KMS Default Key Usage
Checks AWS services to ensure the default KMS key is not being used
It is recommended not to use the default key to avoid encrypting disparate sets of data with the same key. Each application should have its own customer-managed KMS key
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the AWS Management Console.
-
Select the “Services” option and search for KMS.
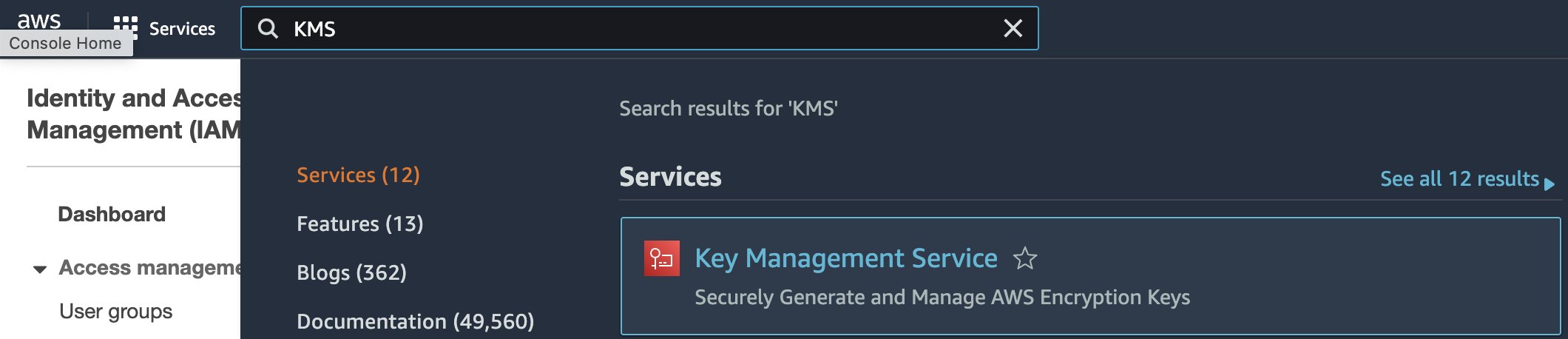
-
Scroll down the left navigation panel and choose “AWS managed keys” under “Key Management Service”.
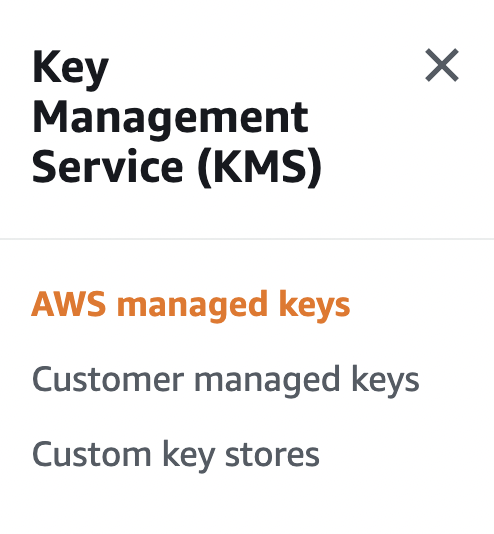
-
Select the “KMS key” that needs to be verified by clicking on the alias of the key under “Alias”.
