Secret Expiration Enabled
Ensures that all secrets in Azure Key Vault have an expiry time set.
Setting an expiry time on all secrets forces secret rotation and removes unused and forgotten secrets from being used.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Microsoft Azure Management Console.
-
In the search bar at the top search for Vaults and select “Key Vaults” from the search result.
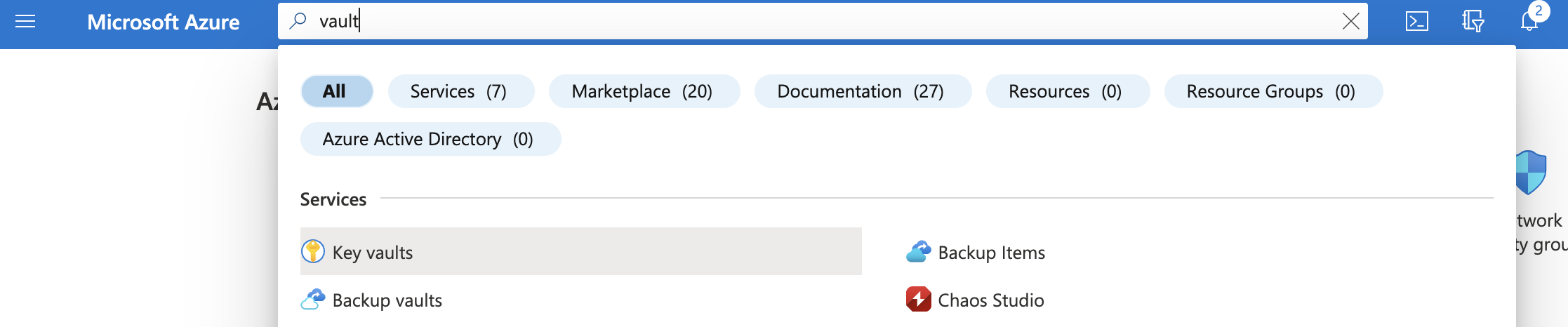
-
In the Key Vaults page, select a key vault by clicking on the “Name” link to access the configuration changes.
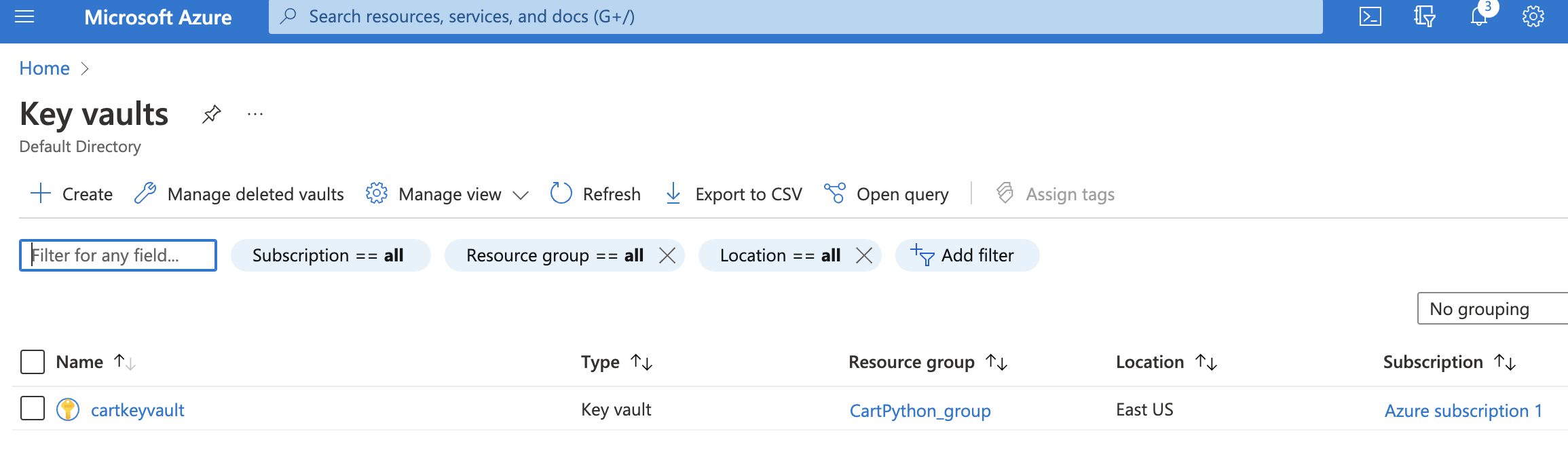
-
Scroll down and click “Secrets” from the navigation pane on the left.
