Audit Action Groups Enabled
Ensures that SQL Server Audit Action and Groups is configured properly
SQL Server Audit Action and Groups should be configured to at least include SUCCESSFUL_DATABASE_AUTHENTICATION_GROUP, FAILED_DATABASE_AUTHENTICATION_GROUP and BATCH_COMPLETED_GROUP.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Microsoft Azure Management Console.
-
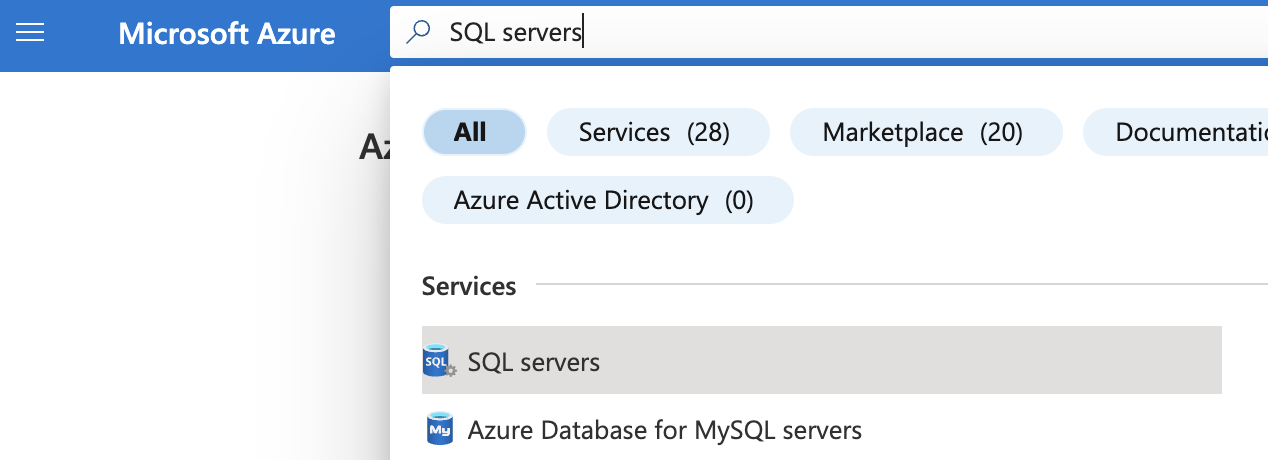
Select the “Search resources, services, and docs” option at the top and search for “SQL servers”.
-
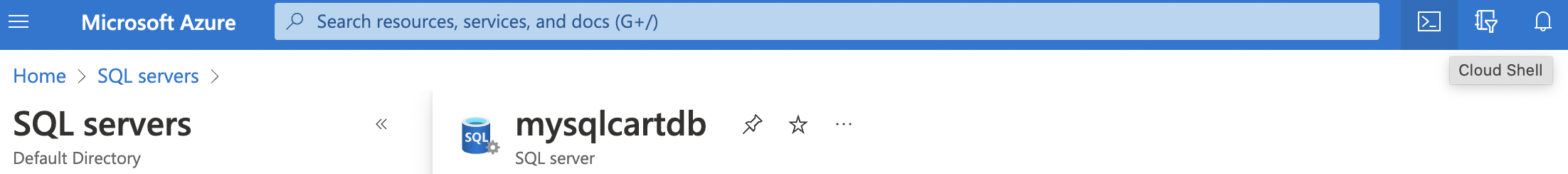
On the “SQL server” page, click on the “Cloud shell” icon at the top next to the search bar as “Audit Action Groups Enabled” cannot be checked from Azure “UI Console”.
-
In the box that opens at the bottom, select “PowerShell”.

