Kinesis stream is unencrypted.
Kinesis streams should be encrypted to ensure sensitive data is kept private. Additionally, non-default KMS keys should be used so granularity of access control can be ensured.
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Enable in transit encryption
|
|
-
Log in to the AWS Management Console.
-
Select the “Services” option and search for “Kinesis”.
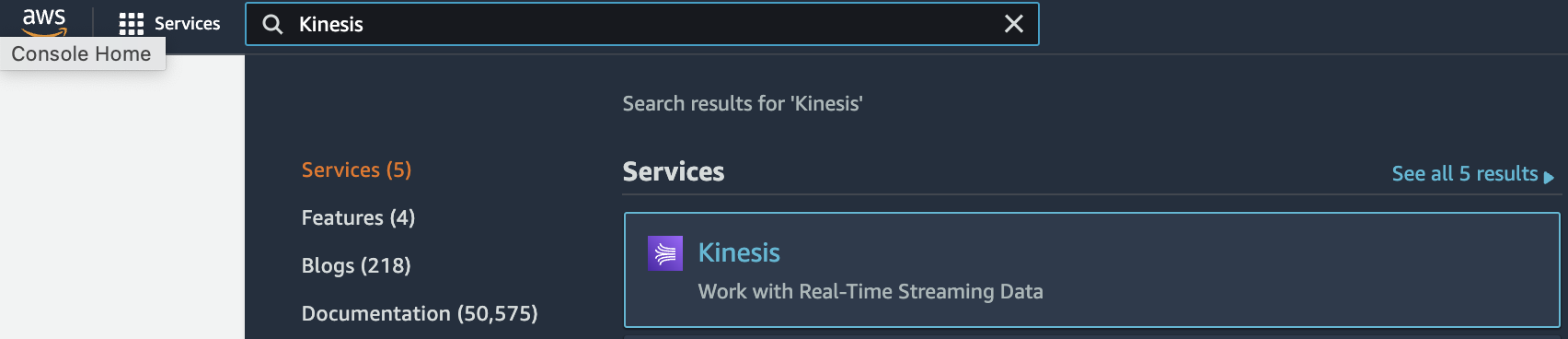
-
Under the “Amazon Kinesis dashboard” choose “Data Firehose” or “Delivery streams” from the left navigation panel.
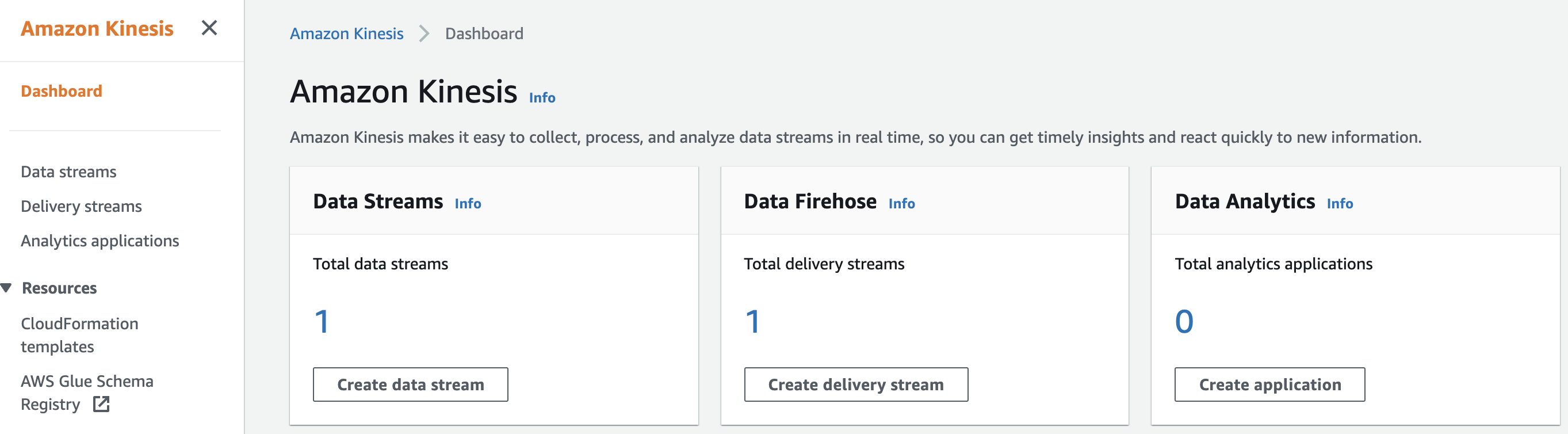
-
Select the “Firehose Delivery System” that needs to be verified and click on the “Name” to access the delivery stream.
