SQS Cross Account Access
Ensures SQS policies disallow cross-account access
SQS policies should be carefully restricted to prevent publishing or reading from the queue from unexpected sources. Queue policies can be used to limit these privileges.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the AWS Management Console.
-
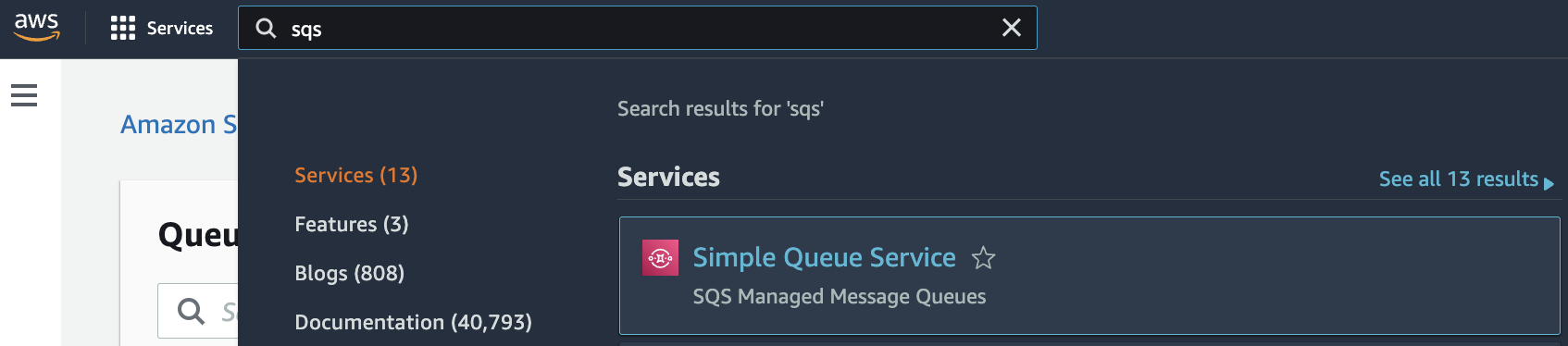
Select the “Services” option and search for SQS.
-
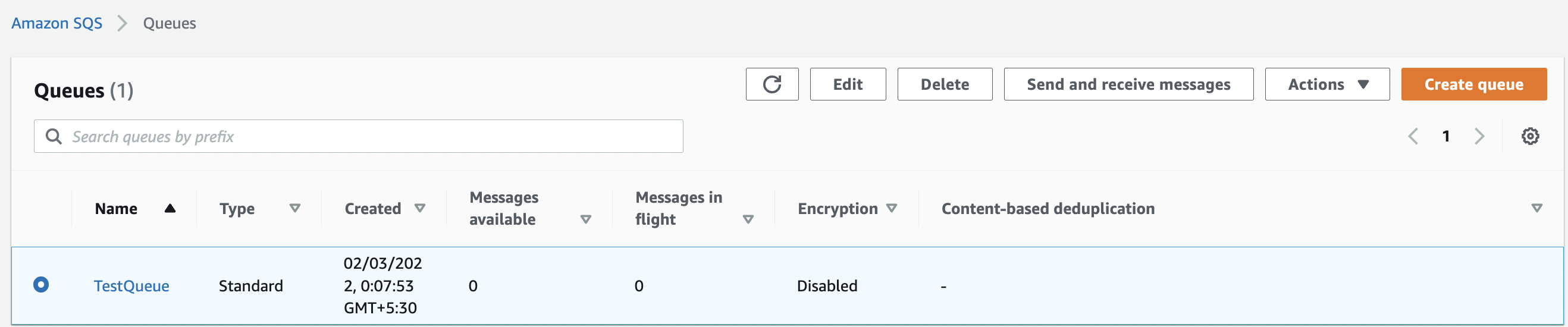
Select the “SQS” queue that needs to be verified by clicking on its “Name”.
