Detect Insecure Custom Origin
Ensures that HTTPS is enabled for CDN endpoints with a custom origin
All Azure CDN endpoints should enable HTTPS to secure traffic to the backend custom origin.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Microsoft Azure Management Console.
-
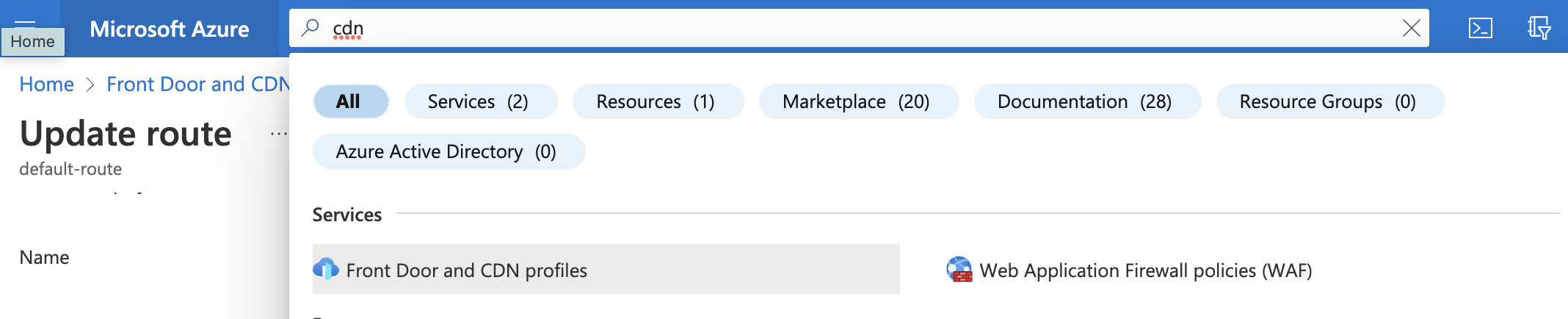
Select the “Search resources, services, and docs” option at the top and search for CDN. Select “Front Door and CDN profiles”.
-
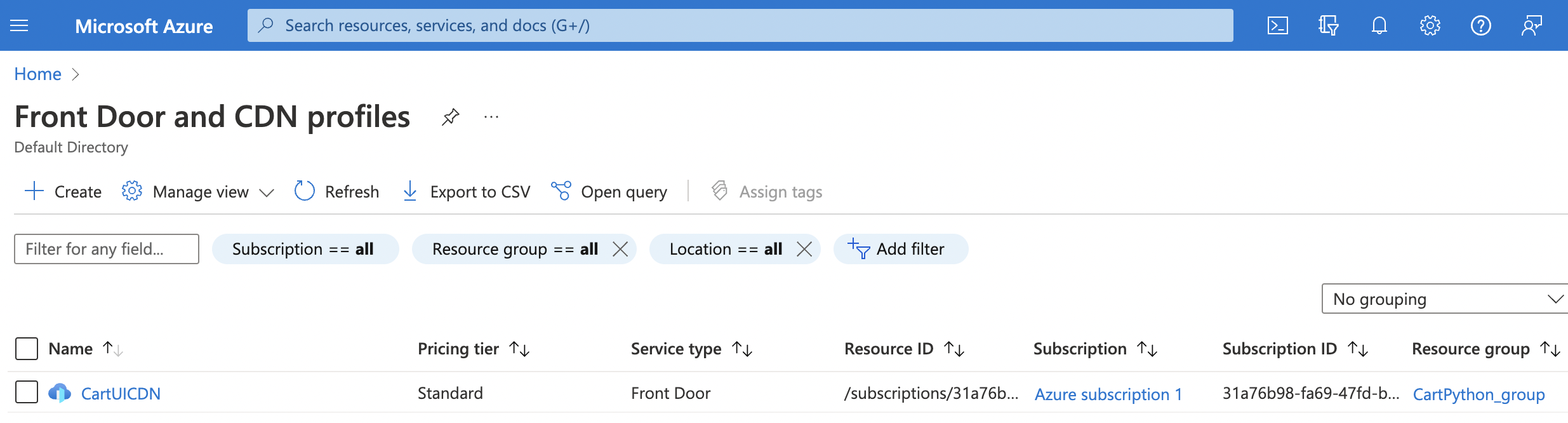
On the “Front Door and CDN profiles” page, click on the “Name” link to access the configuration changes.
