KMS Key Policy
Validates the KMS key policy to ensure least-privilege access.
KMS key policies should be designed to limit the number of users who can perform encrypt and decrypt operations. Each application should use its own key to avoid over exposure.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the AWS Management Console.
-
Select the “Services” option and search for KMS.
-
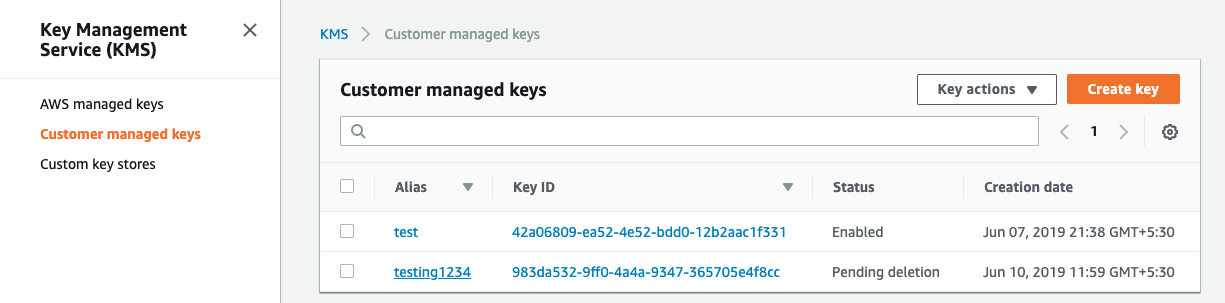
Scroll down the left navigation panel and choose “Customer managed keys” under “Key Management Service”.

-
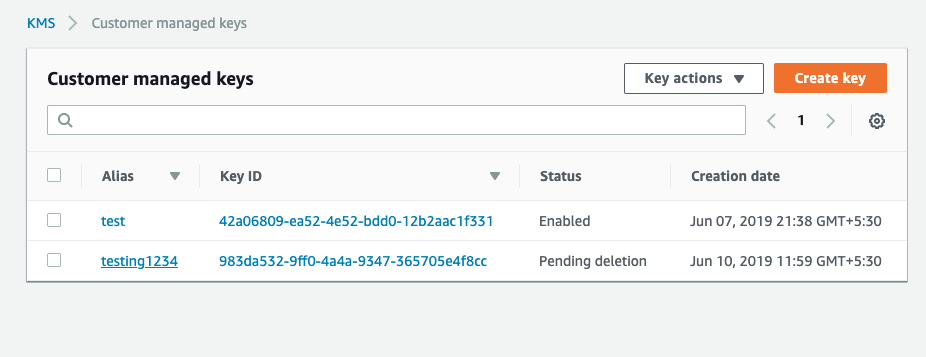
Select the “KMS key” that needs to be verified.
-
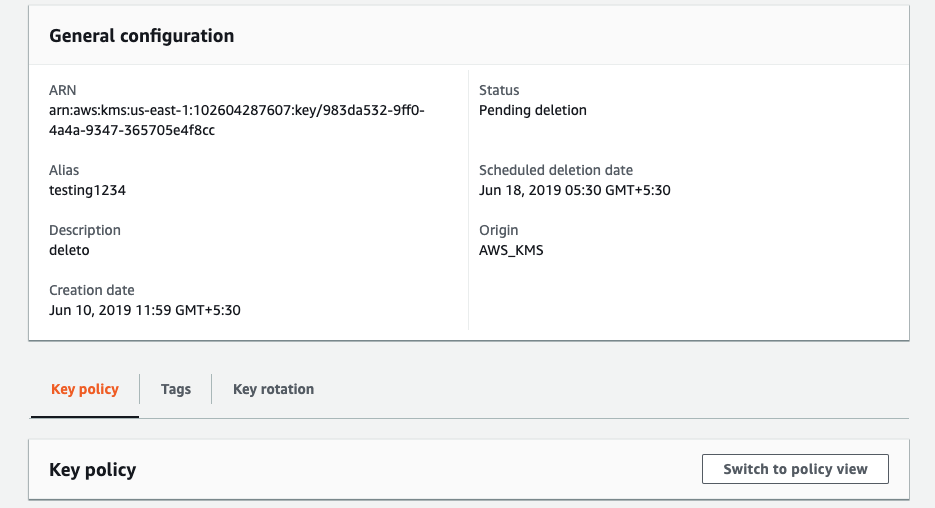
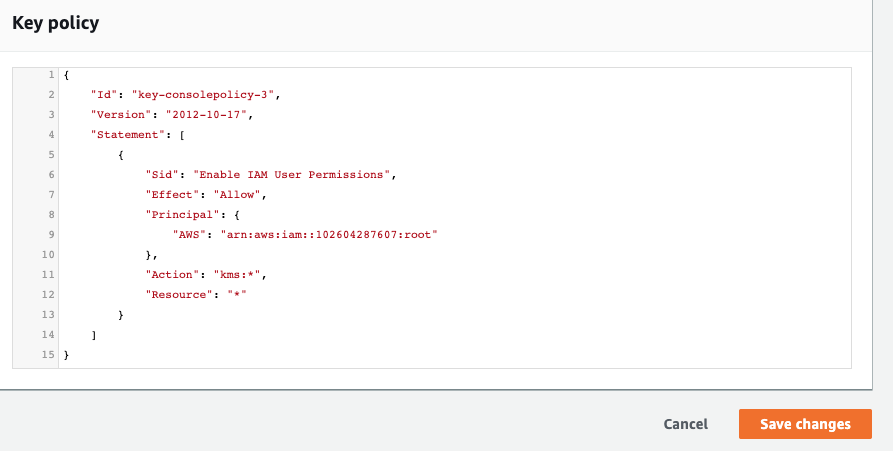
On the “Customer managed keys” page scroll down and on the “Key policy” tab click on the “Switch to policy view” button.
-
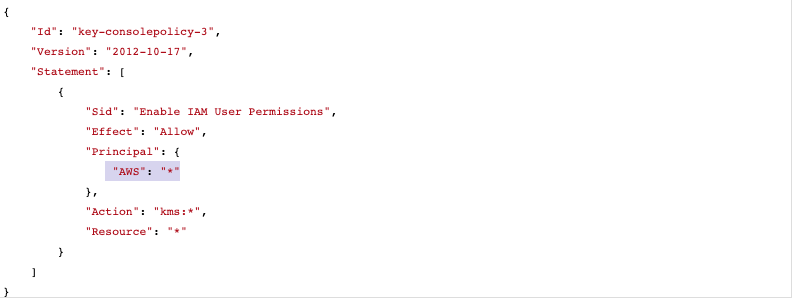
In the “key policy” tab if the “Principal” element value is set to (“AWS” : * ) and there are no Condition clauses to filter the access then the selected “KMS policy” is using wildcards.
-
Repeat step number 2 - 6 to verify other “KMS key” in the region.
-
Navigate to “Customer Managed Keys” under “Key Management Service” and select the “KMS key” that needs to modify to restrict the he number of users and roles that can perform encrypt and decrypt operation and have any wildcards.
-
On the “Customer managed keys” page scroll down and on the “Key policy” tab click on the “Switch to policy view” button and replace the “Everyone” grantee (“AWS” : * ) from the Principal element value with an “AWS account ID” or “AWS ARN” and click on the “Save” changes button.
-
Restrict the number of users and roles that can use the selected “KMS key” for encrypt and decrypt operations by making each application should use its own key .
-
Repeat steps number 7 - 10 to modify the “KMS key” policy of other “KMS keys” in the selected region.