-
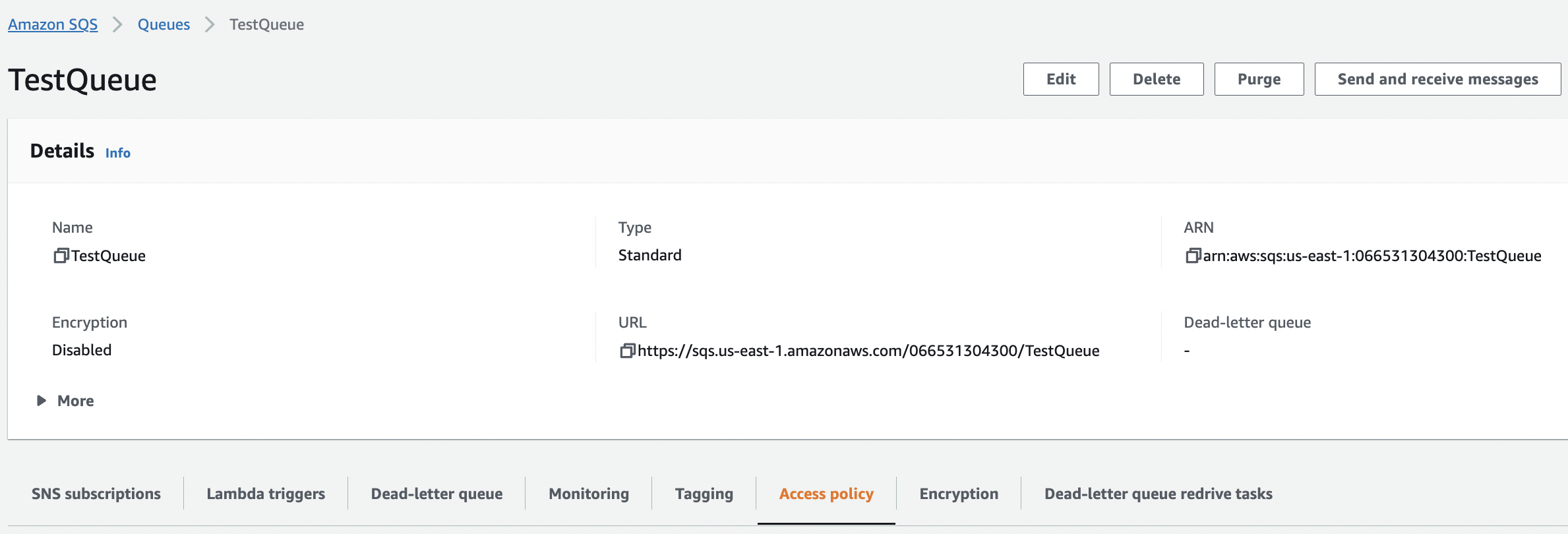
Scroll down the page and click on the “Access Policy” tab from the bottom panel.