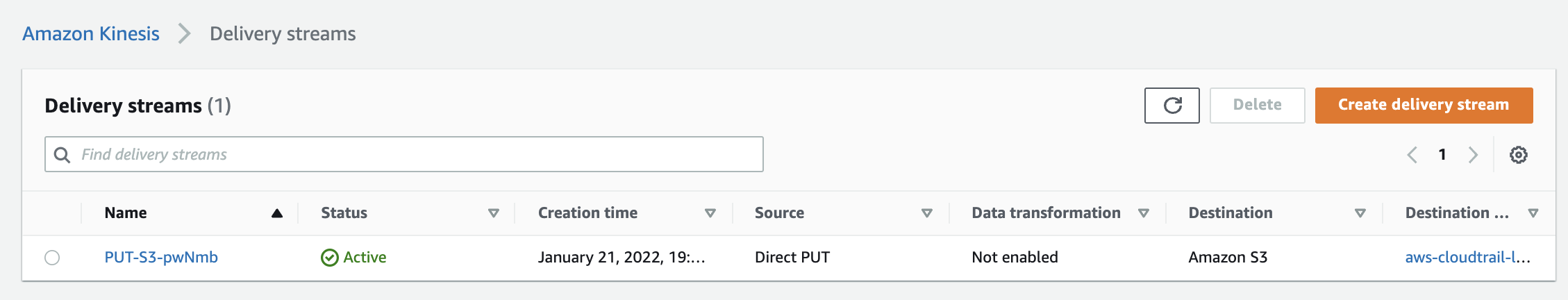
-
Select the “Configuration” tab and scroll down to “Amazon S3 destination”. Click on the S3 bucket link to check the “Encryption” value.
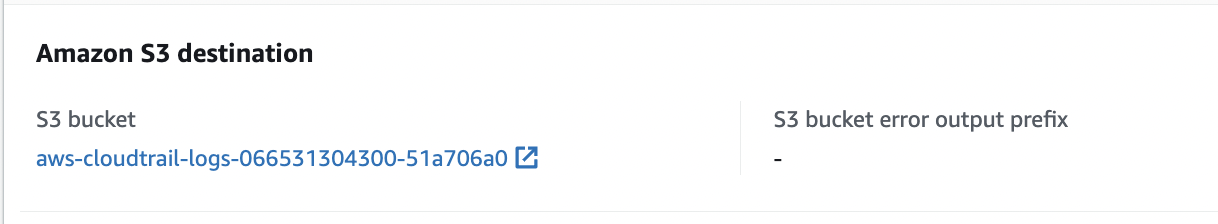
-
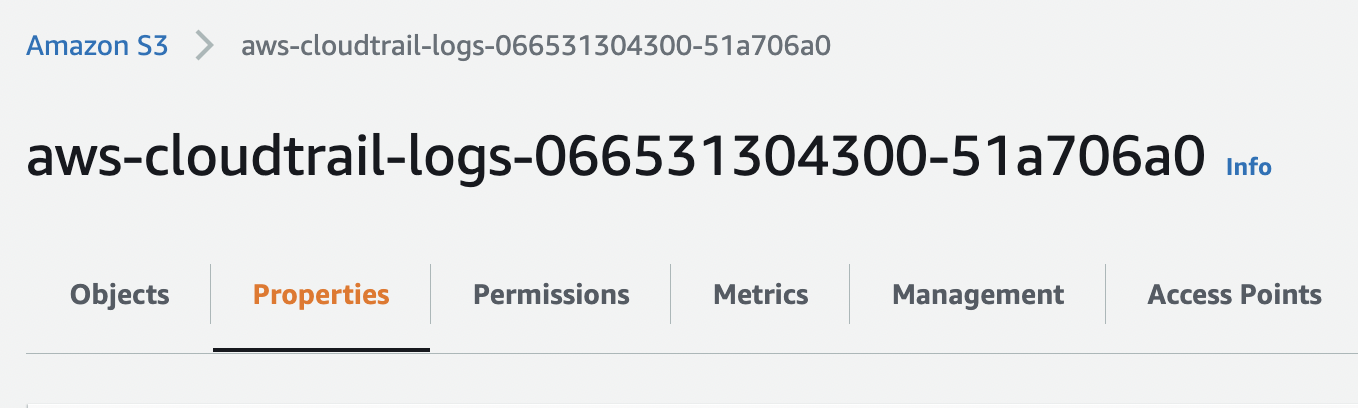
In the Amazon S3 bucket configuration tab that opens, select “Properties” tab.
