Disable serial port connectivity for all instances
When serial port access is enabled, the access is not governed by network security rules meaning the port can be exposed publicly.
Impact
Recommended Actions
Follow the appropriate remediation steps below to resolve the issue.
-
Log into the Google Cloud Platform Console.
-
Scroll down the left navigation panel and choose the “Compute Engine” to select the “VM Instances” option.
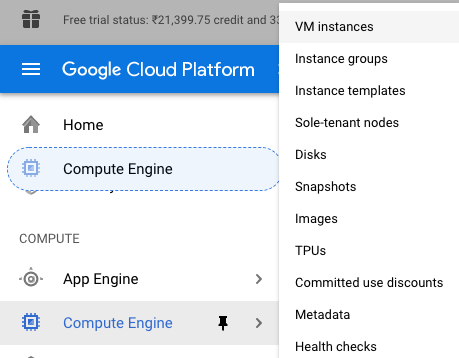
-
On the “VM Instances” page, select the VM instance which needs to be verified.
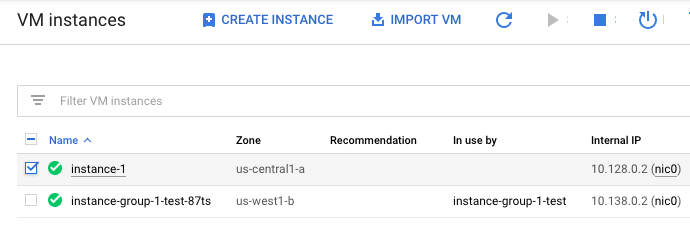
-
On the “VM instance details” page, scroll down and check “Enable connecting to serial ports” is enabled or not for VM instances.
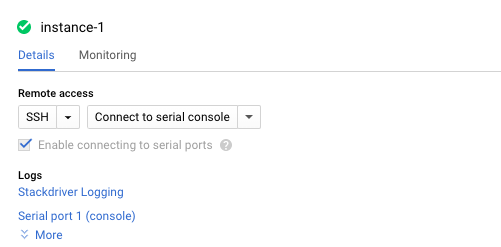
-
Repeat steps number 2 - 4 to verify other VM instances in the network.
-
Navigate to “Compute Engine”, choose the “VM instances” and select the “VM instance” which needs to disabled “Connecting to serial ports” for VM instances.
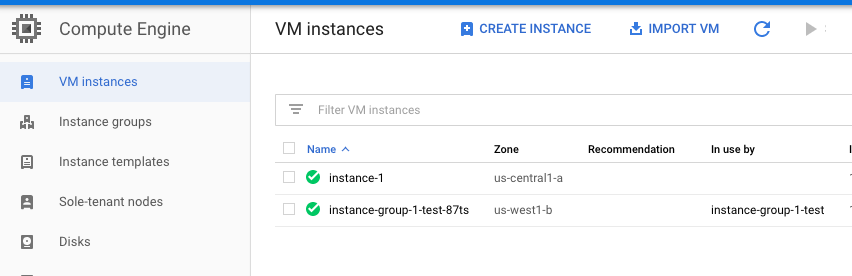
-
On the “VM instance details” page, select the “Edit” button at the top.
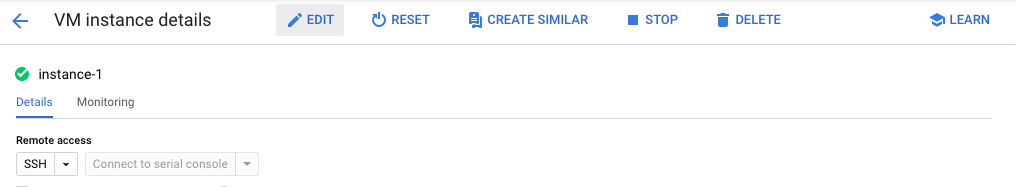
-
On the “VM instance details - Edit page”, unselect the checkbox next to “Enable connecting to serial ports.”
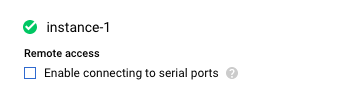
-
Click on the “Save” button to make the changes.
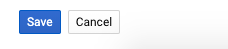
-
Repeat steps number 6 - 9 to ensure the “Enable Connecting to Serial Ports” option is disabled for all compute instances.
Disable serial port access
|
|