Web App accepts incoming client certificate
The TLS mutual authentication technique in enterprise environments ensures the authenticity of clients to the server. If incoming client certificates are enabled only an authenticated client with valid certificates can access the app.
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Microsoft Azure Management Console.
-
Select the “Search resources, services, and docs” option at the top and search for App Services.
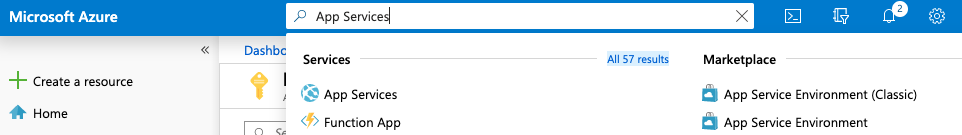
-
Select the “App Services” by clicking on the “Name” link to access the configuration changes.
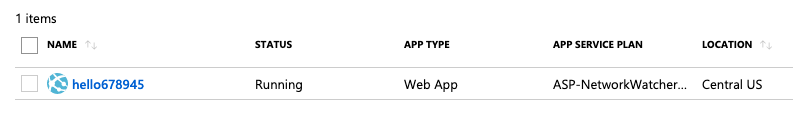
-
On left navigation panel that opens, click on Configuration tab.</br
-
Select General settings tab on the Configurations page.
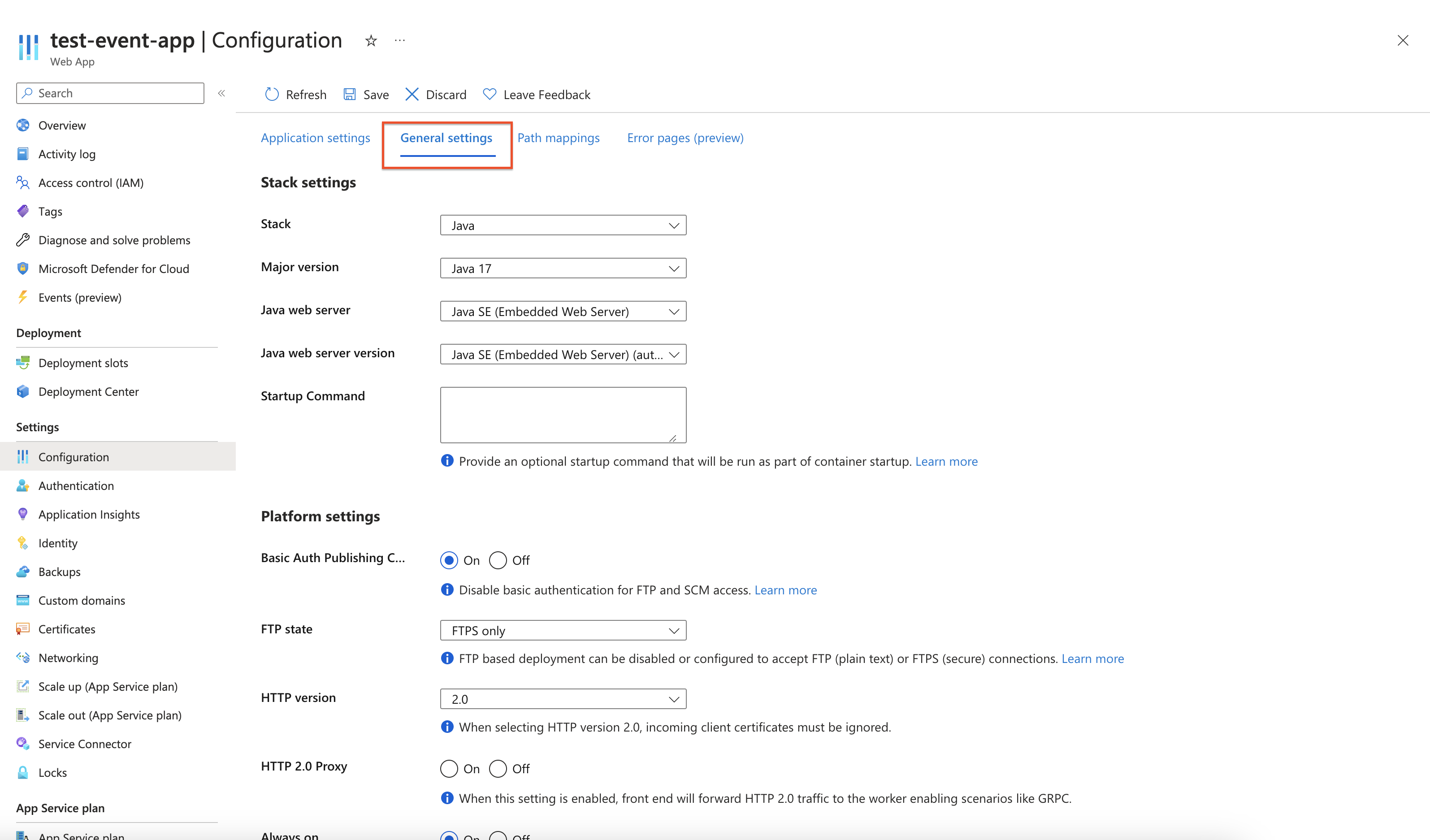
-
Scroll down to check for Incoming client certificates at the bottom and select one of the following “Required”, “Allowed”, or “Optional”, according to requirement. .
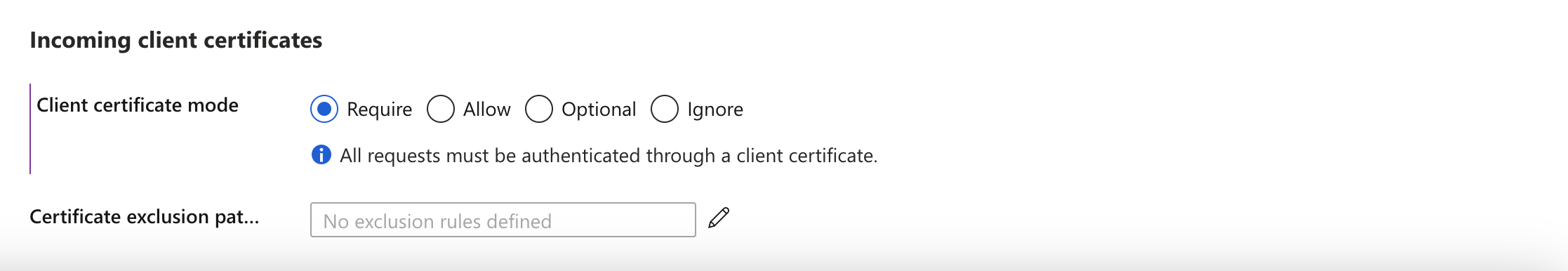
-
Repeat above steps to ensures “Client Certificates” are enabled for “App Services”, only allowing clients with valid certificates to reach the app. “NOTE: This plugin shows positive result when HTTP2.0 is enabled”
Enable incoming certificates for clients
|
|