-
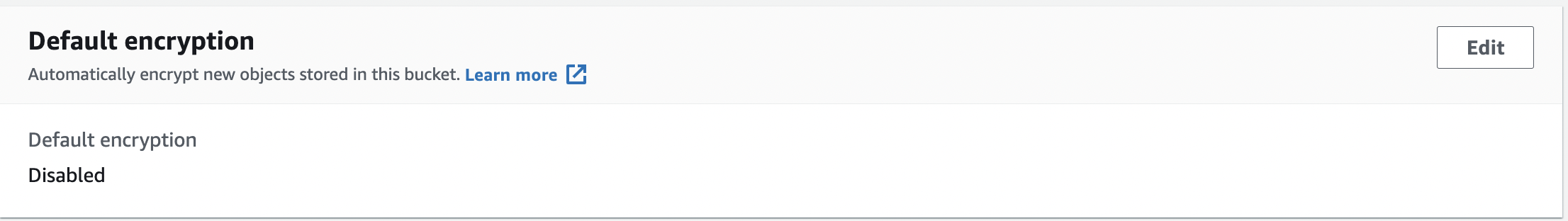
Scroll down to “Default encryption”, and if it’s set to “Disabled” then the selected “Firehose Delivery System” data is not encrypted.
-
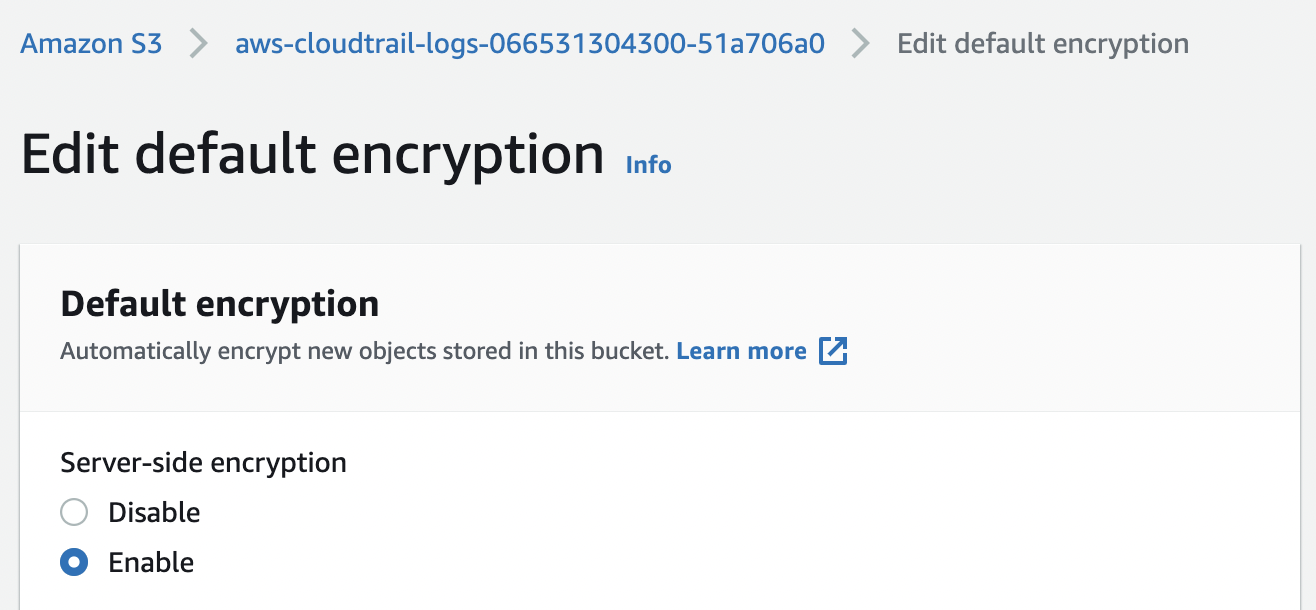
Click “Edit” and on the “Edit default encryption” page select “Enable”.