-
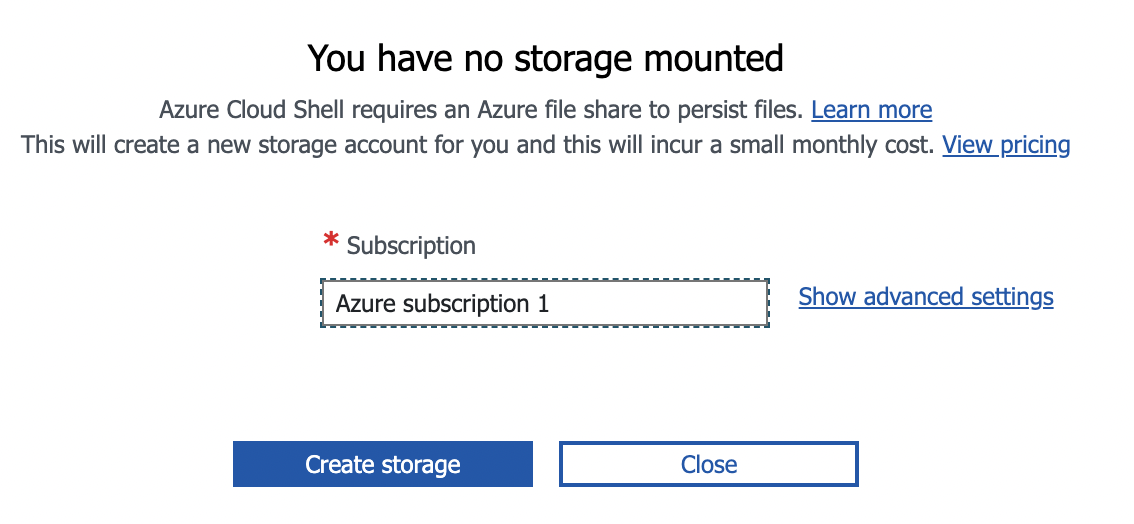
In the next screen, select the desired Azure Subscription & click on “Create storage” button.
-
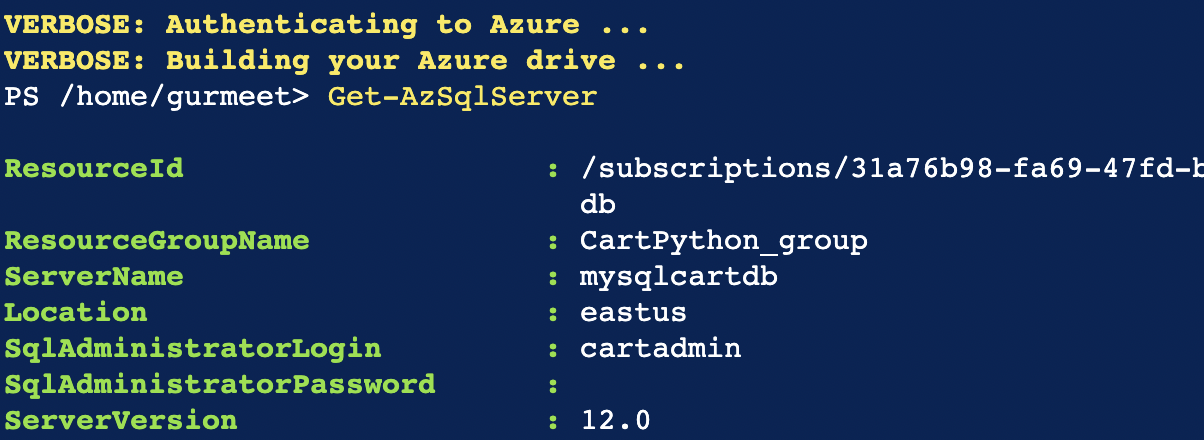
Run “Get-AzSqlServer” PowerShell command in the PowerShell prompt, to list all the “SQL servers” in the selected subscription. Note the “ResourceGroupName” and “ServerName” of the desired SQL server.
-
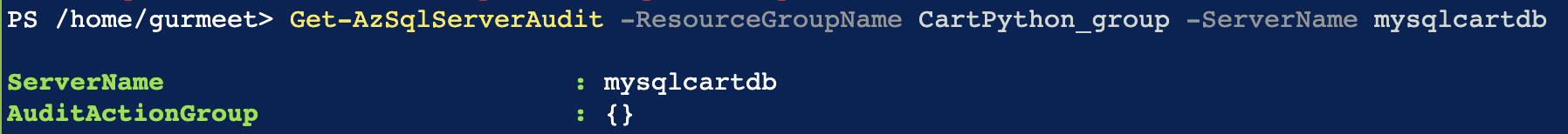
Run “Get-AzSqlServerAudit -ResourceGroupName your_resource_group_name -ServerName your_server_name” PowerShell command.

-
In the result if the “AuditActionGroup” property value is {}(empty) then Audit Action Groups are not enabled.
-
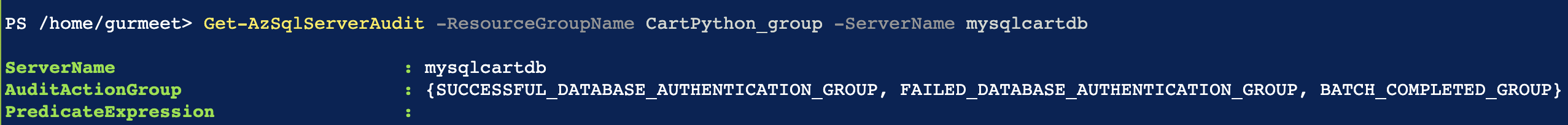
Run “Set-AzSqlServerAudit -ServerName your_server_name -ResourceGroupName your_resource_group_name -AuditActionGroup SUCCESSFUL_DATABASE_AUTHENTICATION_GROUP, FAILED_DATABASE_AUTHENTICATION_GROUP, BATCH_COMPLETED_GROUP”.

-
Run “Get-AzSqlServerAudit -ResourceGroupName your_resource_group_name -ServerName your_server_name” PowerShell command to verify that “AuditActionGroup” property value is not {}(empty).
-
Repeat step number 3-10 to check and configure SQL Server Audit Groups for all other SQL servers.