Storage Accounts Encryption
Ensures encryption is enabled for Storage Accounts
Storage accounts can be configured to encrypt data-at-rest. By default Azure will create a set of keys to encrypt the storage account, but the recommended approach is to create your own keys using Azure Key Vault.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Microsoft Azure Management Console.
-
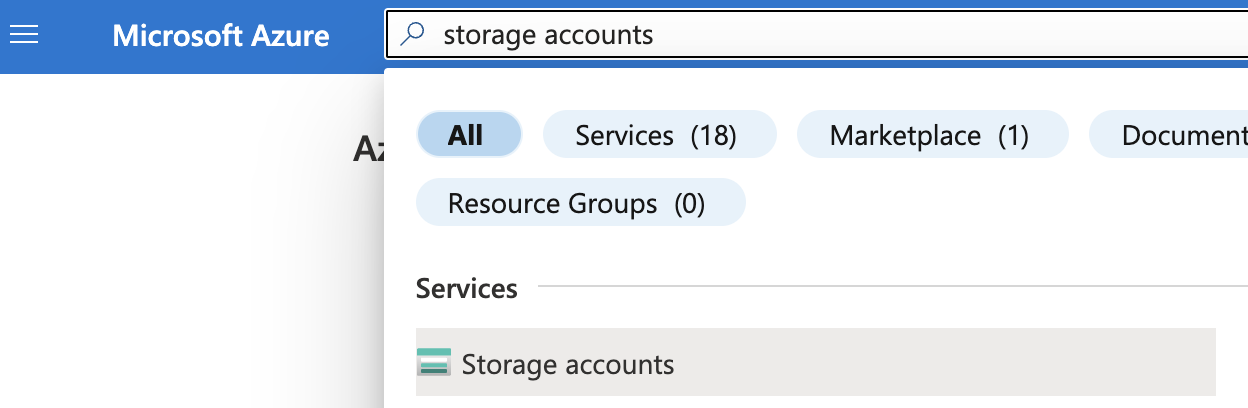
Select the “Search resources, services, and docs” option at the top and search for Storage account.
-
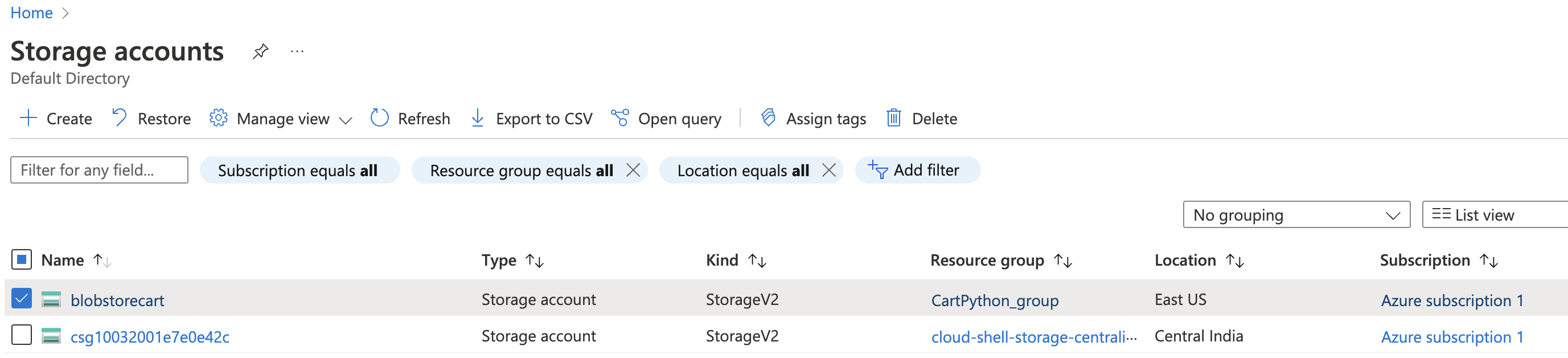
Select the “Storage account” by clicking on the “Name” link to access the configuration changes.
-
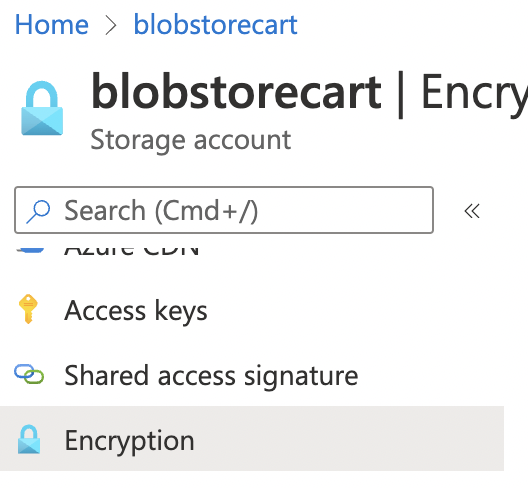
Scroll down the selected “Storage account” navigation panel and under “Settings” select “Encryption”.
-
On the “Encryption” tab if “Microsoft-managed keys” is seleceted then encryption is not enabled for Storage Account.
-
To ensure the selected storage Account is configured with a BYOK encryption select “Customer-managed keys”.
-
Under “Key Selection” select “Encryption key” as “Select from key vault”. In the “Key vault and key” click on “Select a key vault and key”.
-
On the “Select a key” page, select “Key store type” as “Key vault” and select “Key vault” and “key” from the dropdown. Click “Select” at the bottom.
-
Click “Save” button at the bottom.
-
Repeat steps 3 - 9 to ensure all Storage Accounts are configured with a BYOK key.