TDE Protector Encrypted
Ensures SQL Server TDE protector is encrypted with BYOK (Bring Your Own Key)
Enabling BYOK in the TDE protector allows for greater control and transparency, as well as increasing security by having full control of the encryption keys.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Microsoft Azure Management Console.
-
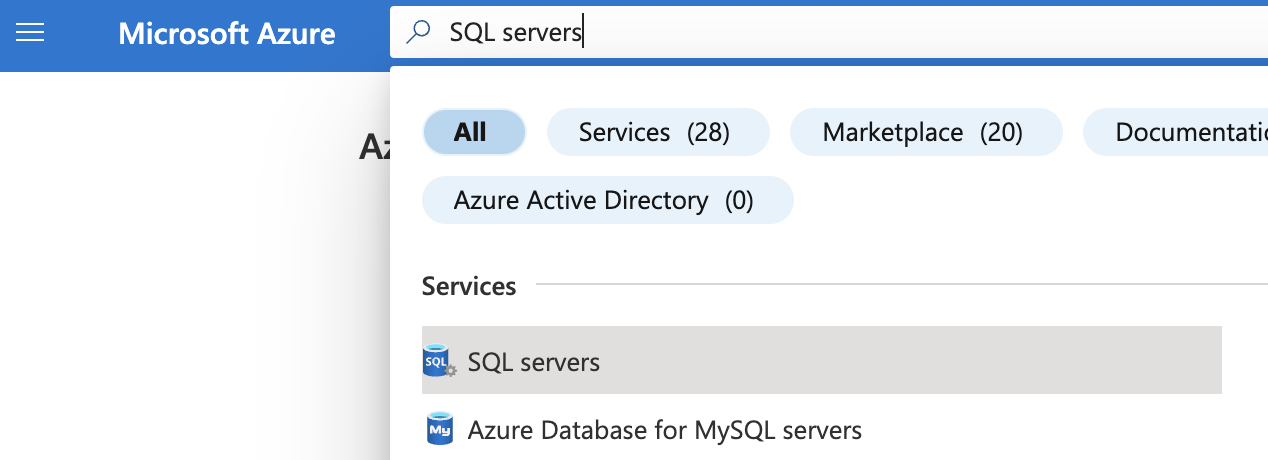
Select the “Search resources, services, and docs” option at the top and search for “SQL servers”.
-
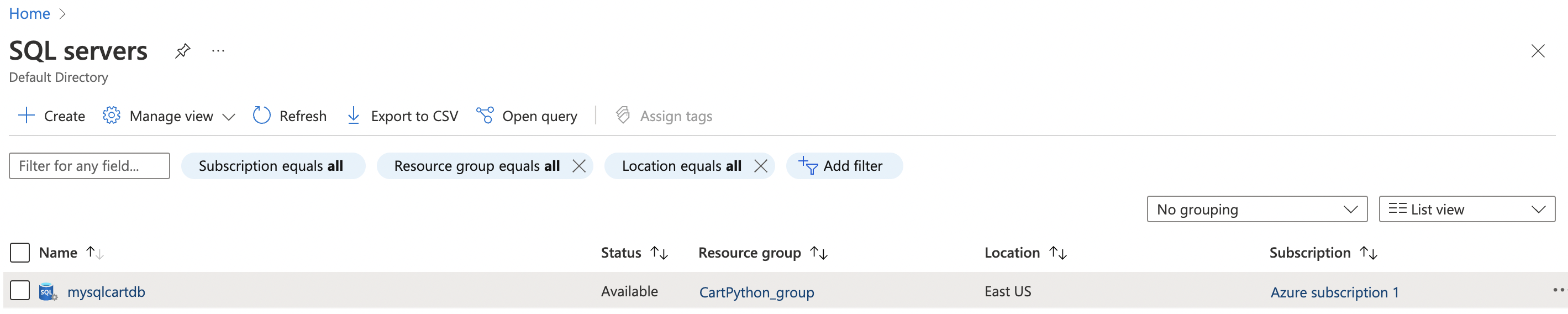
On the “SQL server” page, select the SQL server that needs to be examined.
