Trusted MS Access Enabled
Ensures that Trusted Microsoft Services Access is enabled on Storage Accounts
Enabling firewall rules on Storage Accounts blocks all access by default. To ensure that Microsoft and Azure services that connect to the Storage Account still retain access, trusted Microsoft services should be allowed to access the storage account.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Microsoft Azure Management Console.
-
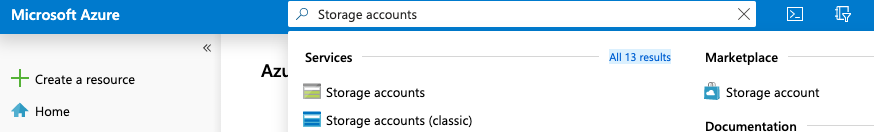
Select the “Search resources, services, and docs” option at the top and search for Storage account.
-
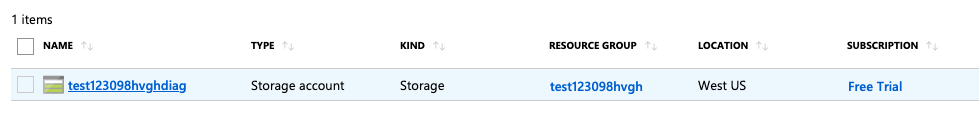
Select the “Storage account” by clicking on the “Name” link to access the configuration changes.
-
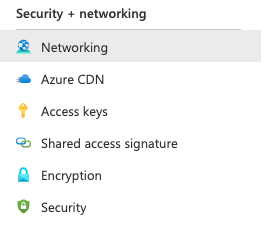
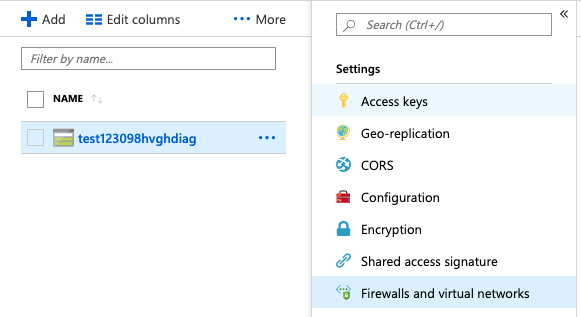
Scroll down the selected “Storage account” navigation panel and in “Security + networking” click on the “Networking”.
-
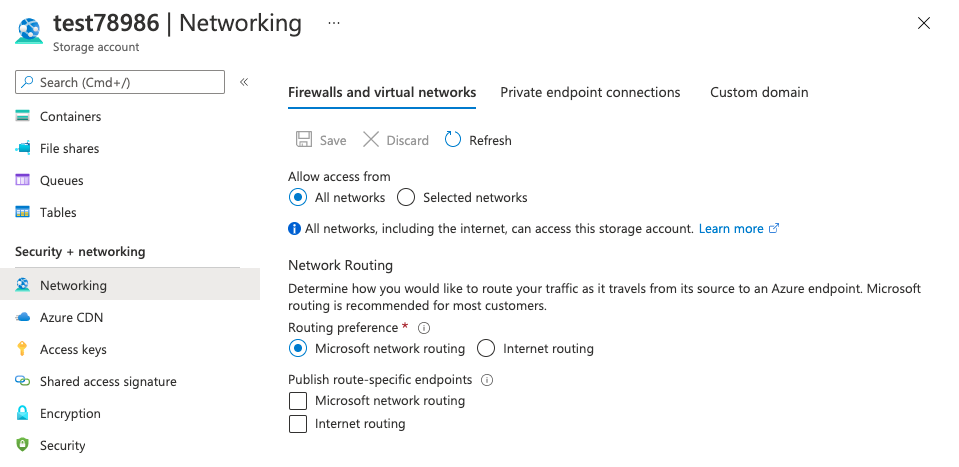
On the “Networking” tab scroll down and cross-check whether the “Trusted Microsoft Services Access is enabled on Storage Accounts” or not under “Exceptions”.
-
Repeat steps number 2 - 5 to check other “Storage account” in the account.
-
Navigate to the “Storage accounts”, select the “Storage account” and click on the “Name”, select the “Networking” under “Security + networking” that needs to disable the “Allow access for all networks.”
-
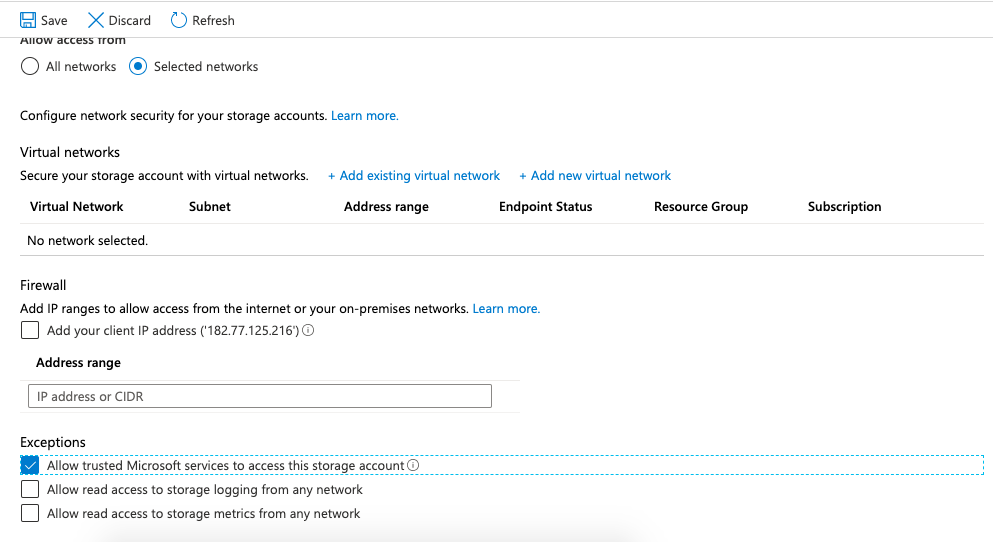
On the “Firewalls and virtual networks” tab under “Exceptions” choose the option of “Allow trusted Microsoft services to access this storage account” and click on the “Save” button at the top to make the changes.
-
Repeat steps number 7 - 8 to ensure that each Storage Account, has an exception for trusted Microsoft services.