Open All Ports
Ensures Network Security Groups do not expose all ports to the public
While some ports such as HTTP and HTTPS are required to be open to the public to function properly, almost all services should be restricted to known IP addresses.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Microsoft Azure Management Console.
-
Click on the search bar and search for Network security groups.
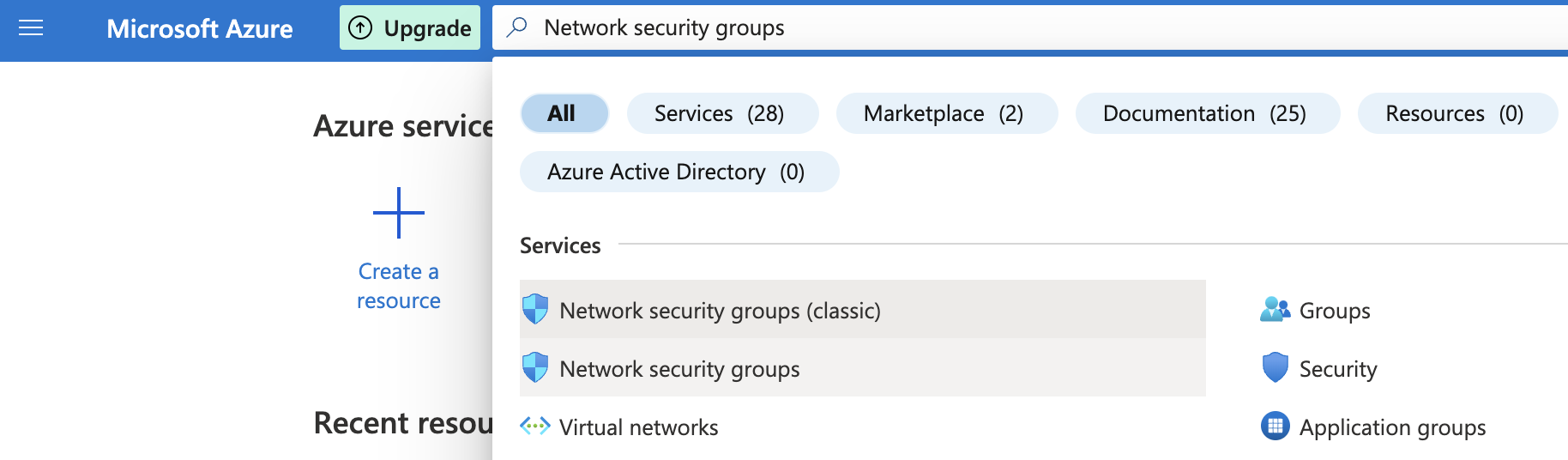
-
Select the “Network security group” that needs to be verified.
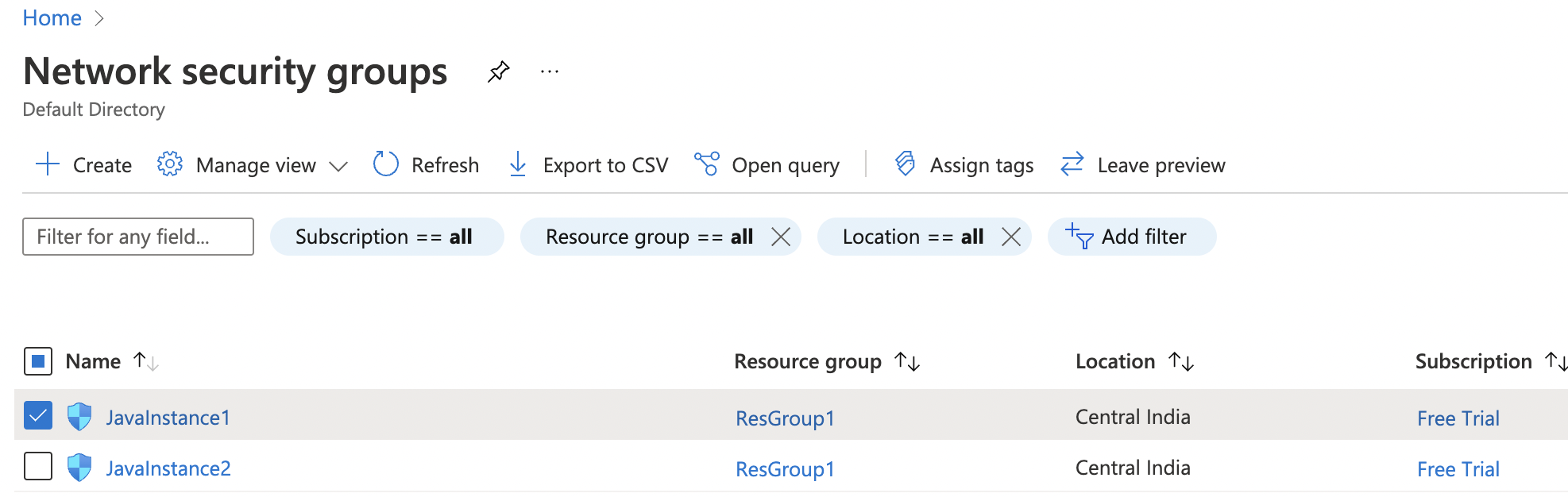
-
Click on the “Name” of the selected “Network security group” to access the port configurations.
