KMS Scheduled Deletion
Detects KMS keys that are scheduled for deletion
Deleting a KMS key will permanently prevent all data encrypted using that key from being decrypted. Avoid deleting keys unless no encrypted data is in use.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the AWS Management Console.
-
Select the “Services” option and search for KMS.
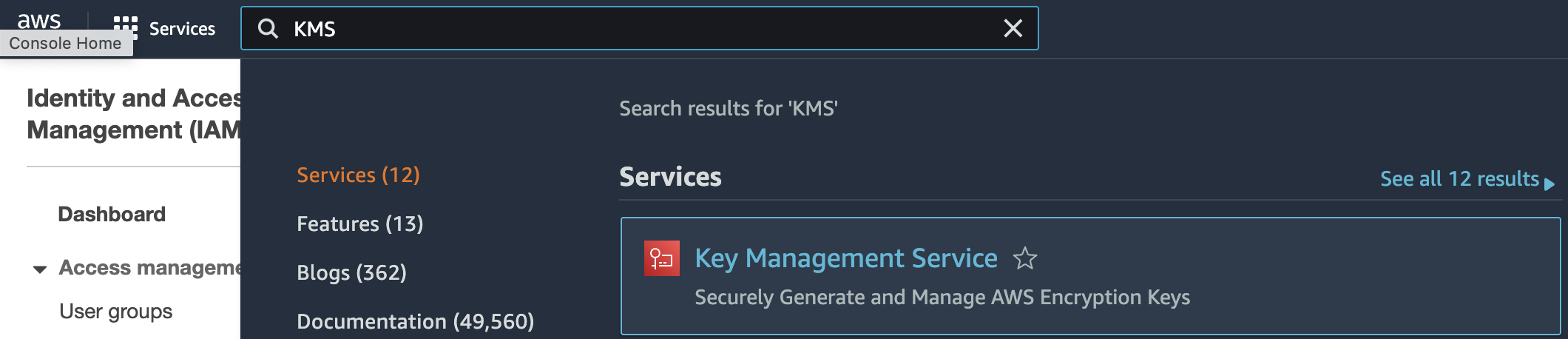
-
Scroll down the left navigation panel and choose “Customer Managed Keys” under “Key Management Service”.
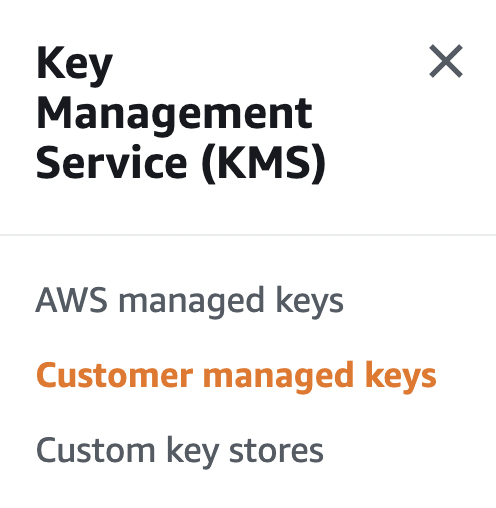
-
Verify the “KMS keys” that are scheduled for deletion and “Status” is shown as “Pending deletion” under the “Customer managed keys”.
