S3 Bucket Logging
Ensures S3 bucket logging is enabled for S3 buckets
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
Add a logging block to the resource to enable access logging
|
|
-
Log in to the AWS Management Console.
-
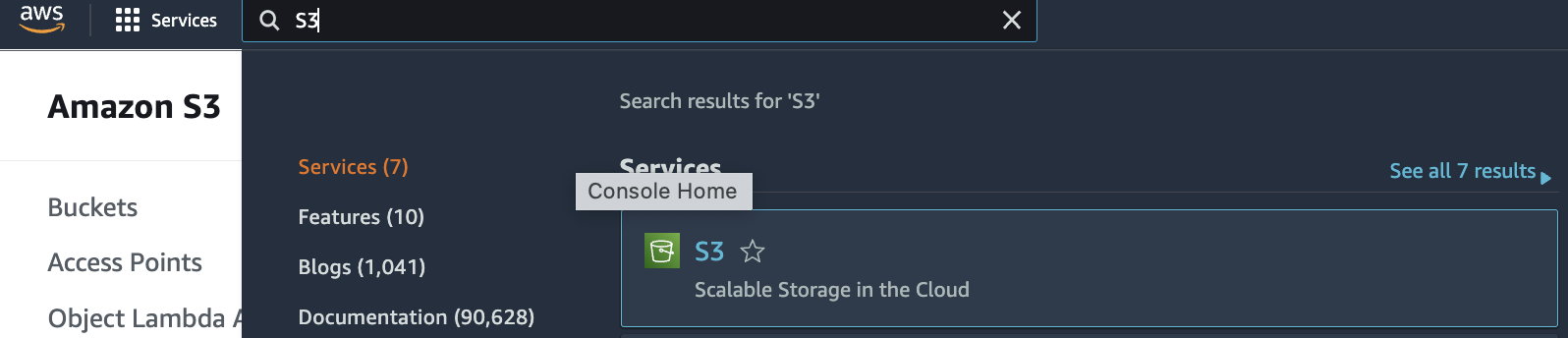
Select the “Services” option and search for S3.
-
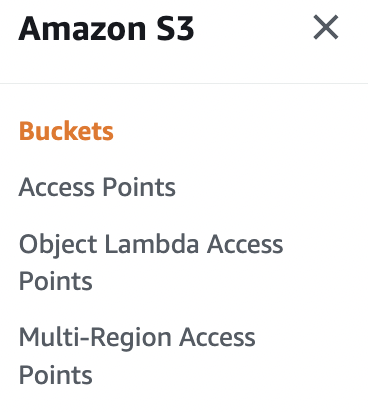
Scroll down the left navigation panel and choose “Buckets”.
-
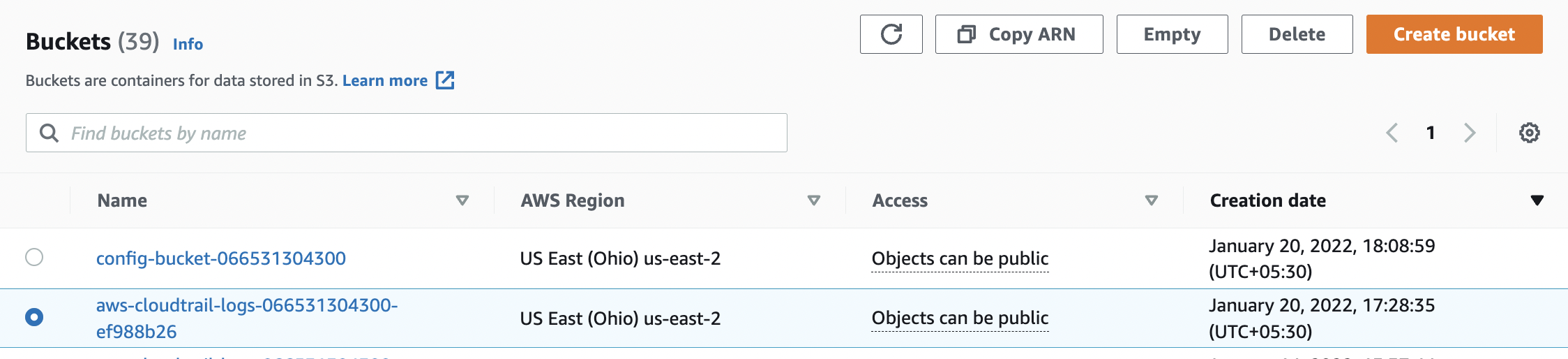
Select the “Bucket” that needs to be verified and click on its identifier(name) from the “Bucket name” column.