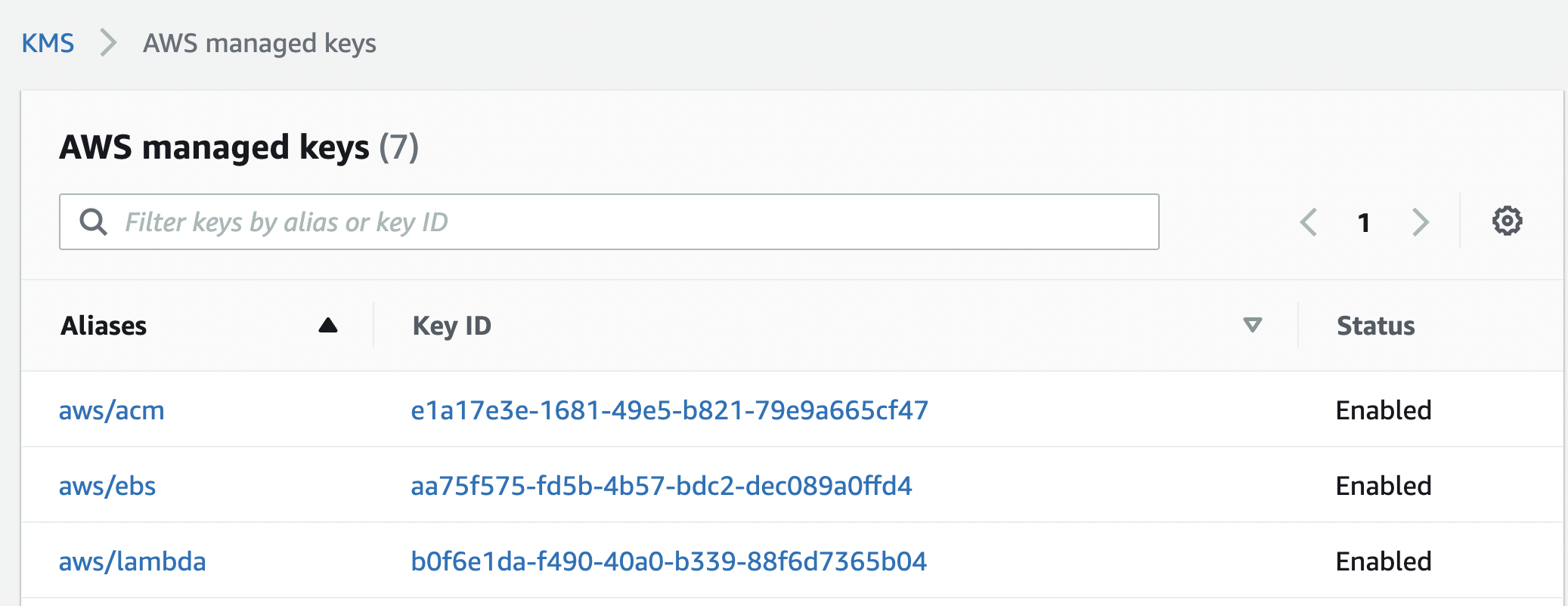
-
On the “AWS managed keys” page verify the “General configuration” and check the “Description” tab. If “Default master key”(for e.g. aws/ebs) is showing then the selected “Amazon KMS key” is a default master key.
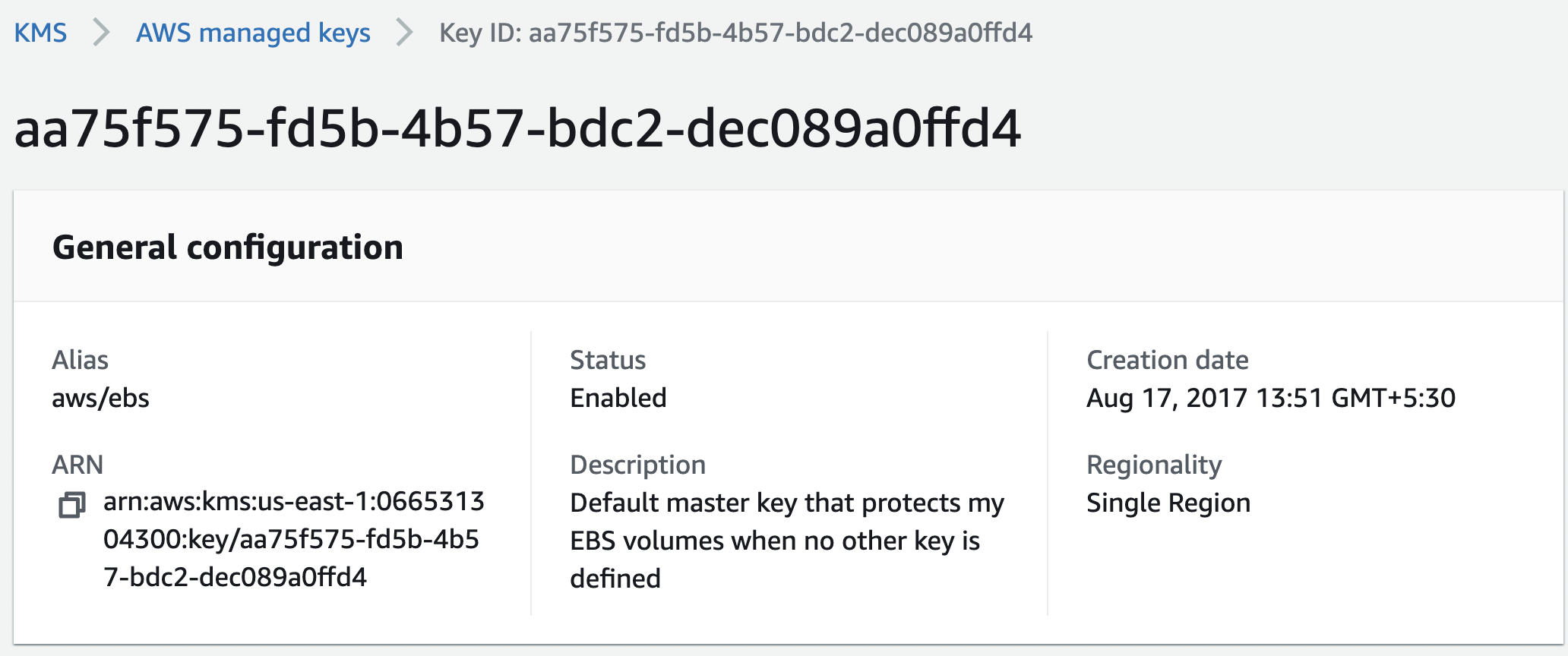
-
Naviagte to the “EC2 dashboard” and select the “Snapshots” under “Elastic Block Store”.

