Enforce PostgreSQL SSL Connection
Ensures SSL connections are enforced on PostgreSQL Servers
SSL prevents infiltration attacks by encrypting the data stream between the server and application.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Microsoft Azure Management Console.
-
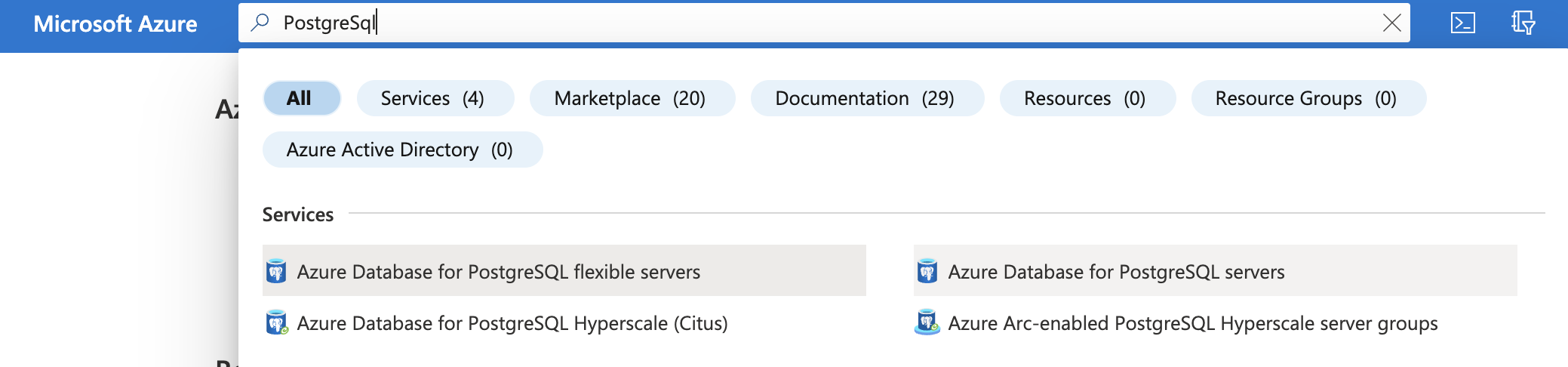