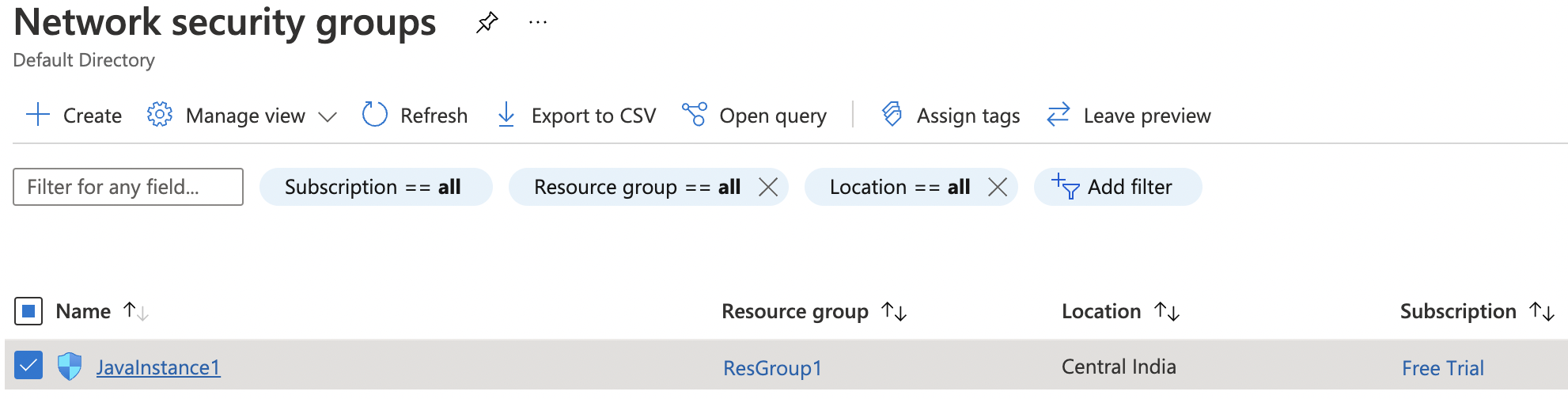
-
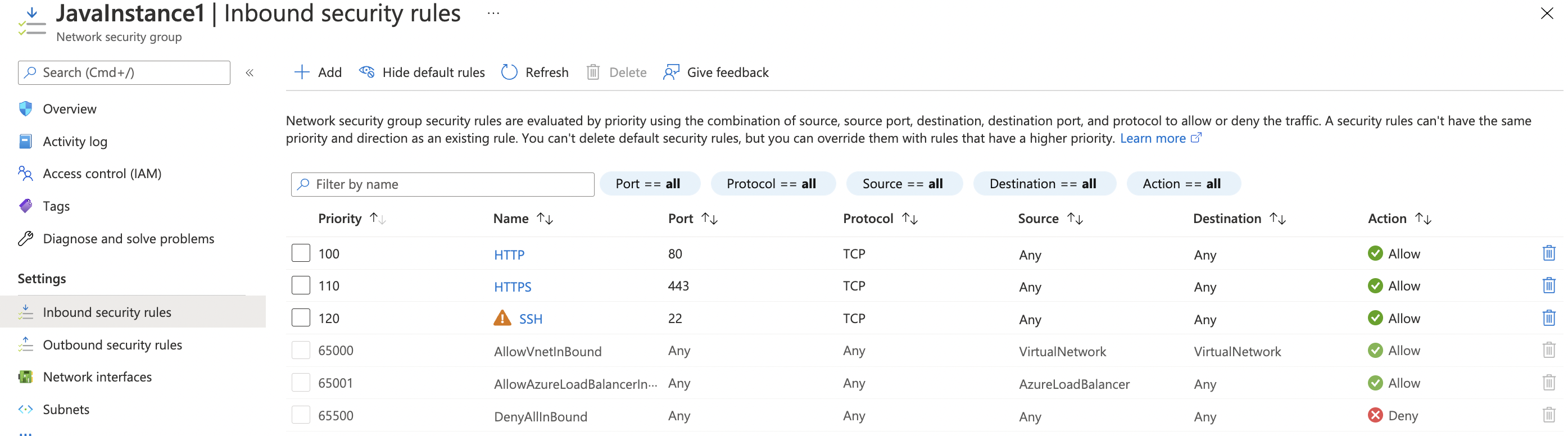
In the “Overview” tab scroll down the page and check the “Inbound security rules.”