-
Select the “Snapshot” that needs to be verified and check the “Description” tab from the bottom panel. Check the “KMS Key Aliases” and if the value is set to “aws/ebs then the selected EBS volume is using the default master key.
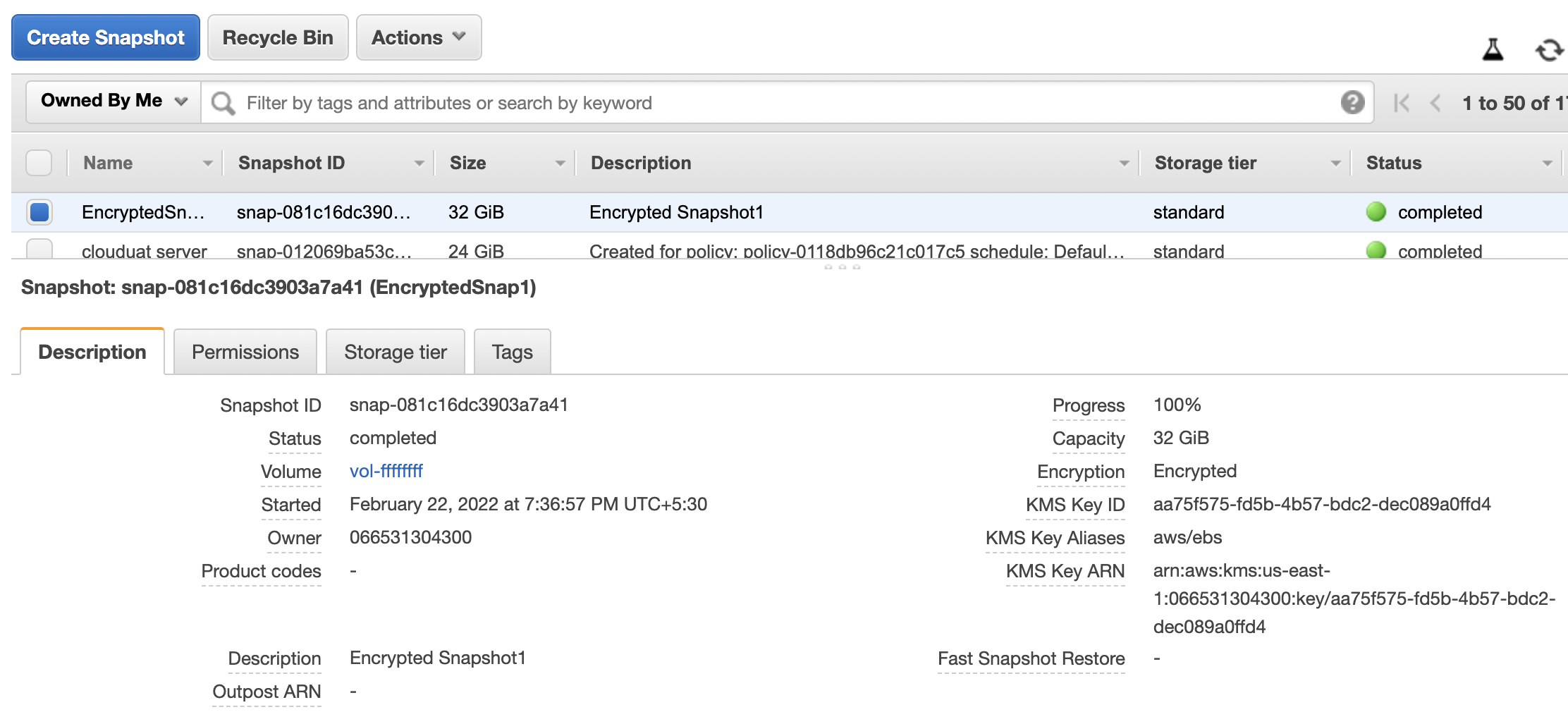
-
Repeat step number 2 - 7 to verify other “KMS Default keys Usage” in the selected region.
