Log Container Public Access
Ensures that the Activity Log Container does not have public read access
The container used to store Activity Log data should not be exposed publicly to avoid data exposure of sensitive activity logs.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Microsoft Azure Management Console.
-
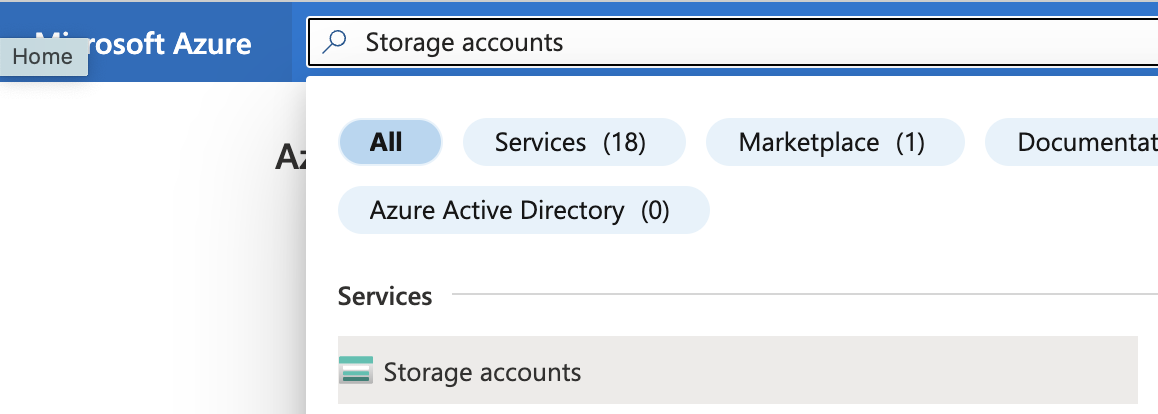
Select the “Search resources, services, and docs” option at the top and search for “Storage accounts”.
-
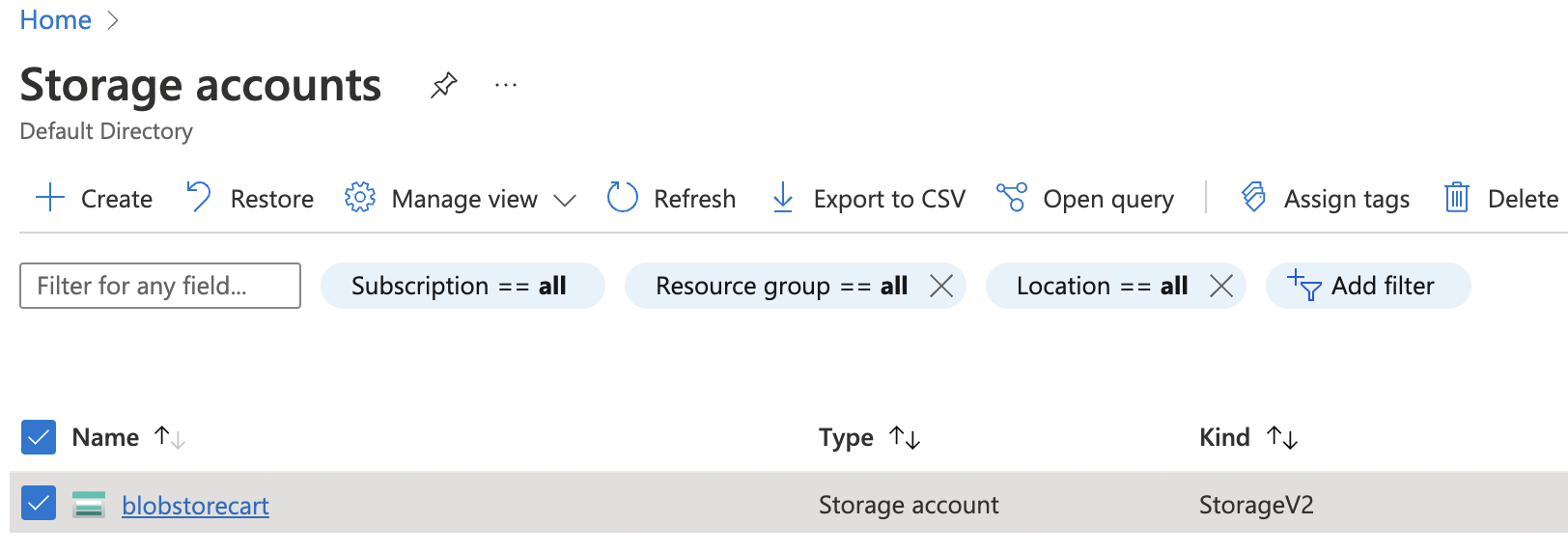
Select the “Storage account” by clicking on its “Name” to get into its configuration page.
