Security Policy Alerts Enabled
Ensures Activity Log alerts for create or update Security Policy Rule events are enabled
Monitoring for create or update Security Policy Rule events gives insight into policy changes and may reduce the time it takes to detect suspicious activity.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Microsoft Azure Management Console.
-
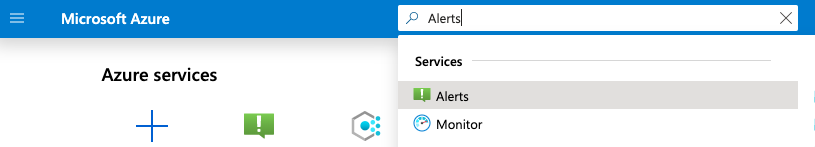
Select the “Search resources, services, and docs” option at the top and search for Alerts.
-
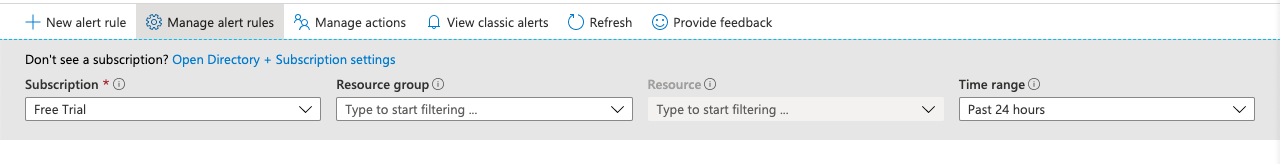
On the “Alerts” page, click on the “Manage alert rules” at the top panel.
-
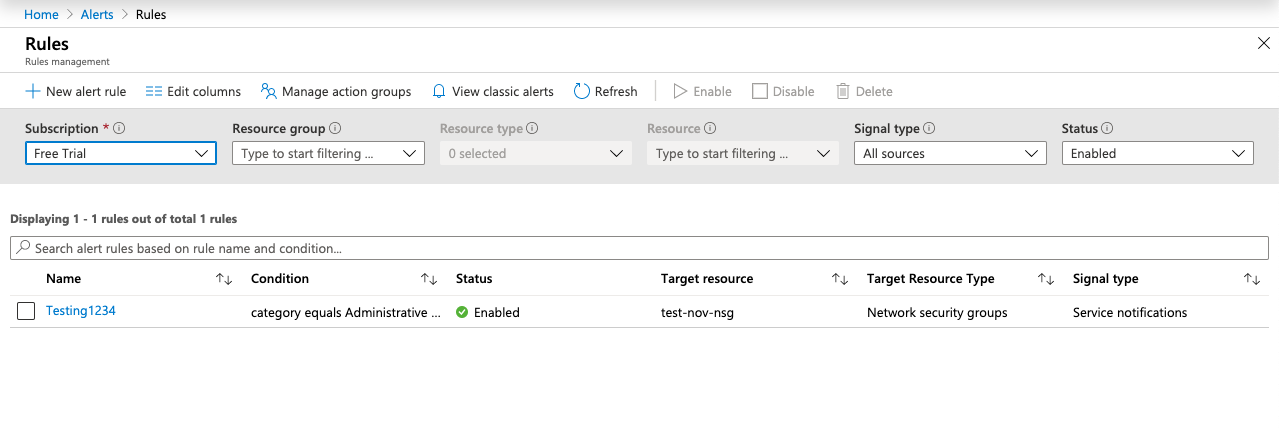
On the “Rules” page, scroll down the page and check the “Target Resource Type” and check if there is any rules for “Security Policy Alerts”. If there is no “Alerts” configured then “Activity Log Alerts” for the create or update “Security Policy Rule” events are not enabled.
-
Repeat steps number 2 - 4 to check other Azure accounts.
-
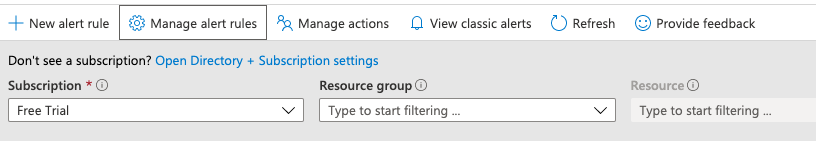
Navigate to the “Alerts” and click on the “New alert rule” at the top.
