SQL Server Public Access
Ensures that SQL Servers do not allow public access
Unless there is a specific business requirement, SQL Server instances should not have a public endpoint and should only be accessed from within a VNET.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Microsoft Azure Management Console.
-
Select the “Search resources, services, and docs” option at the top and search for SQL servers.
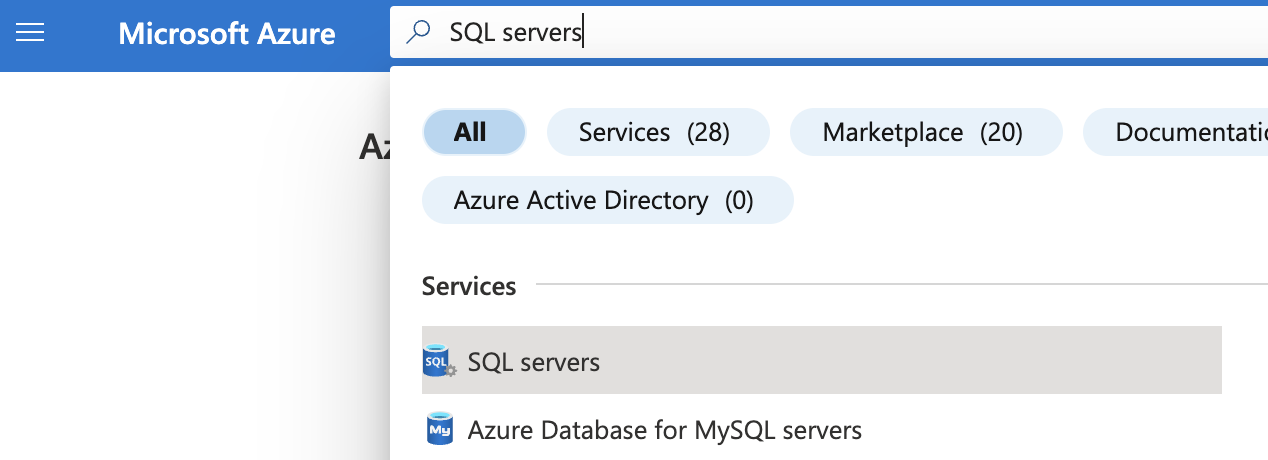
-
On the “SQL server” page, select the SQL server that needs to be examined.
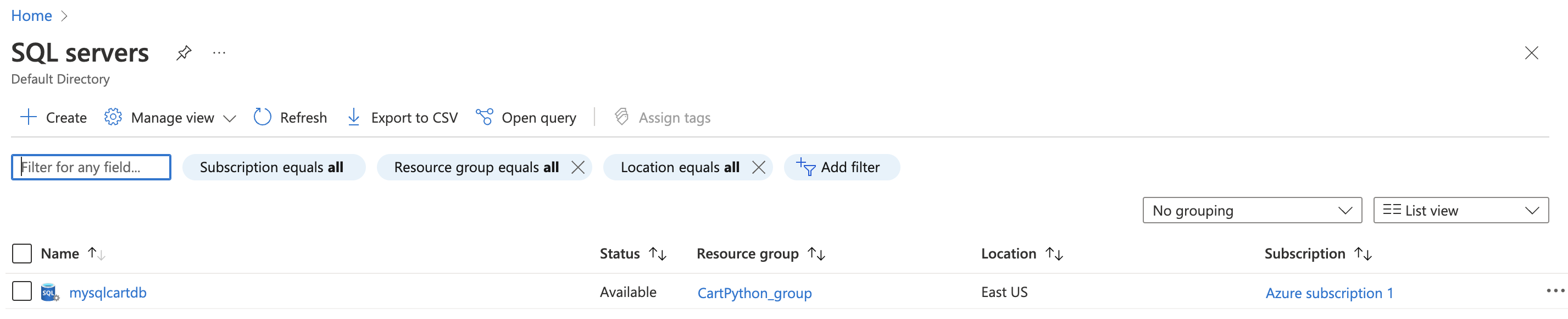
-
On the selected “SQL server” page, scroll down the left navigation panel and select “Networking” under the “Security”.
