Users Password And Keys
Detects whether users with a console password are also using access keys
Access keys should only be assigned to machine users and should not be used for accounts that have console password access.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the AWS Management Console.
-
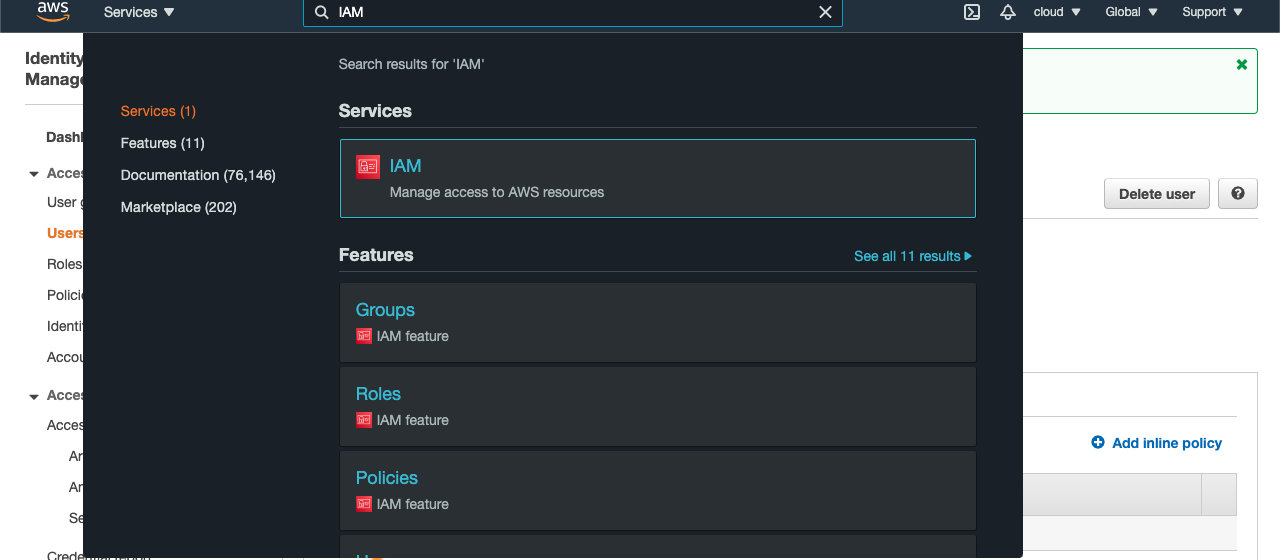
Select the “Services” option and search for IAM.
-
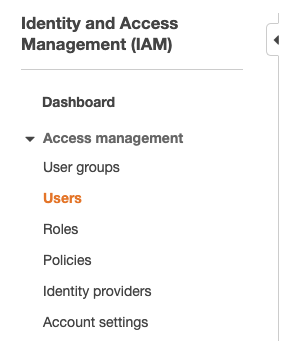
Scroll down the left navigation panel and choose “Users”.
-
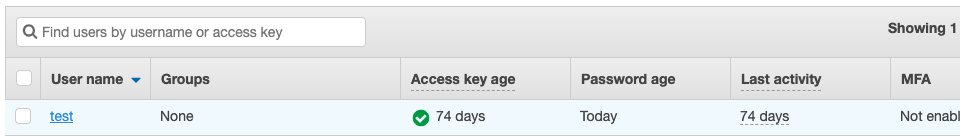
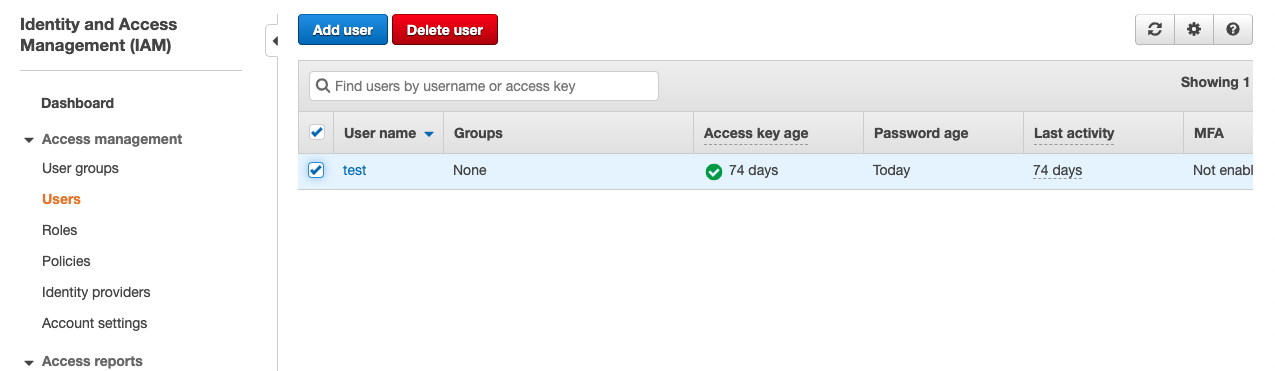
On the “Users” page, click on the “User” in the “User name” column.