-
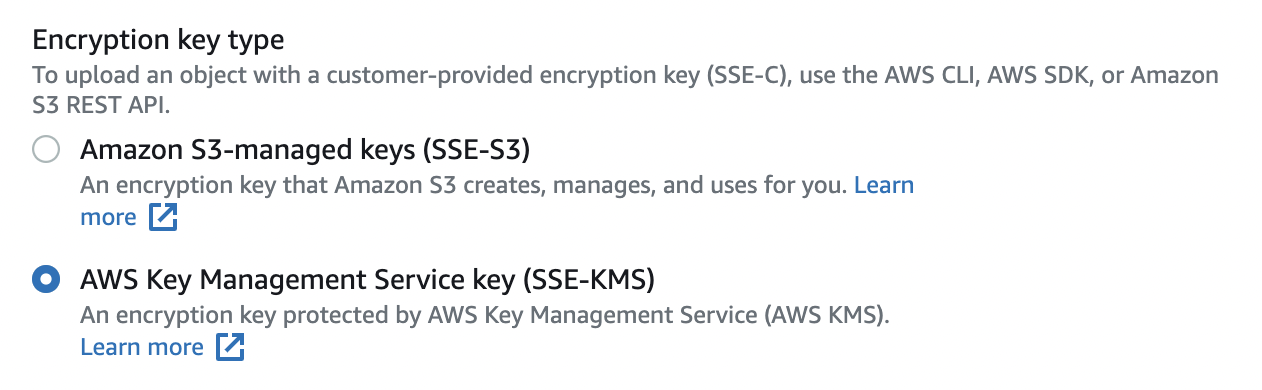
Under the “Encryption key type” select “AWS Key Management Service key (SSE-KMS)”.
-
In the “AWS KMS key” section select option “Choose from your AWS KMS keys” and in the “AWS KMS key” select your key from the dropdown.
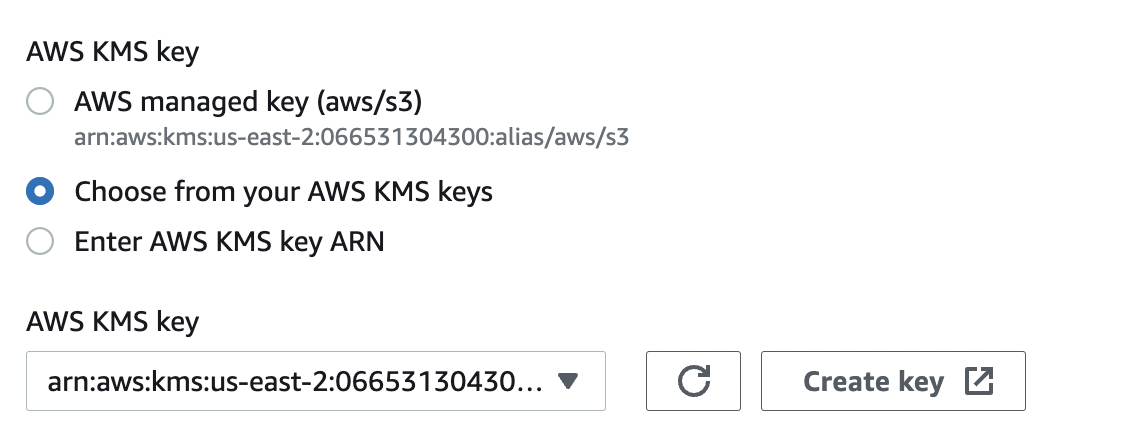
-
Select the “Enable” option under “Bucket Key” and click on “Save changes” to enable the encryption.