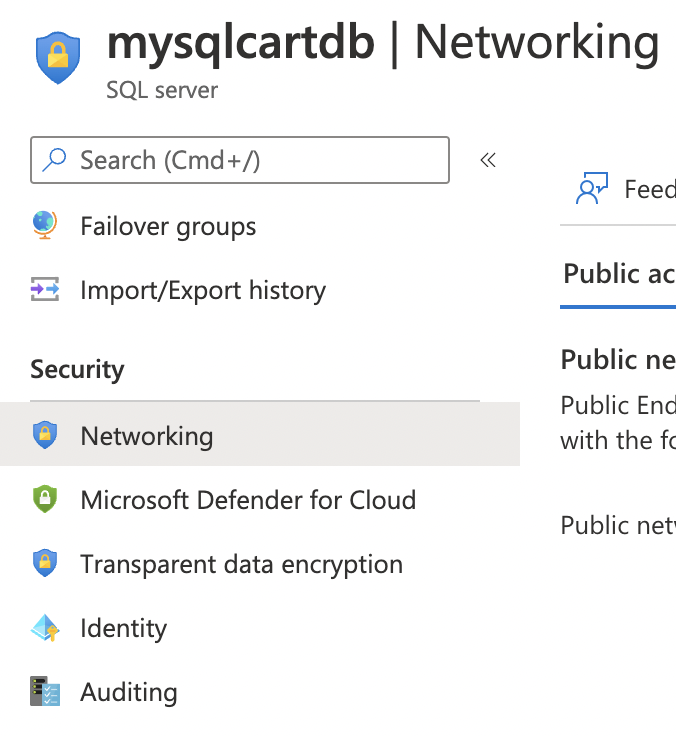
-
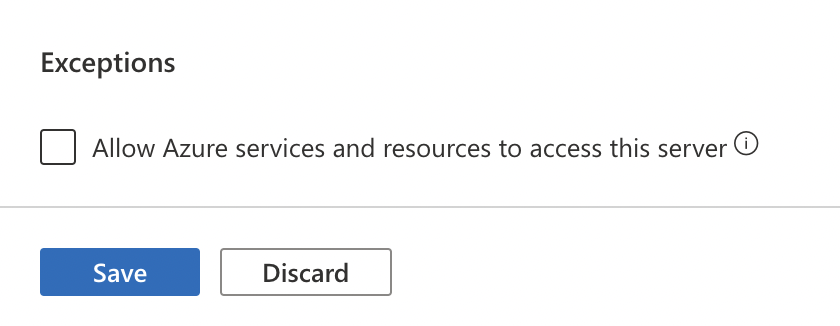
On the “Networking” page, under “Exceptions” if “Allow Azure services and resources to access this server” is “ON” then the selected “SQL server” allows public access.
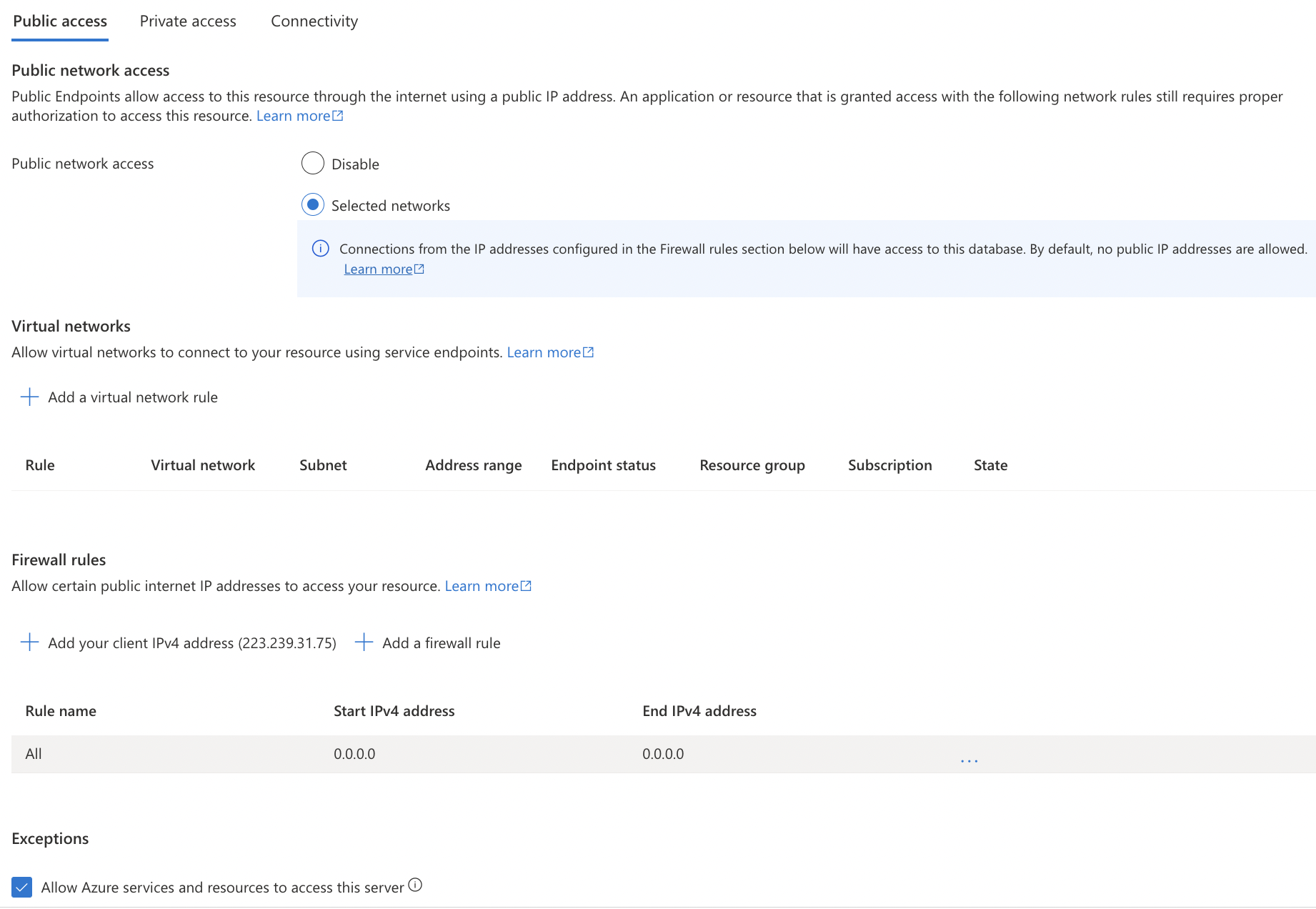
