Log Retention Period
Ensures logs are configured to be retained for 4 or more days for PostgreSQL servers
Having a long log retention policy ensures that all critical logs are stored for long enough to access and view in case of a security incident.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Microsoft Azure Management Console.
-
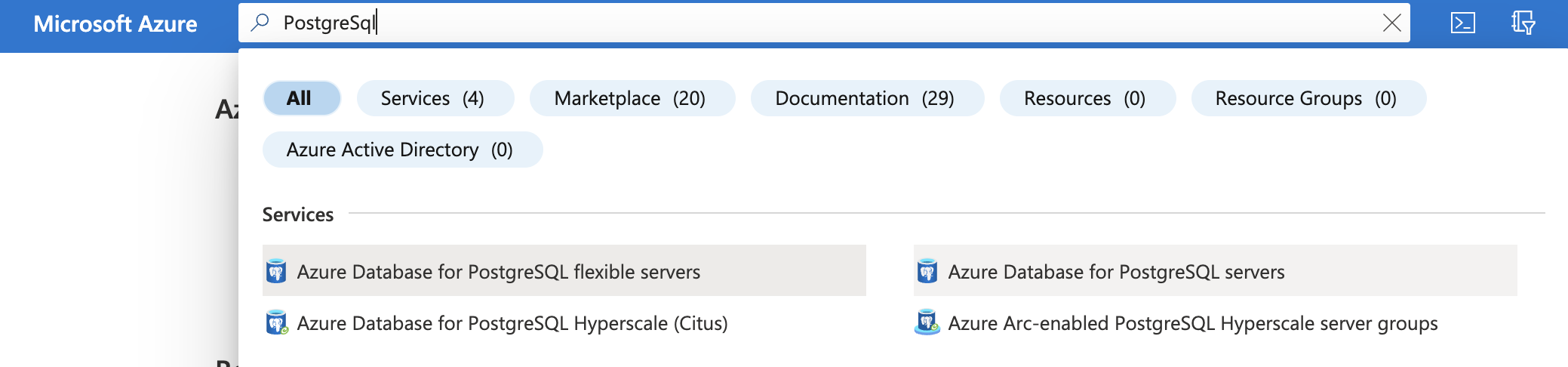
Select the “Search resources, services, and docs” option at the top and search for PostgreSQL.
-
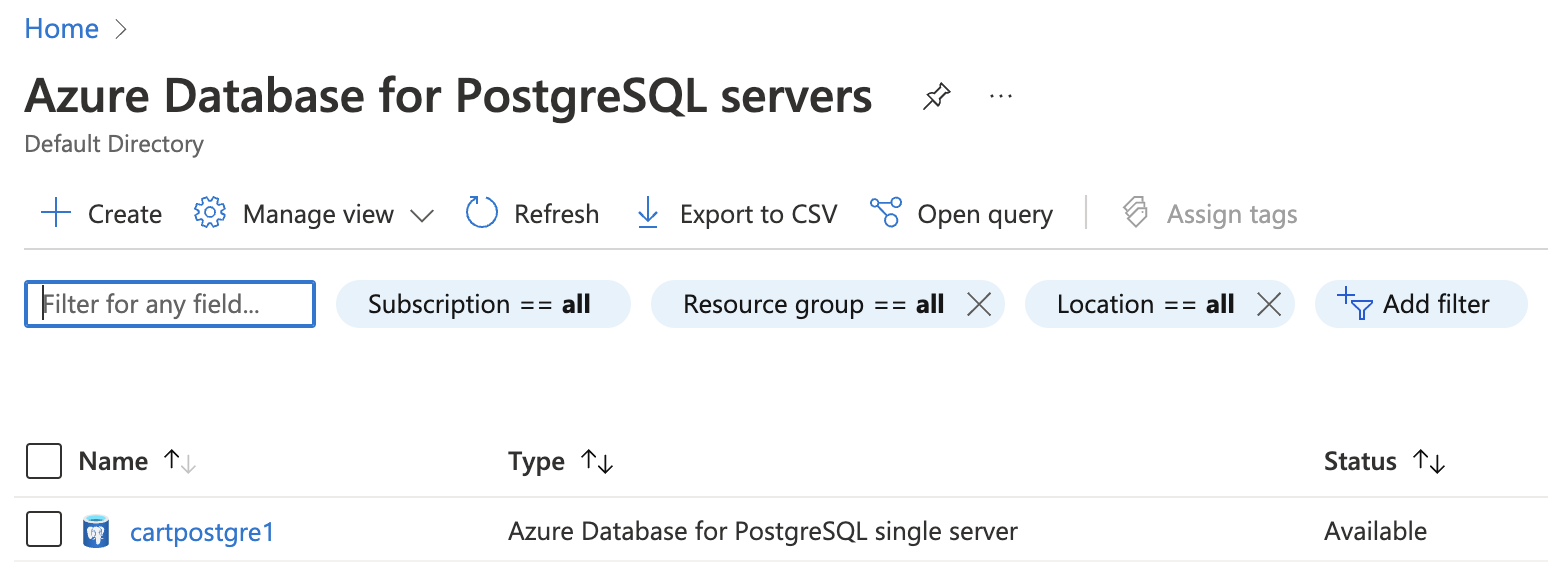
On the “Azure Database for PostgreSQL servers” page, select the database by clicking on the “Name” as a link that needs to be examined.