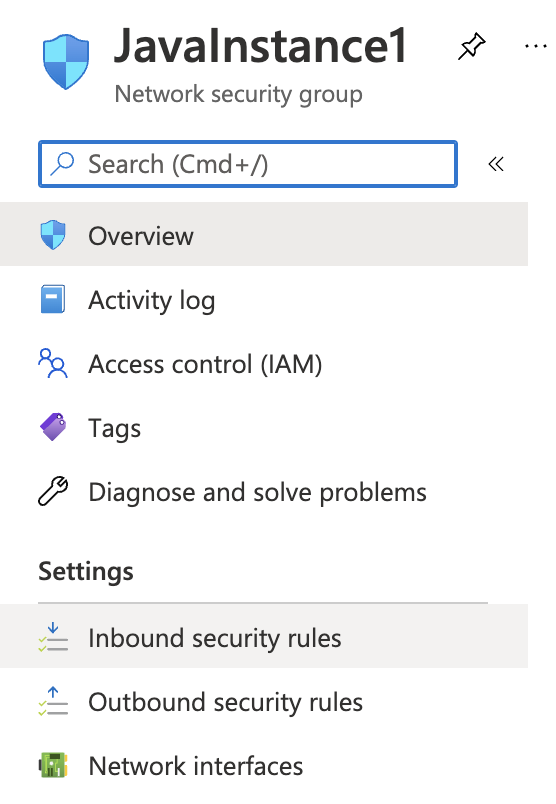
-
On the “Inbound security rules” page under the “Settings”, please verify all the ports apart from HTTP/HTTPS are not open to public and if any port such as SSH is open to the public then it’s not as per the recommendation of Azure best practices.
-
Repeat step number 2 - 6 to verify other “Network security groups”.
-
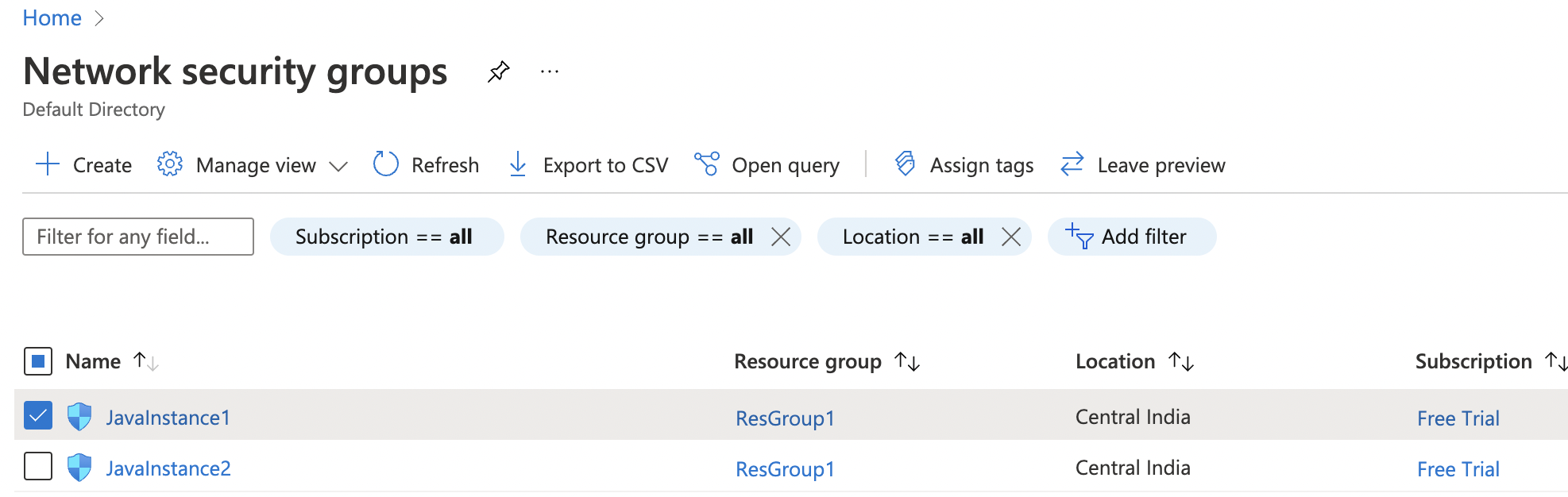
Navigate to the “Network security group” and select the security group that needs to modify for restricting the other ports to specific IP Address.