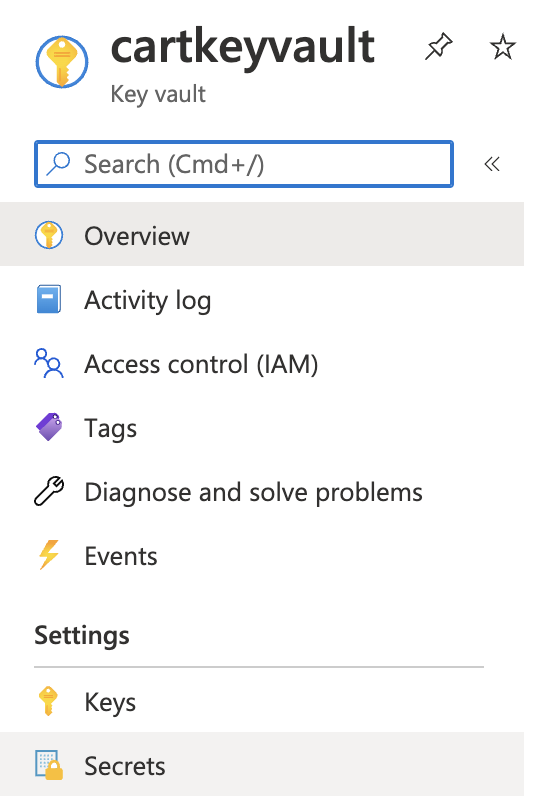
-
Then, from the list of secrets, select a secret with no expiration date under “Expiration date” column.
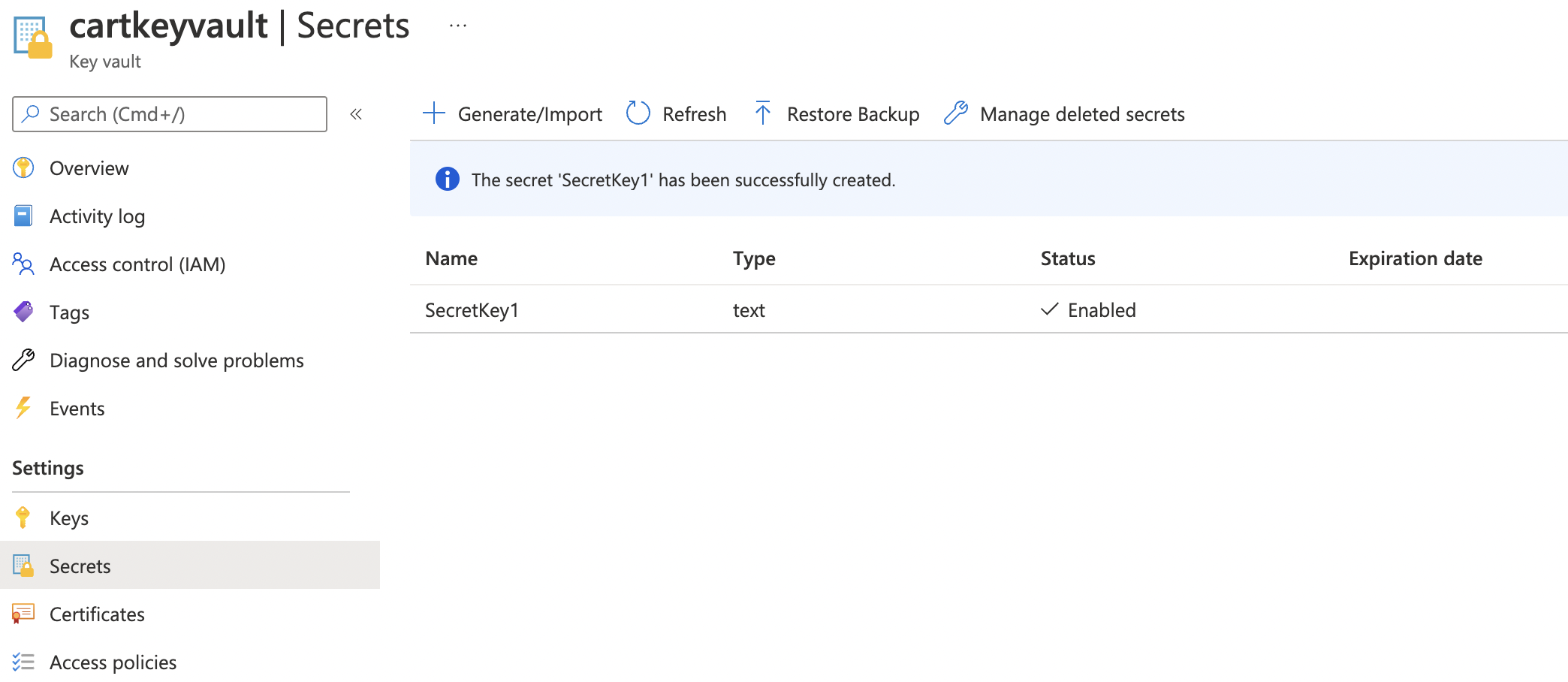
-
In the secret versions pane that opens, select the