Excessive Security Groups
Determines if there are an excessive number of security groups in the account
Keeping the number of security groups to a minimum helps reduce the attack surface of an account. Rather than creating new groups with the same rules for each project, common rules should be grouped under the same security groups. For example, instead of adding port 22 from a known IP to every group, create a single “SSH” security group which can be used on multiple instances.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Microsoft Azure Management Console.
-
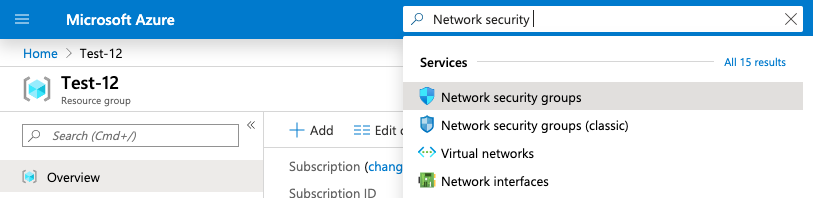
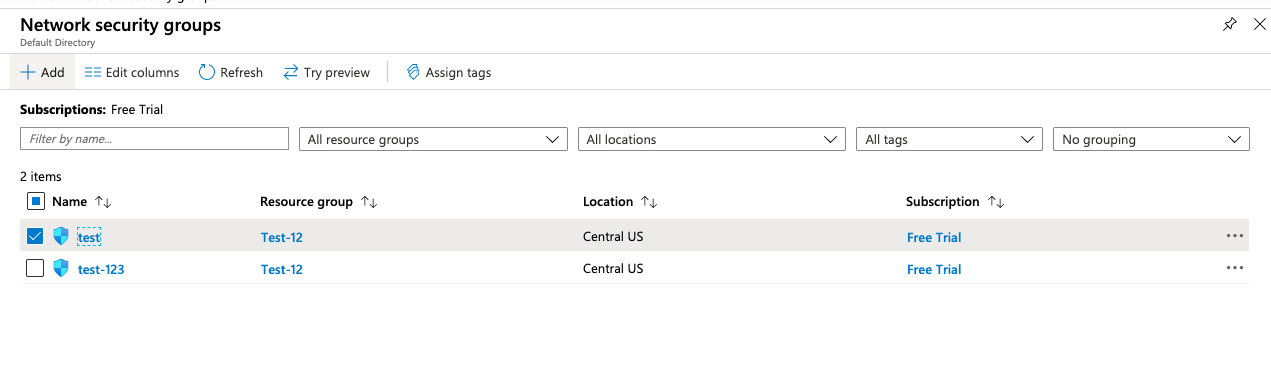
Select the “Search resources, services, and docs” option at the top and search for Network security groups.
-
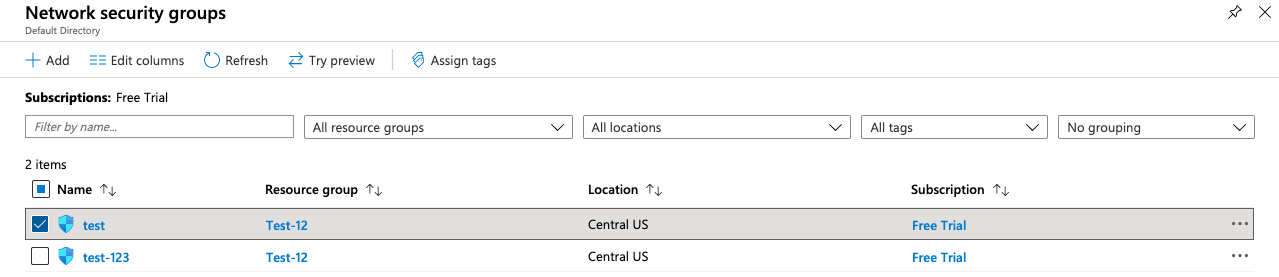
Verify the number of Security Groups which are having the same security rules and used separately.