-
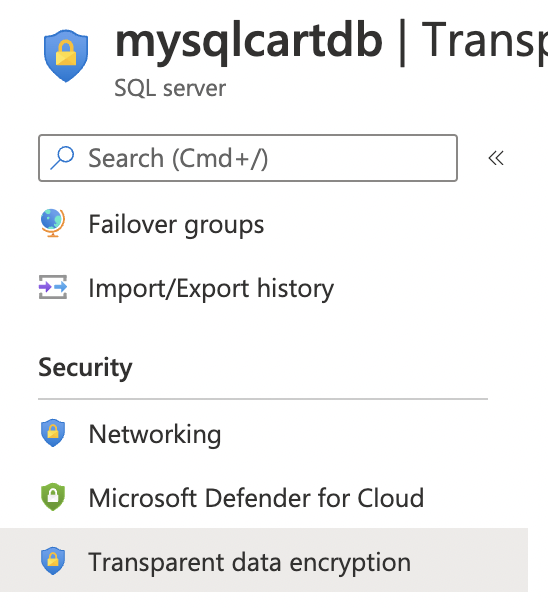
On the selected “SQL server” page, scroll down the left navigation panel and select “Transparent data encryption” under the “Security”.
-
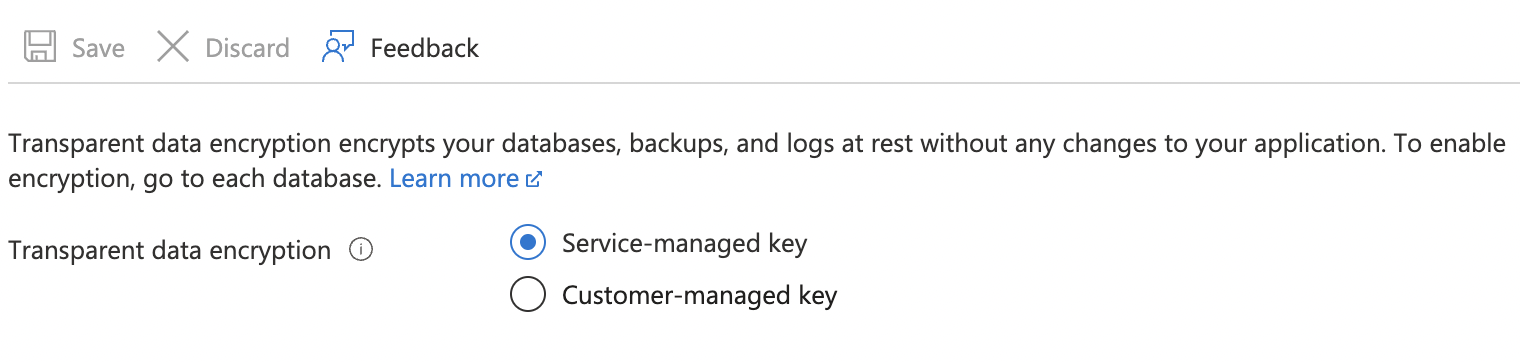
On the “Transparent data encryption” page, if “Transparent data encryption” is set to “Service-managed key” then the selected “SQL server TDE protector” is not encrypted with BYOK (Bring Your Own Key).
-
To ensure that a custom BYOK is used, select “Customer-managed key” for “Transparent data encryption”.
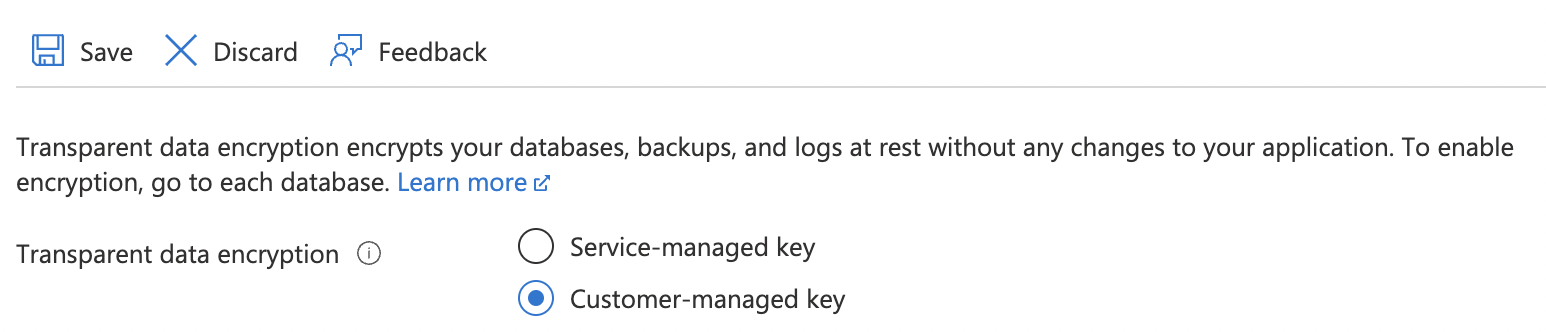
-
Under “Key selection method” choose “Select a key” and click on “Change key” under “Key”.
