Table Service All Access ACL
Ensures tables do not allow full write, delete, or read ACL permissions
Table Service tables can be configured to allow to read, write or delete on objects. This option should not be configured unless there is a strong business requirement.
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log in to the Microsoft Azure Management Console.
-
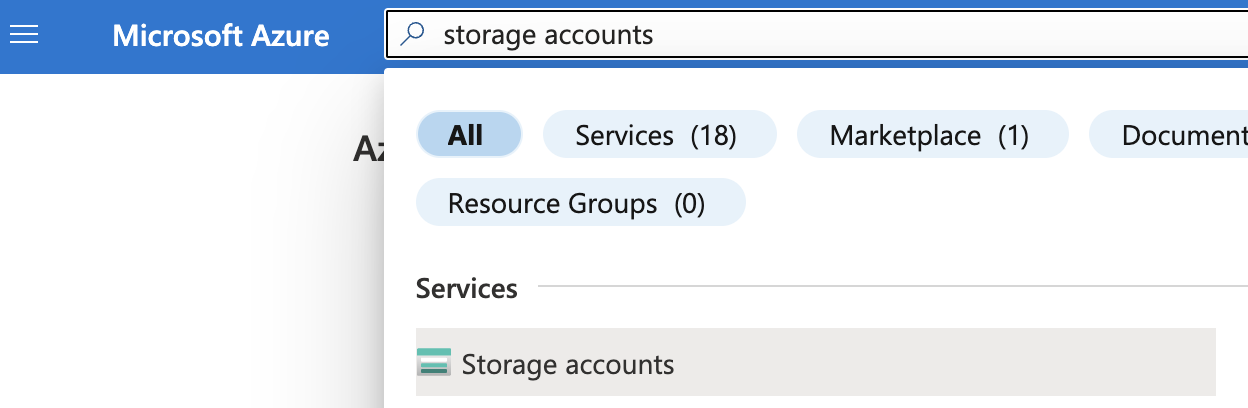
Select the “Search resources, services, and docs” option at the top and search for “Storage accounts”.
-
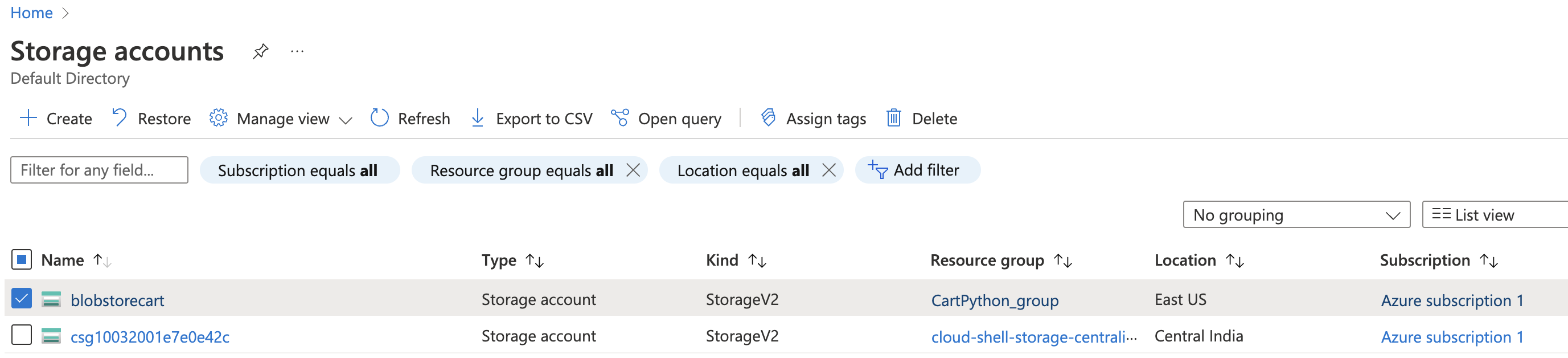
Select the “Storage account” by clicking on the “Name” link to access the configuration changes.