-
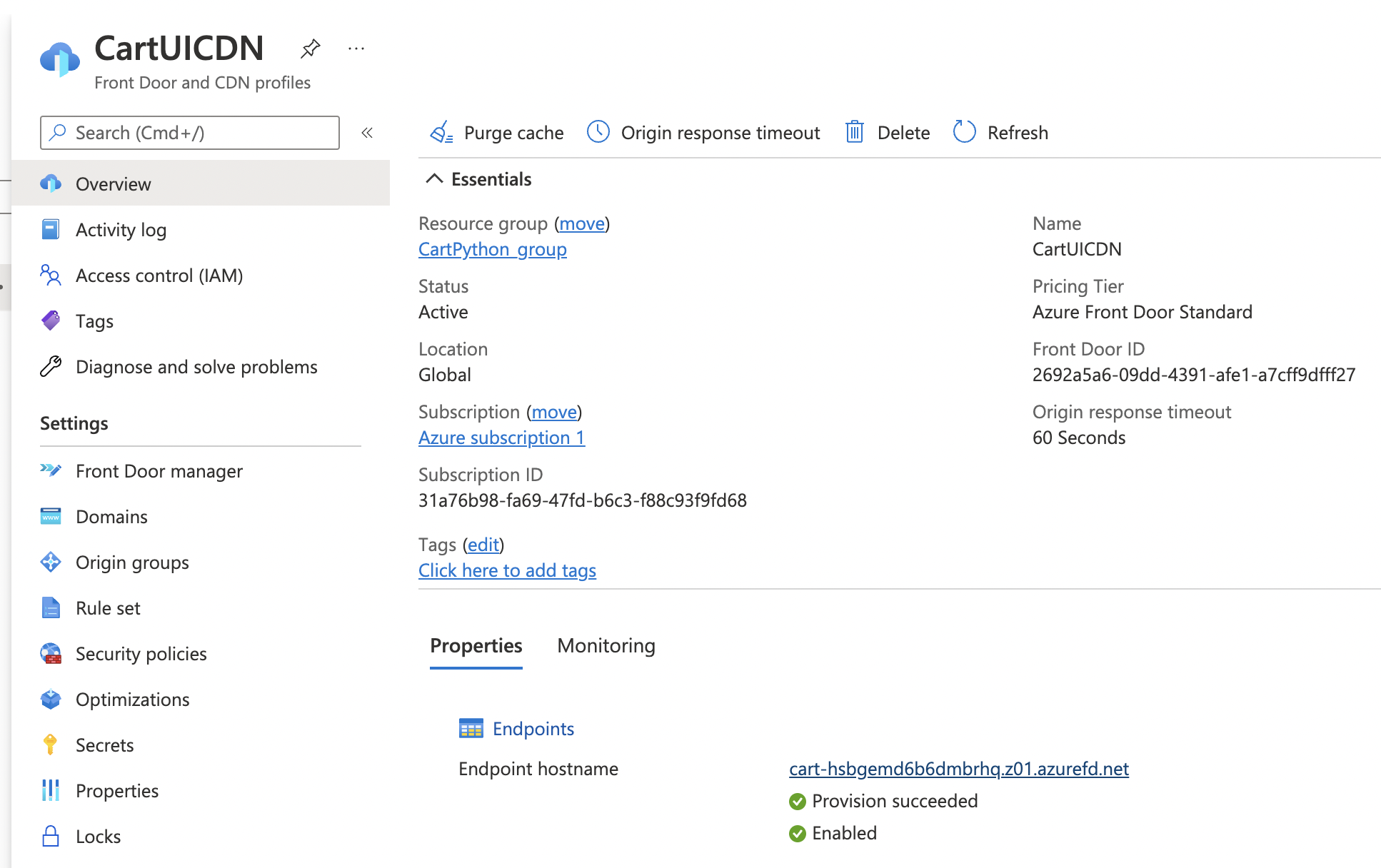
In the CDN details pane that opens, click on the “Endpoints” link under “Properties”.