Select the “Search resources, services, and docs” option at the top and search for PostgreSQL.
-
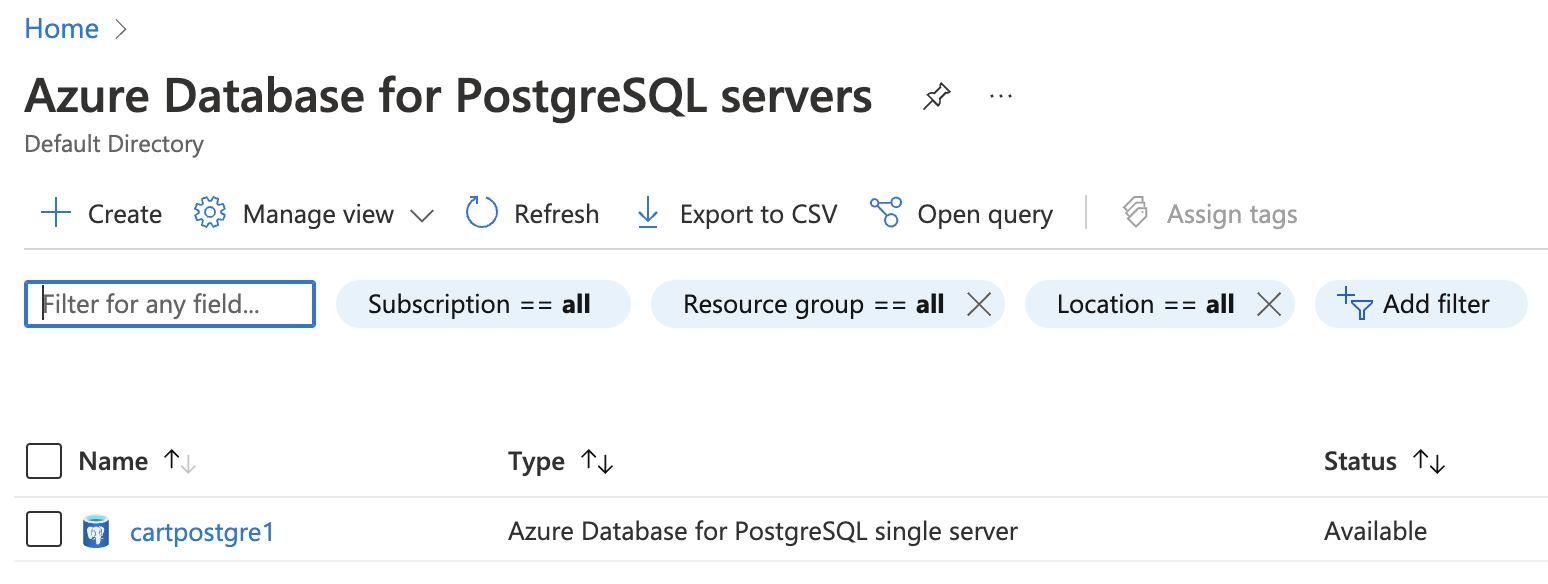
On the “Azure Database for PostgreSQL servers” page, select the database by clicking on the “Name” as a link that needs to be examined.
-
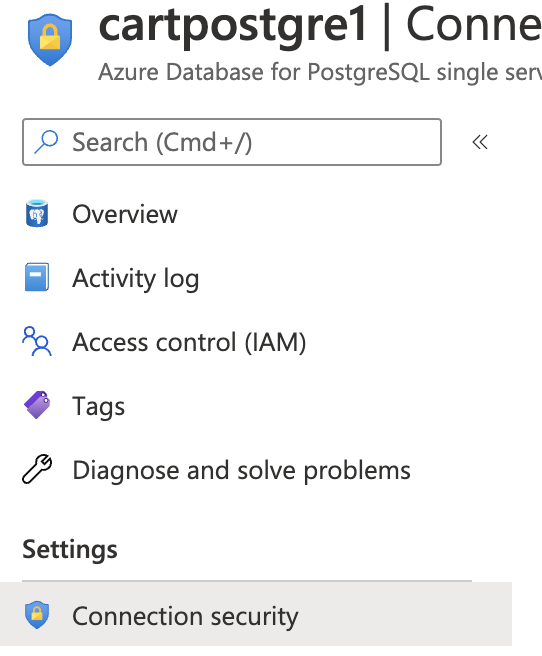
Scroll down the left navigation panel and choose “Connection Security” under “Settings.”
