S3 Bucket All Users Policy
Ensures S3 bucket policies do not allow global write, delete, or read permissions
S3 buckets can be configured to allow the global principal to access the bucket via the bucket policy. This policy should be restricted only to known users or accounts.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the AWS Management Console.
-
Select the “Services” option and search for S3.
-
Scroll down the left navigation panel and choose “Buckets”.
-
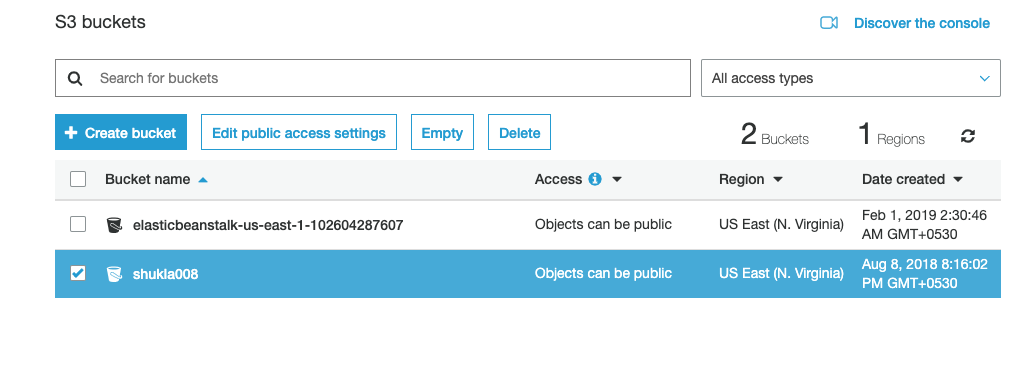
Select the “Bucket” that needs to be verified and click on its identifier(name) from the “Bucket name” column.
-
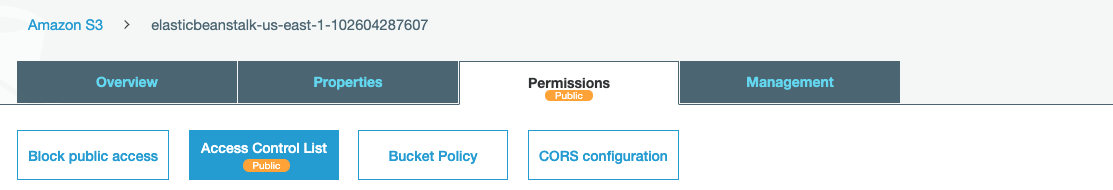
Click on the “Permissions” tab on the top menu.
-
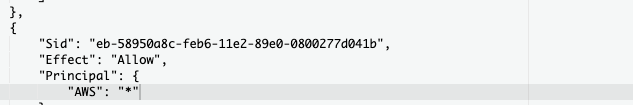
Check the “Bucket Policy” option under “Properties” abd check the “Effect” and “Principal” value.If the “Effect” element value is set to “Allow” and the “Principal” element value is set to everyone ( * ) then the selected S3 bucket is publicly accessible.
-
Repeat steps number 2 - 6 to verify other S3 buckets in the region.
-
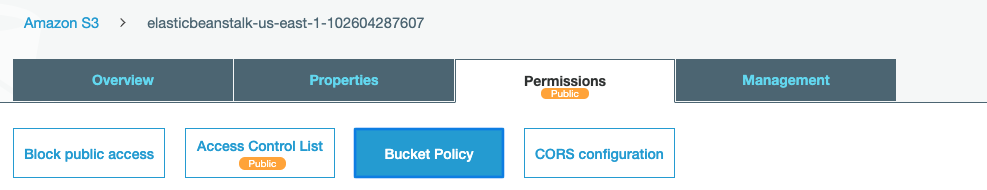
Select the publicly accessible S3 bucket that needs to configure and click on the “Permissions” tab and click on the “Bucket Policy” option.
-
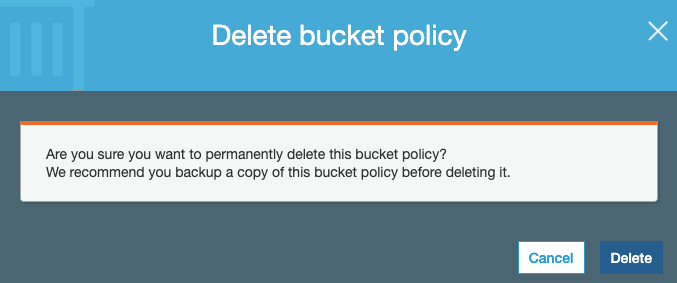
In the “Bucket Policy” option either remove the public accessibility by deleting the policy for the selected S3 bucket. Click on the “Delete” option at the top and click on “Delete” button on the “Delete Bucket Policy” tab.
-
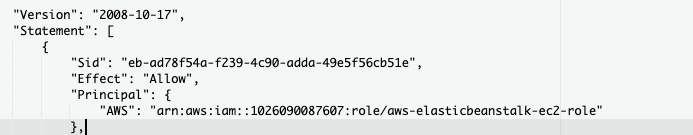
In order to limit the public accessibility replace the Principal element current value with the Amazon Resource Name (ARN) ( e.g. { “AWS”: “arn:aws:iam::102604298007:role/aws-elasticbeanstalk-ec2-role” } ) of the AWS account that should have access to the selected S3 bucket.
-
Click on the save button at the top to make the necessary changes.
-
Repeat steps number 8 - 11 to remove wildcard principals for other S3 buckets.