-
On the “Create rule” page, click on the “Select” option under the “Resources” and search for “Security Policy (policies)” from the “Filter by resource type” and select the “Resource” accordingly.
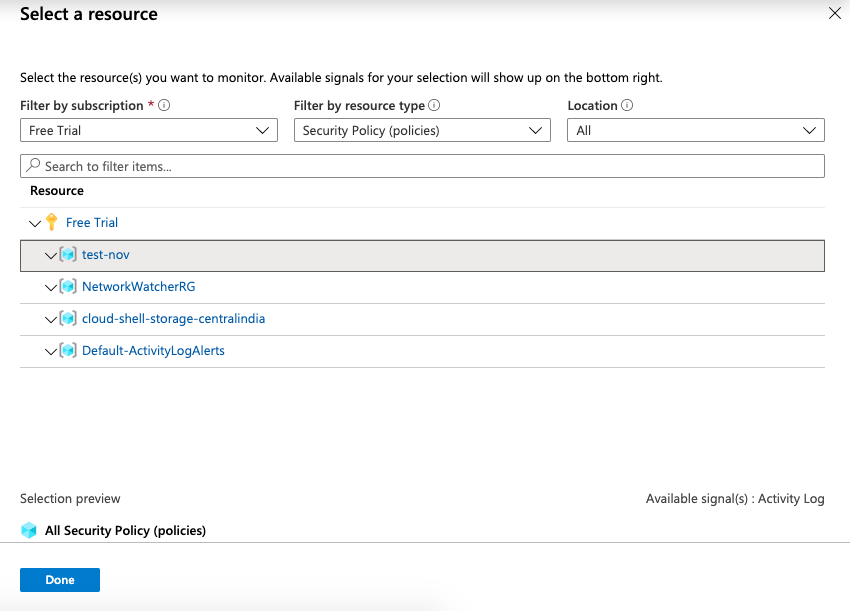
-
On the “Create rule” page, click on the “Add” option under the “Condition” and select “All Security Operations” from the options and click on the “Done” option at the bottom of the tab.
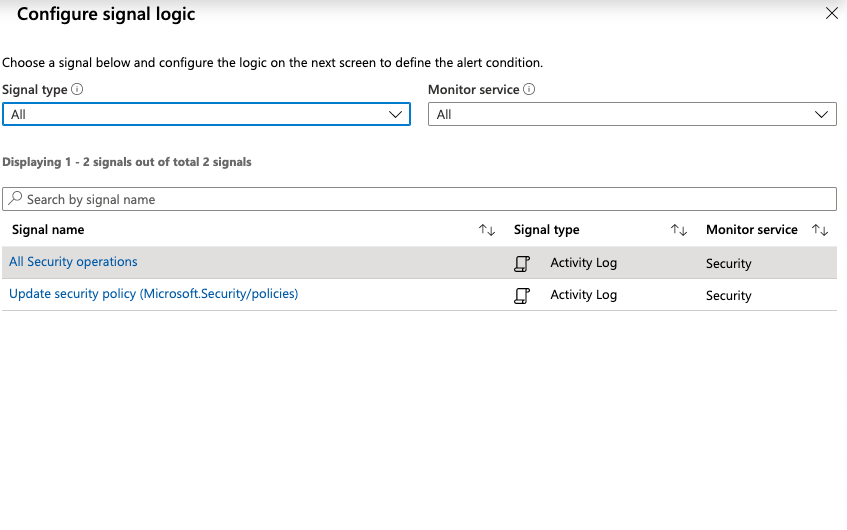
-
Under the “Actions”, select the “Action group” or “Create action group” accordingly.
