Resource Location Matches Resource Group
Ensures a policy is configured to audit that deployed resource locations match their resource group locations
Using Azure Policy to monitor resource location compliance helps ensure that new resources are not launched into locations that do not match their resource group.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Microsoft Azure Management Console.
-
Find the search bar at the top and search for Policy.
-
On the “Policy” page, scroll down the left navigation panel and choose “Assignments” under “Authoring”.
-
On the “Policy - Assignments” page, check the “Policies” listed and if there are no “Policies” for “Resource Location Matches Resource Group” then the selected “Assignment” don’t have any “Resource Location Matches Resource Group” policy.
-
If there is no policy for “Resource Location Matches Resource Group” then click on “Assign policy” at the top to create a new policy.
-
On the “Assign Policy” page, under “Basics” tab, select “Scope” accordingly and click on the “…” dots icon next to “Policy definition”.
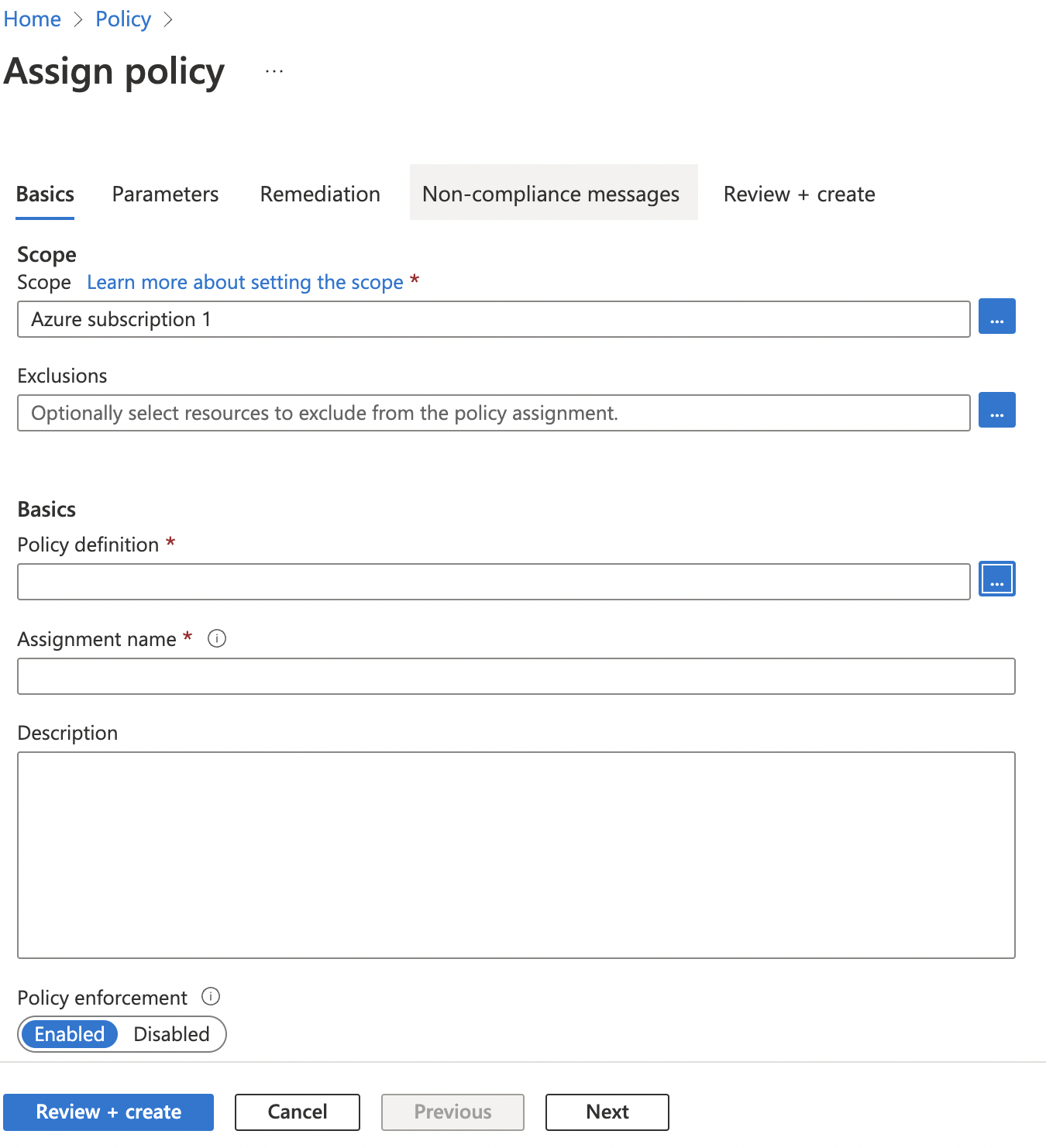
-
On the “Available Definitions” page, click on the “Search” box and search for “Resource Location Matches Resource Group”. Click the Policy Definition found and then click “Select” button at the bottom.