-
To disable public access, uncheck “Allow Azure services and resources to access this server” and click “save” button.
-
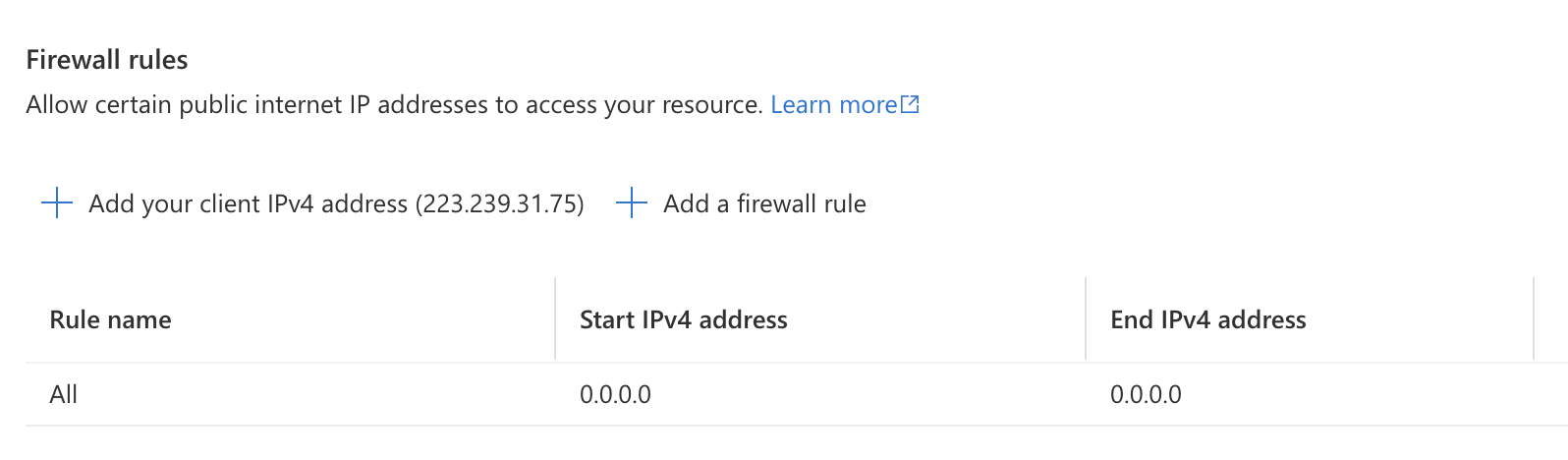
Under “Firewall Rules” if you see an entry for IP address “0.0.0.0” then traffic from global public IPs is allowed.