-
Navigate to “KMS key” dashbaord and click on the “Create key” button at the top panel to create a new “KMS key”.

-
On the “Configure key” page select key type as “Symmetric”. In the Advanced options select “KMS” in the Key material origin and Regionality as “Single-Region key” and click “Next” button.
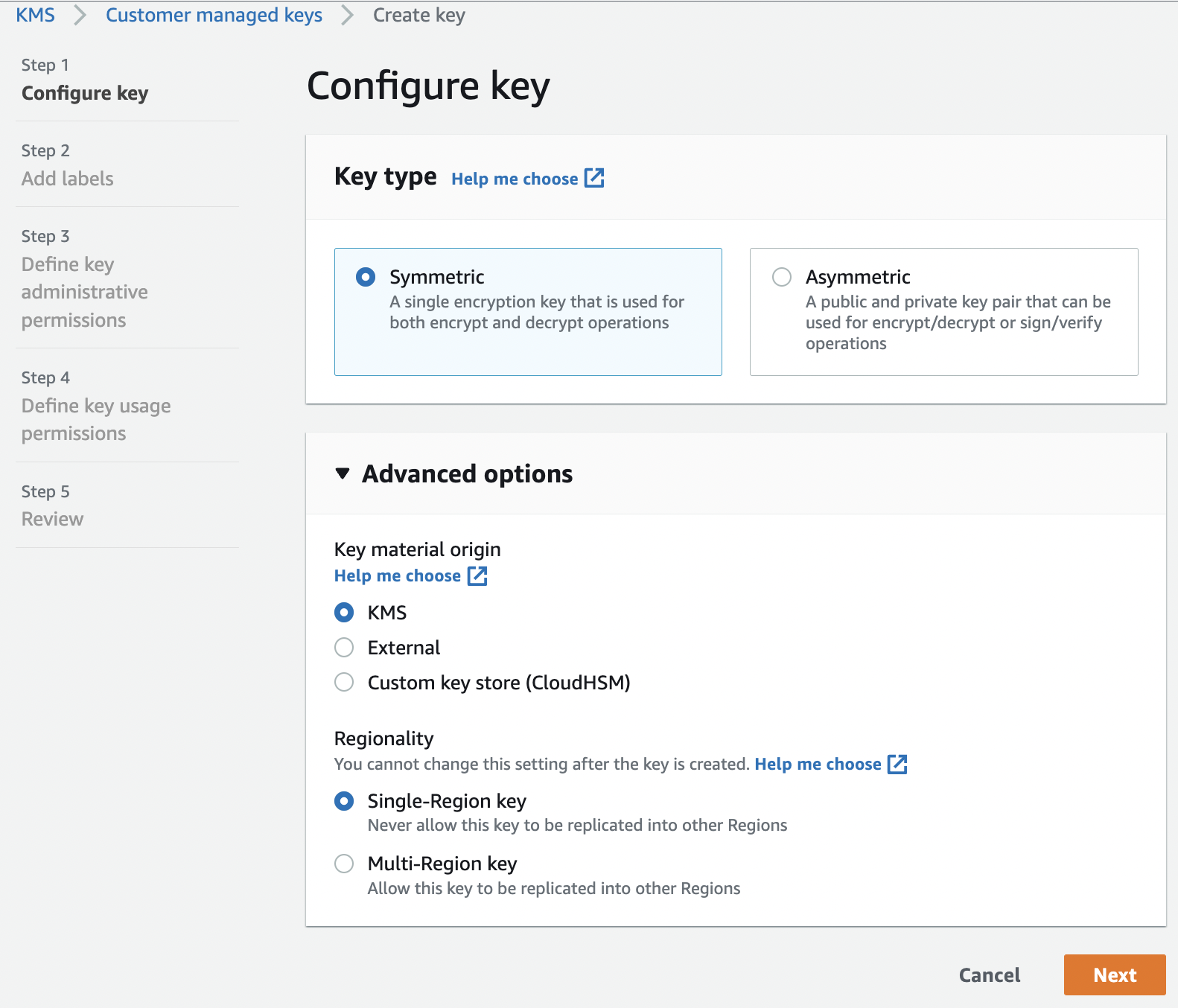
-
On the “Add labels” page add alias and description to provide the “Alias” and “Description” for the new “KMS key” and click on the “Next” button.