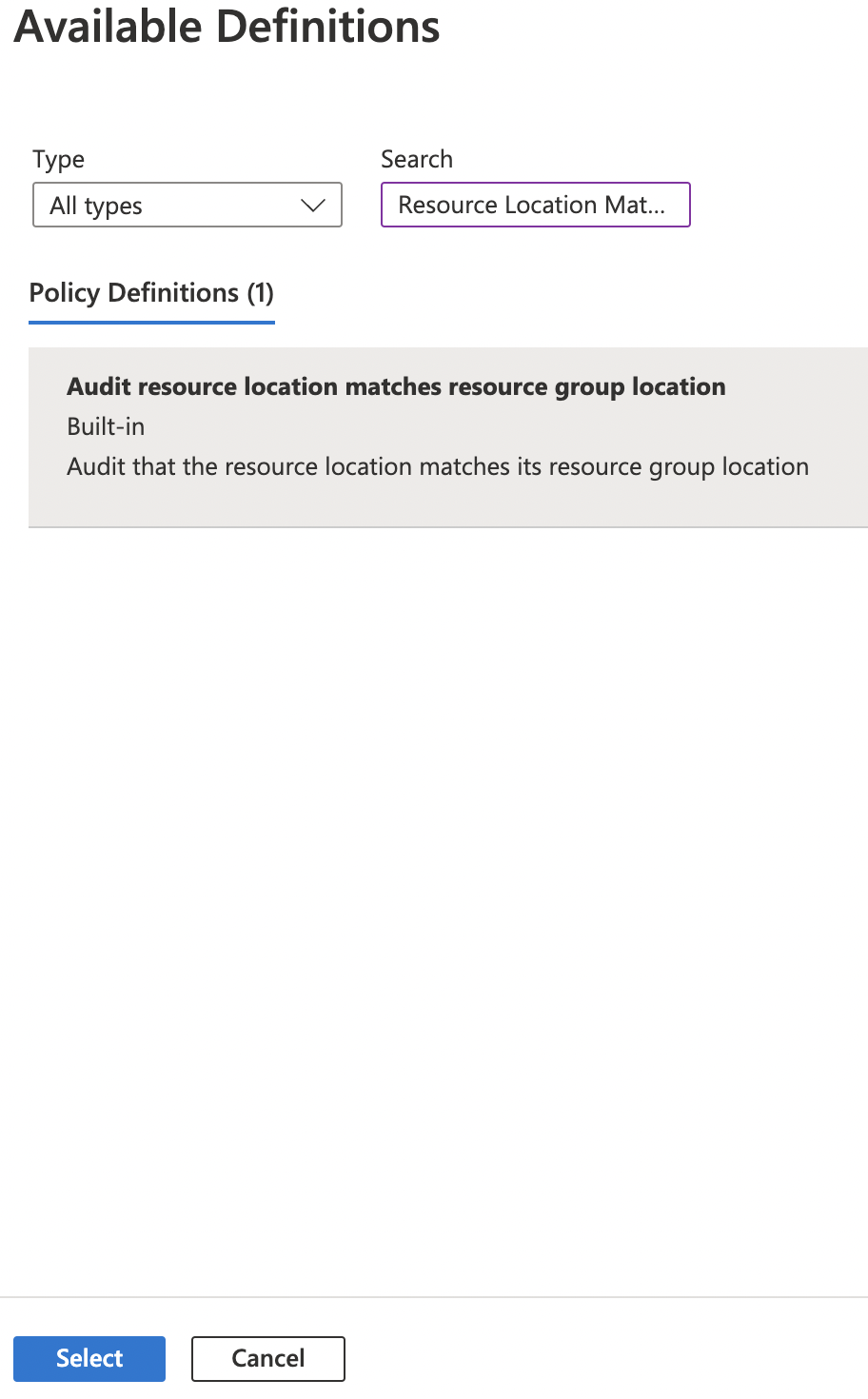
-
Once back on the “Assign Policy” page, provide a “Description” and click on the “Next” button at the bottom. Now select “Allowed locations” on “Parameters” tab and click Next at the bottom.