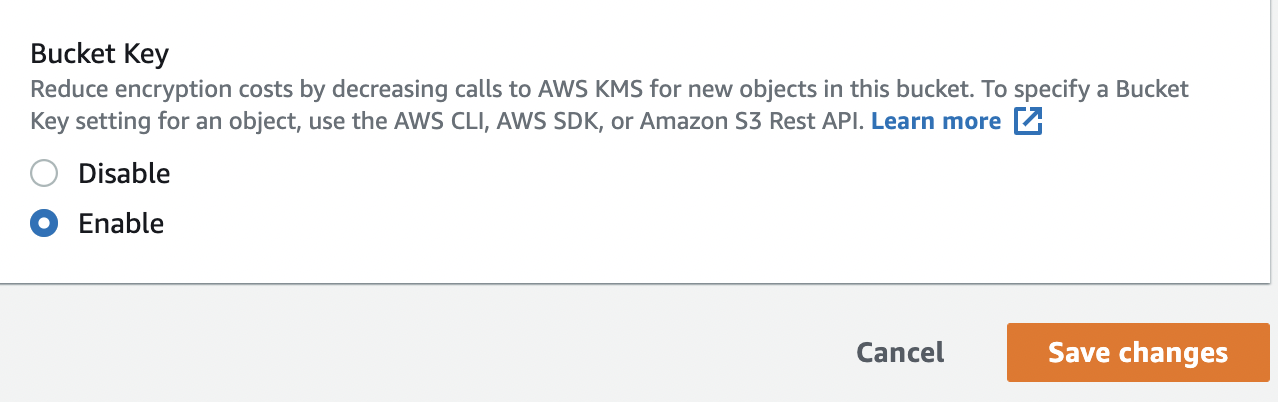
-
On the successful configuration changes, one will get “Successfully edited default encryption” message.
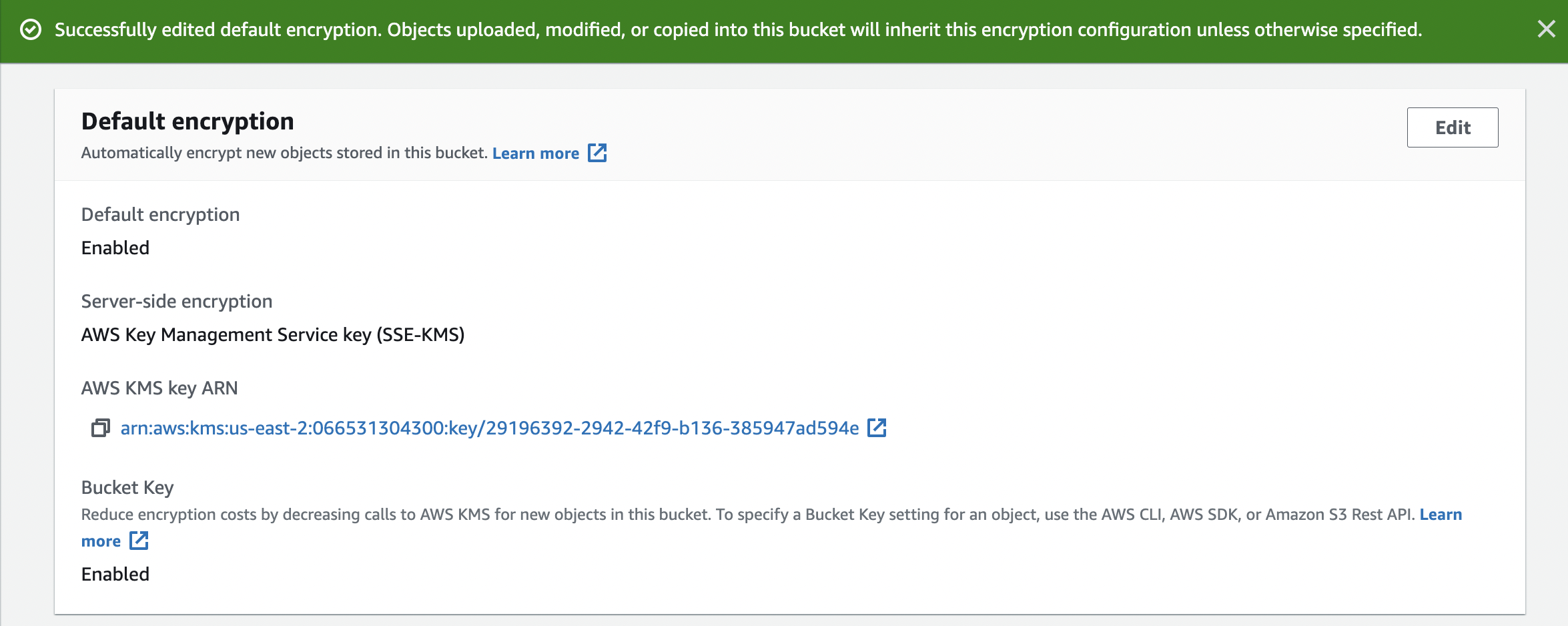
-
Repeat step number 4 and 12 to verify all other “Firehose Delivery System”.