-
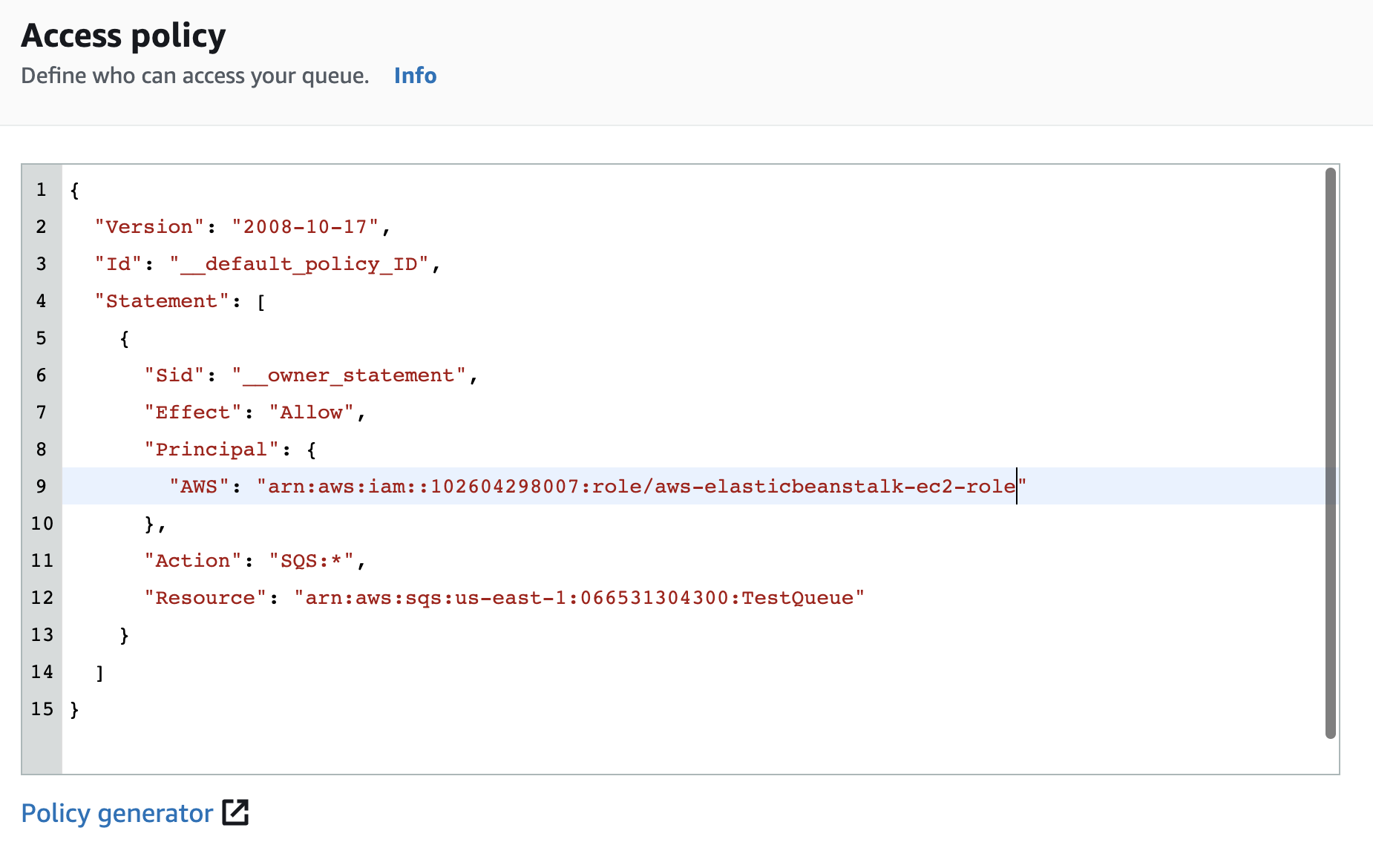
Check the “Principal” key under “Access policy (Permissions)” and if set to “*” or an “AWS Account ID” which does not match any of the trusted AWS accounts then the selected “SQS” queue cross-account access is not secured.

-
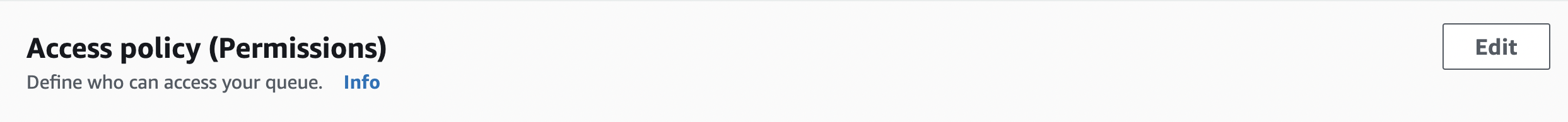
To edit the selected “SQS” queue permission click on “Edit button”.
-
On the “Edit Queue” page scroll down to “Access policy” and change the “Principal” value from Everyone(*) to relevant AWS Account Id.
-
Click on the “Save” button to make the necessary changes.

-
Repeat steps number 3 - 8 to update the SQS policy to prevent access from external accounts.