-
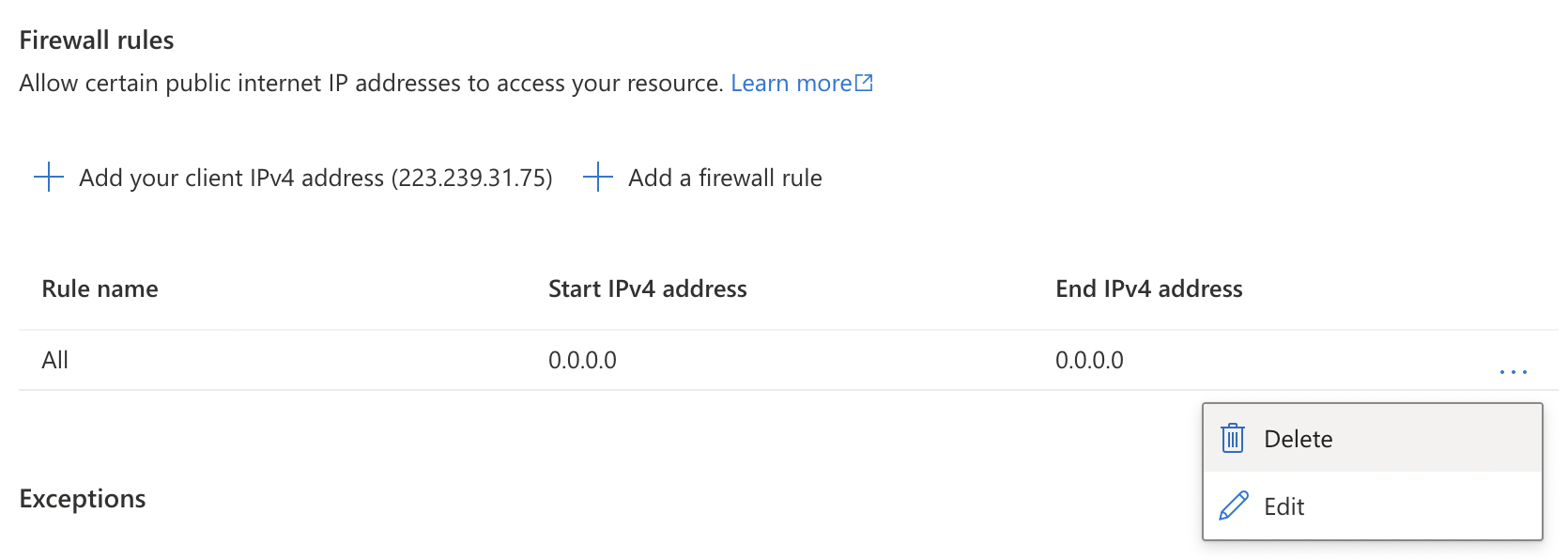
To disable traffic from global public IPs, remove the firewall rule with IP address “0.0.0.0”. To delete it, click on the triple dot (…) at the end and select “Delete” from the dropdown menu.
-
Click on the “Save” button to make the changes.

-
Repeat steps number 3 - 9 to ensure that the firewall of each SQL Server is configured to prohibit traffic from the public 0.0.0.0 global IP address.