-
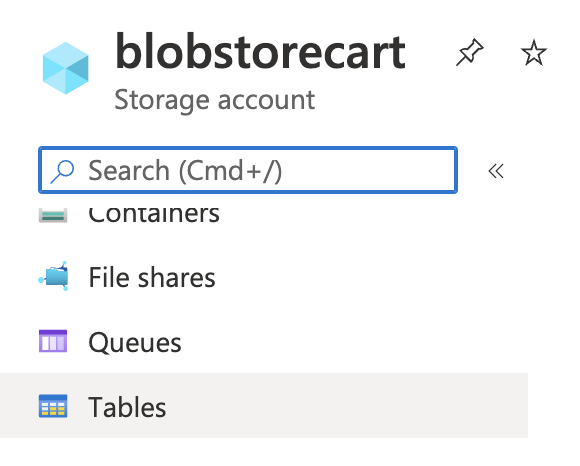
In the left navigation panel, click on the “Tables” under “Data Storage”.
-
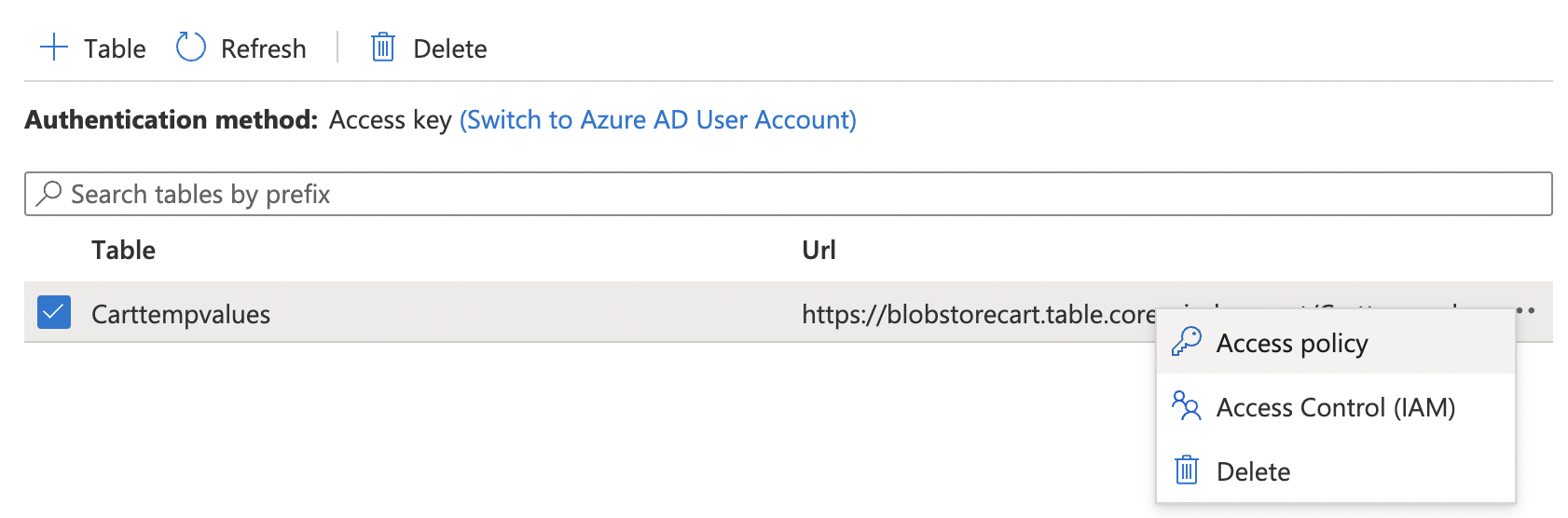
Select the “Table” by clicking on three dots (…) on the right corner to choose the “Access policy.”