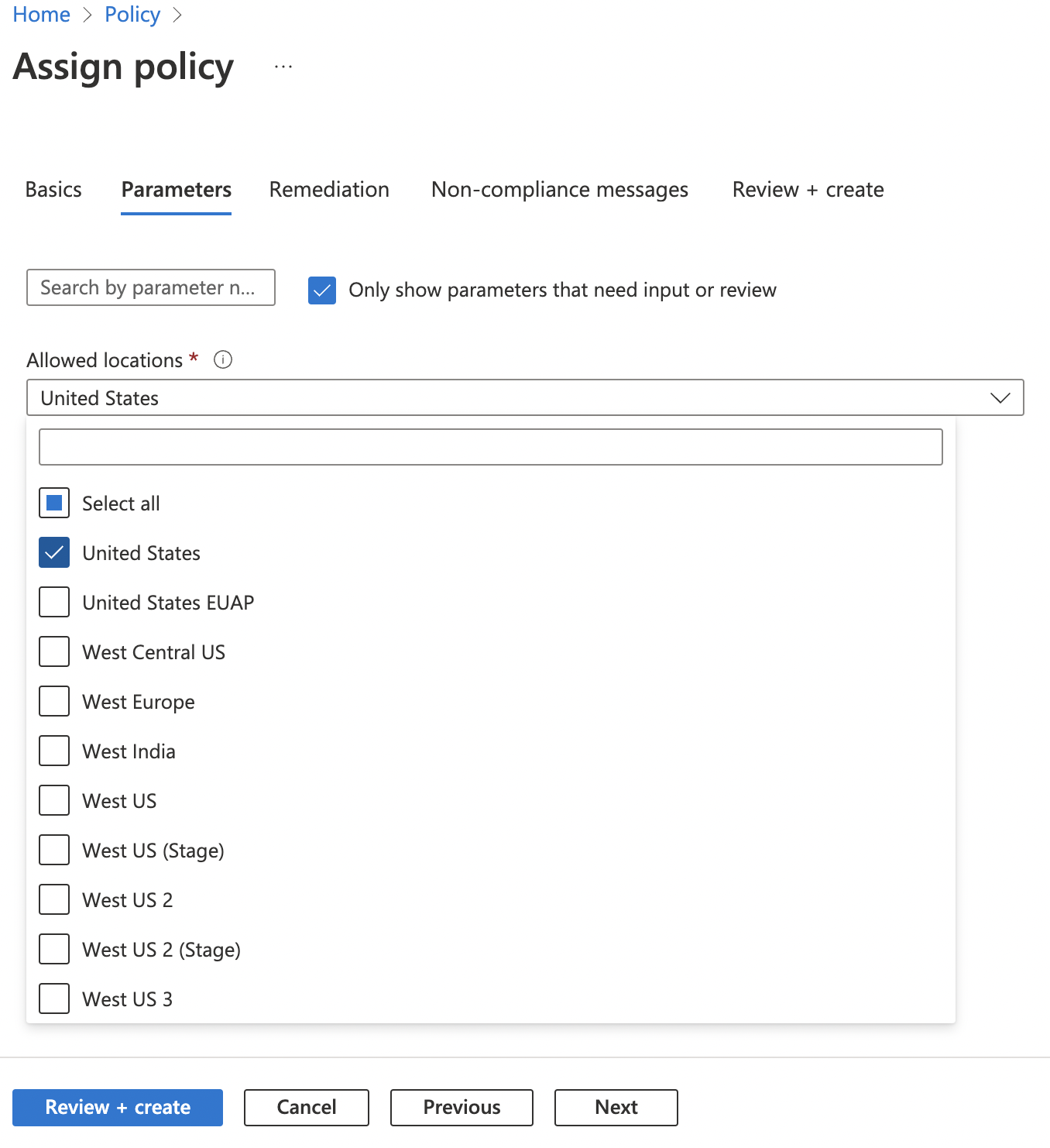
-
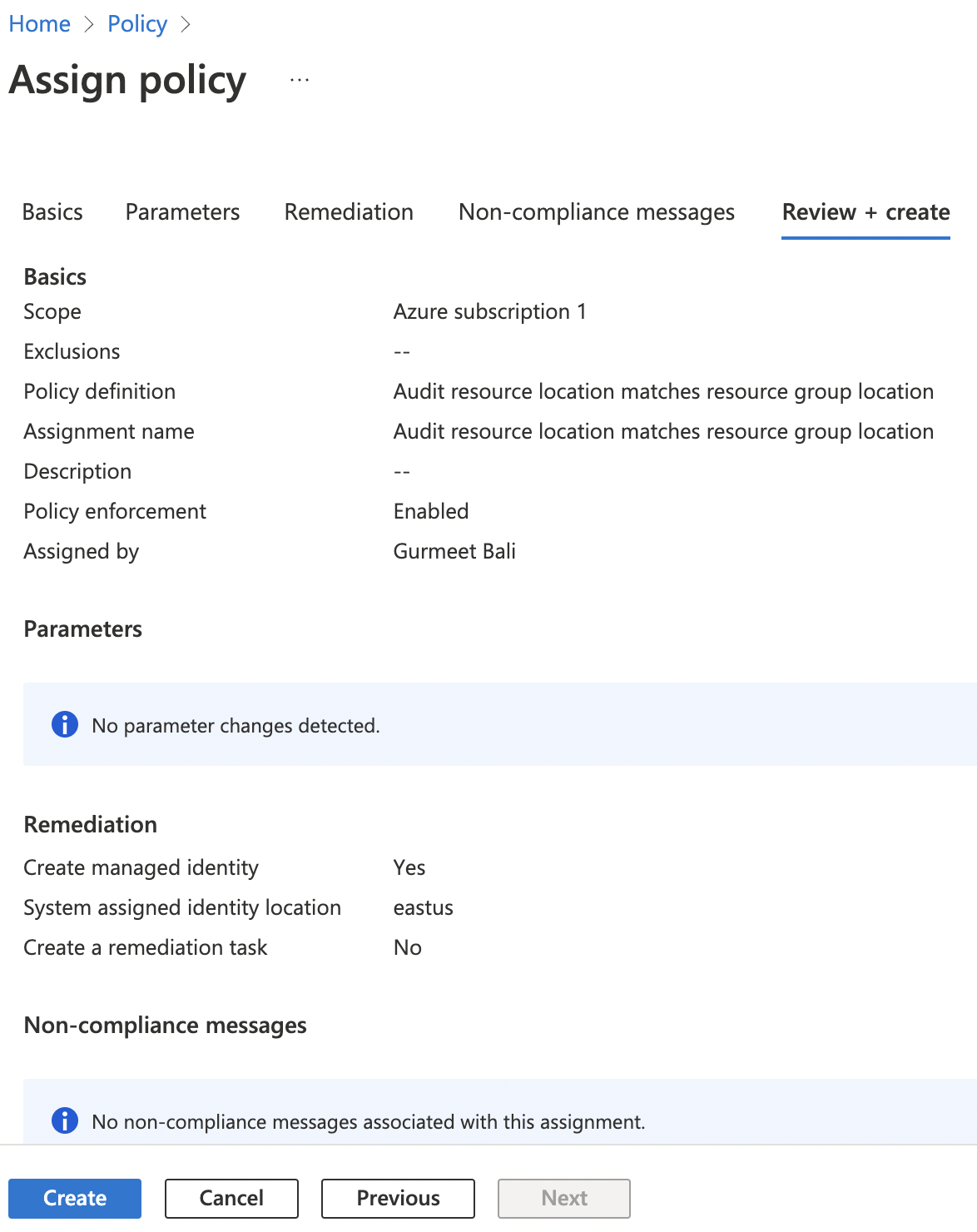
On the “Remediation” tab, click on the checkbox next to the “Create a Managed Identity” and select desired “Managed Identity Location”. Click “Review + create” button at the bottom.
