Queue Service All Access ACL
Ensures queues do not allow full write, delete, or read ACL permissions
Queues can be configured to allow object read, write or delete. This option should not be configured unless there is a strong business requirement.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Microsoft Azure Management Console.
-
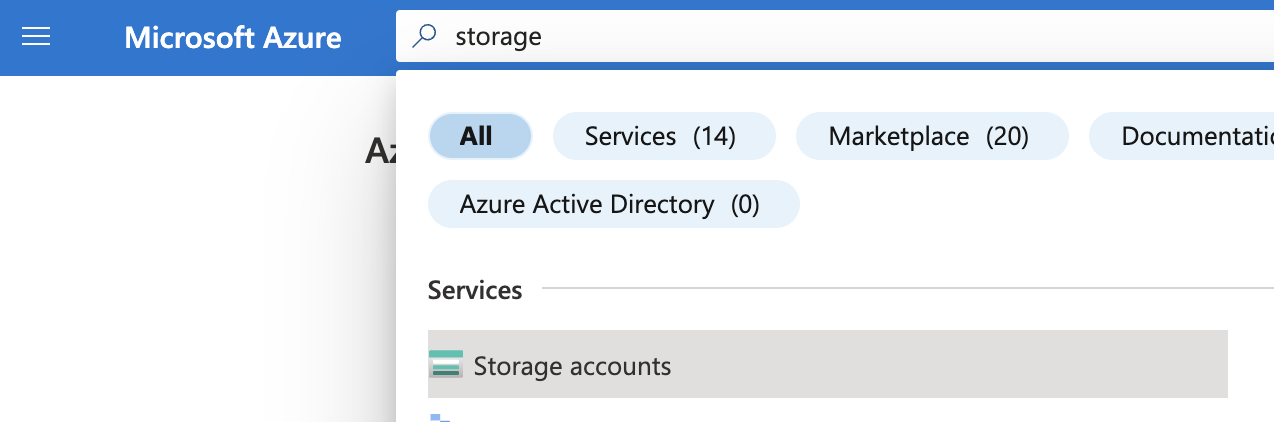
In the search bar at the top search for Storage and select “Storage accounts” from the result.
-
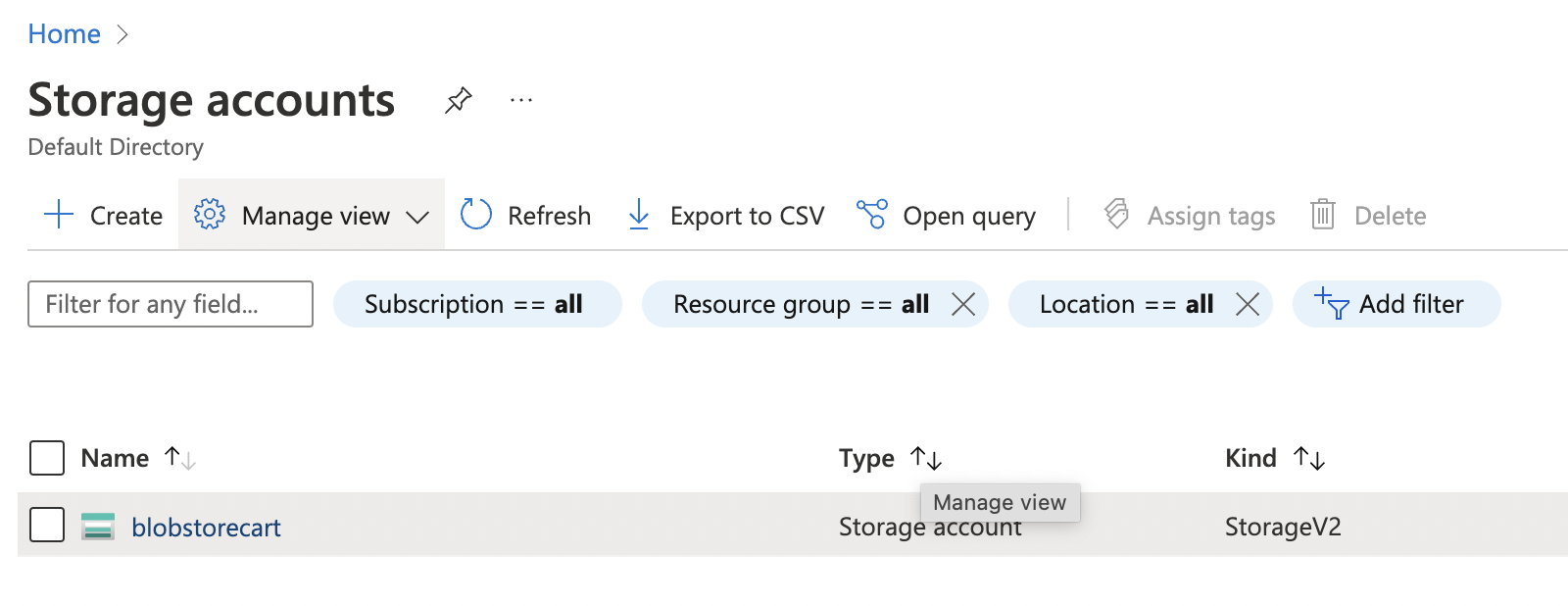
Select the “Storage account” by clicking on the “Name” link to access the configuration changes.