currently “Enabled” version by clicking on it.
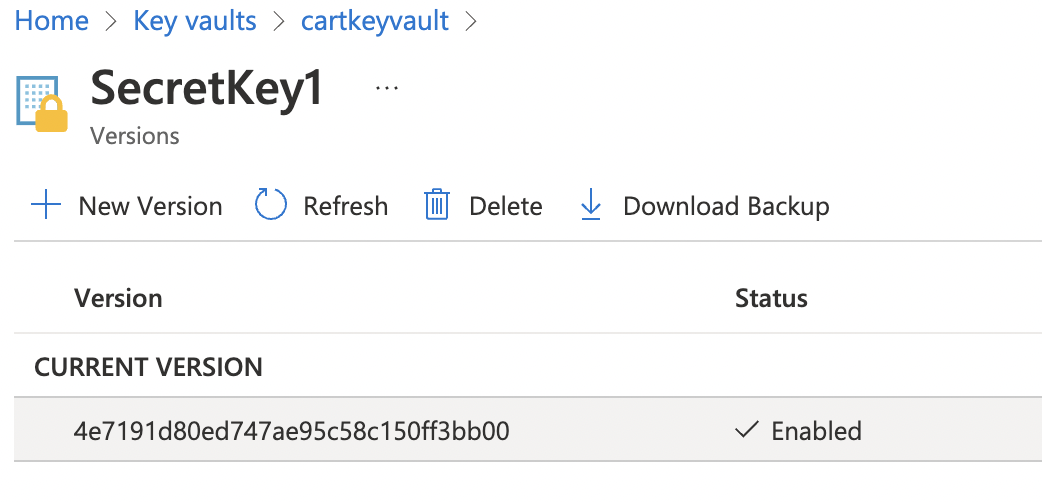
-
In the secret version pane, if the “Set expiration date” checkbox is not selected, then expiration is not set for this secret. This is a security vulnerability.
