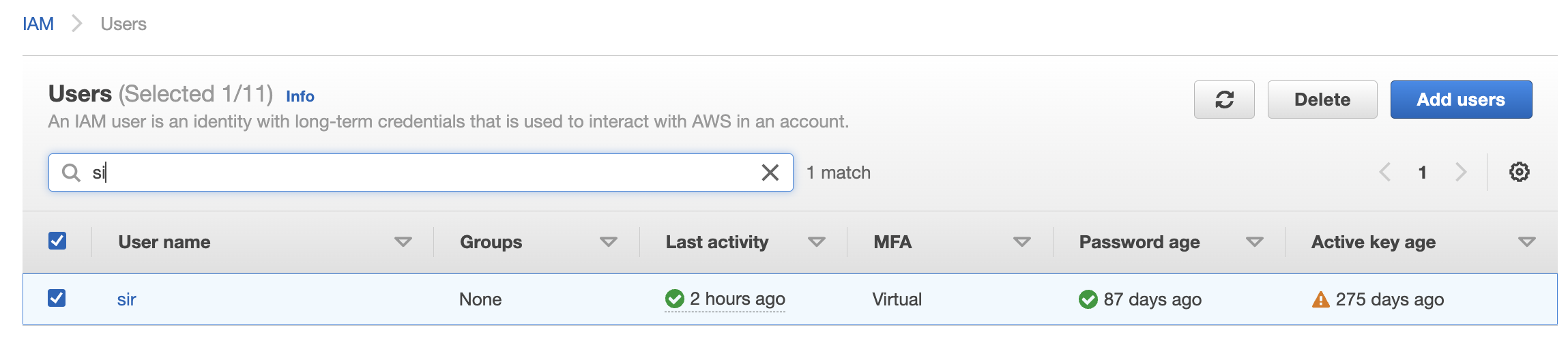
Select the “User” that needs to be verified and click on the “User name” to access the selected “IAM User”.
-
Click on the “Security Credentials” under the configuration page.
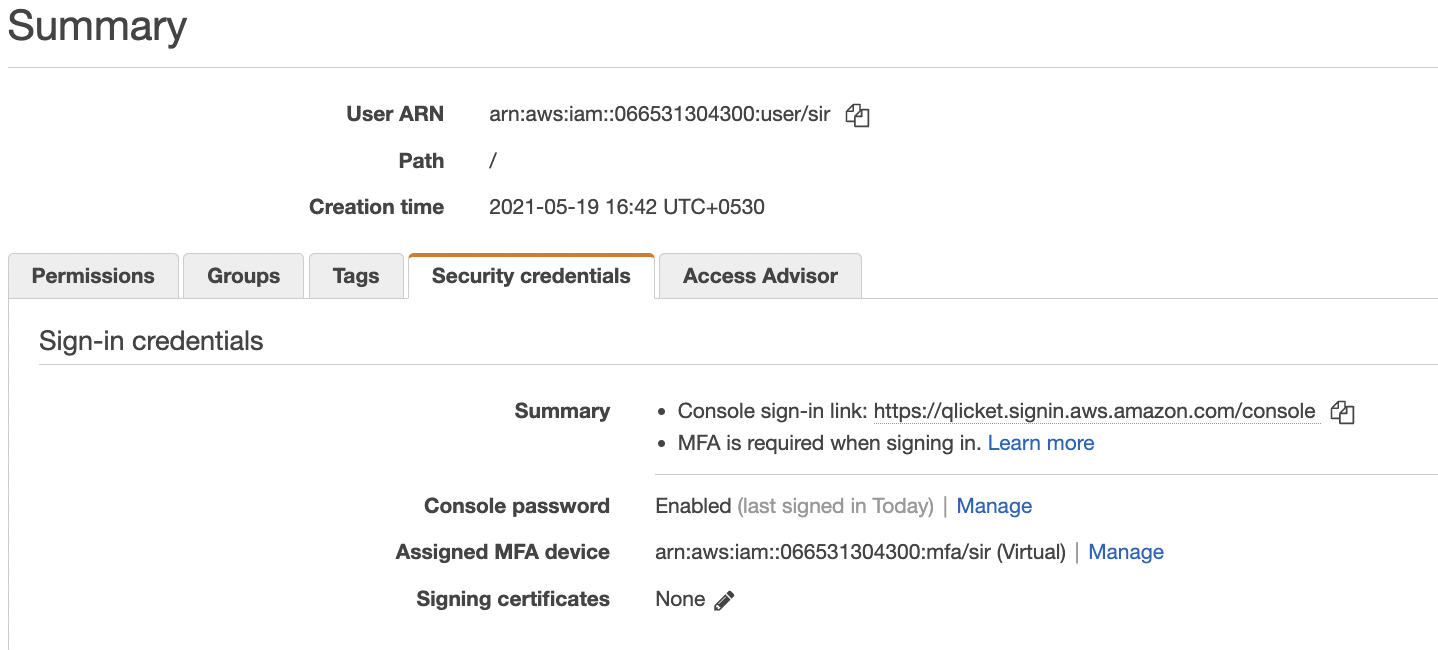
-
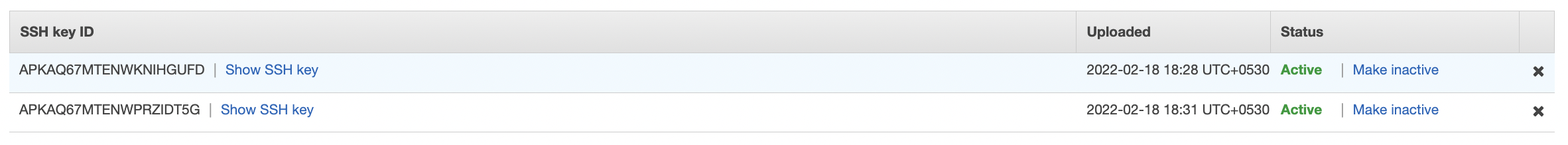
Scroll down the “Security Credentials” tab and check the “SSH keys for AWS CodeCommit” section. Check the “Uploaded” column and if any SSH key is older than 180 days than that SSH key is outdated and needs to be changed.