-
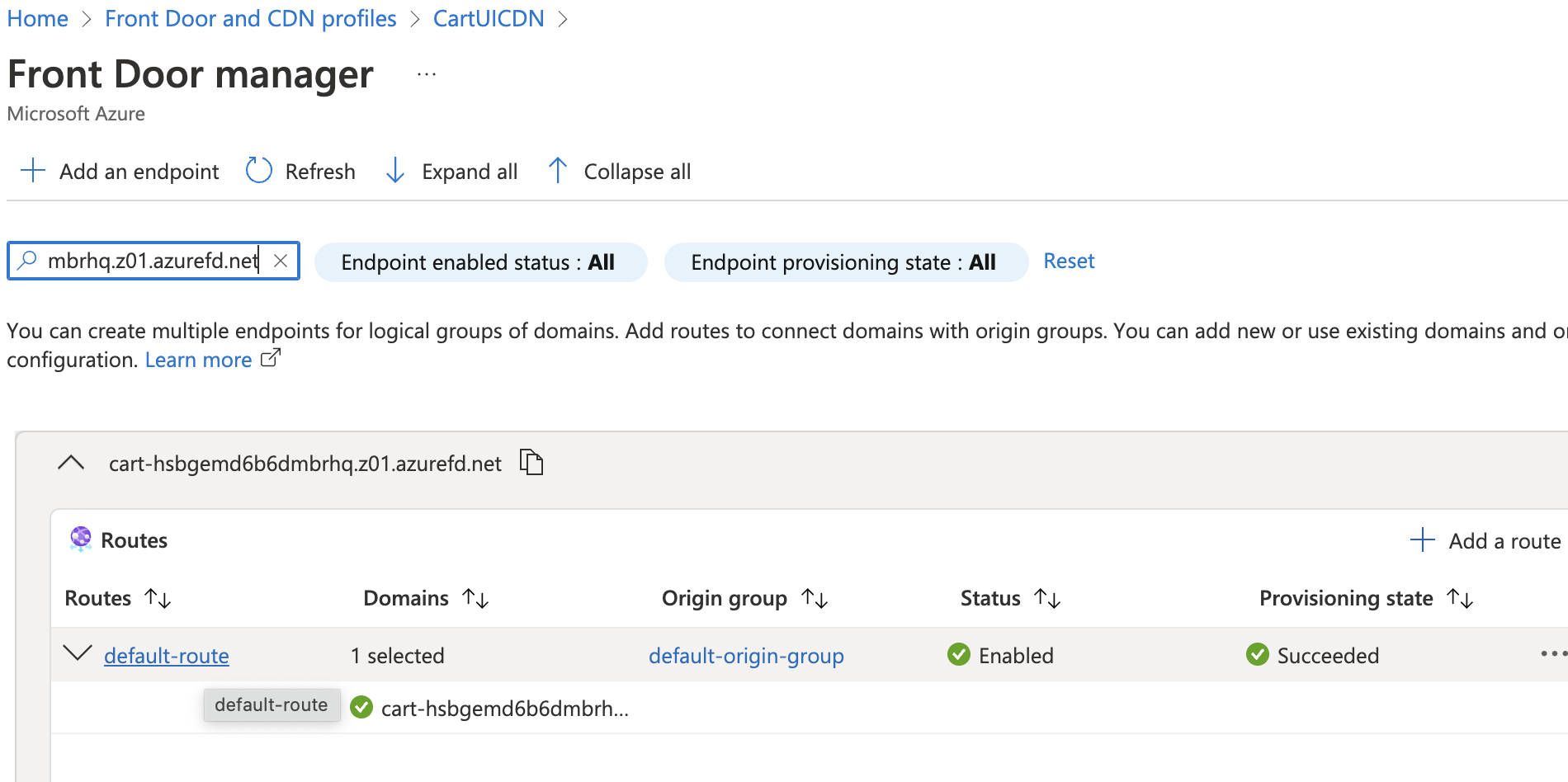
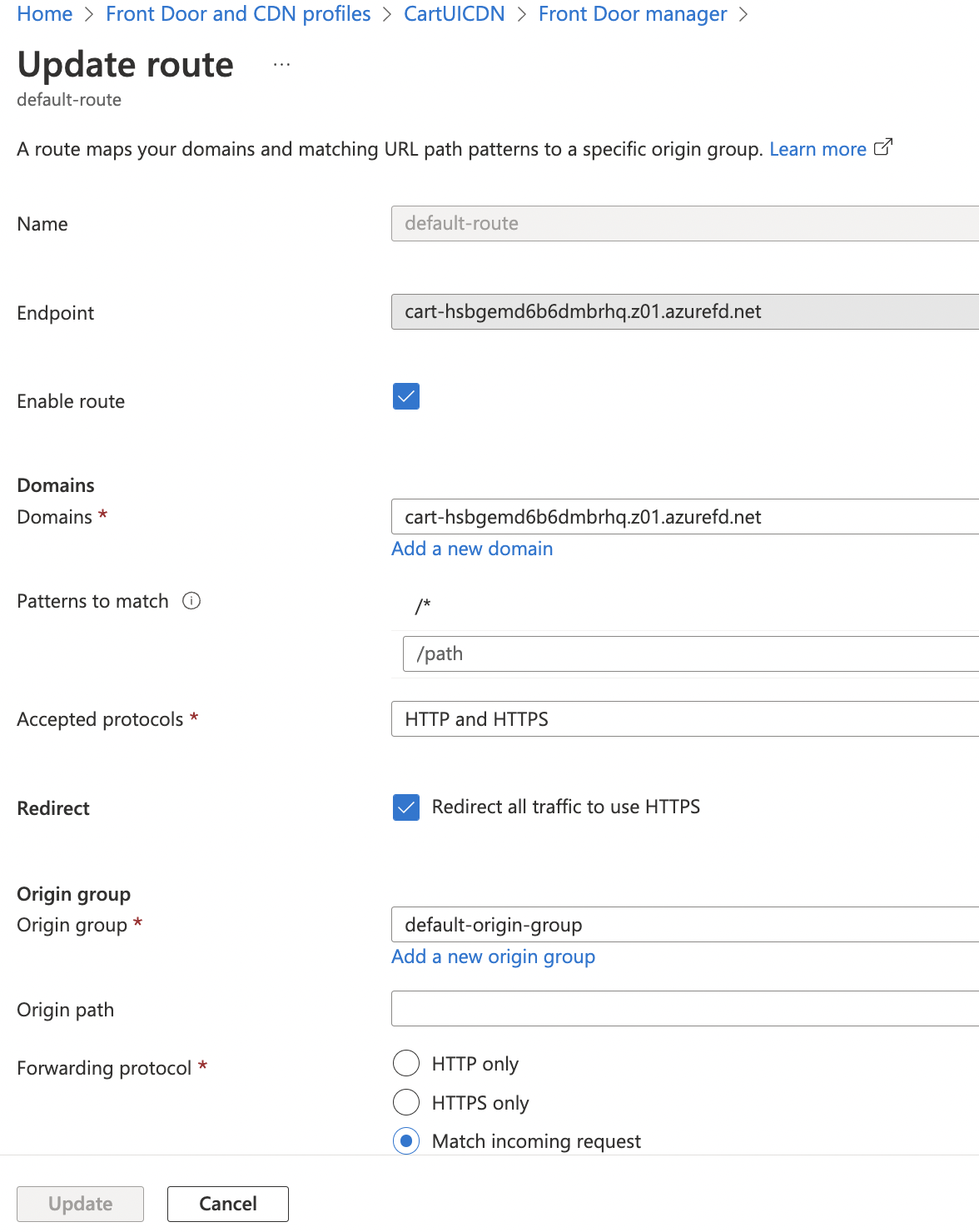
On the endpoint management page that opens, click on “default-route” under “Routes” column to load the route configuration page.
-
On the “Update route” page, check the value of “Accepted protocols” dropdown. If it is set to “HTTP only” or “HTTP and HTTPS” then the endpoint allows insecure traffic. This is a security threat.