-
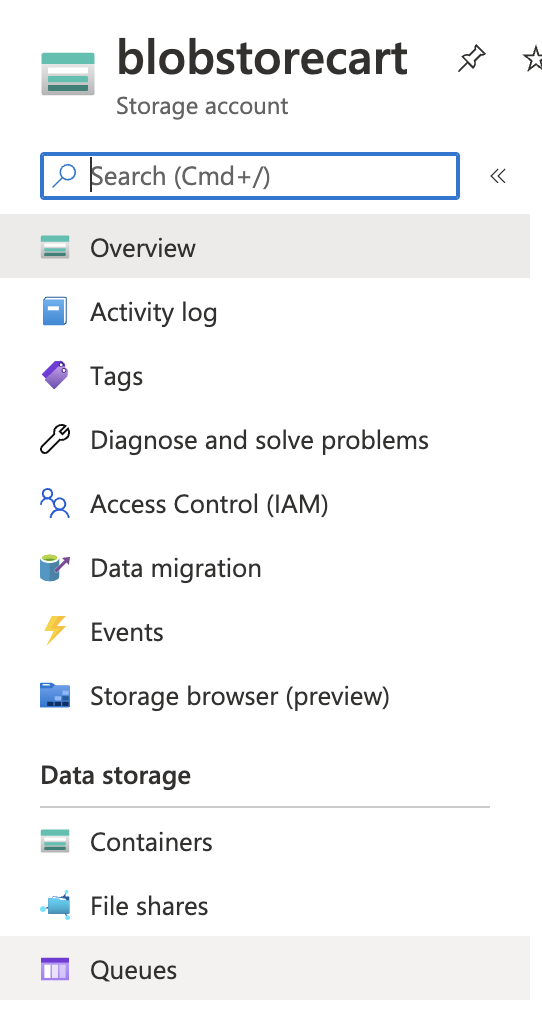
In the left navigation panel, scroll down and click on the “Queues” option under “Data storage”.
-
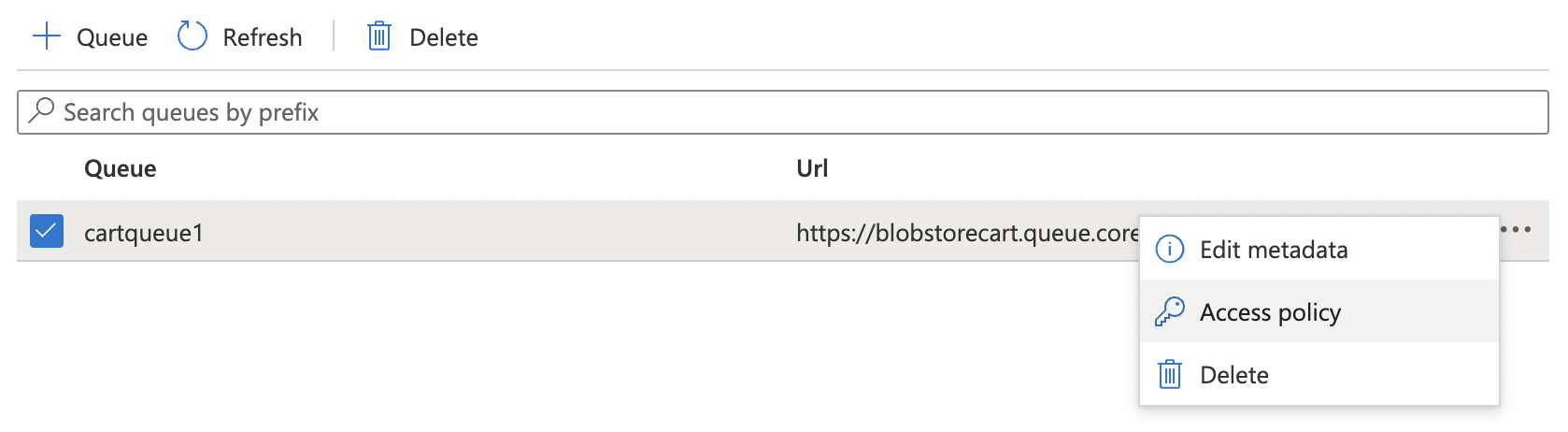
Select the “Queue” by clicking on the triple dots (…) at the end of the row and click “Access policy”.
-
On the “Access Policy” panel check the “Permissions” associated with the “Queue”. If it says “raup” then the queue allows full write, delete, or read ACL permissions and is not as per the security recommendations.