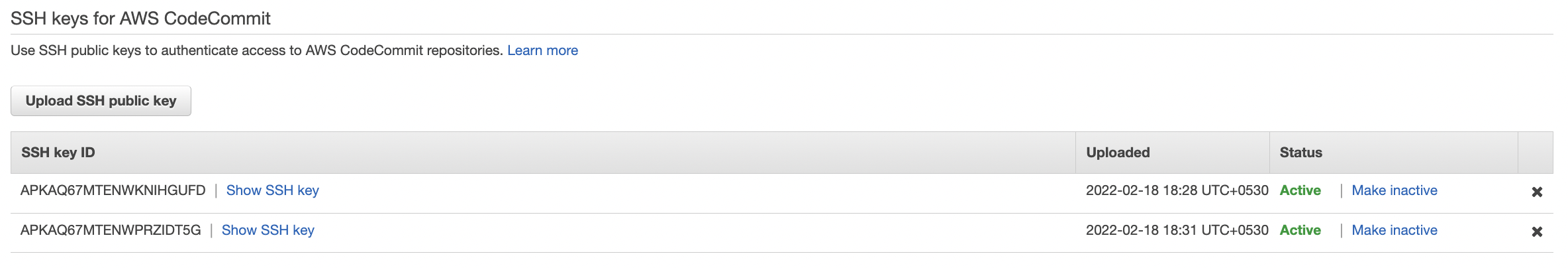
-
Repeat steps number 3 - 6 to verify any other IAM user.
-
To update the SSH key scroll down the “Security Credentials” tab and check the “SSH keys for AWS CodeCommit” section. Click on “Upload SSH public key” button to upload the new SSH key.
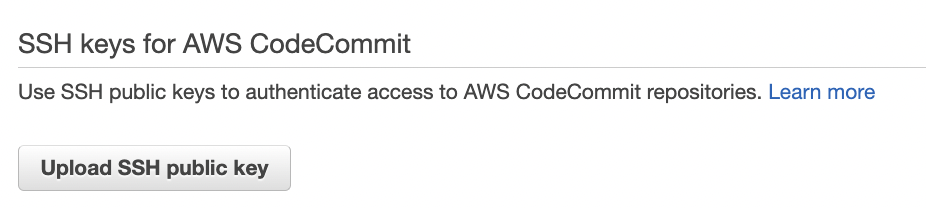
-
In the “Upload SSH public key” tab upload the new SSH key and click on the “Upload SSH public key” button.