-
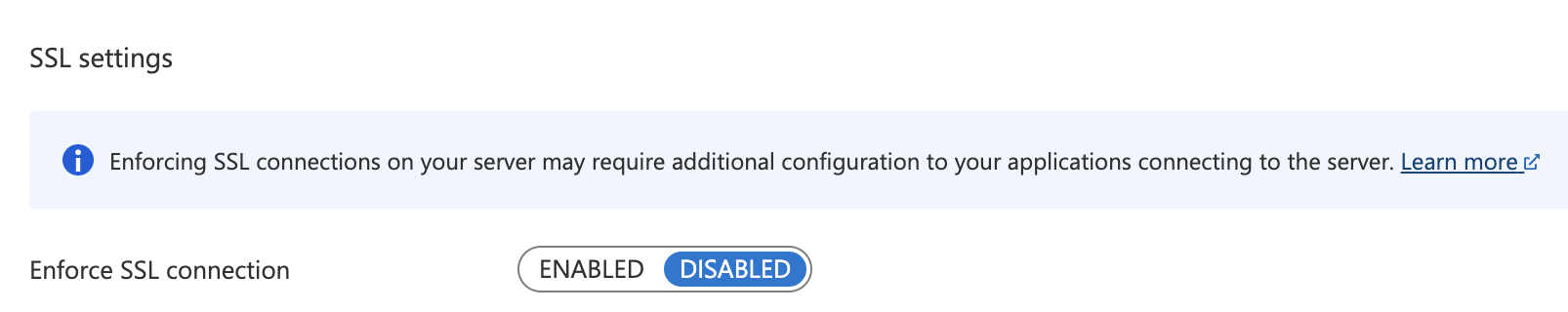
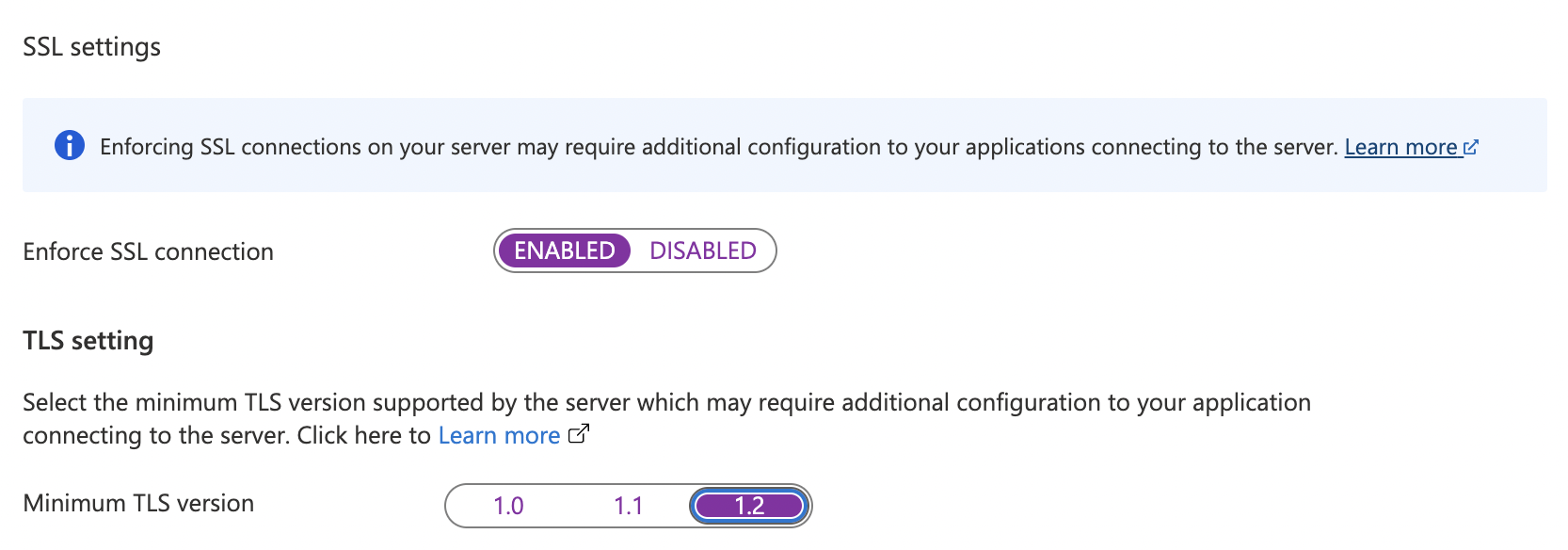
On the “Connection Security” page, search for “SSL settings”. If the Enforce SSL connection is set to “DISABLED” this is a security risk as data is transmitted unencrypted. This is against azure best practices.
-
To enable the “SSL Connection” select “ENABLED” from the toggle configuration button. In the “TLS setting” select the highest version “1.2” as of now.
-
Click on the “Save” button at the top to make the changes.

-
Repeat step number 3 - 7 to ensure the server parameters for each PostgreSQL server have the ssl connection enabled.