-
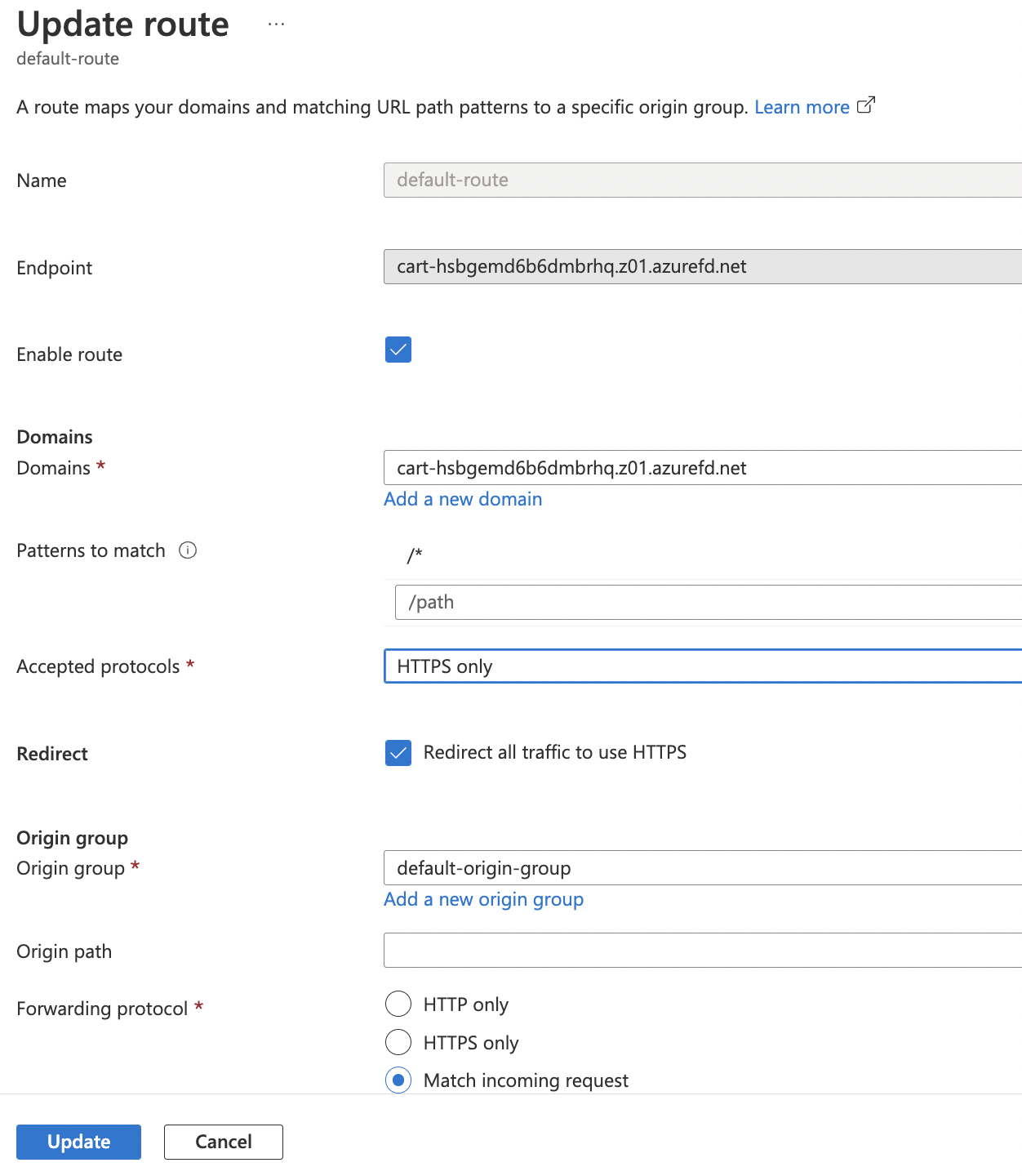
Click on the “Accepted protocols” dropdown and select “HTTPS only”. This will configure the endpoint to accept only secure traffic.
-
Ensure that the checkbox for “Redirect” is selected to “Redirect all traffic to use HTTPS”.
-
Click “Update” at the bottom of the page to save the changes.
-
Repeat steps 4 - 9 for all other CDN endpoints.