-
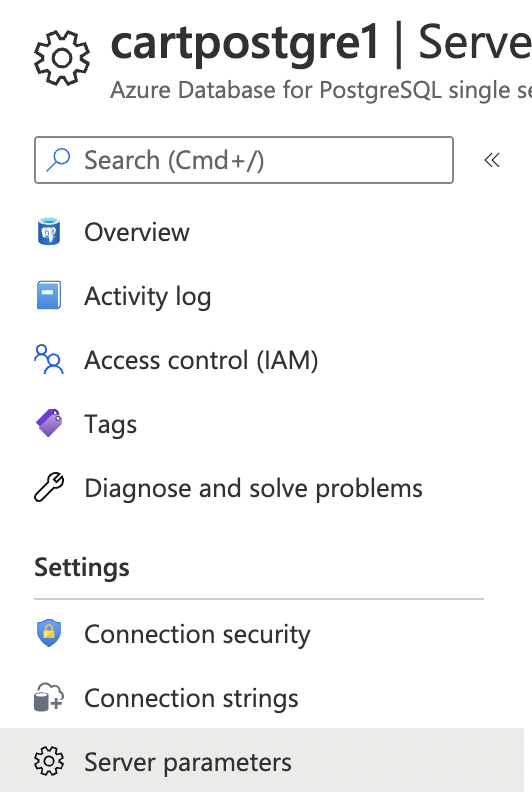
Scroll down the left navigation panel and choose “Server parameters” under “Settings.”
-
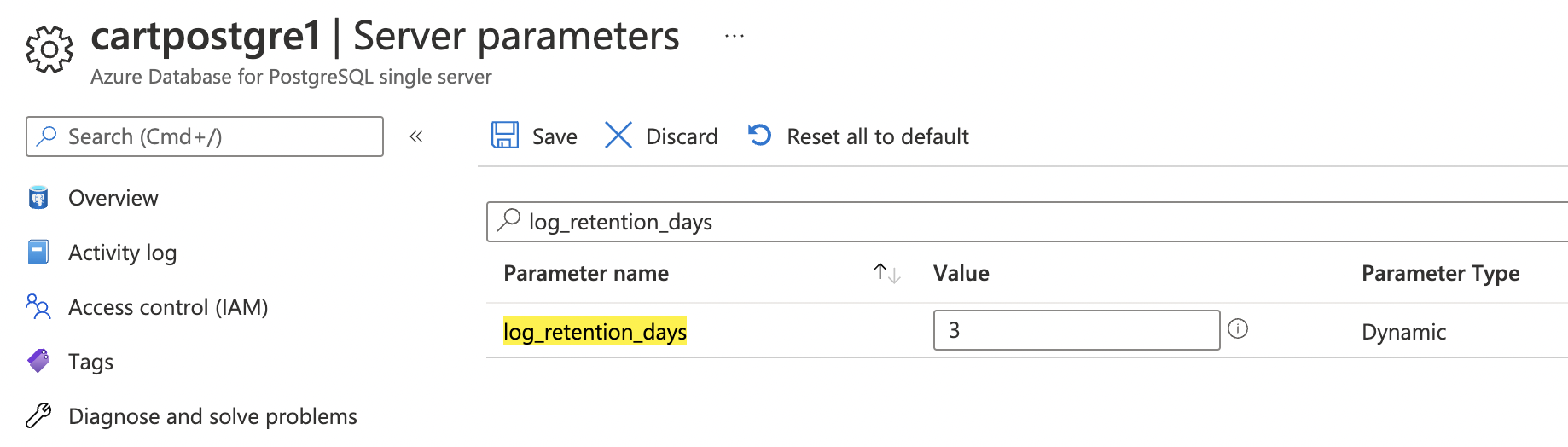
On the “Server parameters” page, search for “log_retention_days” paramter using the “Search for filter item search box.” If the value is set to less than “3 days” then the “log_retention_days” is not as per best practices for PostgreSQL servers.
-
To increase the value of log_retention_days set the “log_retention_days” by typing the “Value” to more than “4” days in the textbox.

-
Click on the “Save” button at the top to make the changes.

-
Repeat step number 3 - 7 to ensure the server parameters for each PostgreSQL server have the log_retention_days setting set to 4 or more days.