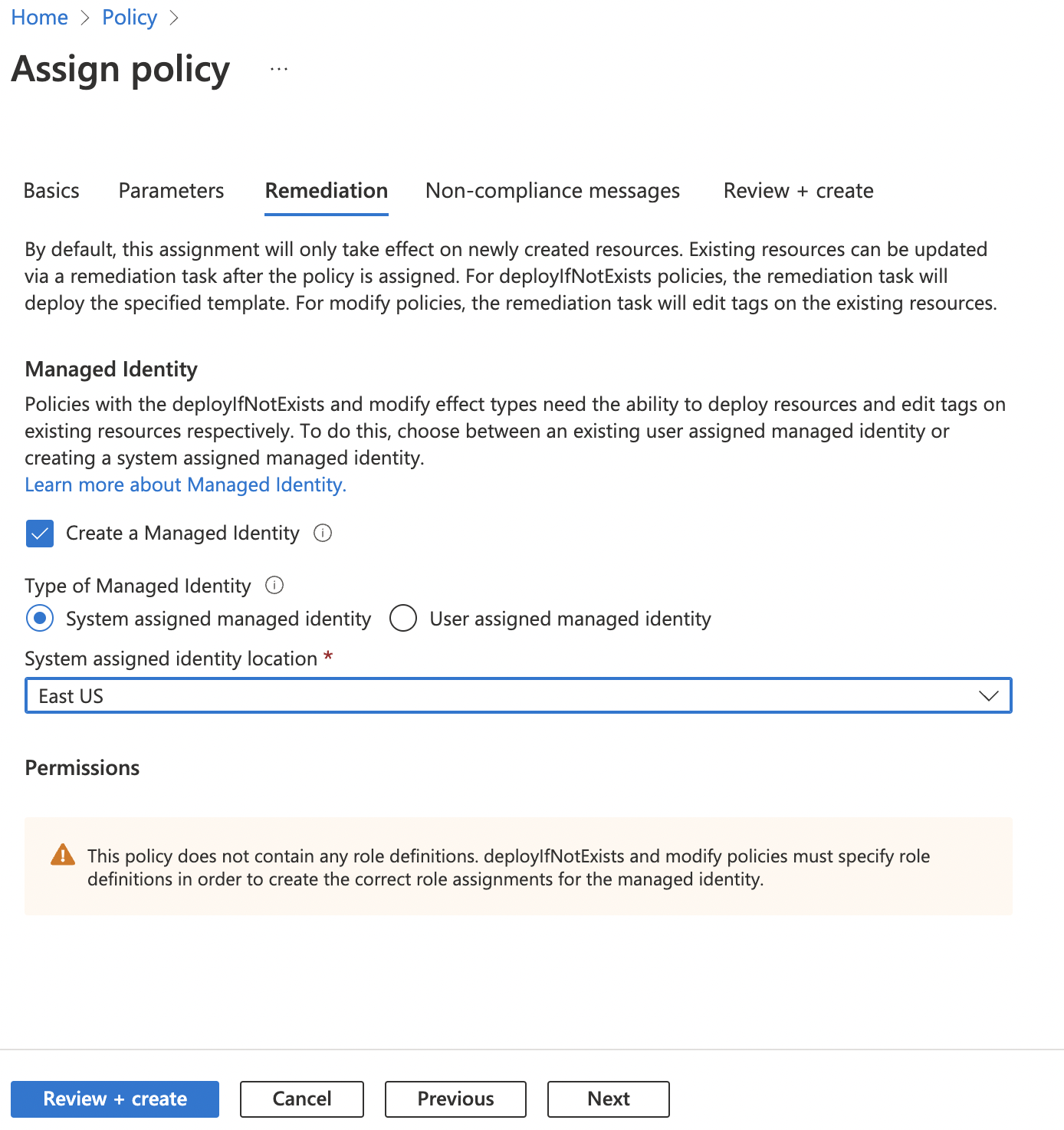
-
On the “Review + Create” tab, click “Create” button at the bottom to create the specific “Resource Location Matches Resource Group” policy.
-
Repeat steps number 6 - 10 to enable the built-in “Azure Policy definition: Audit resource location matches resource group location” for all directories.