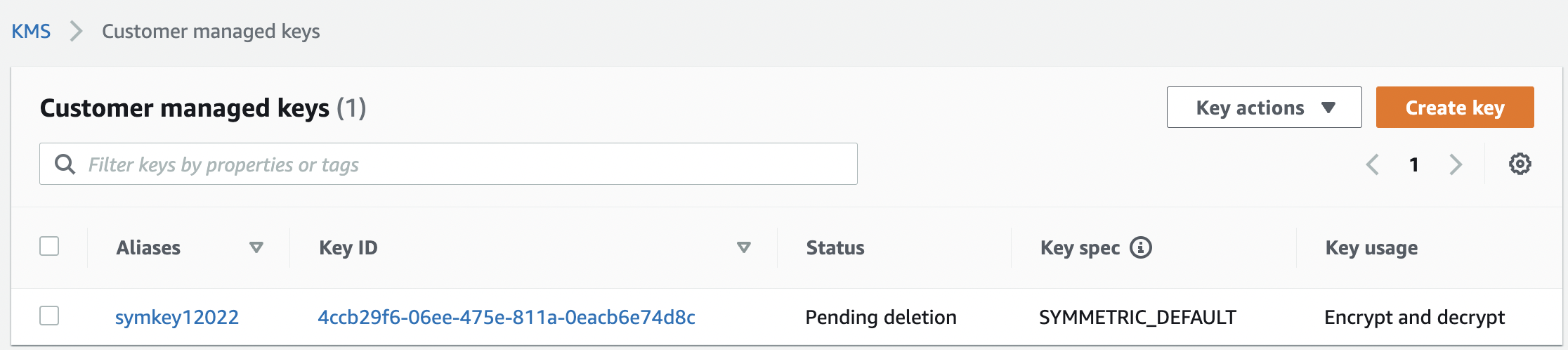
-
Repeat step number 2 - 4 to verify other “KMS keys” which are scheduled for deletion in other regions in AWS.
-
Navigate to “Customer Managed Keys” under “Key Management Service” and select the “KMS key” that needs to be modified to disable the scheduled key deletion.
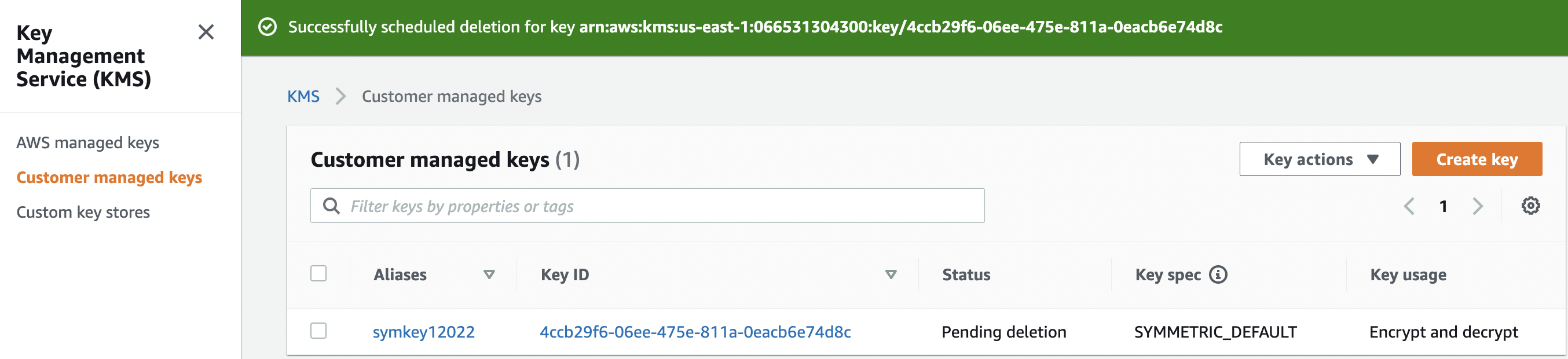
-
Click on the “Key actions” button at the top and select the “Cancel key deletion” option to disable the scheduled deletion.
