Disable project-wide SSH keys for all instances
Use of project-wide SSH keys means that a compromise of any one of these key pairs can result in all instances being compromised. It is recommended to use instance-level keys.
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Google Cloud Platform Console.
-
Scroll down the left navigation panel and choose the “Compute Engine” to select the “VM Instances” option.
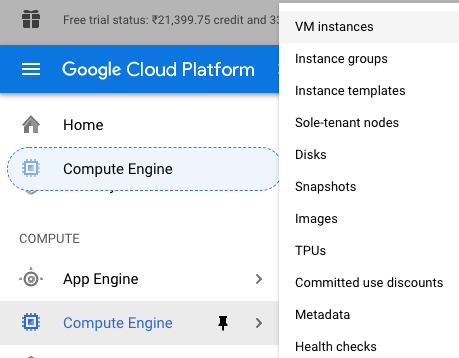
-
On the “VM Instances” page, select the VM instance which needs to be verified.
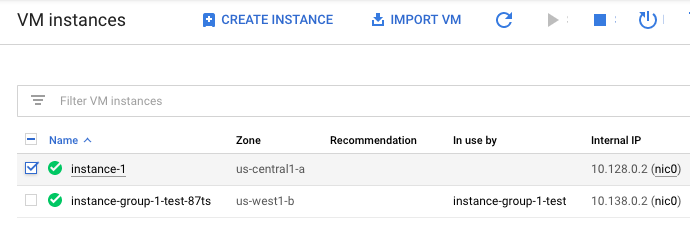
-
On the “VM instance details” page, scroll down and check “Block project-wide SSH keys” is enabled or not for VM instances.
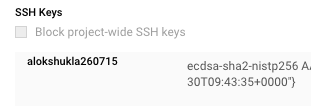
-
Repeat steps number 2 - 4 to verify other VM instances in the network.
-
Navigate to “Compute Engine”, choose the “VM instances” and select the “VM instance” which needs to enable “Block project-wide SSH keys” for VM instances.
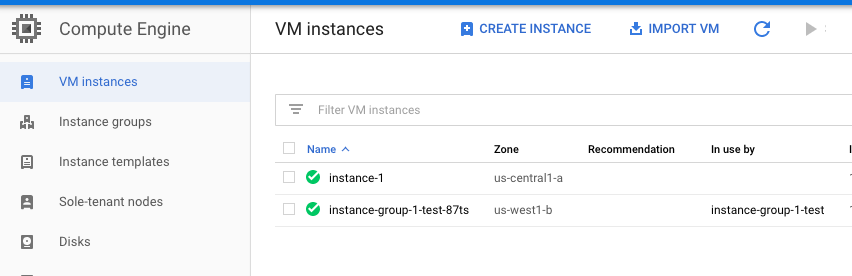
-
On the “VM instance details” page, select the “Edit” button at the top.
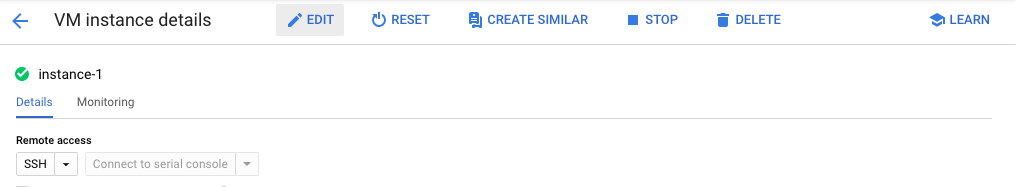
-
On the “VM instance details - Edit page”, select the checkbox next to “Block project-wide SSH keys.”
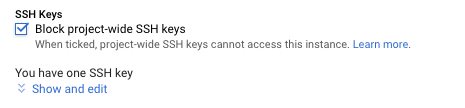
-
Click on the “Save” button to make the changes.
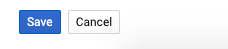
-
Repeat steps number 6 - 9 to ensure project-wide SSH keys are blocked for all instances.
Disable project-wide SSH keys
|
|