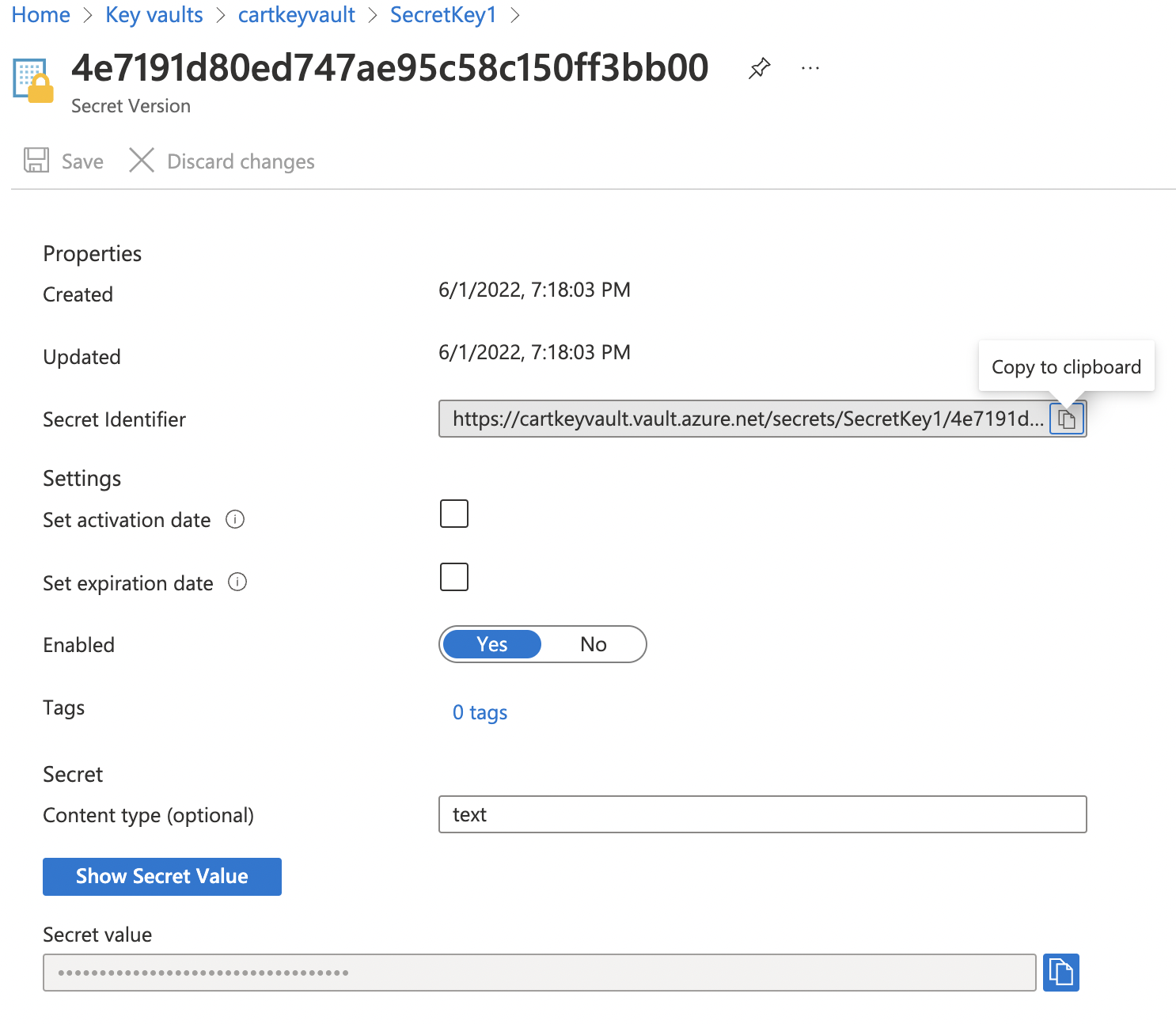
-
Select the “Set expiration date” checkbox to enable expiration.
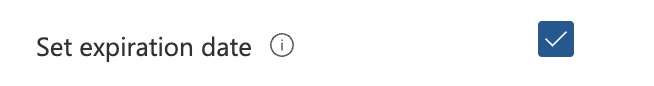
-
Now click on the calendar for “Expiration date” and select a date after 27 days to set as expiration date.