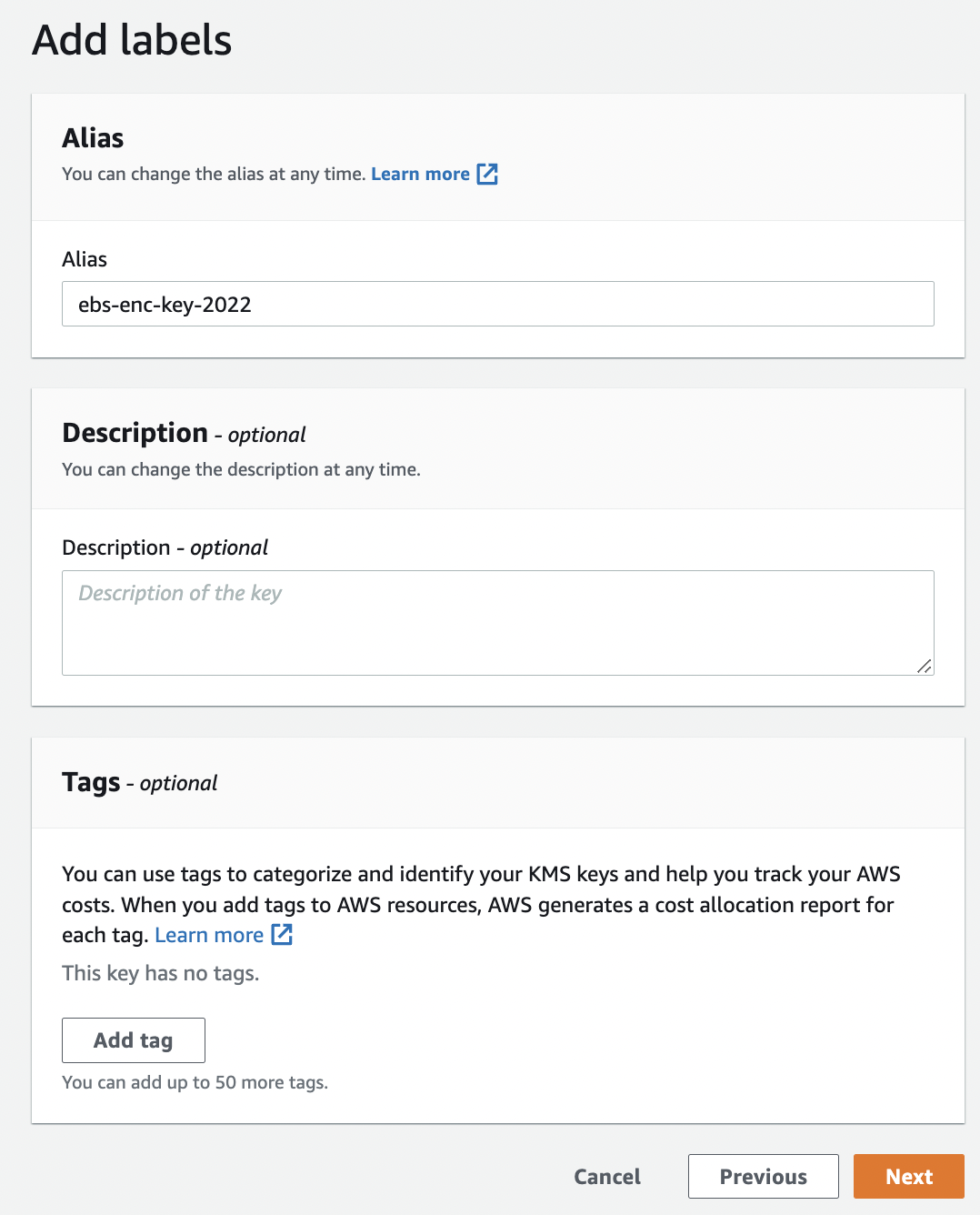
-
On the “Define key administrative permissions” page select the “IAM users” and roles who can administer the new “KMS key” through the KMS API. Click on the “Next” button at the bottom to continue the new “KMS key” process.