-
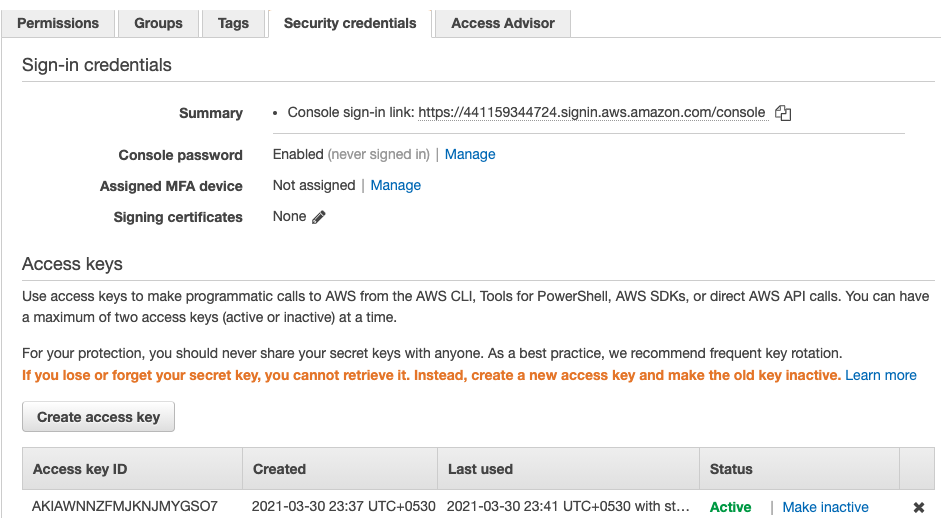
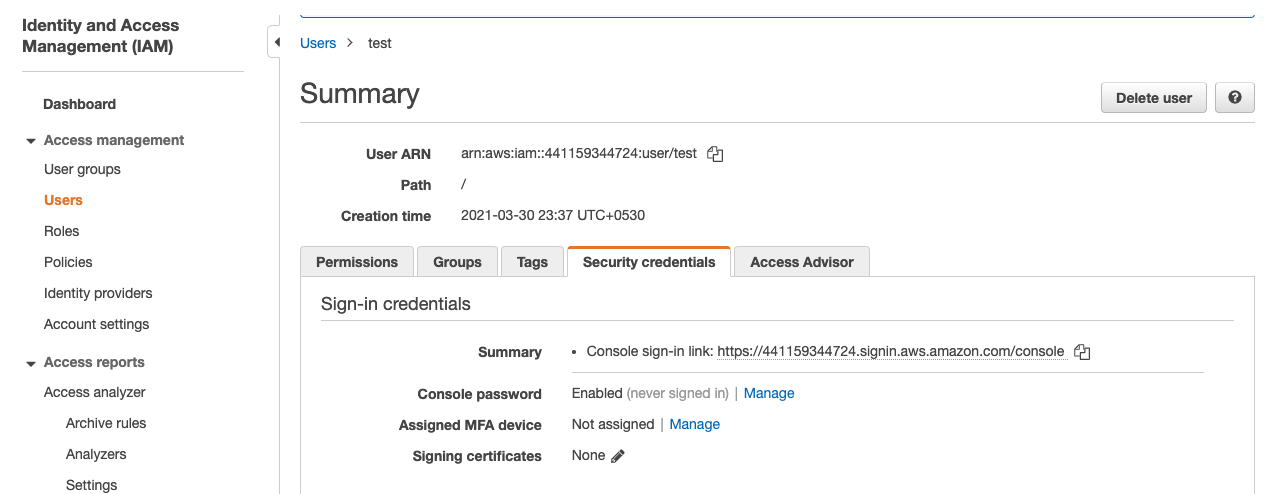
In the “Users - Summary” page, click on the Security Credentials to check whether the selected user have Console access and Access Keys as well.
-
Repeat steps number 2 - 5 to check other users in the account.
-
Navigate to IAM dashboard at https://console.aws.amazon.com/iam/.
-
In the “IAM dashboard”, click on the “Users” option at the left navigation panel and select the user who have Access key and Console access both.
-
In the “users - Summary” page, click on the Security Credentials to remove the “Access key” from the selected user.
-
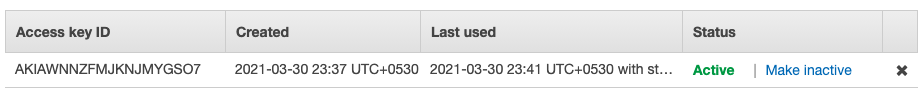
In the “Security Credential” page, scroll down and click on the (x) button under the Access Keys to remove the access key.
-
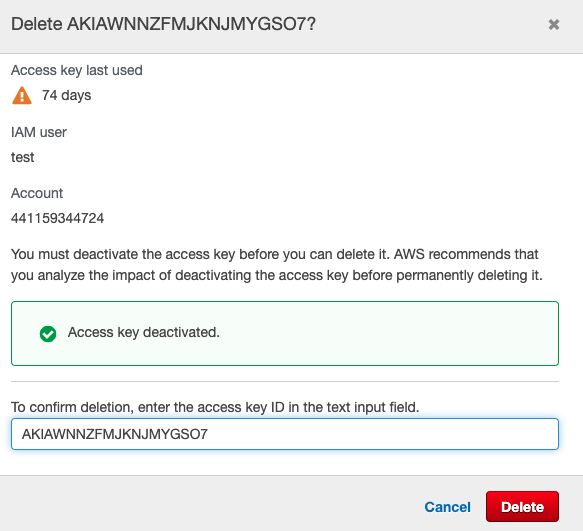
On the “Delete” tab, first click on “Deactivate” the key and then provide the Key Attribute and click on the “Delete” button.
-
Repeat steps number 7 - 11 to remove access keys from all users with console access.