-
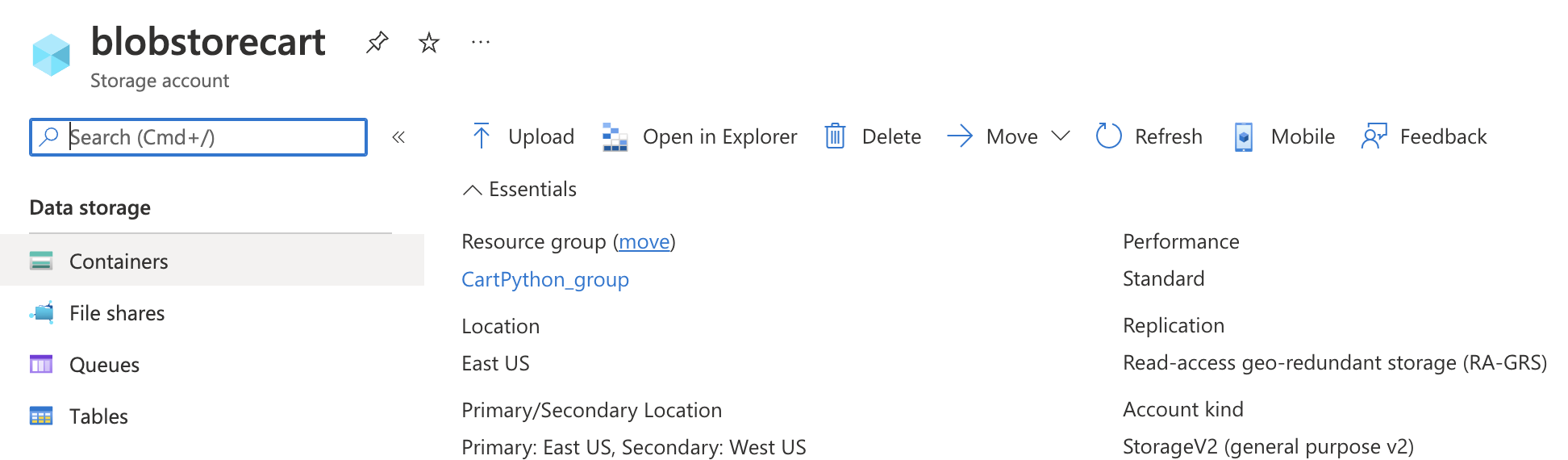
On the “Storage accounts” page, select the “Containers” under “Data storage”.
-
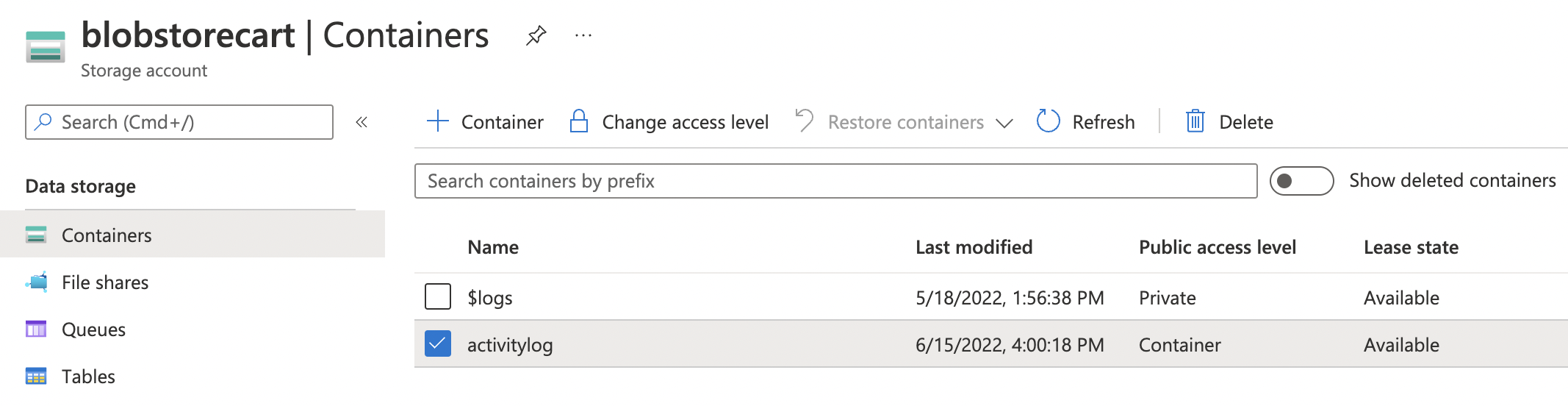
On the “Containers” page, select the “Activity Log Container” and check the “Public Access” column. If it’s not set to “Private” then the Activity Log Container has public read access.
-
Select the “Actvity Log Container” which needs to be set to private. Click on the “Change access level” option at the top.
-
On the “Change access level” page, click on the dropdown menu under “Public access level” and select the “Private (no anonymous access)” option.
-
Click on the “OK” button to save the changes.
-
Repeat steps number 2 - 8 to ensure the access level for the storage account containing Activity Log data is set to private.