-
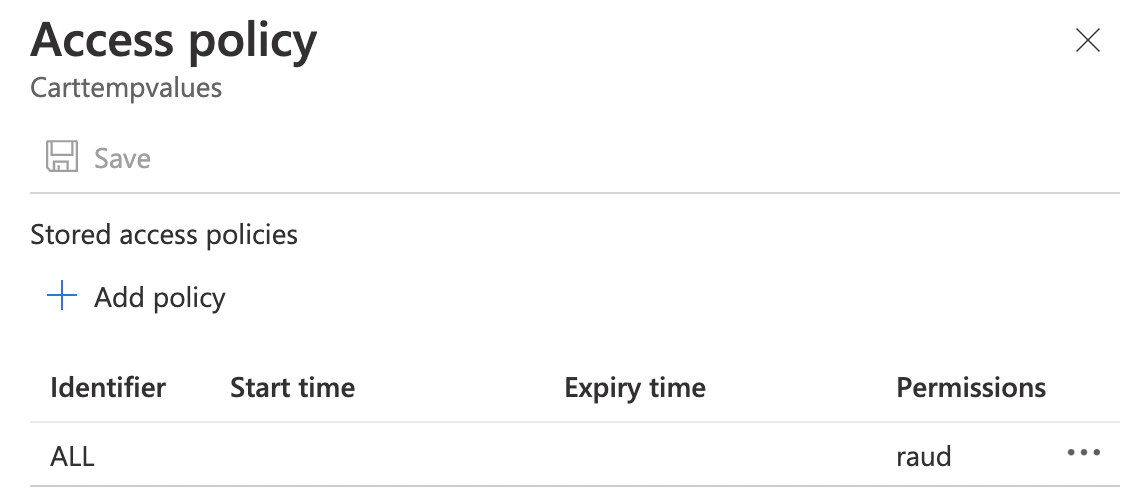
On the Access Policy panel on the right, check the “Permissions” assosciated with the “Table”. If the “Table” allows full read, write, delete and update permissions then the selected “Table” is not as per the standard configuration.
-
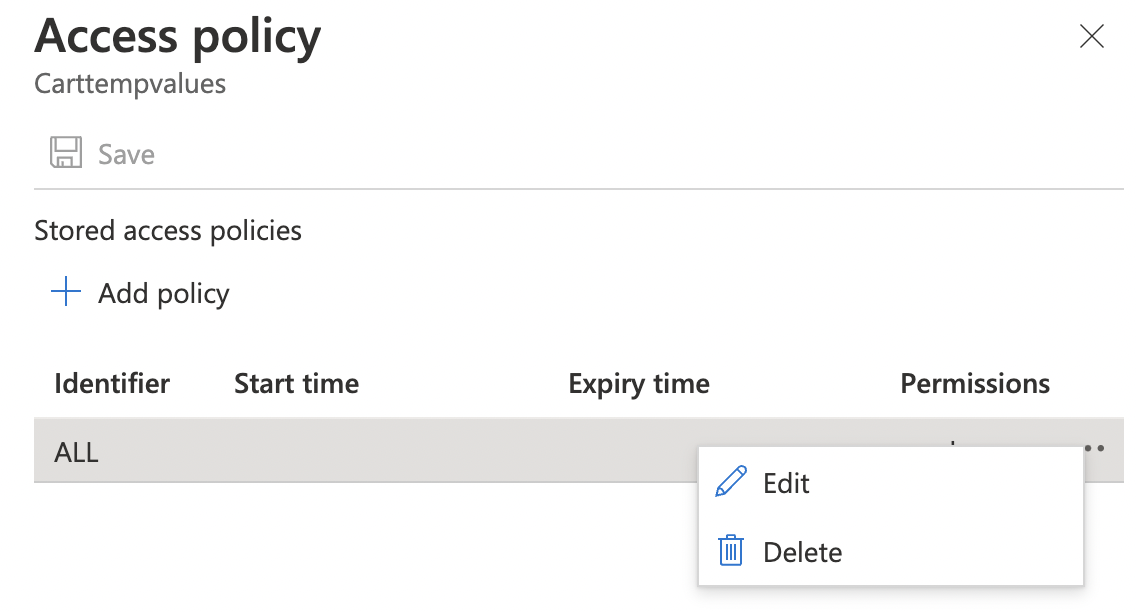
To ensure tables do not allow full read, write, delete and update ACL permissions, click on the three dots (…) on the extreme right and select “Edit”.