-
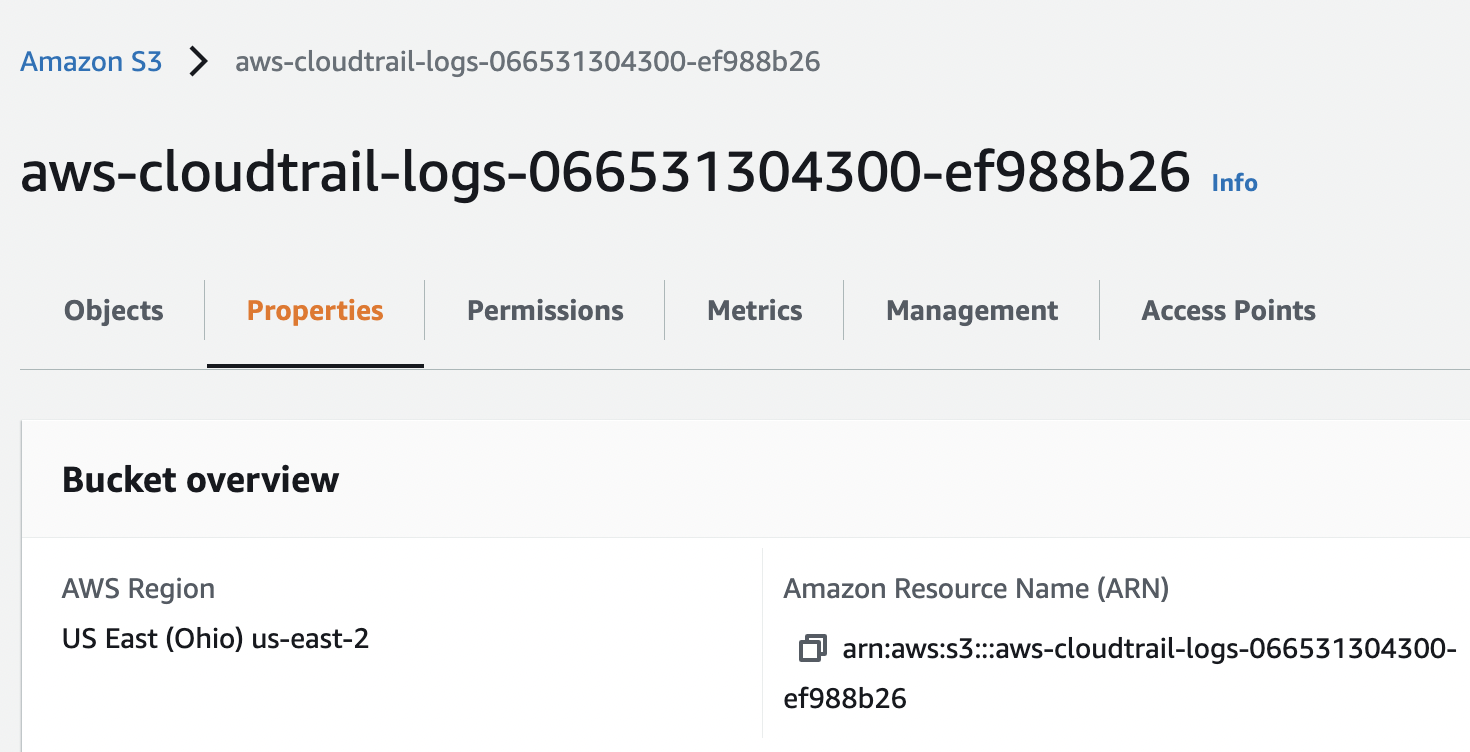
Click on the “Properties” tab on the top menu.
-
Check the “Server access logging” option under “Properties” and if it’s set to “Disabled” then S3 bucket logging is not enabled for the selected S3 bucket.
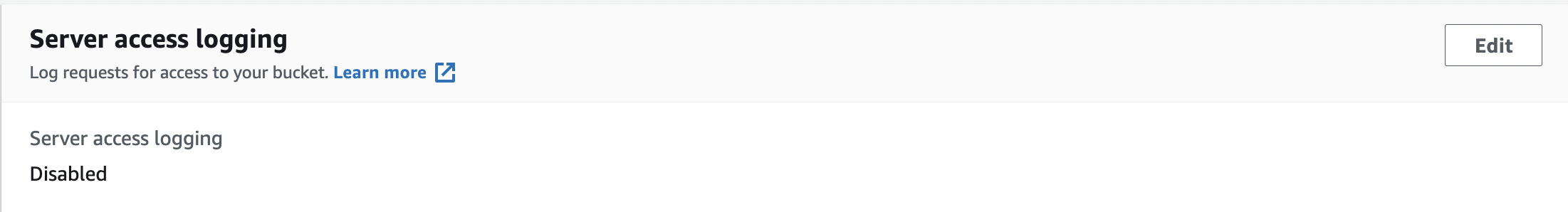
-
To enable Server access logging click on the “Edit” button under “Server access logging” option. On the “Edit server access logging” page select “Enable” and choose the “Target bucket” from the dropdown menu for storing the logs.