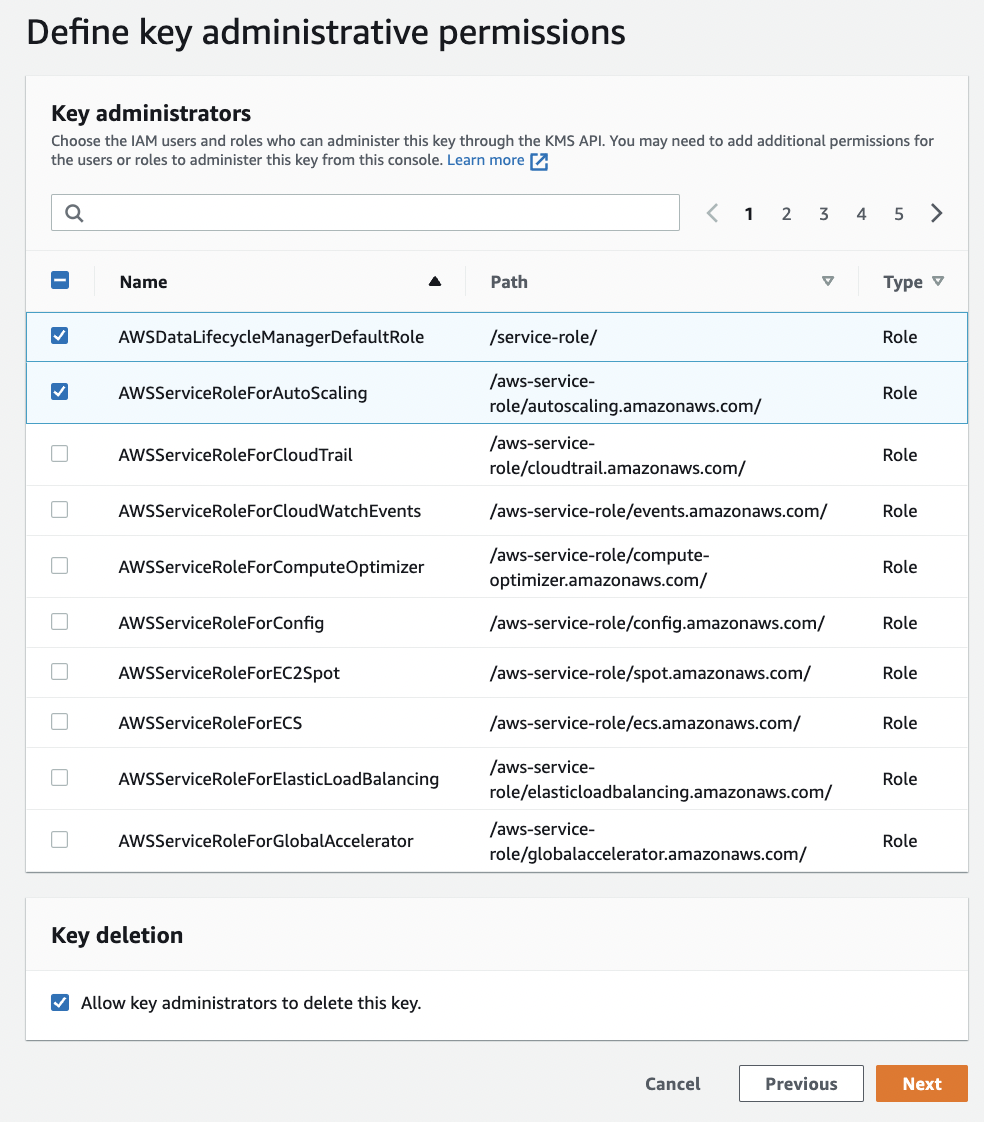
-
On the “Define key usage permissions” page select the IAM users and roles that can use the CMK to encrypt and decrypt data with the “AWS KMS API” and click on the “Next” button.