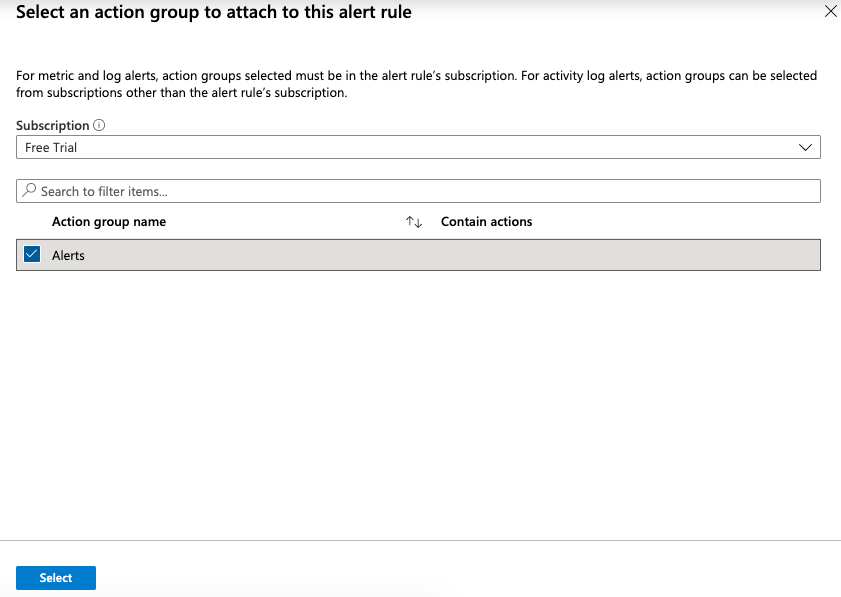
-
Enter the “Alert rule name” and “Description” under the “Alert Details” and click on the “Yes” button under the “Enable rule upon creation” to quickly enable the “Security Policy Alerts”. Click on the “Create alert rule” button at the bottom to create a rule.
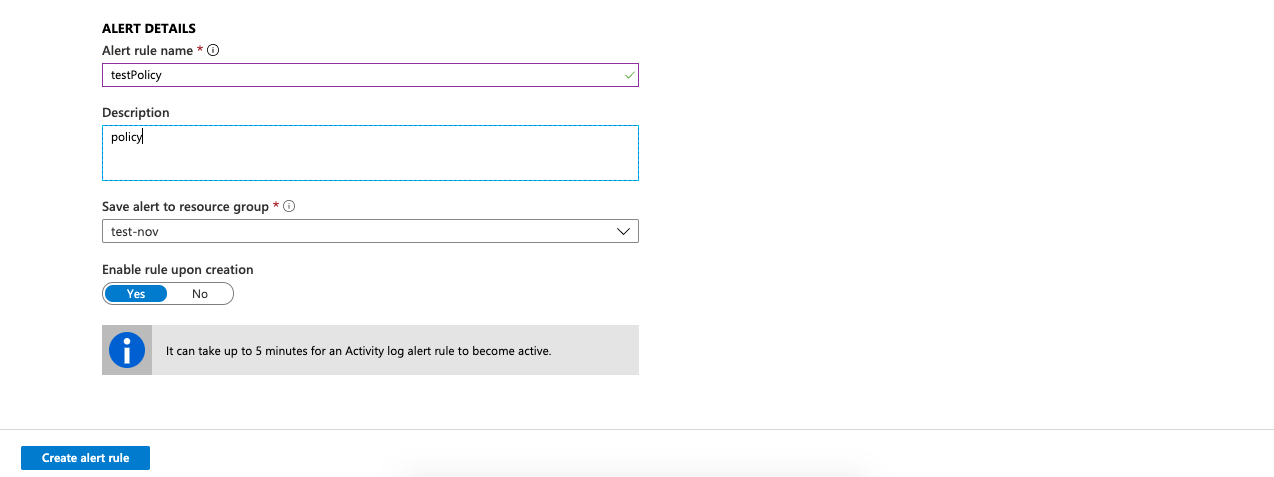
-
Repeat steps number 6 - 10 to add a new log alert to the Alerts service that monitors for Security Policy Rule create or update events.