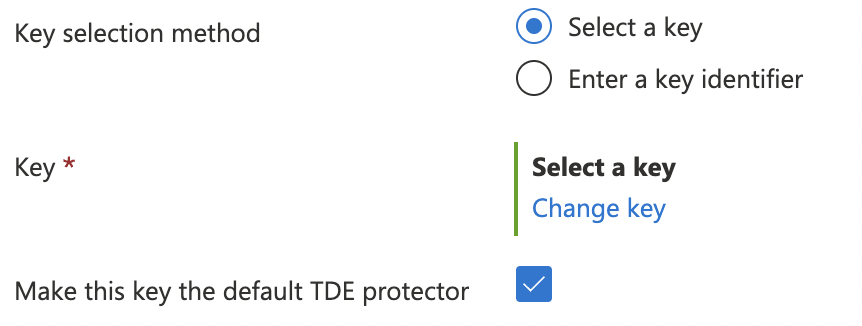
-
In the “Select a key” page, select the “Key vault” under “Key store type” and then select desired “Key” and “version” accordingly. Click on “Select” button at the bottom to proceed.
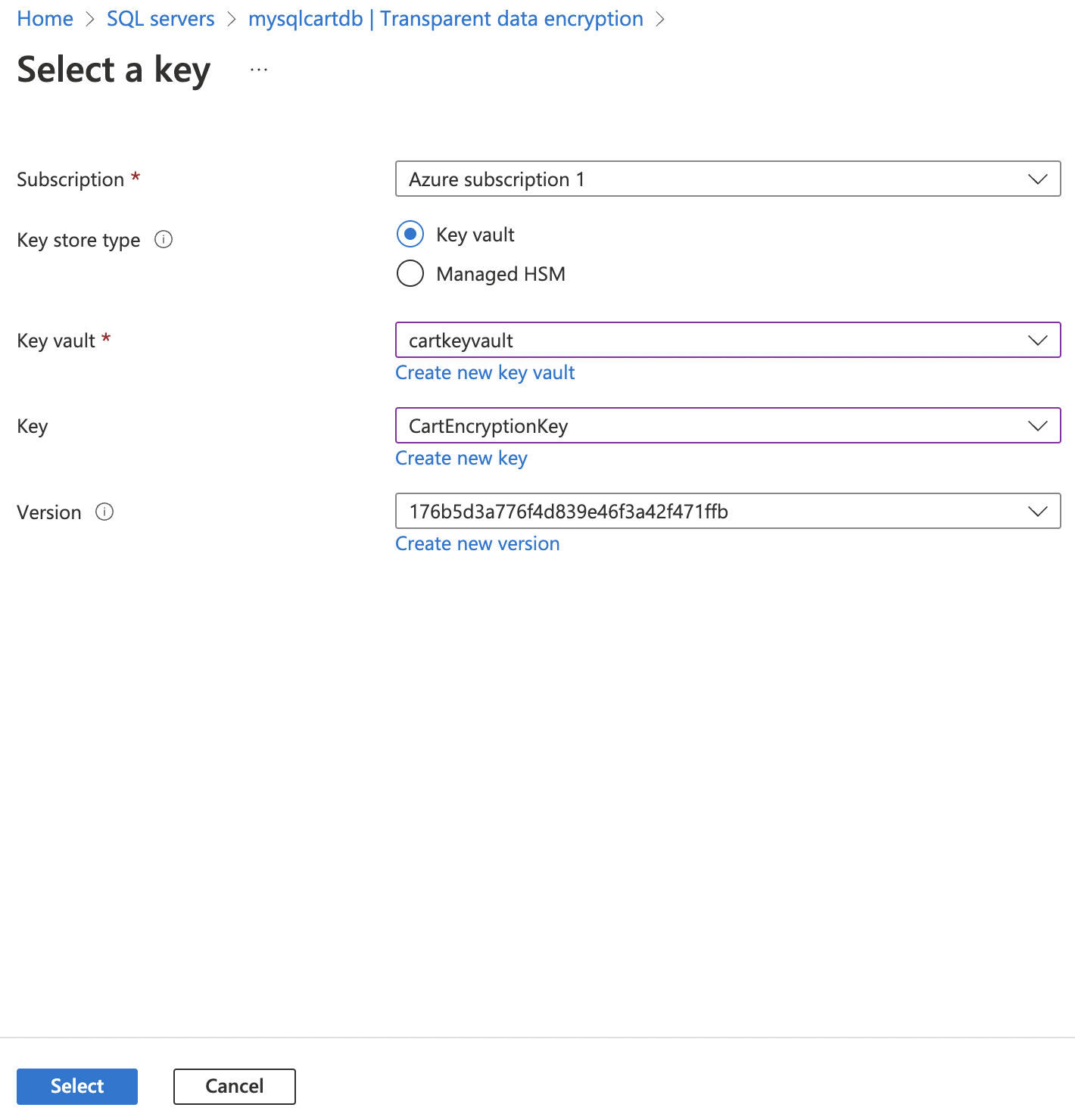
-
Click on the “Save” button at the top to make the necessary changes.