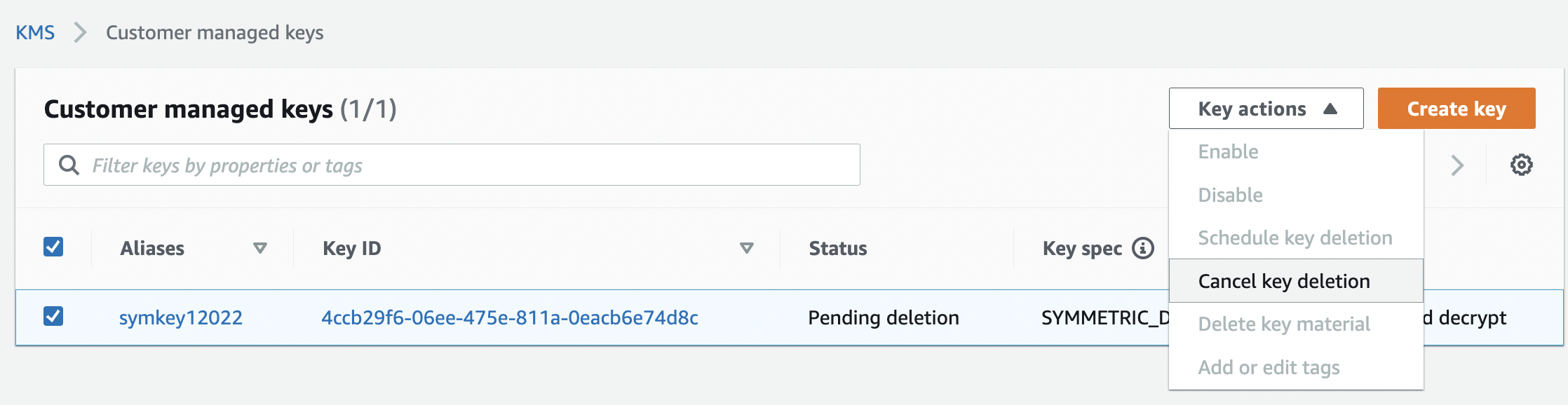
-
Click on the “Disable” option under “Key actions” to disable the selected “KMS key” instead of deleting the key.
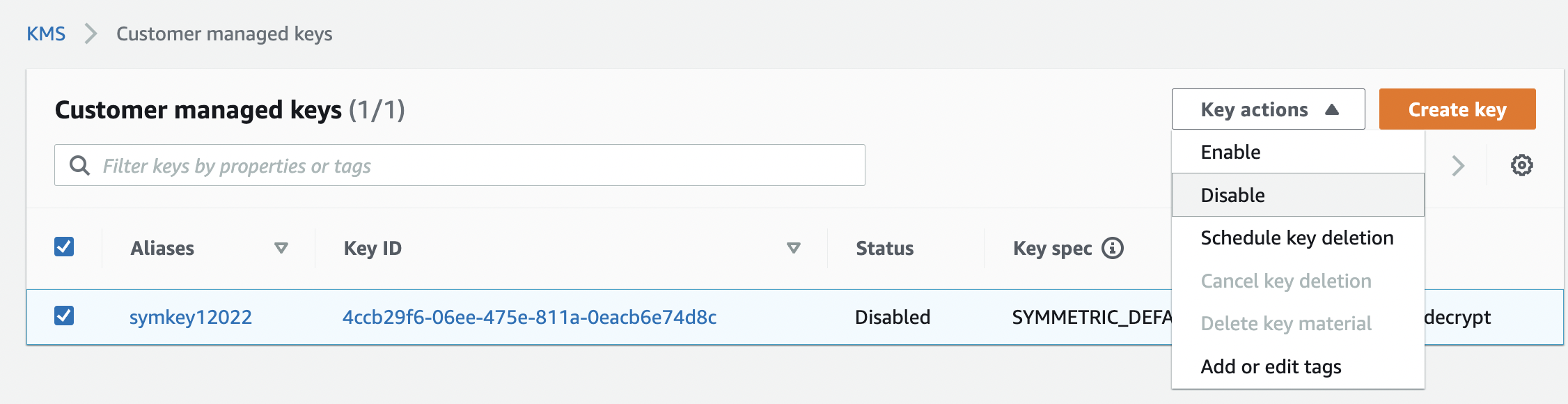
-
Repeat step number 6 - 8 to disable the key deletion before the scheduled deletion time.