-
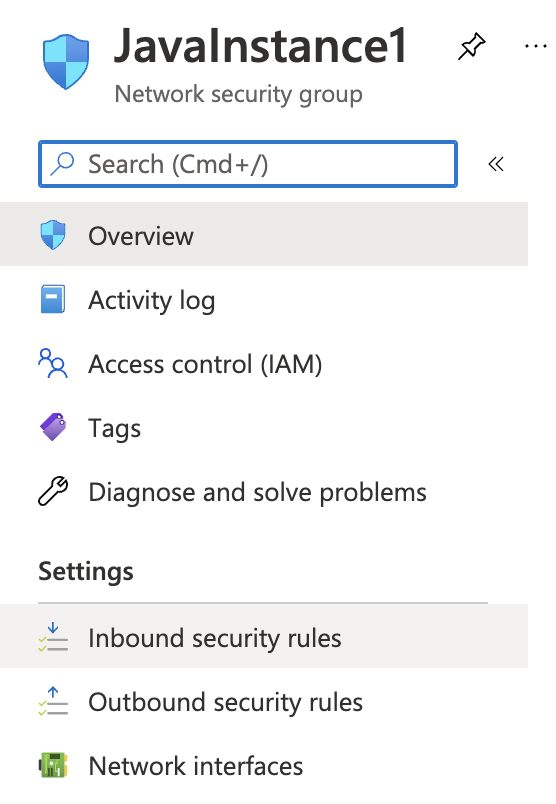
Scroll down the left navigation panel and choose “Inbound security rules” under “Settings”.
-
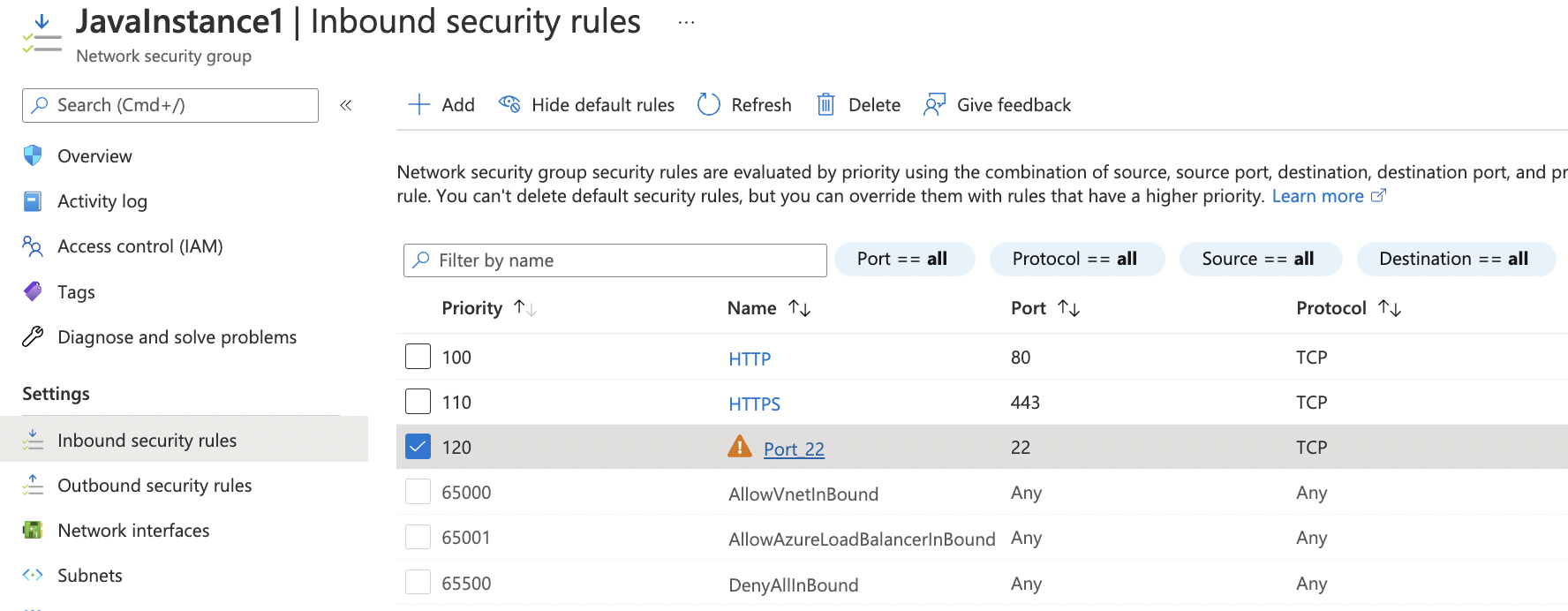
Click on “Name” column of the “SSH or any” protocol you want to modify.