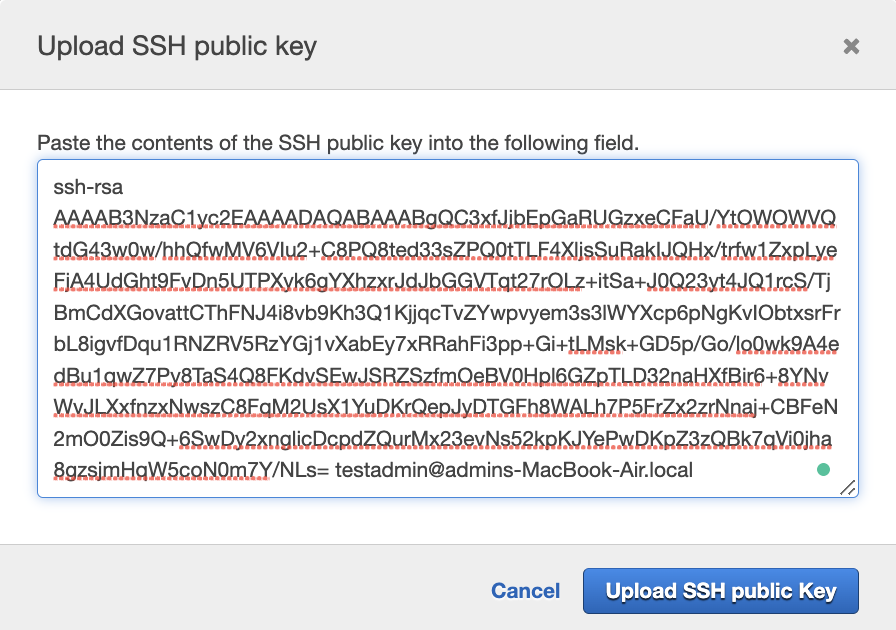
-
Use the new “SSH key” for AWS CodeCommit repositories and replace the older key with the new one. Make sure that the new “Access key” pair is working fine.
-
To remove the older “SSH key” once you verified that the new “SSH key” is working fine click on “Security Credentials” under IAM user configuration page and select the older “SSH key ID” which needs to be removed.
-
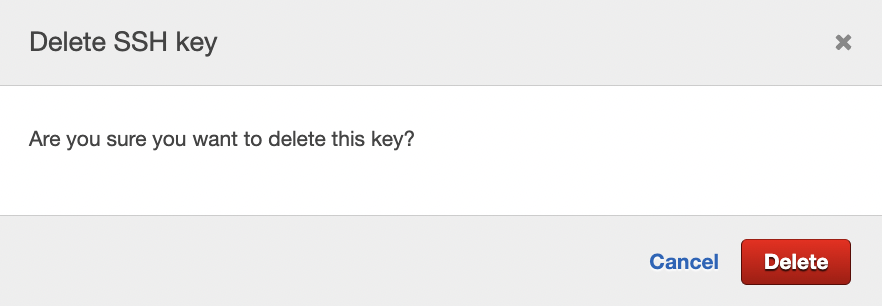
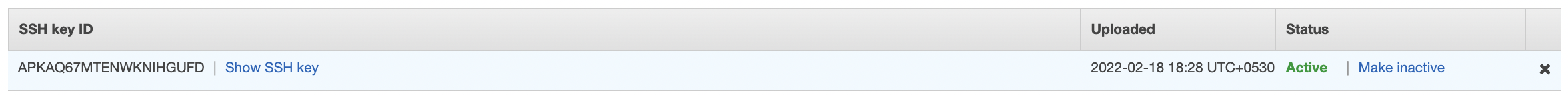
Click on the cross(×) symbol at the extreme right to remove the selected key.
-
Click on “Delete” button under the “Delete SSH key” tab to delete the older “SSH Key”.