-
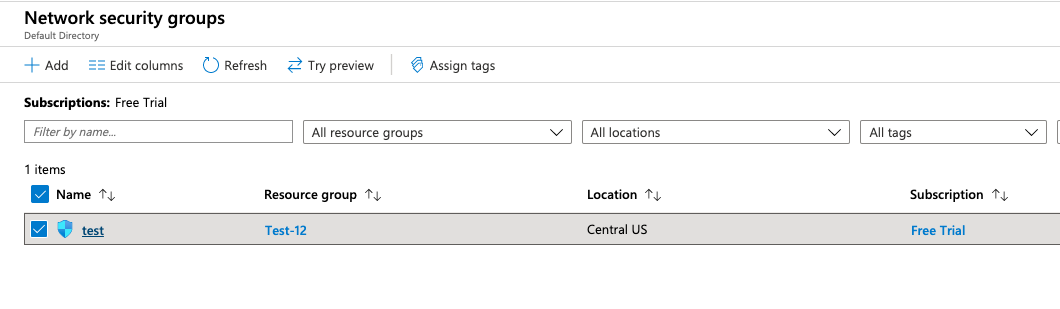
Click on the “Name” of the selected “Network security group” to access the port configurations.
-
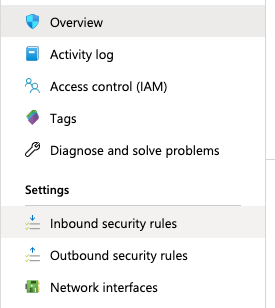
In the “Overview” tab scroll down the page and check the “Inbound security rules.”
-
Copy the Inbound and Outbound “security rules” which are in common in both the security groups.
-
Repeat steps number 2 - 6 to verify other “Security Groups” in the account.
-
Navigate to the “Network security group” and click on the “Add” button at the top to add new security groups having common security rules.
-
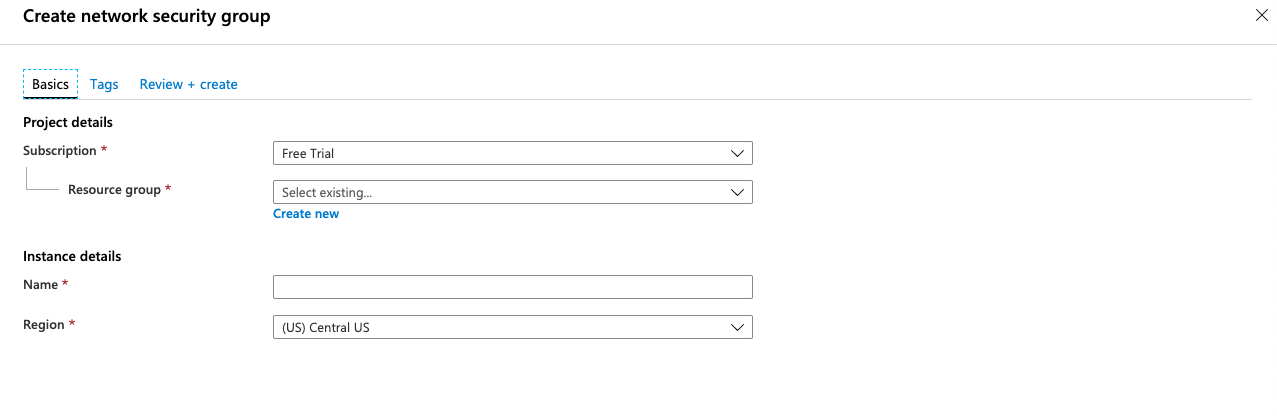
On the “Create a network security group” page enter the details Resource Group, Name, Details and click on the “Review+Create” button to make the changes.