-
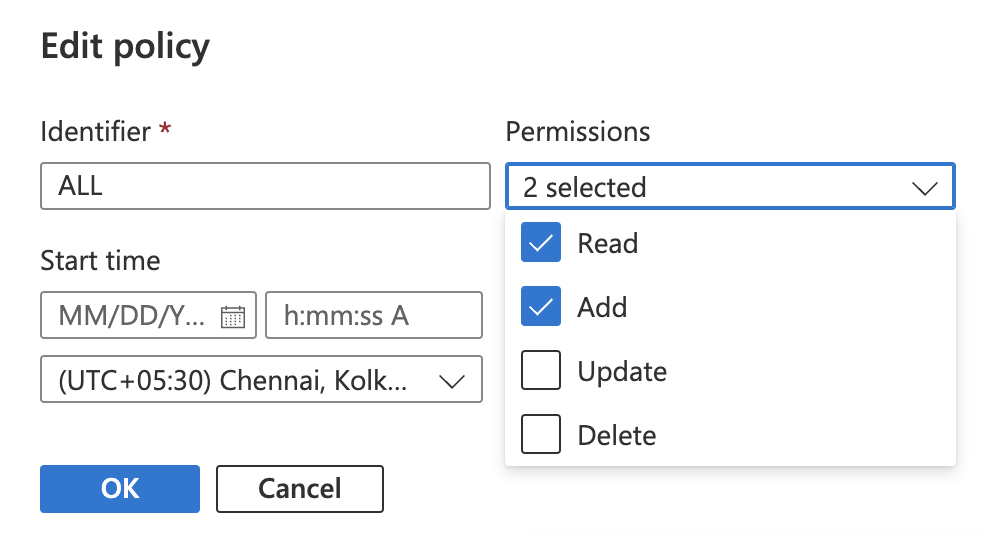
In the “Edit policy” popup uncheck the desired permissions and click on “OK” button.
-
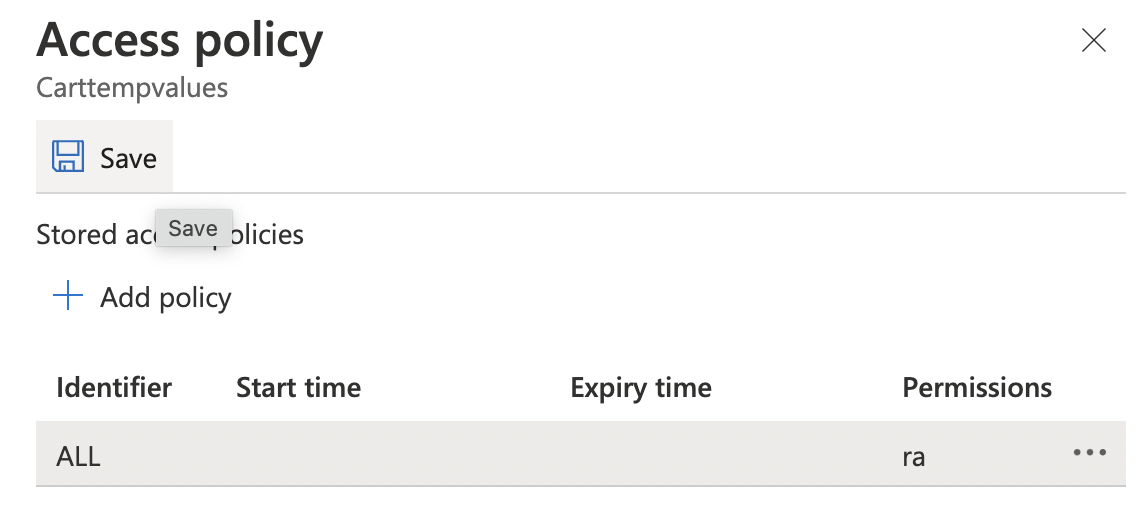
Click on “Save” buttton at the top to make the necessary changes.
-
Repeat steps 3 - 9 for all other tables.