-
On the “Review and edit key policy” page review the policy and click on the “Finish” button to create a new “KMS key” which can be used to encrypt/decrypt the data.
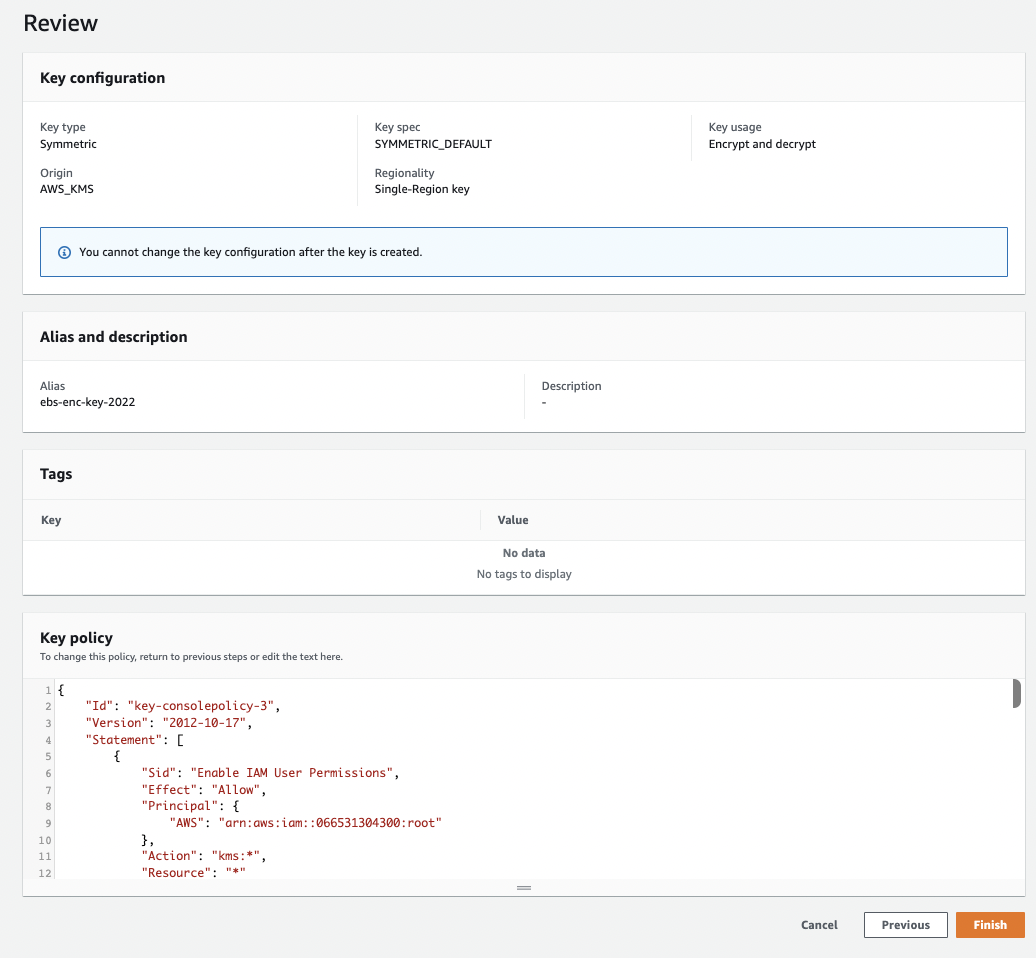
-
Replace the “Default KMS key” with newly created “Customer managed key”.
-
Repeat step number 9 - 14 to avoid using the default KMS key for all other resources.