-
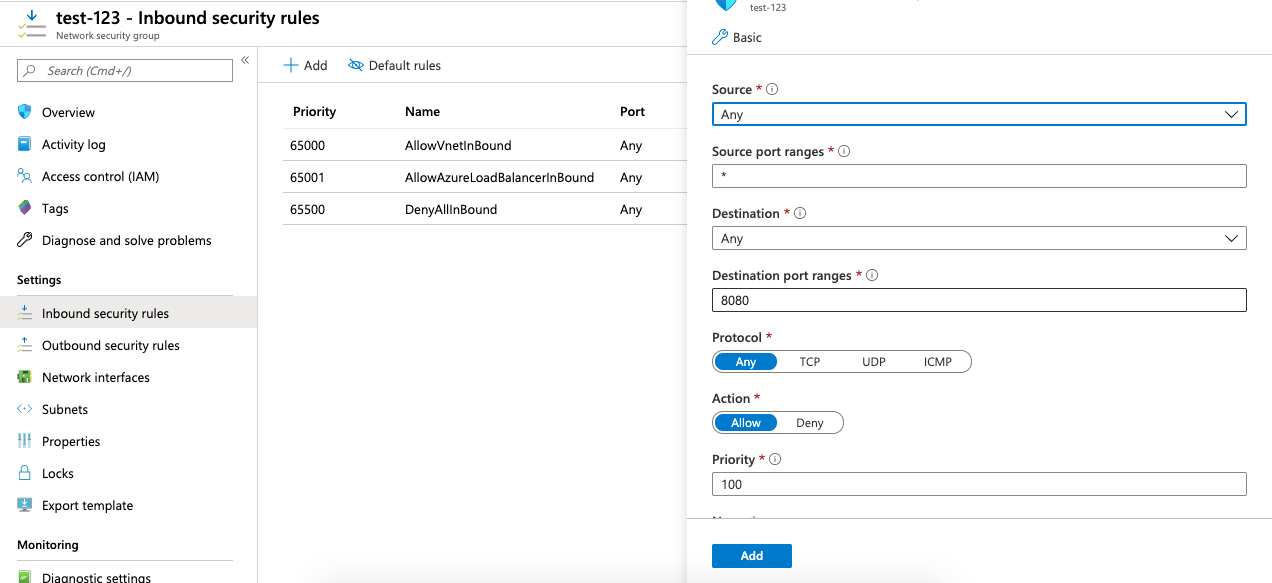
Click on the newly created “Network Security Group” and select the “Inbound security rules” under Security.
-
Click on the “Add” button at the top and paste the rules copied in Step 6.
-
Once the new security group has all the same rules, navigate to the “Resources” using those Security Groups and change the groups accordingly.
-
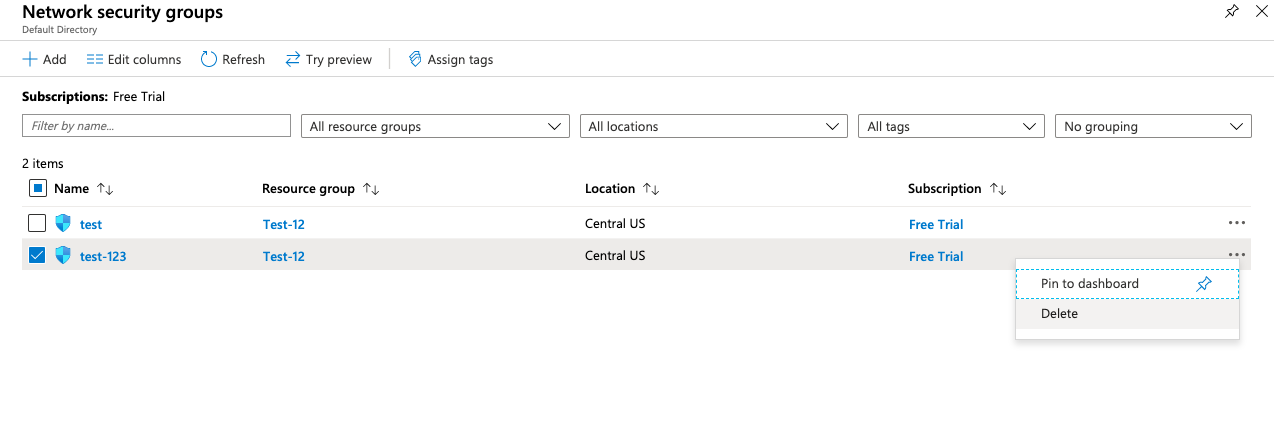
Navigate to “Network Security Group” and delete the old “Security Groups” to prevent accidental authorizations.
-
Repeat steps number 8 - 13 to limit the number of security groups to prevent accidental authorizations.