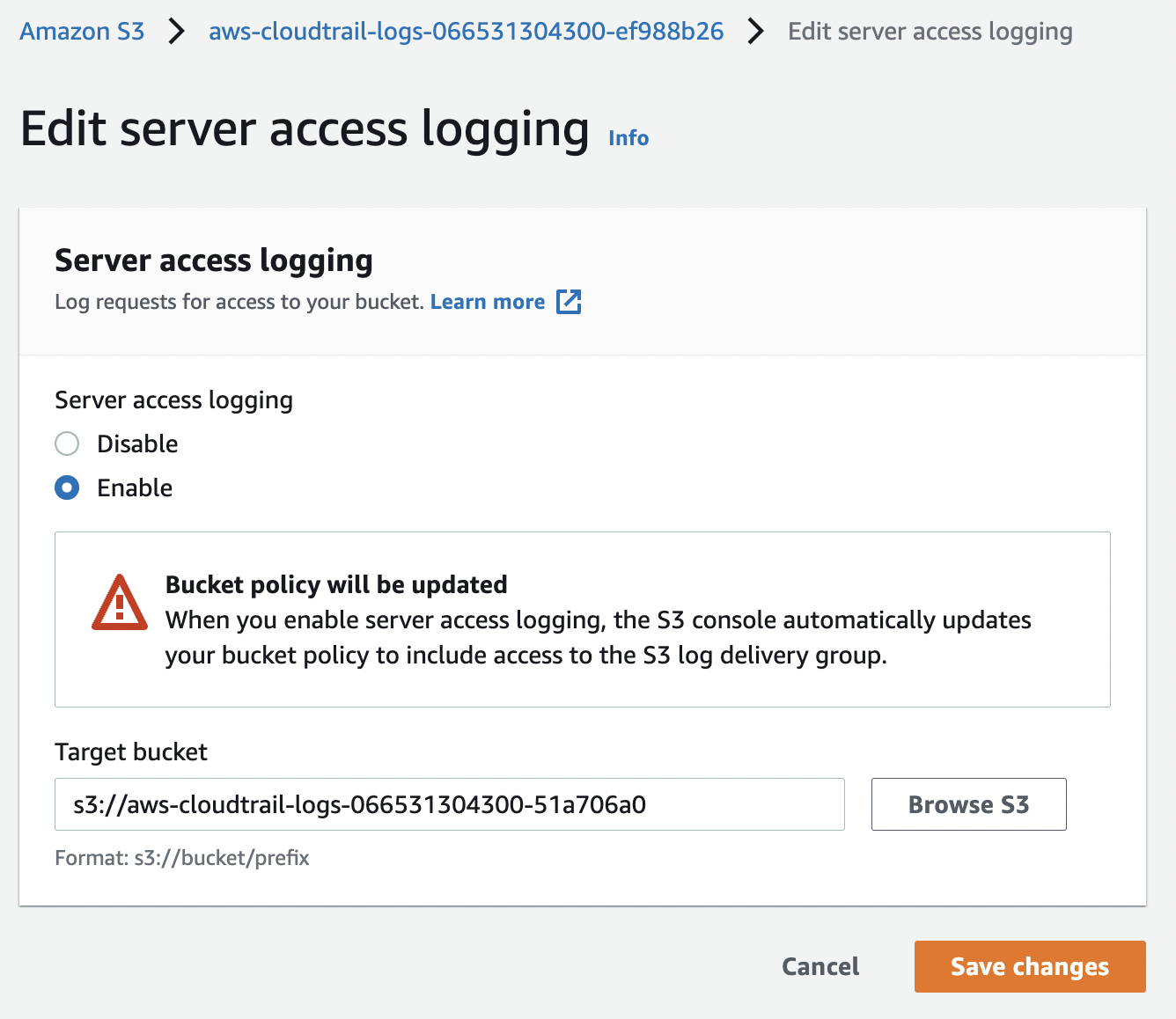
-
Click on the “Save changes” button to make the necessary changes.

-
Repeat steps number 4 - 8 to enable “Logging” for other S3 buckets.
Add a logging block to the resource to enable access logging
|
|
|
|