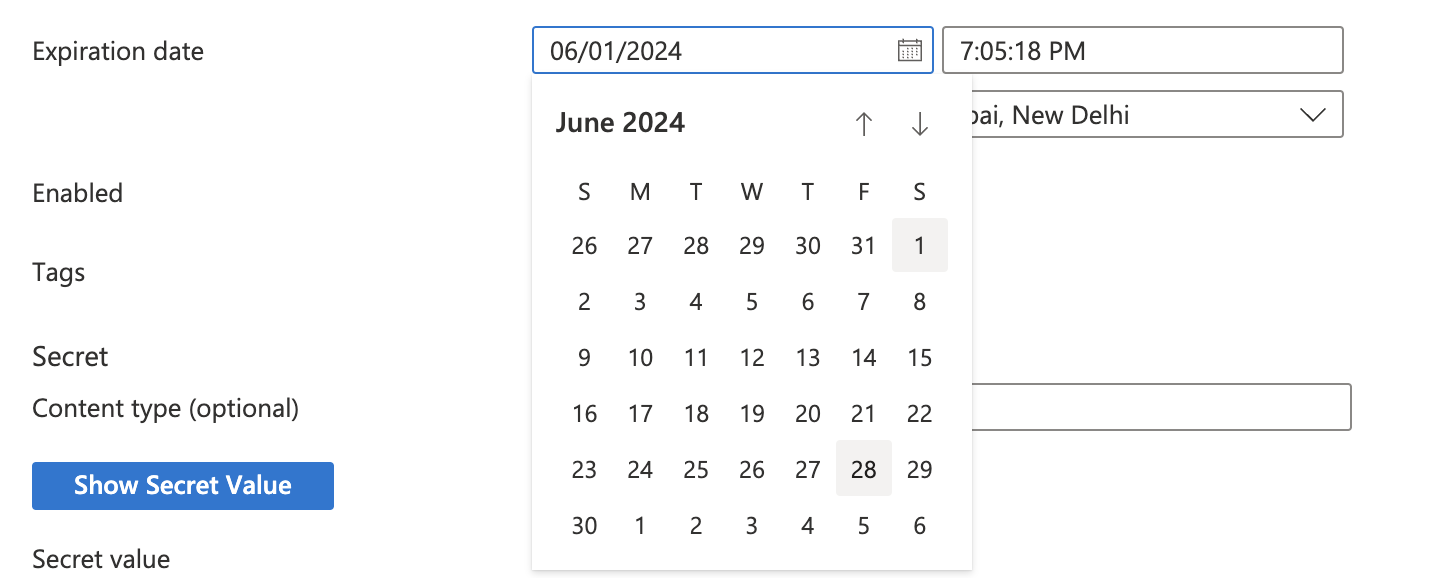
-
Finally, hit “Save” at the top of the pane to complete the changes.
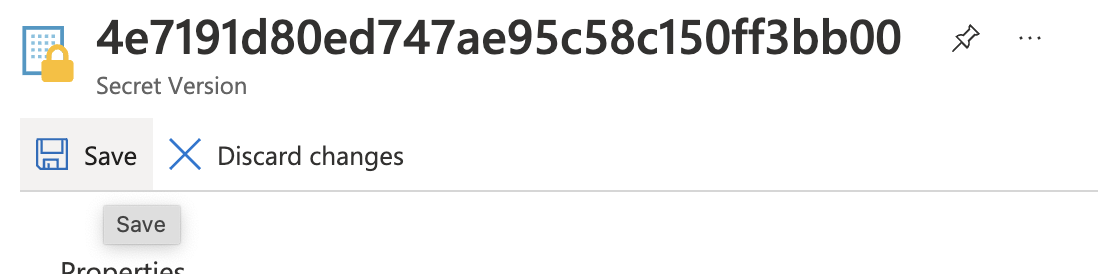
-
Repeat step number 3 - 10 for all other key vaults and keys without expiration date.