-
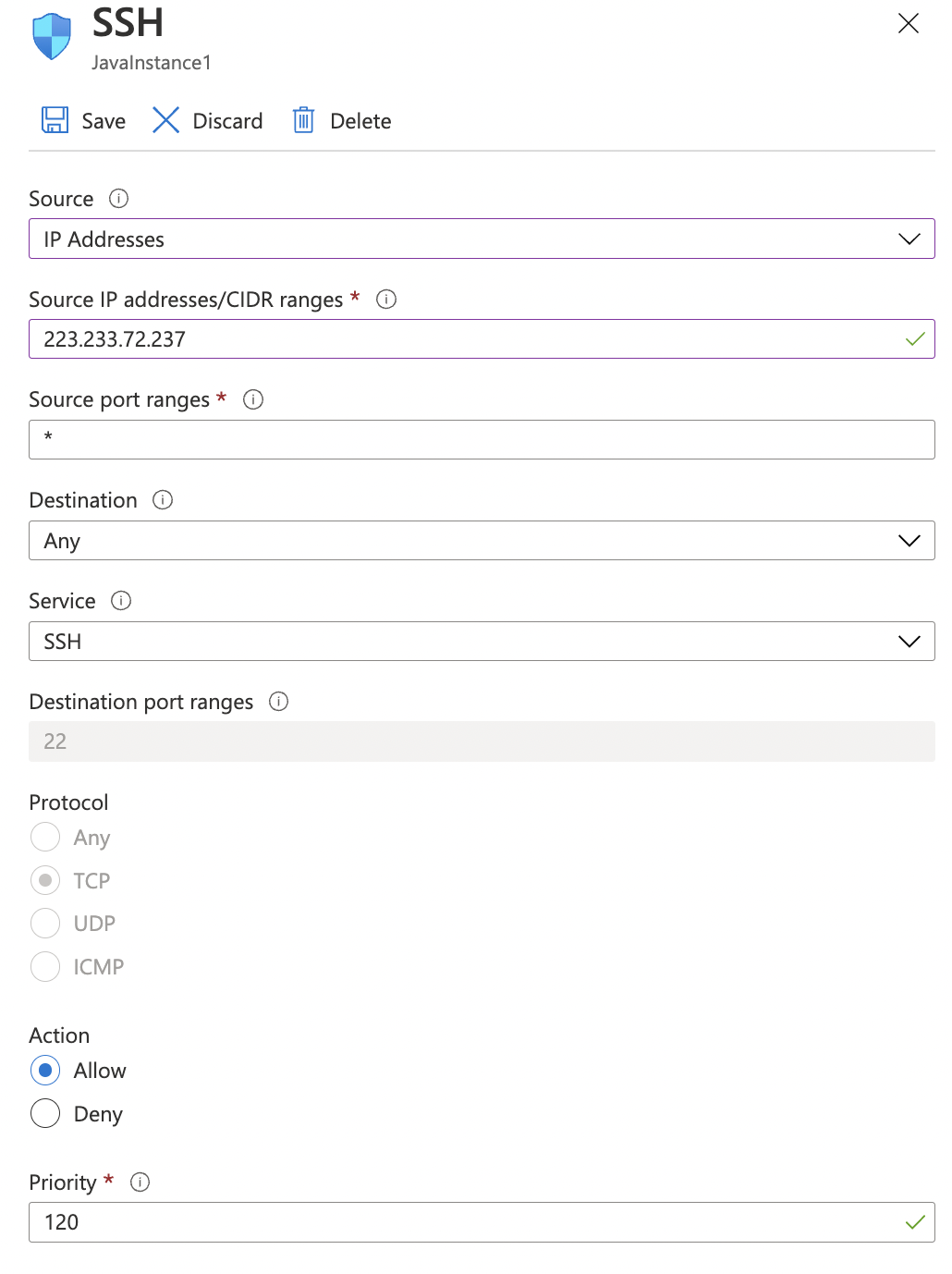
In the right pane, under “Source” select the “IP Addresses” from the dropdown menu and enter the “Source IP addresses/CIDR ranges” as per the requirement, select the required Protocol and Action, enter the priority and click on the “Save” option at the top of the pane.
-
Repeat step number 8 - 11 to restrict ports to known IP addresses.