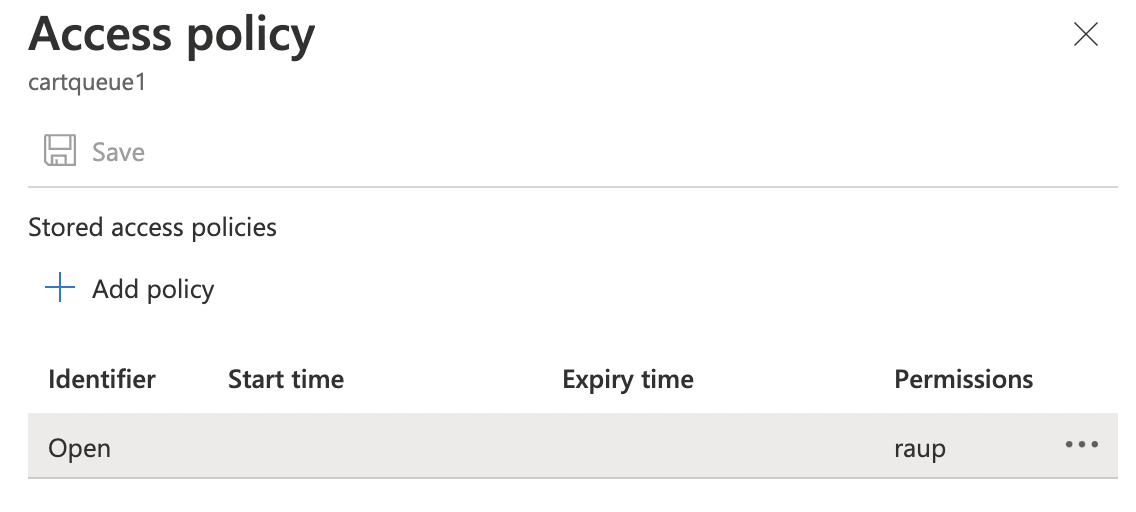
-
Click the triple dots (…) and click “Edit” option to make changes.
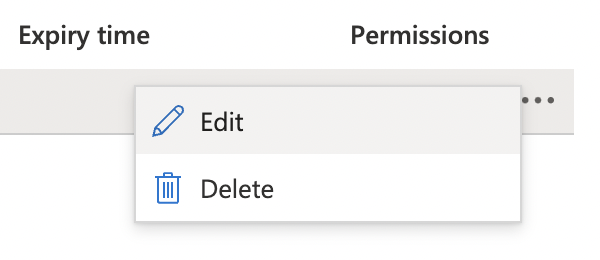
-
In the “Edit policy” pop up that opens, click the “Permissions” dropdown, uncheck the global read and update policies, then click on the “OK” button to save the changes.
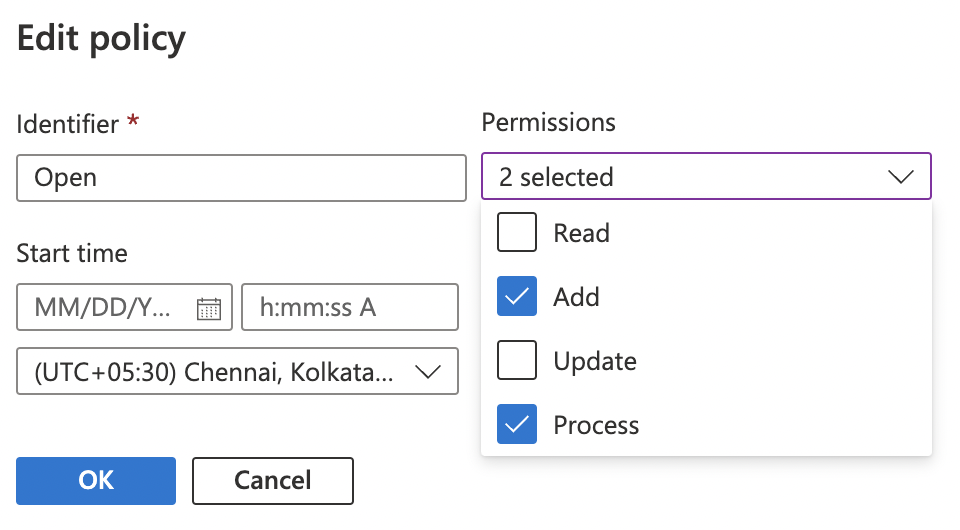
-
Click on the “Save” button at the top to save the configuration changes.
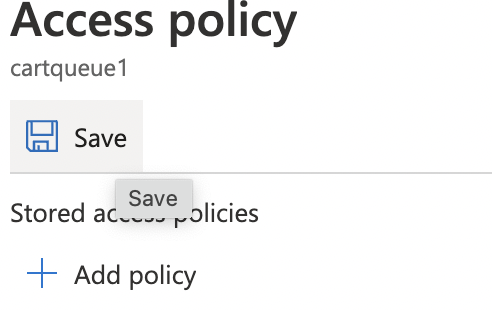
-
Repeat step number 4 - 9 to check all other “Queues” do not allow full write, delete, or read ACL permissions.