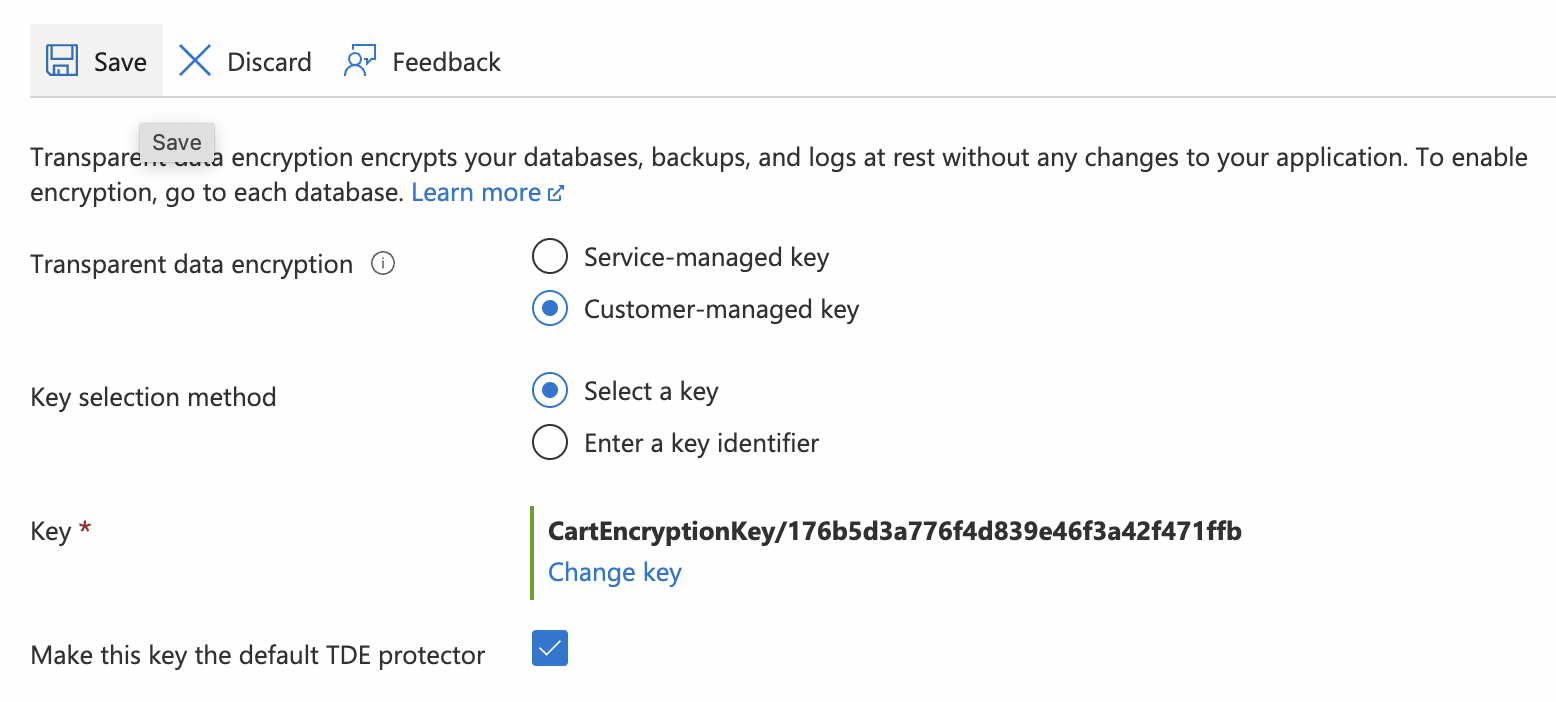
-
Reepat steps number 3 - 9 to ensure that a BYOK key is set for the Transparent Data Encryption of each SQL Server.